NetGear(s) in AP Mode will not communicate on different LANs (Resolved)
-
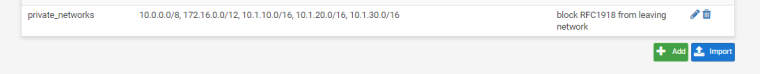
Navigate to Firewall > Aliases:
Create an alias for the RFC1918 network ranges. Call it private_networks and include the following ranges:- 10.0.0.0/8
- 172.16.0.0/12
- 192.168.0.0/16
-Rico
-
Hello Rico,
Thank you for the instructions, I did make a small change due to my LANs IP addresses. correct?
Internet works on LAN2 however still not working on LAN1 VPN internet?
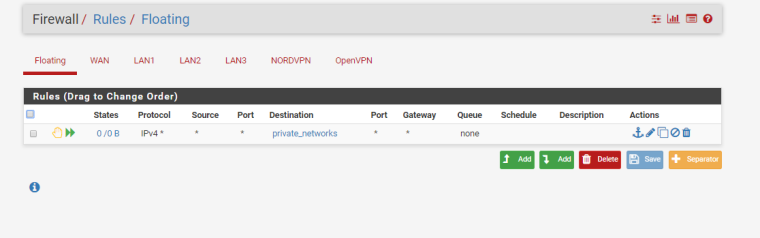
-
Got the VPN internet back on LAN1 by adding to NAT? Does this look correct?
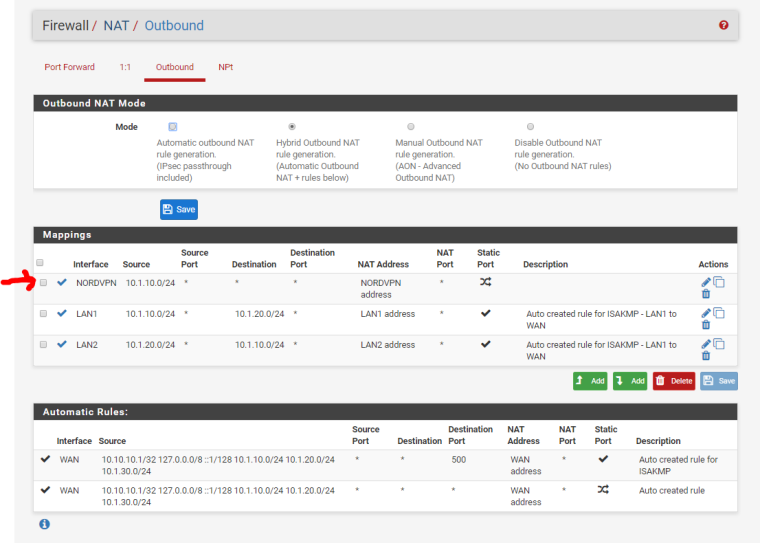
-
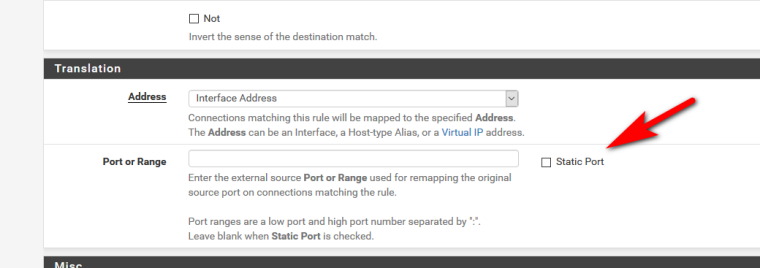
Why did you check static port on the LAN1 and LAN2 NAT rules. Nobody told you to do that.
-
Hello Derelict,
pfsense defaulted to static. LOL now it's corrected.
-
And does it work? Sniff on lan2 interface when trying to talk to lan2 AP from lan 1... Is the source IP your Lan2 interface IP.. Does the AP answer?
If works really no reason to sniff - but if not working they validate that pfsense is sending with source IP changed..
And NO pfsense does not default to static
-
The only way I can see it behaving like you thought static port was the default is if you used the copy icon on one of the existing static port NAT rules for ISAKMP. Which looks to be the case baseed on the rule description. :)
-
John,
Still not working? What do you mean to sniff?
Correct, I copied the rule and it was checked. Sorry for the false information, thanks for the correction.
-
@z71prix So you are trying to connect from a host on LAN2 to an AP on LAN1 (10.1.10.104).
What are the firewall rules on the LAN2 interface?
Can you ping the AP instead of trying to connect to it?
-
Derelict,
I'm on LAN1 now and pinged router AP on LAN2 ok, however cannot connect on web interface still.
Rules on LAN2
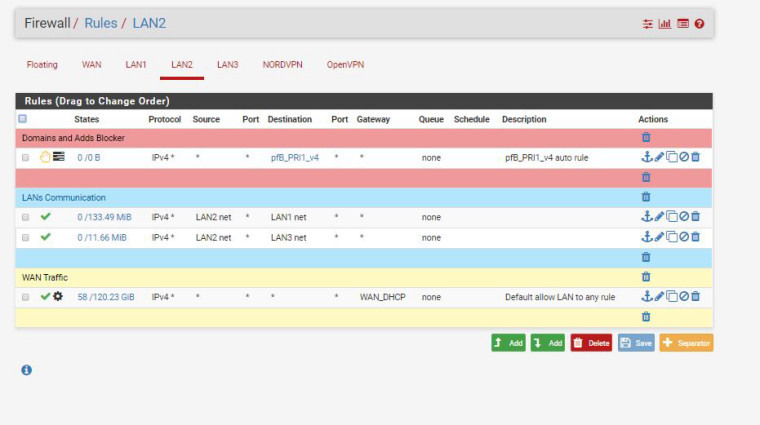
Rules on LAN1
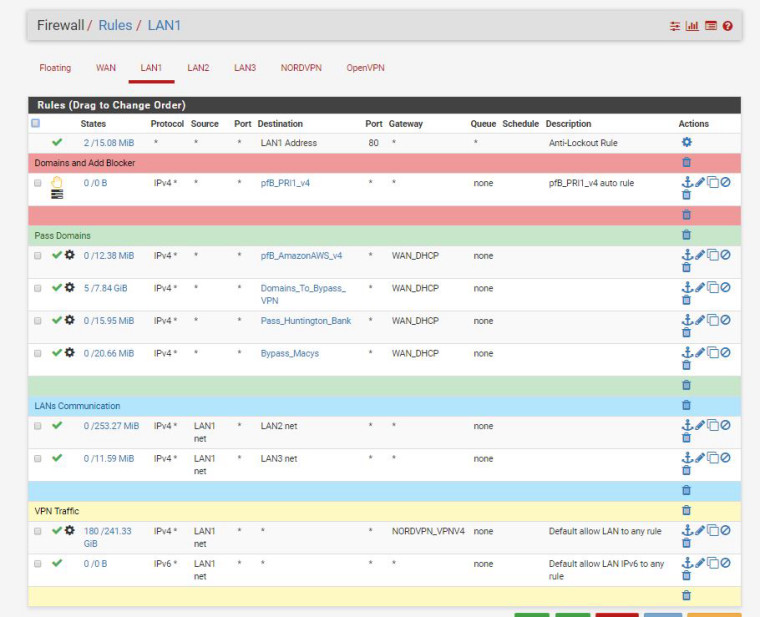
thank you -
Don't ping from the firewall, ping from the same host you are trying to connect from.
