IPv6 Native with Telstra, Australia
-
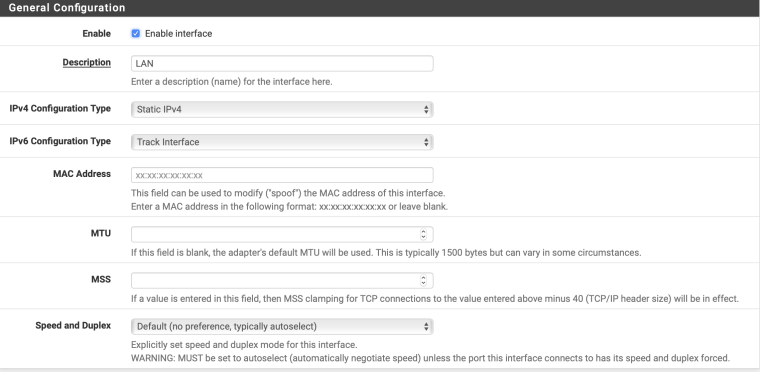
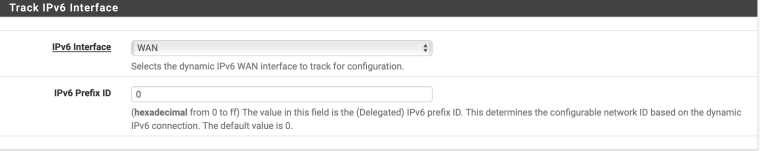
What's with all that advanced configuration? Especially setting LAN as the PD interface. Is that you stabbing in the dark with your fingers crossed?
Feb 26 08:17:55 dhcp6c 79587 reset a timer on igb1, state=INIT, timeo=0, retrans=891 Feb 26 08:17:56 dhcp6c 79587 Sending Solicit Feb 26 08:17:56 dhcp6c 79587 a new XID (781bad) is generated Feb 26 08:17:56 dhcp6c 79587 set client ID (len 14) Feb 26 08:17:56 dhcp6c 79587 set identity association Feb 26 08:17:56 dhcp6c 79587 set elapsed time (len 2) Feb 26 08:17:56 dhcp6c 79587 set option request (len 4) Feb 26 08:17:56 dhcp6c 79587 set IA_PD prefix Feb 26 08:17:56 dhcp6c 79587 set IA_PD Feb 26 08:17:56 dhcp6c 79587 send solicit to ff02::1:2%igb1 Feb 26 08:17:56 dhcp6c 79587 reset a timer on igb1, state=SOLICIT, timeo=0, retrans=1091 Feb 26 08:17:56 dhcp6c 79587 receive advertise from fe80::2e86:d2ff:fe89:2019%igb1 on igb1 Feb 26 08:17:56 dhcp6c 79587 get DHCP option client ID, len 14 Feb 26 08:17:56 dhcp6c 79587 DUID: 00:ff:ee:dd:cc:09:0f:68:00:08:a2:0a:59:41 Feb 26 08:17:56 dhcp6c 79587 get DHCP option server ID, len 14 Feb 26 08:17:56 dhcp6c 79587 DUID: 00:01:00:01:55:f6:d0:f4:f8:bc:12:3e:b6:9c Feb 26 08:17:56 dhcp6c 79587 get DHCP option DNS, len 32 Feb 26 08:17:56 dhcp6c 79587 get DHCP option identity association, len 40 Feb 26 08:17:56 dhcp6c 79587 IA_NA: ID=0, T1=43200, T2=69120 Feb 26 08:17:56 dhcp6c 79587 get DHCP option IA address, len 24 Feb 26 08:17:56 dhcp6c 79587 IA_NA address: 2600:aaaa:bbbb:1c00:4417:7125:99fd:24cb pltime=86400 vltime=86400 Feb 26 08:17:56 dhcp6c 79587 get DHCP option IA_PD, len 41 Feb 26 08:17:56 dhcp6c 79587 IA_PD: ID=0, T1=43200, T2=69120 Feb 26 08:17:56 dhcp6c 79587 get DHCP option IA_PD prefix, len 25 Feb 26 08:17:56 dhcp6c 79587 IA_PD prefix: 2600:aaaa:ccc:ab00::/56 pltime=86400 vltime=86400 Feb 26 08:17:56 dhcp6c 79587 server ID: 00:01:00:01:55:f6:d0:f4:f8:bc:12:3e:b6:9c, pref=-1 Feb 26 08:17:56 dhcp6c 79587 reset timer for igb1 to 0.973168 Feb 26 08:17:57 dhcp6c 79587 picked a server (ID: 00:01:00:01:55:f6:d0:f4:f8:bc:12:3e:b6:9c) Feb 26 08:17:57 