Auto update check, checks for updates to base system + packages and sends email alerts
-
2025-08-13 update: The script has been minimally updated and is confirmed compatible with pfSense 2.8.x and 25.07. I'm waiting for a base system update (e.g. 25.07.1) to confirm that those are properly detected.
Here's an "automatic update checker" for pfSense. The script will check for major updates to the base pfSense system, as well as updates to any builtin or installed packages. If any updates are found, an email summary will be sent out with the details.
I wanted to put this out there now, get feedback, comments etc. My goal is to make this into an actual pfSense package to make it simpler to install, but I'm still learning how to create packages. This should still be useful as-is. (Any pointers anyone has on getting this cobbled together into a real package would be greatly appreciated!)
To install:
- Download the script from GitHub, unzip it, and copy
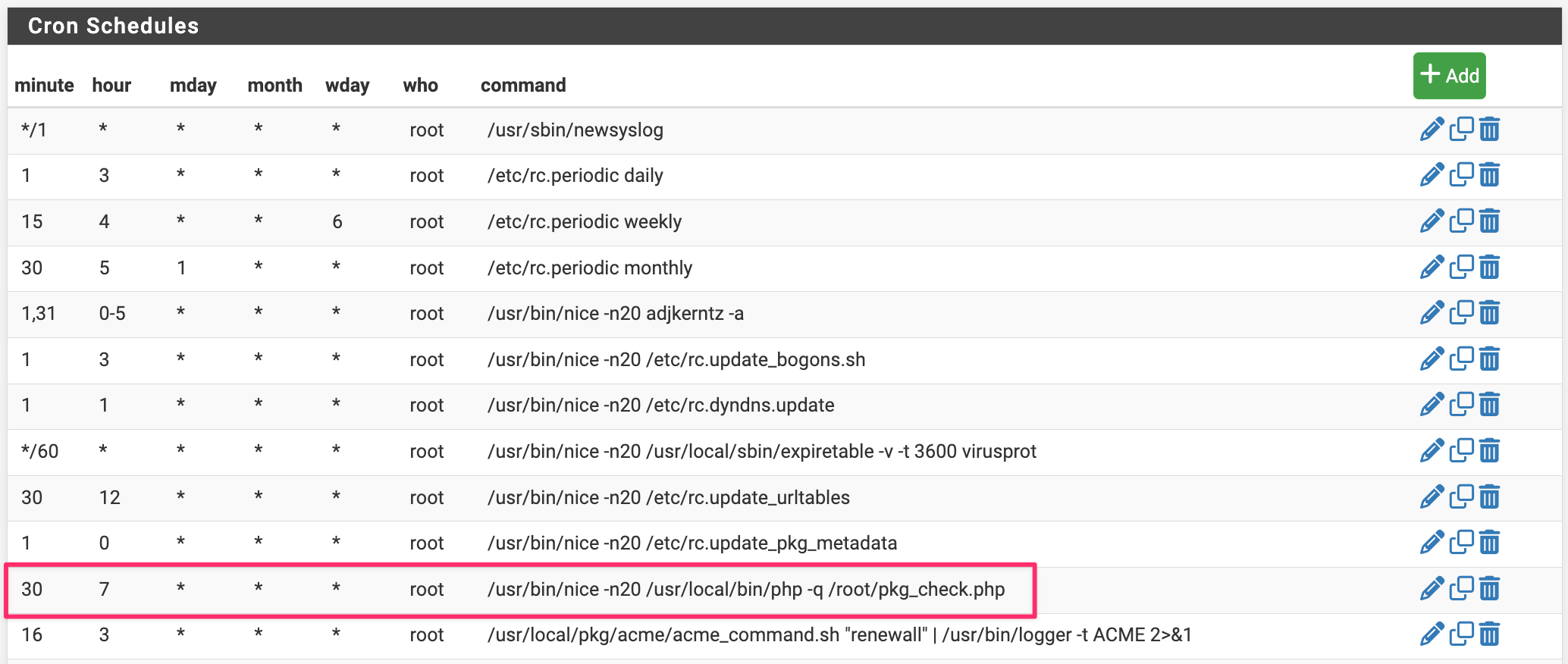
pkg_check.phpto the/rootdirectory of your pfSense firewall - Set it up to run on whatever schedule you like using the Cron package. A sample screenshot* of how to configure the script is below.
- Make sure you have valid SMTP (or other notification types) settings defined so you get the alerts!
- To change the notification type from email to Slack, Telegram, or Pushover– modify lines 93-95 and uncomment (remove the
//) the lines pertaining to your service - If you just want to send alerts to all configured targets, see the note on line 88 and make that small change
*if you want to copy/paste the Cron command, use:
/usr/bin/nice -n20 /usr/local/bin/php -q /root/pkg_check.php - Download the script from GitHub, unzip it, and copy
-
Needs more blinkenlight action!

