Need assistance willing to pay up
-
Again I have MULTIPLE roku's You only have to discover them once - then you can switch to them in the APP... You do not need to be on their network to control them.
I just sent into the guest bedroom, fired up that roku and controlled it with my phone.
Also - if you want to control your rokus, just connect your phone to vlan 20... I mean how freaking hard is that?
All of my rokus are on a roku vlan, along with my directv box.... And my harmony remote.. If I use my phone I Just pick the device
-
@johnpoz I will attempt your method, but with due respect, please hold the condescension, It is apparently hard enough where i am offering to pay for help and there are many others on the internet with the same issue.
-
There is a strong chance what you are wanting to do is not possible....not because of pfSense, rather the Roku software won't allow it. We cannot fix that limitation.
-
If that is true than so be it. I do not know enough about networking to know how the different discovery protocols work and broadcast. Again, I will try what @Derelict suggested and see what i come up with, Thanks all!
-
@johnpoz As an FYI, this did work as you described, Thank you, I just am at the mercy of always being told by a family member that somethings isn't working, so I fear, they update the Roku Remote app etc, then it stops being able to connect. It would be easier if it could discover across VLANS as I use SSID whitelisting and getting a new device becomes a process, but not a very heavy lift.
However, Thank you for the resolution.
-
Why these companies rely on multicast or broadcast discovery is beyond me.. You should be able to just hard code the IP of the device..
So the port used per their SDK for controlling them is 8060..
A quick sniff validates that.
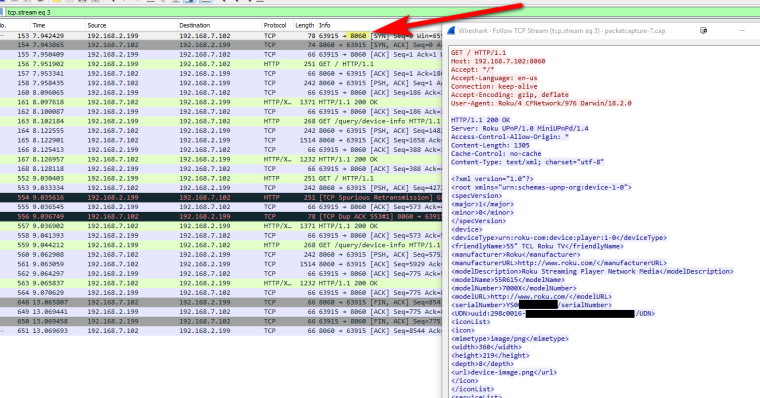
So as long as you don't block port 8060 from your vlan 1 to your vlan 20 you should have no issue.
To be honest allowing multicast from 1 vlan into another vlan defeats the whole purpose of vlan isolation. If your going to allow that you almost might as well just run everything on the 1 vlan.
I would hope your users smart enough to connect to different vlans... if they have issues talking to a roku, just have them switch over to the vlan 20 ssid.
Here is some fun on this link too on how to send out your own ssdp query
https://sdkdocs.roku.com/display/sdkdoc/External+Control+APIBut to be honest the roku app atleast on the ios even mentions that you should be on the same wireless, and lists the wireless your on.. Or click little button to put in the IP of your roku.. This is where IP reservations come in handy so your roku's always have the same IP... Still need to do that for my TV.. it was xmas gift to myself and havn't gotten around to it yet... Doing that now ;) hehehe
-
I did see this as well with a capture however this was before putting my phone on VLAN20, there wasn't much I could do as I could not see the Roku from my app. I had an any any rule in place between the segments for the Roku IP and still nothing.
After moving my phone to VLAN20 I was able to see a connection to 8060,
I appreciate the assistance I mean I've tried everything I created anilao rule for the multicast addresses that I saw for ssdp and mdns I was just at a loss.
So it seems the upshot is allow 8060 but I'll have to move the device to the VLAN temporarily and then back. I appreciate you taking the time to take the capture and working with me on this.
-
Good excuse to do my own research ;) I had never bothered to look at their SDK before... Seems you could do some pretty neat shit if you wanted too...
Doesn't look too secure heheeh - might have some fun over at buddies house and their roku's hehehe
I am not really a fan of multicast anything to be honest... I block it from a few things on my network.. Damn plex server can not get it to stop sending out discovery every freaking 10 seconds... So I just put in an ACL at the switch port.. F U I say plex... My query on their forums on how to make it stop got nothing in response..
My wife prints some stuff every now and then via airprint from her phone or ipad. I told her if not working make sure your on this SSID.. If she can figure that out.. pretty sure your family can be trained as well... hehehehe
-
At least they seem to give you the option of entering an IP manually. That's more than many app developers doing similar things.