dhcp6c 79587 Sending Request Feb 26 08:17:57 dhcp6c 79587 a new XID (804c2e) is generated Feb 26 08:17:57 dhcp6c 79587 set client ID (len 14) Feb 26 08:17:57 dhcp6c 79587 set server ID (len 14) Feb 26 08:17:57 dhcp6c 79587 set IA address Feb 26 08:17:57 dhcp6c 79587 set identity association Feb 26 08:17:57 dhcp6c 79587 set elapsed time (len 2) Feb 26 08:17:57 dhcp6c 79587 set option request (len 4) Feb 26 08:17:57 dhcp6c 79587 set IA_PD prefix Feb 26 08:17:57 dhcp6c 79587 set IA_PD Feb 26 08:17:57 dhcp6c 79587 send request to ff02::1:2%igb1 Feb 26 08:17:57 dhcp6c 79587 reset a timer on igb1, state=REQUEST, timeo=0, retrans=909 Feb 26 08:17:57 dhcp6c 79587 receive reply from fe80::2e86:d2ff:fe89:2019%igb1 on igb1 Feb 26 08:17:57 dhcp6c 79587 get DHCP option client ID, len 14 Feb 26 08:17:57 dhcp6c 79587 DUID: 00:ff:ee:dd:cc:09:0f:68:00:08:a2:0a:59:41 Feb 26 08:17:57 dhcp6c 79587 get DHCP option server ID, len 14 Feb 26 08:17:57 dhcp6c 79587 DUID: 00:01:00:01:55:f6:d0:f4:f8:bc:12:3e:b6:9c Feb 26 08:17:57 dhcp6c 79587 get DHCP option DNS, len 32 Feb 26 08:17:57 dhcp6c 79587 get DHCP option identity association, len 46 Feb 26 08:17:57 dhcp6c 79587 IA_NA: ID=0, T1=43200, T2=69120 Feb 26 08:17:57 dhcp6c 79587 get DHCP option status code, len 2 Feb 26 08:17:57 dhcp6c 79587 status code: success Feb 26 08:17:57 dhcp6c 79587 get DHCP option IA address, len 24 Feb 26 08:17:57 dhcp6c 79587 IA_NA address: 2600:aaaa:bbbb:1c00:4417:7125:99fd:24cb pltime=86400 vltime=86400 Feb 26 08:17:57 dhcp6c 79587 get DHCP option IA_PD, len 47 Feb 26 08:17:57 dhcp6c 79587 IA_PD: ID=0, T1=43200, T2=69120 Feb 26 08:17:57 dhcp6c 79587 get DHCP option status code, len 2 Feb 26 08:17:57 dhcp6c 79587 status code: success Feb 26 08:17:57 dhcp6c 79587 get DHCP option IA_PD prefix, len 25 Feb 26 08:17:57 dhcp6c 79587 IA_PD prefix: 2600:aaaa:ccc:ab00::/56 pltime=86400 vltime=86400 Feb 26 08:17:57 dhcp6c 79587 dhcp6c Received REQUEST Feb 26 08:17:57 dhcp6c 79587 nameserver[0] 2001:578:3f::30 Feb 26 08:17:57 dhcp6c 79587 nameserver[1] 2001:578:3f:1::30 Feb 26 08:17:57 dhcp6c 79587 make an IA: PD-0 Feb 26 08:17:57 dhcp6c 79587 status code for PD-0: success Feb 26 08:17:57 dhcp6c 79587 create