Please stick with ONE and ONLY ONE test scenario. Bouncing between connecting to 10.1.10.104 then 10.1.20.115 only confuses the troubleshooting steps. Fix the first and you'll probably fix both.
Diagnostics > Packet Capture
Interface: LAN2
Host: 10.1.10.104
Packets: 10000
Level of Detail: Full
Start
ping from the host you are trying to connect from. Windows default of a 4 count should be fine.
Try to connect to the web interface. Let if fail.
Stop the Capture
Copy/paste what is there here.Then:
Diagnostics > Packet Capture
Interface: LAN1
Host: 10.1.10.104
Packets: 10000
Level of Detail: Full
Start
ping from the host you are trying to connect from. Windows default of a 4 count should be fine.
Try to connect to the web interface Let it fail.
Stop the Capture
Copy/paste what is there here. -
Ok, I'm currently on LAN1 trying to connect to AP on LAN2 IP 10.1.20.115
Here's the results:
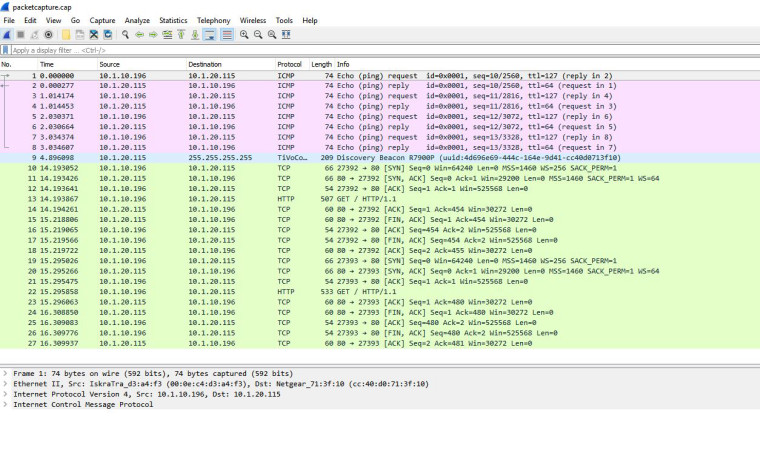
-
I didn't ask for you to post wireshark screen shots. I asked that you copy paste what is in the packet capture on the Diagnostics > Packet Capture screen.
If you want to upload the pcaps so we can bring them into wireshark, you can do that too. Need BOTH pcaps on BOTH interfaces.
What I see there, however, is the AP rejecting the HTTP/1.1 GET for
/- it returns nothing and disconnects the browser session. The FIN is sourced from the AP at 10.1.20.115. -
Derelict,
Sorry about that I downloaded the file. Here's exactly what you wanted following your instructions. (I'm going to take a break and get dinner) Look forward to troubleshooting further in a couple of hours. Thank you so much for helping.
Diagnostics > Packet Capture Interface: LAN2
Nothing CapturedDiagnostics > Packet Capture Interface: LAN1
16:21:26.109729 2c:30:33:51:a0:5e > 00:0e:c4:d3:a4:f2, ethertype IPv4 (0x0800), length 590: (tos 0x0, ttl 64, id 32744, offset 0, flags [DF], proto UDP (17), length 576)
10.1.10.104.68 > 10.1.10.1.67: [udp sum ok] BOOTP/DHCP, Request from 2c:30:33:51:a0:5e, length 548, xid 0xc2e4a653, Flags [none] (0x0000)
Client-IP 10.1.10.104
Client-Ethernet-Address 2c:30:33:51:a0:5e
Vendor-rfc1048 Extensions
Magic Cookie 0x63825363
DHCP-Message Option 53, length 1: Request
Client-ID Option 61, length 7: ether 2c:30:33:51:a0:5e
Hostname Option 12, length 5: "R8500"
Vendor-Class Option 60, length 11: "udhcp 0.9.8"
Parameter-Request Option 55, length 11:
Subnet-Mask, Default-Gateway, Domain-Name-Server, Hostname
Domain-Name, BR, Static-Route, Netbios-Name-Server
Classless-Static-Route, Classless-Static-Route-Microsoft, Option 212
16:21:26.110790 00:0e:c4:d3:a4:f2 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.10.104 tell 10.1.10.1, length 28
16:21:26.110957 2c:30:33:51:a0:5e > 00:0e:c4:d3:a4:f2, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Reply 10.1.10.104 is-at 2c:30:33:51:a0:5e, length 46
16:21:26.110973 00:0e:c4:d3:a4:f2 > 2c:30:33:51:a0:5e, ethertype IPv4 (0x0800), length 342: (tos 0x0, ttl 64, id 18032, offset 0, flags [none], proto UDP (17), length 328)
10.1.10.1.67 > 10.1.10.104.68: [bad udp cksum 0x29b0 -> 0xf76c!] BOOTP/DHCP, Reply, length 300, xid 0xc2e4a653, Flags [none] (0x0000)
Client-IP 10.1.10.104
Your-IP 10.1.10.104
Client-Ethernet-Address 2c:30:33:51:a0:5e
Vendor-rfc1048 Extensions
Magic Cookie 0x63825363
DHCP-Message Option 53, length 1: ACK
Server-ID Option 54, length 4: 10.1.10.1
Lease-Time Option 51, length 4: 7200
Subnet-Mask Option 1, length 4: 255.255.255.0
Default-Gateway Option 3, length 4: 10.1.10.1
Domain-Name-Server Option 6, length 4: 10.1.10.1
Domain-Name Option 15, length 11: "localdomain"
16:21:26.111165 2c:30:33:51:a0:5e > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.10.104 tell 10.1.10.104, length 46
16:21:28.102311 2c:30:33:51:a0:5e > 00:0e:c4:d3:a4:f2, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 32943, offset 0, flags [DF], proto UDP (17), length 64)
10.1.10.104.35443 > 10.1.10.1.53: [udp sum ok] 2+ A? time-a.netgear.com. (36)
16:21:30.719628 00:0e:c4:d3:a4:f2 > 2c:30:33:51:a0:5e, ethertype IPv4 (0x0800), length 94: (tos 0x0, ttl 64, id 50436, offset 0, flags [none], proto UDP (17), length 80)
10.1.10.1.53 > 10.1.10.104.35443: [bad udp cksum 0x28b8 -> 0x5013!] 2 q: A? time-a.netgear.com. 1/0/0 time-a.netgear.com. A 206.16.42.194 (52)
16:21:30.764214 2c:30:33:51:a0:5e > 00:0e:c4:d3:a4:f2, ethertype IPv4 (0x0800), length 78: (tos 0x0, ttl 64, id 33209, offset 0, flags [DF], proto UDP (17), length 64)
10.1.10.104.50204 > 10.1.10.1.53: [udp sum ok] 2+ A? time-a.netgear.com. (36)
16:21:30.764413 00:0e:c4:d3:a4:f2 > 2c:30:33:51:a0:5e, ethertype IPv4 (0x0800), length 94: (tos 0x0, ttl 64, id 33976, offset 0, flags [none], proto UDP (17), length 80)