-
@stephenw10 yeah that's kind of cool but it didn't work unfortunately not sure why it still needed to discover it
-
@johnpoz said in Need assistance willing to pay up:
To be honest allowing multicast from 1 vlan into another vlan defeats the whole purpose of vlan isolation. If your going to allow that you almost might as well just run everything on the 1 vlan.
@johnpoz How is allowing multicast between defeating the purpose of vlan isolation?
-
Because you just joined the L2s, they are no longer 2 different networks.. You might as just put everything on 1 L2 and not have to deal with any of such issues.
-
@johnpoz So while I can now connect to some device in my iot vlan over a random udp port after making changes to allow Roku through... the IOT vlan isn't capable of connecting back to my super secret server with ssh exposed.
Badly implemented network stacks in the Roku app does not mean segmenting networks and poking holes in them to allow known services through is a bad idea - it's the entire point of segmentation. -
L2 discovery makes it easy for grandma to find her shiny new roku from here phone.. But should be able to just point the IP in the client.. So I can open the port(s) needed and be done with it..
I shouldn't be letting anything in L2 A discover anything it wants in L2 B.
-
@johnpoz
The ability to discover and the ability to connect are two very different things.
I can discover what the IP address of company's SMTP server is all day, it does not mean I can connect to it. In fact, I can "discover" infrastructure all day courtesy of the internetz and dns records but that doesn't mean much thanks to segmentation. -
Oh my gawd you have users here hiding their rfc1918 space because they think they are giving away something... While you think its ok for all your iot devices on your isolated vlan to discover anything they want on any other vlan you have...
Have at it... It not good practice..
here
https://www.sans.org/reading-room/whitepapers/networkdevs/paper/246
IPv4 Multicast Security: A Network PerspectiveIn some home network is not a big deal most likely.. But the problem is letting people think its ok to just have data flow from 1 L2 to another L2 is introducing them to bad security practice..
-
@johnpoz So to that point we should not use Avahi, IGMP Proxy, and disallow IGMP from leaving L2?
Thank you. -
Ideally, yes.
But as with many things security vs convenience is a trade off. If you are aware of the risks then you can make an informed decision about the convenience.
As has been said for most home users the risks with allowing multicast between L2 segments are minimal but increased convenience is substantial. But that's not the case in other environments.
Steve
-
@Digital_ADHD said in Need assistance willing to pay up:
we should not use Avahi, IGMP Proxy, and disallow IGMP from leaving L2?
In my opinion no you shouldn't I sure wouldn't use them.. But your take might be different.. Without fully understanding the security implications that might be involved, its better to just isolate them completely.. Like these iot devices. I wouldn't put them on my normal vlans. The only thing I allow my roku's to do from their vlan is talk to my plex on 32400. I have found zero reason to allow multicast from 1 L2 to another in my home.. You know the simple solution for air printing to your printer from your wifi network.. Put the printer on the same vlan.. Done - no L2 boundaries to cross no avahi to setup, etc.
My devices on my lan network have no issues getting to the printer, since they just print to the IP.. But when my wife wants to print from her phone or tablet.. She can still use L2 discovery to find it (airprint).. Now no multicast spreading into any of my other vlans.. Its isolated to that L2 those devices using that shit are on.. Be it a security concern or not - its noise I don't need my other networks.
My iot devices are isolated - what exactly would they be discovering.. Other than joining that IOT wireless vlan to setup a new devices that needs L2 discovery have zero reason for my mobile devices to join that network Once the devices are discovered I don't need to be on that network... I can control my roku's just fine from my phone without being on the roku vlan... Need to join it once to discover any new roku's but once the roku is found no need to be on that vlan again.
Don't need to be on any specific L2 to control any of my smart lightbulbs, power outlets, etc.
The big word used here is "convenience" which is always going to be at the cost of security. If what you want is for shit to be convenient.. Why not just 1 flat network, where everything is on the same L2.. Its easy that way ;)
Just because pfsense provides a feature, doesn't mean you "have" to use it ;) Its provided for the people that want to use it, or maybe need to use since sure that would be better than 1 flat network ;) But its not something that to be honest should be required.. I have many a techy device in my home. Alexa's, Smart Bulbs, I get alerted when my garage door opens and closes, can control from my phone even. My thermostat is connected, nest protect, harmony remote, etc. etc. None which any of them require to break the L2 boundary to function. All of these devices are isolated to their own vlans and don't touch any other network.. Other than the roku's can talk to my plex.. And I let them talk to my ntp server that is on its own isolated dmz vlan.