a prefix 2600:aaaa:ccc:ab00::/56 pltime=86400, vltime=86400 Feb 26 08:17:57 dhcp6c 79587 add an address 2600:aaaa:ccc:ab01:208:a2ff:fe0a:593f/64 on lagg0.223 Feb 26 08:17:57 dhcp6c 79587 add an address 2600:aaaa:ccc:ab02:208:a2ff:fe0a:593f/64 on lagg0.999 Feb 26 08:17:57 dhcp6c 79587 add an address 2600:aaaa:ccc:ab03:208:a2ff:fe0a:593f/64 on lagg0.1003 Feb 26 08:17:57 dhcp6c 79587 add an address 2600:aaaa:ccc:ab10:208:a2ff:fe0a:593f/64 on lagg0.1004 Feb 26 08:17:57 dhcp6c 79587 add an address 2600:aaaa:ccc:ab04:208:a2ff:fe0a:593f/64 on lagg0.224 Feb 26 08:17:57 dhcp6c 79587 make an IA: NA-0 Feb 26 08:17:57 dhcp6c 79587 status code for NA-0: success Feb 26 08:17:57 dhcp6c 79587 create an address 2600:aaaa:bbbb:1c00:4417:7125:99fd:24cb pltime=86400, vltime=11447309925244555648 Feb 26 08:17:57 dhcp6c 79587 add an address 2600:aaaa:bbbb:1c00:4417:7125:99fd:24cb/128 on igb1 Feb 26 08:17:57 dhcp6c 79587 executes /var/etc/dhcp6c_wan_script.sh Feb 26 08:19:06 dhcp6c dhcp6c REQUEST on igb1 - running rc.newwanipv6 Feb 26 08:19:06 dhcp6c 79587 script "/var/etc/dhcp6c_wan_script.sh" terminated Feb 26 08:19:06 dhcp6c 79587 removing an event on igb1, state=REQUEST Feb 26 08:19:06 dhcp6c 79587 removing server (ID: 00:01:00:01:55:f6:d0:f4:f8:bc:12:3e:b6:9c) Feb 26 08:19:06 dhcp6c 79587 got an expected reply, sleeping.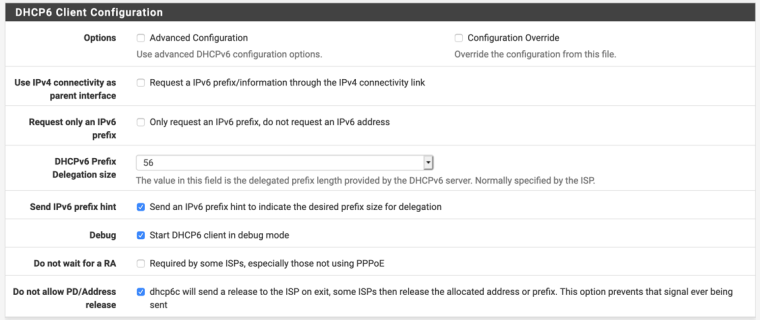
And if I do check advanced configuration to view it:
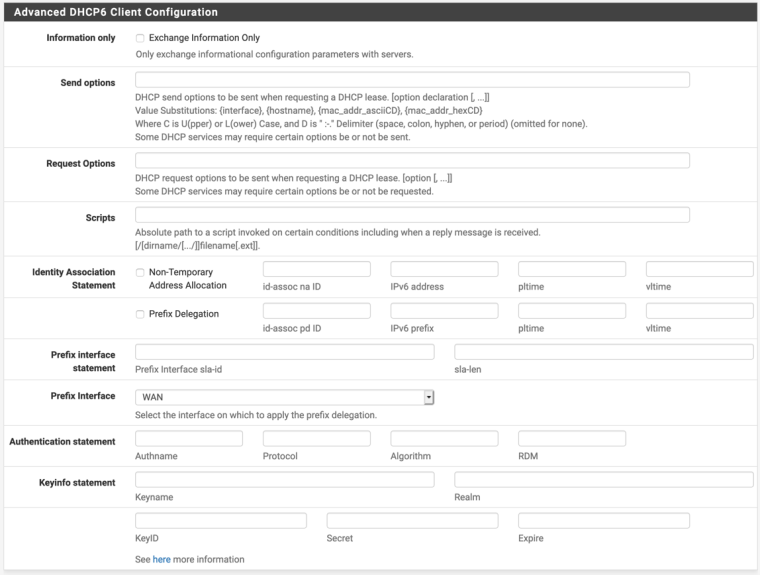
-
-
@derelict said in IPv6 Native with Telstra, Australia:
What's with all that advanced configuration? Especially setting LAN as the PD interface. Is that you stabbing in the dark with your fingers crossed?
It's me following other ISP implementations where people have said its close to how Telstra work. That said, you are right - its me stabbing in the dark trying to get it to work. I am reading info on how other 3rd party routers have got theirs up and running with Telstra and trying to translate that into pfsense. But long and short - its flying darts blind folded.
-
I would get rid of all of that and start over with basically what I have there and start the information gathering and pasting evolution over again.