10.1.10.1.53 > 10.1.10.104.50204: [bad udp cksum 0x28b8 -> 0x166a!] 2 q: A? time-a.netgear.com. 1/0/0 time-a.netgear.com. A 206.16.42.194 (52)
16:21:30.764668 2c:30:33:51:a0:5e > 00:0e:c4:d3:a4:f2, ethertype IPv4 (0x0800), length 90: (tos 0x0, ttl 64, id 33209, offset 0, flags [DF], proto UDP (17), length 76)
10.1.10.104.123 > 206.16.42.194.123: [udp sum ok] NTPv3, length 48
Client, Leap indicator: (0), Stratum 0 (unspecified), poll 4 (16s), precision -6
Root Delay: 1.000000, Root dispersion: 1.000000, Reference-ID: (unspec)
Reference Timestamp: 0.000000000
Originator Timestamp: 0.000000000
Receive Timestamp: 0.000000000
Transmit Timestamp: 3757526490.642349998 (2019/01/26 16:21:30)
Originator - Receive Timestamp: 0.000000000
Originator - Transmit Timestamp: 3757526490.642349998 (2019/01/26 16:21:30)
16:21:30.836666 00:0e:c4:d3:a4:f2 > 2c:30:33:51:a0:5e, ethertype IPv4 (0x0800), length 90: (tos 0x48, ttl 46, id 0, offset 0, flags [DF], proto UDP (17), length 76)
206.16.42.194.123 > 10.1.10.104.123: [udp sum ok] NTPv3, length 48
Server, Leap indicator: (0), Stratum 1 (primary reference), poll 4 (16s), precision -18
Root Delay: 0.000000, Root dispersion: 0.000991, Reference-ID: GPS^@
Reference Timestamp: 3757526490.402142892 (2019/01/26 16:21:30)
Originator Timestamp: 3757526490.642349998 (2019/01/26 16:21:30)
Receive Timestamp: 3757526490.795658616 (2019/01/26 16:21:30)
Transmit Timestamp: 3757526490.795771112 (2019/01/26 16:21:30)
Originator - Receive Timestamp: +0.153308618
Originator - Transmit Timestamp: +0.153421114
16:21:33.107942 2c:30:33:51:a0:5e > 00:0e:c4:d3:a4:f2, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.10.1 tell 10.1.10.104, length 46
16:21:33.107974 00:0e:c4:d3:a4:f2 > 2c:30:33:51:a0:5e, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Reply 10.1.10.1 is-at 00:0e:c4:d3:a4:f2, length 28
16:21:47.854289 e4:6f:13:33:ca:5e > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.10.104 tell 1.1.1.1, length 46
16:21:53.992774 2c:30:33:51:a0:5e > ff:ff:ff:ff:ff:ff, ethertype IPv4 (0x0800), length 208: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto UDP (17), length 194)
10.1.10.104.2190 > 10.1.10.255.2190: [udp sum ok] UDP, length 166
16:21:59.858631 2c:30:33:51:a0:5e > 01:00:5e:7f:ff:fa, ethertype IPv4 (0x0800), length 60: (tos 0xc0, ttl 1, id 0, offset 0, flags [DF], proto IGMP (2), length 32, options (RA))
10.1.10.104 > 239.255.255.250: igmp v2 report 239.255.255.250
16:22:03.281186 2c:30:33:51:a0:5e > 00:0e:c4:d3:a4:f2, ethertype IPv4 (0x0800), length 75: (tos 0x0, ttl 64, id 36461, offset 0, flags [DF], proto UDP (17), length 61)
10.1.10.104.58974 > 10.1.10.1.53: [udp sum ok] 2+ A? www.netgear.com. (33)
16:22:03.342427 00:0e:c4:d3:a4:f2 > 2c:30:33:51:a0:5e, ethertype IPv4 (0x0800), length 182: (tos 0x0, ttl 64, id 32580, offset 0, flags [none], proto UDP (17), length 168)
10.1.10.1.53 > 10.1.10.104.58974: [bad udp cksum 0x2910 -> 0x674e!] 2 q: A? www.netgear.com. 5/0/0 www.netgear.com. CNAME d3jdtixm7cvu7y.cloudfront.net., d3jdtixm7cvu7y.cloudfront.net. A 13.249.142.61, d3jdtixm7cvu7y.cloudfront.net. A 13.249.142.101, d3jdtixm7cvu7y.cloudfront.net. A 13.249.142.6, d3jdtixm7cvu7y.cloudfront.net. A 13.249.142.27 (140)
16:22:03.342909 2c:30:33:51:a0:5e > 00:0e:c4:d3:a4:f2, ethertype IPv4 (0x0800), length 98: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto ICMP (1), length 84)
10.1.10.104 > 13.249.142.61: ICMP echo request, id 5157, seq 0, length 64
16:22:03.360447 00:0e:c4:d3:a4:f2 > 2c:30:33:51:a0:5e, ethertype IPv4 (0x0800), length 98: (tos 0x28, ttl 243, id 12428, offset 0, flags [none], proto ICMP (1), length 84)
13.249.142.61 > 10.1.10.104: ICMP echo reply, id 5157, seq 0, length 64
16:22:03.592472 2c:30:33:51:a0:5e > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.10.103 tell 10.1.10.104, length 46
16:22:03.592654 2c:30:33:51:a0:5e > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.10.200 tell 10.1.10.104, length 46
16:22:03.592660 2c:30:33:51:a0:5e > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.10.1 tell 10.1.10.104, length 46
16:22:03.592667 00:0e:c4:d3:a4:f2 > 2c:30:33:51:a0:5e, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Reply 10.1.10.1 is-at 00:0e:c4:d3:a4:f2, length 28
16:22:03.592670 2c:30:33:51:a0:5e > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.10.196 tell 10.1.10.104, length 46
16:22:03.592674 2c:30:33:51:a0:5e > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.10.139 tell 10.1.10.104, length 46
16:22:03.592713 2c:30:33:51:a0:5e > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.10.109 tell 10.1.10.104, length 46
16:22:03.592734 2c:30:33:51:a0:5e > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.10.105 tell 10.1.10.104, length 46