Steve
-
Pkg update notification has been at the top of my wish list for a while. I’ll difinately give this a try.
-
This works great btw. Only problem I had getting it setup was a typo due to the fact that I missed a space in your cron screenshot.
-
Glad to hear you got it working! I added a little text block below the screenshot to make it copy/pasteable.
-
Nice job, like the way you set out the easy copy & paste also
-
@luckman212 Thanks for this it works great!
I notice the email notification mentioned updating packages that are not in the package manager via pkg update. There were a few packages not in the package manager which had new versions. I did the update and all went well. However, I was reading that the pkg update (FreeBSD method?) is not a supported pfSense update method.
https://forum.netgate.com/topic/118626/pkg-update-upgrade-vs-console-webgui-updates
In there it mentions the only methods supported are the GUI update and option 13 from console/SSH. This particular thread did not mention the GUI method for updating packages but that must be supported as well.
My guess is as long as updates to the actual pfSense version and installed packages are done via the GUI and/or option 13, then updating the remaining packages via pkg update should not be an issue?Thanks,
Raffi -
@raffi_ said in Auto update check, checks for updates to base system + packages and sends email alerts:
I notice the email notification mentioned updating packages that are not in the package manager via pkg update.
Probably those: https://forum.netgate.com/topic/140637/update-pfsense-packages-to-protect-against-nginx-libzmq4-and-curl-vulnerabilities you better update them.
-
@Grimson Thanks for the link. Yes, those were the exact updates which came up. I went ahead and updated them when I got the email notification thanks to the script. I'm on 2.4.4-p2. Wow they were major security updates I wouldn't have known about with this script. You learn something new everyday.
Thanks for the help and education guys.
Raffi -
@raffi_ The post you linked to was pretty old. Updating via console should be safe as long as you have not messed with the repos. It's basically the same process that occurs when you update via the GUI, as
pkgis always used anyway. -
@luckman212 Awesome, thanks for the explanation. You're being too modest :)
I learned your script is not the same as the GUI update, it's actually better! The GUI didn't tell me about those vulnerabilities in the packages which required updating, but your script did.Raffi
-
This post is deleted! -
Nice plugin - has anybody made an Nagios or CheckMK plugin out of it?
-
Will this script work with the built in pushover notifications enabled or do I need to still use SMTP?
-
@raidflex Not the original one, but here's a quick modified version that should work, I haven't tested it so please give it a try.
-
@luckman212 said in Auto update check, checks for updates to base system + packages and sends email alerts:
@raidflex Not the original one, but here's a quick modified version that should work, I haven't tested it so please give it a try.
Looks to be working properly, thank you for the updated script!
-
 G Gertjan referenced this topic on
G Gertjan referenced this topic on
-
 G Gertjan referenced this topic on
G Gertjan referenced this topic on
-
I love this script but I modified it ever so slightly to notify all configured methods setup in pfSense. If you find the line "notify_via_smtp($msg);" and replace it with "notify_all_remote($msg);" it will send out notifications to ALL configured methods. I've tested this and it works well.
Thanks for all the hardwork!
-
-
 G Gertjan referenced this topic on
G Gertjan referenced this topic on
-
 L luckman212 referenced this topic on
L luckman212 referenced this topic on
-
 L luckman212 referenced this topic on
L luckman212 referenced this topic on
-
 F fireodo referenced this topic on
F fireodo referenced this topic on
-
K khorton referenced this topic on
-
Will this get wiped out from /root/ when a system update is installed?
-
Fast answer :
Yes.
No.
Maybe.Fill in the condition that will apply in the future' and then one of the 3 answers will be valid.
I'll explain : when you upgrade to "MFS" (Marvelous File System, the next file system version that will be sued after the current ZFS) then the drive partitions will get reset : that's a total content loss.
And when you drive dies : that's a Yes.An usual (up until now) GUI or console upgrade/update : That's a No.
(IMHO : I will never presume this No for granted)Maybe : Netgate can decide that /root/ will be cleaned out in the future. Call them for more precise answers.
But the question was wrong ^^ Nothing lasts forever.
So, all that counts is : how to get back to a known working situation in case of emergency ?Easy.
Install the pfSense Notes package.
It's identical to the Notes app in your phone.Copy paste in there the source of the script.
Copy also the setting for the cron package (and thus the reminder that cron package needs to be installed also).
A link to this forum post so you can find the online "manual" right away, if needed.Btw : keep on using Notes for any setting changes that you might want to remember after xx days/months/years.
Now your set up for pretty any situation

Or use the Filer package. never used that one myself, but you can make backups with that package.
-
 G Gertjan referenced this topic on
G Gertjan referenced this topic on