No need to fly blind with actual information from the ISP and an ISP willing to help.
-
So I now have the config you posted above. Results below. I would also say the ISP doesn't know a thing about pfsense, so not sure how much help they will be to us. That said, the guy does respond to me if I have specific questions.
Here is the debug DHCP log with the config you suggested above:
Feb 27 03:43:11 dhcp6c 17859 reset a timer on em0, state=SOLICIT, timeo=3, retrans=8065
Feb 27 03:43:11 dhcp6c 17859 send solicit to ff02::1:2%em0
Feb 27 03:43:11 dhcp6c 17859 set IA_PD
Feb 27 03:43:11 dhcp6c 17859 set IA_PD prefix
Feb 27 03:43:11 dhcp6c 17859 set option request (len 4)
Feb 27 03:43:11 dhcp6c 17859 set elapsed time (len 2)
Feb 27 03:43:11 dhcp6c 17859 set identity association
Feb 27 03:43:11 dhcp6c 17859 set client ID (len 14)
Feb 27 03:43:11 dhcp6c 17859 Sending Solicit -
@derelict Here is the new packet capture from the settings you told me to implement:
-
@derelict Interestingly, zero UDP packets in the packet captures. All ICMP neighbor solicitation.
-
@derelict Also, no idea how to packet capture their router doing DHCPv6 negotiation. Their router plugs straight into the IPoE interface and I don't have a hub where I can plug wireshark or anything like that to capture packets. Any ideas welcome on how to achieve that. Their router also has custom firmware so no ability to packet capture off of it. I can check their limited logs, but that's about it. Let me know if you want me to that.
-
-
They do not have to know anything about pfSense. They should be able to tell you what is required of ANY dhcp6 client to pull an address and PD. Then we just make pfSense do what they require instead of guessing.
-
@derelict said in IPv6 Native with Telstra, Australia:
They do not have to know anything about pfSense. They should be able to tell you what is required of ANY dhcp6 client to pull an address and PD. Then we just make pfSense do what they require instead of guessing.
What I've given you is everything they have given me when I've asked. I don't think they intend on giving me any more info unless there is a specific question you want me to go back and ask them. They haven't provided me with any further info. I've literally given you exactly what they have given me. They think the issue is to do with neighbor solicitation and pfsense not accepting it.
-
@derelict said in IPv6 Native with Telstra, Australia:
They do not have to know anything about pfSense. They should be able to tell you what is required of ANY dhcp6 client to pull an address and PD. Then we just make pfSense do what they require instead of guessing.
So in summary - I'm out of moves. I feel that if this is ever going to get resolved, and we need more info from Telstra, then I would need to ask them specific questions for them to answer (and I don't know what those questions are).
I've asked the general questions like you've already asked me which is "how do they expect a client to get a DHCPv6 PD" and their response was the email above, plus the monitoring of my control plane, and coming back to me saying its a neighbor solicitation issue with pfsense.
-
You should absolutely see traffic on WAN on UDP/547
That is Solicit, Advertise, Request, Reply
All I did was start that capture then edit/save Interfaces > WAN
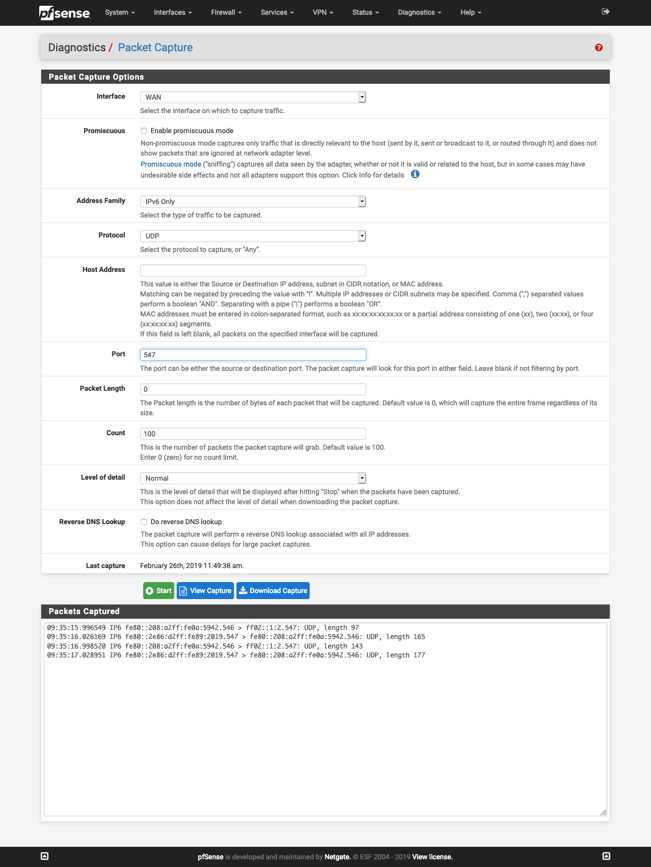
-
@larrikin said in IPv6 Native with Telstra, Australia:
I am reading info on how other 3rd party routers have got theirs up and running with Telstra and trying to translate that into pfsense.