16:22:03.592793 2c:30:33:51:a0:5e > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.10.150 tell 10.1.10.104, length 46
16:22:03.592826 2c:30:33:51:a0:5e > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.10.106 tell 10.1.10.104, length 46
16:22:03.592856 2c:30:33:51:a0:5e > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.10.152 tell 10.1.10.104, length 46
16:22:03.592887 2c:30:33:51:a0:5e > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.10.198 tell 10.1.10.104, length 46
16:22:04.148790 2c:30:33:51:a0:5e > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.10.103 tell 10.1.10.104, length 46
16:22:04.148818 2c:30:33:51:a0:5e > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.10.200 tell 10.1.10.104, length 46
16:22:04.148858 2c:30:33:51:a0:5e > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.10.1 tell 10.1.10.104, length 46
16:22:04.148869 00:0e:c4:d3:a4:f2 > 2c:30:33:51:a0:5e, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Reply 10.1.10.1 is-at 00:0e:c4:d3:a4:f2, length 28
16:22:04.148885 2c:30:33:51:a0:5e > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.10.196 tell 10.1.10.104, length 46
16:22:04.148915 2c:30:33:51:a0:5e > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.10.139 tell 10.1.10.104, length 46
16:22:04.149008 2c:30:33:51:a0:5e > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.10.109 tell 10.1.10.104, length 46
16:22:04.149042 2c:30:33:51:a0:5e > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.10.105 tell 10.1.10.104, length 46
16:22:04.149083 2c:30:33:51:a0:5e > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.10.150 tell 10.1.10.104, length 46
16:22:04.149134 2c:30:33:51:a0:5e > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.10.106 tell 10.1.10.104, length 46
16:22:04.149165 2c:30:33:51:a0:5e > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.10.152 tell 10.1.10.104, length 46
16:22:04.149196 2c:30:33:51:a0:5e > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.10.198 tell 10.1.10.104, length 46
16:22:04.678788 2c:30:33:51:a0:5e > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.10.103 tell 10.1.10.104, length 46
16:22:04.678831 2c:30:33:51:a0:5e > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.10.200 tell 10.1.10.104, length 46
16:22:04.678854 2c:30:33:51:a0:5e > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.10.1 tell 10.1.10.104, length 46
16:22:04.678860 00:0e:c4:d3:a4:f2 > 2c:30:33:51:a0:5e, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Reply 10.1.10.1 is-at 00:0e:c4:d3:a4:f2, length 28
16:22:04.678887 2c:30:33:51:a0:5e > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.10.196 tell 10.1.10.104, length 46
16:22:04.678941 2c:30:33:51:a0:5e > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.10.139 tell 10.1.10.104, length 46
16:22:04.679035 2c:30:33:51:a0:5e > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.10.109 tell 10.1.10.104, length 46
16:22:04.679068 2c:30:33:51:a0:5e > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.10.105 tell 10.1.10.104, length 46
16:22:04.679098 2c:30:33:51:a0:5e > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.10.150 tell 10.1.10.104, length 46
16:22:04.679125 2c:30:33:51:a0:5e > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.10.106 tell 10.1.10.104, length 46
16:22:04.679155 2c:30:33:51:a0:5e > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.10.152 tell 10.1.10.104, length 46
16:22:04.679186 2c:30:33:51:a0:5e > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.10.198 tell 10.1.10.104, length 46
16:22:05.236287 2c:30:33:51:a0:5e > 00:0e:c4:d3:a4:f2, ethertype IPv4 (0x0800), length 92: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto UDP (17), length 78)
10.1.10.104.40394 > 10.1.10.1.137: [udp sum ok]NBT UDP PACKET(137): QUERY; REQUEST; BROADCAST
TrnID=0x1
OpCode=0
NmFlags=0x1
Rcode=0
QueryCount=1
AnswerCount=0
AuthorityCount=0
AddressRecCount=0
QuestionRecords:
Name=* NameType=0x00 (Workstation)
QuestionType=0x21
QuestionClass=0x116:22:05.238774 2c:30:33:51:a0:5e > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.10.109 tell 10.1.10.104, length 46
16:22:05.238784 2c:30:33:51:a0:5e > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.10.105 tell 10.1.10.104, length 46
16:22:05.238789 2c:30:33:51:a0:5e > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.10.106 tell 10.1.10.104, length 46
16:22:05.238809 2c:30:33:51:a0:5e > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.10.198 tell 10.1.10.104, length 46 -
That doesn't look like you performed any of the ping or web connection steps. You also continue to bounce between testing 10.1.10.104 and 10.1.20.115. It's pretty frustrating. Please pick one and stick with it.
