Tried everything port forwarding not working??
-
@derelict trust me tried that. Forgot to change before screenshoot. That not the issue here.
What you mean if traffic arriving on Wan?
-
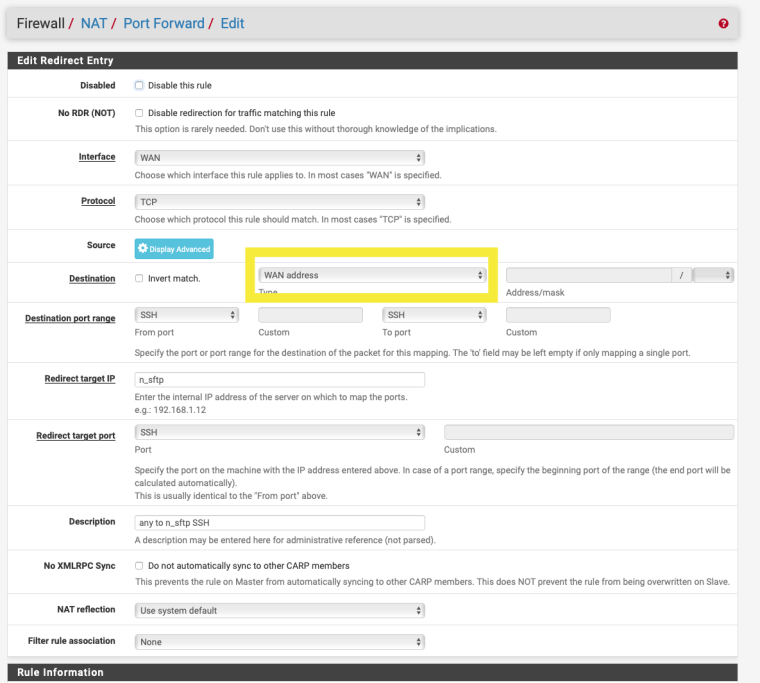
Firewall rule on the WAN interface ?

Do a packet capture on the WAN for port 8080.
-
No nothing actually. I think because it's not in use maybe? I trying to open a port for a game.
-
Do you have a RFC1918 address on your WAN interface ?
https://tools.ietf.org/html/rfc1918
-
@djinn1 said in Tried everything port forwarding not working??:
trust me tried that. Forgot to change before screenshoot. That not the issue here.
What you mean if traffic arriving on Wan?If you had actually tried that you would not be asking this question.
It is step number 5 in the list of things to check there.
Packet capture on WAN for traffic to port 8080 and attempt a connection. Is the SYN there?
If not, it is blocked upstream. If so, packet capture on LAN for port 8080 and test again. Is the SYN forwarded to the inside host? If so, the port forward is working. Is there a response? If not, go to that host and figure out why it is not responding.
-
@nogbadthebad Yes its there.
-
@derelict Hi, you need to explain it a little bit esier. I am not a pro, I have basic network knowledge.
-
Yes what’s there?
If your saying your WAN address is a RFC1918 address your pfSense box is connected to another router, that’s probably why the port forward isn’t working and also why you don’t see any hits on the firewall rule / packet capture.
-
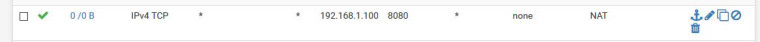
@nogbadthebad My pfsense is only router connected. no other router in the house.
-
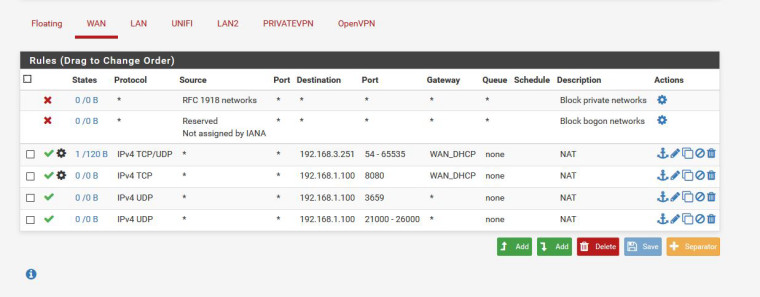
The order of the 3rd and 4th rule needs swapping round.
Firewall rules are read from top to bottom and why have you set a gateway
-
Not really. After the port forward translates the destination address the 54-65535 rule will not match.
-
@nogbadthebad Because I have a VPN on the other subnet.
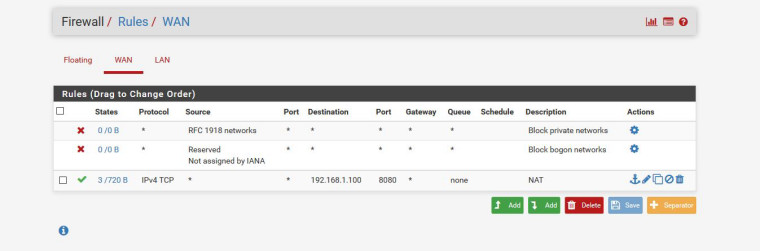
I have reset all my Pfsense box nothing installed and only port forward the 8080 an still not open.