Maybe you should post some of those.
-
@derelict Sure. Here is one https://forums.whirlpool.net.au/archive/2597579
-
OK so prefix-only probably translates to:
Request only an IPv6 prefix
Only request an IPv6 prefix, do not request an IPv6 addressDid you check that?
-
@derelict said in IPv6 Native with Telstra, Australia:
OK so prefix-only probably translates to:
Request only an IPv6 prefix
Only request an IPv6 prefix, do not request an IPv6 addressDid you check that?
Yes - I've tried that too.
-
OK and what did the dhcp6c logs look like when you only enabled that and tried it?
You're going to have to be a lot more forthcoming with information. We can't test it from here. Only you can.
-
Here are the logs. Want another packet capture too?
Feb 27 10:26:01 dhcp6c 48288 reset a timer on em0, state=SOLICIT, timeo=4, retrans=16326
Feb 27 10:26:01 dhcp6c 48288 send solicit to ff02::1:2%em0
Feb 27 10:26:01 dhcp6c 48288 set IA_PD
Feb 27 10:26:01 dhcp6c 48288 set IA_PD prefix
Feb 27 10:26:01 dhcp6c 48288 set option request (len 4)
Feb 27 10:26:01 dhcp6c 48288 set elapsed time (len 2)
Feb 27 10:26:01 dhcp6c 48288 set client ID (len 14)
Feb 27 10:26:01 dhcp6c 48288 Sending Solicit
Feb 27 10:25:53 dhcp6c 48288 reset a timer on em0, state=SOLICIT, timeo=3, retrans=8065
Feb 27 10:25:53 dhcp6c 48288 send solicit to ff02::1:2%em0
Feb 27 10:25:53 dhcp6c 48288 set IA_PD
Feb 27 10:25:53 dhcp6c 48288 set IA_PD prefix
Feb 27 10:25:53 dhcp6c 48288 set option request (len 4)
Feb 27 10:25:53 dhcp6c 48288 set elapsed time (len 2)
Feb 27 10:25:53 dhcp6c 48288 set client ID (len 14)
Feb 27 10:25:53 dhcp6c 48288 Sending Solicit
Feb 27 10:25:49 dhcp6c 48288 reset a timer on em0, state=SOLICIT, timeo=2, retrans=3982
Feb 27 10:25:49 dhcp6c 48288 send solicit to ff02::1:2%em0
Feb 27 10:25:49 dhcp6c 48288 set IA_PD
Feb 27 10:25:49 dhcp6c 48288 set IA_PD prefix
Feb 27 10:25:49 dhcp6c 48288 set option request (len 4)
Feb 27 10:25:49 dhcp6c 48288 set elapsed time (len 2)
Feb 27 10:25:49 dhcp6c 48288 set client ID (len 14)
Feb 27 10:25:49 dhcp6c 48288 Sending Solicit
Feb 27 10:25:47 dhcp6c 48288 reset a timer on em0, state=SOLICIT, timeo=1, retrans=2083
Feb 27 10:25:47 dhcp6c 48288 send solicit to ff02::1:2%em0
Feb 27 10:25:47 dhcp6c 48288 set IA_PD
Feb 27 10:25:47 dhcp6c 48288 set IA_PD prefix
Feb 27 10:25:47 dhcp6c 48288 set option request (len 4)
Feb 27 10:25:47 dhcp6c 48288 set elapsed time (len 2)
Feb 27 10:25:47 dhcp6c 48288 set client ID (len 14)
Feb 27 10:25:47 dhcp6c 48288 Sending Solicit -
@derelict 0_1551224042344_packetcapture.cap.zip
That's the latest packet capture based on turning on "request only an IPv6 prefix".