-
Here's the results of trying to connect to AP 10.1.20.115 on LAN1
Diagnostics > Packet Capture Interface: LAN2
16:28:54.395188 00:0e:c4:d3:a4:f3 > cc:40:d0:71:3f:10, ethertype IPv4 (0x0800), length 74: (tos 0x0, ttl 127, id 10796, offset 0, flags [none], proto ICMP (1), length 60)
10.1.10.196 > 10.1.20.115: ICMP echo request, id 1, seq 22, length 40
16:28:54.395430 cc:40:d0:71:3f:10 > 00:0e:c4:d3:a4:f3, ethertype IPv4 (0x0800), length 74: (tos 0x0, ttl 64, id 10374, offset 0, flags [none], proto ICMP (1), length 60)
10.1.20.115 > 10.1.10.196: ICMP echo reply, id 1, seq 22, length 40
16:28:55.398124 00:0e:c4:d3:a4:f3 > cc:40:d0:71:3f:10, ethertype IPv4 (0x0800), length 74: (tos 0x0, ttl 127, id 10797, offset 0, flags [none], proto ICMP (1), length 60)
10.1.10.196 > 10.1.20.115: ICMP echo request, id 1, seq 23, length 40
16:28:55.398418 cc:40:d0:71:3f:10 > 00:0e:c4:d3:a4:f3, ethertype IPv4 (0x0800), length 74: (tos 0x0, ttl 64, id 10431, offset 0, flags [none], proto ICMP (1), length 60)
10.1.20.115 > 10.1.10.196: ICMP echo reply, id 1, seq 23, length 40
16:28:56.402819 00:0e:c4:d3:a4:f3 > cc:40:d0:71:3f:10, ethertype IPv4 (0x0800), length 74: (tos 0x0, ttl 127, id 10798, offset 0, flags [none], proto ICMP (1), length 60)
10.1.10.196 > 10.1.20.115: ICMP echo request, id 1, seq 24, length 40
16:28:56.403066 cc:40:d0:71:3f:10 > 00:0e:c4:d3:a4:f3, ethertype IPv4 (0x0800), length 74: (tos 0x0, ttl 64, id 10458, offset 0, flags [none], proto ICMP (1), length 60)
10.1.20.115 > 10.1.10.196: ICMP echo reply, id 1, seq 24, length 40
16:28:57.409156 00:0e:c4:d3:a4:f3 > cc:40:d0:71:3f:10, ethertype IPv4 (0x0800), length 74: (tos 0x0, ttl 127, id 10799, offset 0, flags [none], proto ICMP (1), length 60)
10.1.10.196 > 10.1.20.115: ICMP echo request, id 1, seq 25, length 40
16:28:57.409452 cc:40:d0:71:3f:10 > 00:0e:c4:d3:a4:f3, ethertype IPv4 (0x0800), length 74: (tos 0x0, ttl 64, id 10491, offset 0, flags [none], proto ICMP (1), length 60)
10.1.20.115 > 10.1.10.196: ICMP echo reply, id 1, seq 25, length 40
16:28:57.515390 cc:40:d0:71:3f:10 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.20.108 tell 10.1.20.115, length 46
16:28:57.886016 cc:40:d0:71:3f:10 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.20.107 tell 10.1.20.115, length 46
16:28:58.295232 cc:40:d0:71:3f:10 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.20.103 tell 10.1.20.115, length 46
16:28:58.735272 cc:40:d0:71:3f:10 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.20.112 tell 10.1.20.115, length 46
16:28:59.115211 cc:40:d0:71:3f:10 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.20.118 tell 10.1.20.115, length 46
16:28:59.515223 cc:40:d0:71:3f:10 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.20.114 tell 10.1.20.115, length 46
16:28:59.935259 cc:40:d0:71:3f:10 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.20.147 tell 10.1.20.115, length 46
16:29:00.355236 cc:40:d0:71:3f:10 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.20.148 tell 10.1.20.115, length 46
16:29:00.777013 cc:40:d0:71:3f:10 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.20.149 tell 10.1.20.115, length 46
16:29:01.028635 00:0e:c4:d3:a4:f3 > cc:40:d0:71:3f:10, ethertype IPv4 (0x0800), length 66: (tos 0x0, ttl 127, id 10800, offset 0, flags [DF], proto TCP (6), length 52)
10.1.10.196.28951 > 10.1.20.115.80: Flags [S], cksum 0x9aa3 (correct), seq 675810452, win 64240, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
16:29:01.028949 cc:40:d0:71:3f:10 > 00:0e:c4:d3:a4:f3, ethertype IPv4 (0x0800), length 66: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 52)
10.1.20.115.80 > 10.1.10.196.28951: Flags [S.], cksum 0xb606 (correct), seq 3042359319, ack 675810453, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 6], length 0
16:29:01.029158 00:0e:c4:d3:a4:f3 > cc:40:d0:71:3f:10, ethertype IPv4 (0x0800), length 54: (tos 0x0, ttl 127, id 10801, offset 0, flags [DF], proto TCP (6), length 40)
10.1.10.196.28951 > 10.1.20.115.80: Flags [.], cksum 0x60e3 (correct), seq 1, ack 1, win 2053, length 0
16:29:01.029439 00:0e:c4:d3:a4:f3 > cc:40:d0:71:3f:10, ethertype IPv4 (0x0800), length 507: (tos 0x0, ttl 127, id 10802, offset 0, flags [DF], proto TCP (6), length 493)
10.1.10.196.28951 > 10.1.20.115.80: Flags [P.], cksum 0xe98d (correct), seq 1:454, ack 1, win 2053, length 453: HTTP, length: 453
GET / HTTP/1.1
Host: 10.1.20.115
Connection: keep-alive
Authorization: Basic YWRtaW46RGF2aWQ2ODAy
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/71.0.3578.98 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,/;q=0.8
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: XSRF_TOKEN=126778892816:29:01.029738 cc:40:d0:71:3f:10 > 00:0e:c4:d3:a4:f3, ethertype IPv4 (0x0800), length 60: (tos 0x0, ttl 64, id 51818, offset 0, flags [DF], proto TCP (6), length 40)
10.1.20.115.80 > 10.1.10.196.28951: Flags [.], cksum 0x654a (correct), seq 1, ack 454, win 473, length 0
16:29:01.176917 cc:40:d0:71:3f:10 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.20.105 tell 10.1.20.115, length 46
16:29:01.586282 cc:40:d0:71:3f:10 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.20.124 tell 10.1.20.115, length 46
16:29:01.685219 cc:40:d0:71:3f:10 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.20.153 tell 10.1.20.115, length 46
16:29:01.855223 cc:40:d0:71:3f:10 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.20.157 tell 10.1.20.115, length 46
16:29:02.045439 cc:40:d0:71:3f:10 > 00:0e:c4:d3:a4:f3, ethertype IPv4 (0x0800), length 60: (tos 0x0, ttl 64, id 51819, offset 0, flags [DF], proto TCP (6), length 40)
10.1.20.115.80 > 10.1.10.196.28951: Flags [F.], cksum 0x6549 (correct), seq 1, ack 454, win 473, length 0
16:29:02.045661 00:0e:c4:d3:a4:f3 > cc:40:d0:71:3f:10, ethertype IPv4 (0x0800), length 54: (tos 0x0, ttl 127, id 10803, offset 0, flags [DF], proto TCP (6), length 40)
10.1.10.196.28951 > 10.1.20.115.80: Flags [.], cksum 0x5f1d (correct), seq 454, ack 2, win 2053, length 0
16:29:02.046125 00:0e:c4:d3:a4:f3 > cc:40:d0:71:3f:10, ethertype IPv4 (0x0800), length 54: (tos 0x0, ttl 127, id 10804, offset 0, flags [DF], proto TCP (6), length 40)
10.1.10.196.28951 > 10.1.20.115.80: Flags [F.], cksum 0x5f1c (correct), seq 454, ack 2, win 2053, length 0
16:29:02.046292 cc:40:d0:71:3f:10 > 00:0e:c4:d3:a4:f3, ethertype IPv4 (0x0800), length 60: (tos 0x0, ttl 64, id 49331, offset 0, flags [DF], proto TCP (6), length 40)
10.1.20.115.80 > 10.1.10.196.28951: Flags [.], cksum 0x6548 (correct), seq 2, ack 455, win 473, length 0
16:29:02.187260 00:0e:c4:d3:a4:f3 > cc:40:d0:71:3f:10, ethertype IPv4 (0x0800), length 66: (tos 0x0, ttl 127, id 10805, offset 0, flags [DF], proto TCP (6), length 52)
10.1.10.196.28954 > 10.1.20.115.80: Flags [S], cksum 0x4132 (correct), seq 1709779041, win 64240, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
16:29:02.187508 cc:40:d0:71:3f:10 > 00:0e:c4:d3:a4:f3, ethertype IPv4 (0x0800), length 66: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 52)
10.1.20.115.80 > 10.1.10.196.28954: Flags [S.], cksum 0x9448 (correct), seq 666766845, ack 1709779042, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 6], length 0
16:29:02.187720 00:0e:c4:d3:a4:f3 > cc:40:d0:71:3f:10, ethertype IPv4 (0x0800), length 54: (tos 0x0, ttl 127, id 10806, offset 0, flags [DF], proto TCP (6), length 40)
10.1.10.196.28954 > 10.1.20.115.80: Flags [.], cksum 0x3f25 (correct), seq 1, ack 1, win 2053, length 0
16:29:02.188278 00:0e:c4:d3:a4:f3 > cc:40:d0:71:3f:10, ethertype IPv4 (0x0800), length 533: (tos 0x0, ttl 127, id 10807, offset 0, flags [DF], proto TCP (6), length 519)
10.1.10.196.28954 > 10.1.20.115.80: Flags [P.], cksum 0x5cb8 (correct), seq 1:480, ack 1, win 2053, length 479: HTTP, length: 479
GET / HTTP/1.1
Host: 10.1.20.115
Connection: keep-alive
Cache-Control: max-age=0
Authorization: Basic YWRtaW46RGF2aWQ2ODAy
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/71.0.3578.98 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,/;q=0.8
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: XSRF_TOKEN=126778892816:29:02.188481 cc:40:d0:71:3f:10 > 00:0e:c4:d3:a4:f3, ethertype IPv4 (0x0800), length 60: (tos 0x0, ttl 64, id 32536, offset 0, flags [DF], proto TCP (6), length 40)
10.1.20.115.80 > 10.1.10.196.28954: Flags [.], cksum 0x4372 (correct), seq 1, ack 480, win 473, length 0
16:29:02.535325 cc:40:d0:71:3f:10 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.20.132 tell 10.1.20.115, length 46
16:29:03.015212 cc:40:d0:71:3f:10 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.20.123 tell 10.1.20.115, length 46
16:29:03.205472 cc:40:d0:71:3f:10 > 00:0e:c4:d3:a4:f3, ethertype IPv4 (0x0800), length 60: (tos 0x0, ttl 64, id 32537, offset 0, flags [DF], proto TCP (6), length 40)
10.1.20.115.80 > 10.1.10.196.28954: Flags [F.], cksum 0x4371 (correct), seq 1, ack 480, win 473, length 0
16:29:03.205720 00:0e:c4:d3:a4:f3 > cc:40:d0:71:3f:10, ethertype IPv4 (0x0800), length 54: (tos 0x0, ttl 127, id 10808, offset 0, flags [DF], proto TCP (6), length 40)
10.1.10.196.28954 > 10.1.20.115.80: Flags [.], cksum 0x3d45 (correct), seq 480, ack 2, win 2053, length 0
16:29:03.206331 00:0e:c4:d3:a4:f3 > cc:40:d0:71:3f:10, ethertype IPv4 (0x0800), length 54: (tos 0x0, ttl 127, id 10809, offset 0, flags [DF], proto TCP (6), length 40)
10.1.10.196.28954 > 10.1.20.115.80: Flags [F.], cksum 0x3d44 (correct), seq 480, ack 2, win 2053, length 0
16:29:03.206501 cc:40:d0:71:3f:10 > 00:0e:c4:d3:a4:f3, ethertype IPv4 (0x0800), length 60: (tos 0x0, ttl 64, id 49332, offset 0, flags [DF], proto TCP (6), length 40)
10.1.20.115.80 > 10.1.10.196.28954: Flags [.], cksum 0x4370 (correct), seq 2, ack 481, win 473, length 0
16:29:04.025318 cc:40:d0:71:3f:10 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.20.123 tell 10.1.20.115, length 46
16:29:05.035329 cc:40:d0:71:3f:10 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.20.123 tell 10.1.20.115, length 46
16:29:06.105234 cc:40:d0:71:3f:10 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.20.120 tell 10.1.20.115, length 46
16:29:06.166038 cc:40:d0:71:3f:10 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.20.154 tell 10.1.20.115, length 46
16:29:06.486444 cc:40:d0:71:3f:10 > ff:ff:ff:ff:ff:ff, ethertype ARP (0x0806), length 60: Ethernet (len 6), IPv4 (len 4), Request who-has 10.1.20.1 tell 10.1.20.115, length 46
16:29:06.486458 00:0e:c4:d3:a4:f3 > cc:40:d0:71:3f:10, ethertype ARP (0x0806), length 42: Ethernet (len 6), IPv4 (len 4), Reply 10.1.20.1 is-at 00:0e:c4:d3:a4:f3, length 28
16:29:08.229480 00:0e:c4:d3:a4:f3 > cc:40:d0:71:3f:10, ethertype IPv4 (0x0800), length 66: (tos 0x0, ttl 127, id 10810, offset 0, flags [DF], proto TCP (6), length 52)
10.1.10.196.28963 > 10.1.20.115.80: Flags [S], cksum 0xf6d2 (correct), seq 876061801, win 64240, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
16:29:08.229827 cc:40:d0:71:3f:10 > 00:0e:c4:d3:a4:f3, ethertype IPv4 (0x0800), length 66: (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto TCP (6), length 52)
10.1.20.115.80 > 10.1.10.196.28963: Flags [S.], cksum 0x8765 (correct), seq 1309977130, ack 876061802, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 6], length 0
16:29:08.230064 00:0e:c4:d3:a4:f3 > cc:40:d0:71:3f:10, ethertype IPv4 (0x0800), length 54: (tos 0x0, ttl 127, id 10811, offset 0, flags [DF], proto TCP (6), length 40)
10.1.10.196.28963 > 10.1.20.115.80: Flags [.], cksum 0x3242 (correct), seq 1, ack 1, win 2053, length 0
16:29:08.230948 00:0e:c4:d3:a4:f3 > cc:40:d0:71:3f:10, ethertype IPv4 (0x0800), length 533: (tos 0x0, ttl 127, id 10812, offset 0, flags [DF], proto TCP (6), length 519)
10.1.10.196.28963 > 10.1.20.115.80: Flags [P.], cksum 0x4fd5 (correct), seq 1:480, ack 1, win 2053, length 479: HTTP, length: 479
GET / HTTP/1.1
Host: 10.1.20.115
Connection: keep-alive
Cache-Control: max-age=0
Authorization: Basic YWRtaW46RGF2aWQ2ODAy
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/71.0.3578.98 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,/;q=0.8
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: XSRF_TOKEN=126778892816:29:08.231159 cc:40:d0:71:3f:10 > 00:0e:c4:d3:a4:f3, ethertype IPv4 (0x0800), length 60: (tos 0x0, ttl 64, id 57193, offset 0, flags [DF], proto TCP (6), length 40)
10.1.20.115.80 > 10.1.10.196.28963: Flags [.], cksum 0x368f (correct), seq 1, ack 480, win 473, length 0
16:29:09.245546 cc:40:d0:71:3f:10 > 00:0e:c4:d3:a4:f3, ethertype IPv4 (0x0800), length 60: (tos 0x0, ttl 64, id 57194, offset 0, flags [DF], proto TCP (6), length 40)
10.1.20.115.80 > 10.1.10.196.28963: Flags [F.], cksum 0x368e (correct), seq 1, ack 480, win 473, length 0
16:29:09.245776 00:0e:c4:d3:a4:f3 > cc:40:d0:71:3f:10, ethertype IPv4 (0x0800), length 54: (tos 0x0, ttl 127, id 10813, offset 0, flags [DF], proto TCP (6), length 40)
10.1.10.196.28963 > 10.1.20.115.80: Flags [.], cksum 0x3062 (correct), seq 480, ack 2, win 2053, length 0
16:29:09.246280 00:0e:c4:d3:a4:f3 > cc:40:d0:71:3f:10, ethertype IPv4 (0x0800), length 54: (tos 0x0, ttl 127, id 10814, offset 0, flags [DF], proto TCP (6), length 40)
10.1.10.196.28963 > 10.1.20.115.80: Flags [F.], cksum 0x3061 (correct), seq 480, ack 2, win 2053, length 0
16:29:09.246447 cc:40:d0:71:3f:10 > 00:0e:c4:d3:a4:f3, ethertype IPv4 (0x0800), length 60: (tos 0x0, ttl 64, id 49814, offset 0, flags [DF], proto TCP (6), length 40)
10.1.20.115.80 > 10.1.10.196.28963: Flags [.], cksum 0x368d (correct), seq 2, ack 481, win 473, length 0
16:29:14.755356 cc:40:d0:71:3f:10 > ff:ff:ff:ff:ff:ff, ethertype IPv4 (0x0800), length 209: (tos 0x0, ttl 64, id 54776, offset 0, flags [DF], proto UDP (17), length 195)
10.1.20.115.2190 > 255.255.255.255.2190: [udp sum ok] UDP, length 167Diagnostics > Packet Capture Interface: LAN1
16:31:23.177327 70:85:c2:62:63:f7 > 00:0e:c4:d3:a4:f2, ethertype IPv4 (0x0800), length 74: (tos 0x0, ttl 128, id 10828, offset 0, flags [none], proto ICMP (1), length 60)
10.1.10.196 > 10.1.20.115: ICMP echo request, id 1, seq 26, length 40
16:31:23.177655 00:0e:c4:d3:a4:f2 > 70:85:c2:62:63:f7, ethertype IPv4 (0x0800), length 74: (tos 0x0, ttl 63, id 21417, offset 0, flags [none], proto ICMP (1), length 60)
10.1.20.115 > 10.1.10.196: ICMP echo reply, id 1, seq 26, length 40
16:31:24.189744 70:85:c2:62:63:f7 > 00:0e:c4:d3:a4:f2, ethertype IPv4 (0x0800), length 74: (tos 0x0, ttl 128, id 10829, offset 0, flags [none], proto ICMP (1), length 60)
10.1.10.196 > 10.1.20.115: ICMP echo request, id 1, seq 27, length 40
16:31:24.190103 00:0e:c4:d3:a4:f2 > 70:85:c2:62:63:f7, ethertype IPv4 (0x0800), length 74: (tos 0x0, ttl 63, id 21457, offset 0, flags [none], proto ICMP (1), length 60)
10.1.20.115 > 10.1.10.196: ICMP echo reply, id 1, seq 27, length 40
16:31:25.196619 70:85:c2:62:63:f7 > 00:0e:c4:d3:a4:f2, ethertype IPv4 (0x0800), length 74: (tos 0x0, ttl 128, id 10830, offset 0, flags [none], proto ICMP (1), length 60)
10.1.10.196 > 10.1.20.115: ICMP echo request, id 1, seq 28, length 40
16:31:25.196907 00:0e:c4:d3:a4:f2 > 70:85:c2:62:63:f7, ethertype IPv4 (0x0800), length 74: (tos 0x0, ttl 63, id 21528, offset 0, flags [none], proto ICMP (1), length 60)
10.1.20.115 > 10.1.10.196: ICMP echo reply, id 1, seq 28, length 40
16:31:26.212726 70:85:c2:62:63:f7 > 00:0e:c4:d3:a4:f2, ethertype IPv4 (0x0800), length 74: (tos 0x0, ttl 128, id 10831, offset 0, flags [none], proto ICMP (1), length 60)
10.1.10.196 > 10.1.20.115: ICMP echo request, id 1, seq 29, length 40
16:31:26.213043 00:0e:c4:d3:a4:f2 > 70:85:c2:62:63:f7, ethertype IPv4 (0x0800), length 74: (tos 0x0, ttl 63, id 21573, offset 0, flags [none], proto ICMP (1), length 60)
10.1.20.115 > 10.1.10.196: ICMP echo reply, id 1, seq 29, length 40
16:31:37.525307 70:85:c2:62:63:f7 > 00:0e:c4:d3:a4:f2, ethertype IPv4 (0x0800), length 66: (tos 0x0, ttl 128, id 10832, offset 0, flags [DF], proto TCP (6), length 52)
10.1.10.196.29162 > 10.1.20.115.80: Flags [S], cksum 0xef05 (correct), seq 2404601939, win 64240, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0
16:31:37.525650 00:0e:c4:d3:a4:f2 > 70:85:c2:62:63:f7, ethertype IPv4 (0x0800), length 66: (tos 0x0, ttl 63, id 0, offset 0, flags [DF], proto TCP (6), length 52)
10.1.20.115.80 > 10.1.10.196.29162: Flags [S.], cksum 0x940e (correct), seq 922004692, ack 2404601940, win 29200, options [mss 1460,nop,nop,sackOK,nop,wscale 6], length 0
16:31:37.525796 70:85:c2:62:63:f7 > 00:0e:c4:d3:a4:f2, ethertype IPv4 (0x0800), length 60: (tos 0x0, ttl 128, id 10833, offset 0, flags [DF], proto TCP (6), length 40)
10.1.10.196.29162 > 10.1.20.115.80: Flags [.], cksum 0x3eeb (correct), seq 1, ack 1, win 2053, length 0
16:31:37.526445 70:85:c2:62:63:f7 > 00:0e:c4:d3:a4:f2, ethertype IPv4 (0x0800), length 533: (tos 0x0, ttl 128, id 10834, offset 0, flags [DF], proto TCP (6), length 519)
10.1.10.196.29162 > 10.1.20.115.80: Flags [P.], cksum 0x5c7e (correct), seq 1:480, ack 1, win 2053, length 479: HTTP, length: 479
GET / HTTP/1.1
Host: 10.1.20.115
Connection: keep-alive
Cache-Control: max-age=0
Authorization: Basic YWRtaW46RGF2aWQ2ODAy
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/71.0.3578.98 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,/;q=0.8
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: XSRF_TOKEN=126778892816:31:37.526682 00:0e:c4:d3:a4:f2 > 70:85:c2:62:63:f7, ethertype IPv4 (0x0800), length 54: (tos 0x0, ttl 63, id 833, offset 0, flags [DF], proto TCP (6), length 40)
10.1.20.115.80 > 10.1.10.196.29162: Flags [.], cksum 0x4338 (correct), seq 1, ack 480, win 473, length 0
16:31:38.545853 00:0e:c4:d3:a4:f2 > 70:85:c2:62:63:f7, ethertype IPv4 (0x0800), length 54: (tos 0x0, ttl 63, id 834, offset 0, flags [DF], proto TCP (6), length 40)
10.1.20.115.80 > 10.1.10.196.29162: Flags [F.], cksum 0x4337 (correct), seq 1, ack 480, win 473, length 0
16:31:38.546033 70:85:c2:62:63:f7 > 00:0e:c4:d3:a4:f2, ethertype IPv4 (0x0800), length 60: (tos 0x0, ttl 128, id 10835, offset 0, flags [DF], proto TCP (6), length 40)
10.1.10.196.29162 > 10.1.20.115.80: Flags [.], cksum 0x3d0b (correct), seq 480, ack 2, win 2053, length 0
16:31:38.546507 70:85:c2:62:63:f7 > 00:0e:c4:d3:a4:f2, ethertype IPv4 (0x0800), length 60: (tos 0x0, ttl 128, id 10836, offset 0, flags [DF], proto TCP (6), length 40)
10.1.10.196.29162 > 10.1.20.115.80: Flags [F.], cksum 0x3d0a (correct), seq 480, ack 2, win 2053, length 0
16:31:38.546717 00:0e:c4:d3:a4:f2 > 70:85:c2:62:63:f7, ethertype IPv4 (0x0800), length 54: (tos 0x0, ttl 63, id 53683, offset 0, flags [DF], proto TCP (6), length 40)
10.1.20.115.80 > 10.1.10.196.29162: Flags [.], cksum 0x4336 (correct), seq 2, ack 481, win 473, length 0 -
Your outbound NAT is still incorrect. Traffic going outbound on LAN2 sourced from 10.1.10.0/24 (10.1.10.196 in this example) should be source-translated to the interface address 10.1.20.1. That did not happen there so your Outbound NAT on LAN2 is still wrong.
-
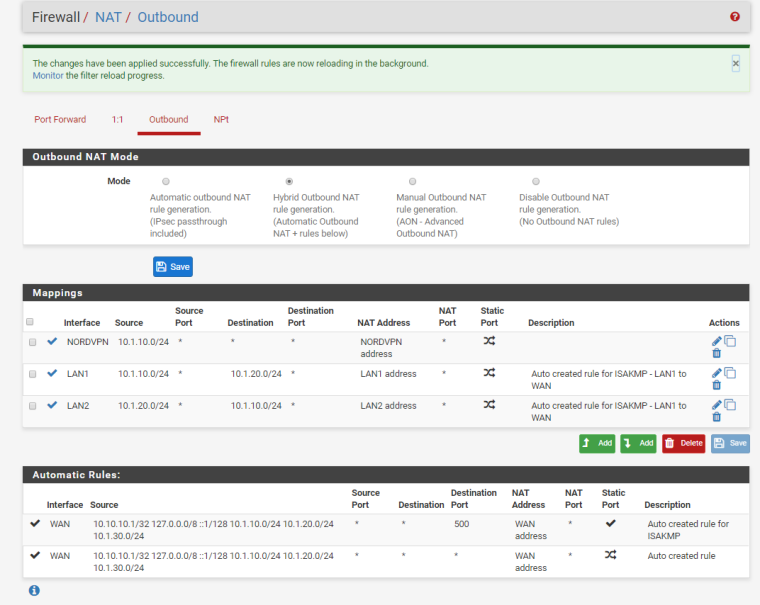
Here's the NAT. Does this look correct?
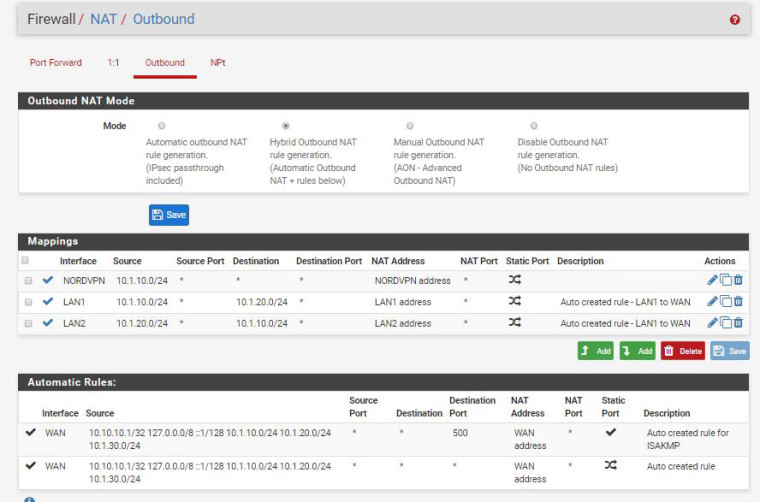
-
No. You have it backwards.
You want to use LAN1 as the source and LAN2 as the destination for the LAN2 rule.
You want to use LAN2 as the source and LAN1 as the destination in the LAN1 rule.
-
That resolved the issue!!! You're awesome!!! Communication works now on both AP(s)
Thank you so much for your help!!
Thank you everyone else as well!!