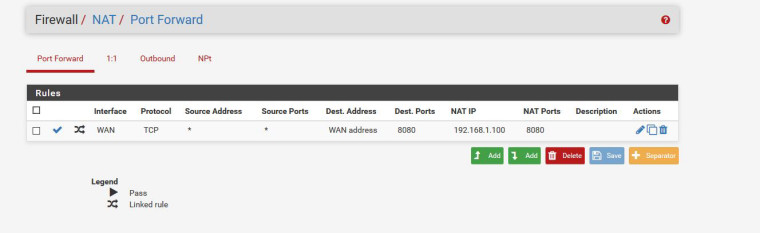
-
@derelict That one is other subnet.
-
Packet capture on the INSIDE 192.168.1.0 interface for traffic to 192.168.1.100 port 8080 and test again. Is the traffic there?
-
@derelict how?
-
Diagnostics > Packet Capture
Interface: WAN
Protocol: TCP
Port: 8080
Count: 10000Start
Run your tests connecting to WAN:8080 from the outside.
Diagnostics > Packet Capture
Stop
What is displayed at the bottom?
THEN:
Diagnostics > Packet Capture
Interface: LAN
Host Address: 192.168.1.100
Protocol: TCP
Port: 8080
Count: 10000Start
Run your tests connecting to WAN:8080 from the outside.
Diagnostics > Packet Capture
Stop
What is displayed at the bottom?
-
@derelict Ok done that what is correct and whats not? Because my ip is there don´t want to share screen.
-
So copy and paste it into a text editor and search and replace for the first three octets of your WAN address substituting something like a.b.c and post the results.
-
@derelict
LAN
19:29:38.996655 IP ab.abc.6.228.56118 > 192.168.1.100.8080: tcp 0
19:29:38.996674 IP ab.abc.6.228.56120 > 192.168.1.100.8080: tcp 0
19:29:38.996908 IP 192.168.1.100.8080 > ab.abc.6.228.56118: tcp 0
19:29:38.996910 IP 192.168.1.100.8080 > ab.abc.6.228.56120: tcp 0
19:29:41.726274 IP ab.abc.6.228.56124 > 192.168.1.100.8080: tcp 0
19:29:41.726277 IP ab.abc.6.228.56126 > 192.168.1.100.8080: tcp 0
19:29:41.726443 IP 192.168.1.100.8080 > ab.abc.6.228.56126: tcp 0
19:29:41.727746 IP 192.168.1.100.8080 > ab.abc.6.228.56124: tcp 0WAN
19:36:45.017850 IP ab.abc.6.228.56158 > ab.abc.12.200.8080: tcp 0
19:36:45.017886 IP ab.abc.6.228.56160 > ab.abc.12.200.8080: tcp 0
19:36:45.018174 IP ab.abc.12.200.8080 > ab.abc.6.228.56158: tcp 0
19:36:45.018239 IP ab.abc.12.200.8080 > ab.abc.6.228.56160: tcp 0
19:36:46.470791 IP ab.abc.6.228.56164 > ab.abc.12.200.8080: tcp 0
19:36:46.470793 IP ab.abc.6.228.56162 > ab.abc.12.200.8080: tcp 0
19:36:46.471078 IP ab.abc.12.200.8080 > ab.abc.6.228.56162: tcp 0
19:36:46.471087 IP ab.abc.12.200.8080 > ab.abc.6.228.56164: tcp 0
19:36:47.605390 IP ab.abc.6.228.56168 > ab.abc.12.200.8080: tcp 0
19:36:47.605393 IP ab.abc.6.228.56166 > ab.abc.12.200.8080: tcp 0
19:36:47.605683 IP ab.abc.12.200.8080 > ab.abc.6.228.56166: tcp 0
19:36:47.605685 IP ab.abc.12.200.8080 > ab.abc.6.228.56168: tcp 0
19:36:48.731989 IP ab.abc.6.228.56172 > ab.abc.12.200.8080: tcp 0
19:36:48.731995 IP ab.abc.6.228.56170 > ab.abc.12.200.8080: tcp 0
19:36:48.732264 IP ab.abc.12.200.8080 > ab.abc.6.228.56170: tcp 0
19:36:48.732271 IP ab.abc.12.200.8080 > ab.abc.6.228.56172: tcp 0
19:36:49.240709 IP ab.abc.6.228.56174 > ab.abc.12.200.8080: tcp 0
19:36:49.240980 IP ab.abc.12.200.8080 > ab.abc.6.228.56174: tcp 0
19:36:49.240994 IP ab.abc.6.228.56176 > ab.abc.12.200.8080: tcp 0
19:36:49.241182 IP ab.abc.12.200.8080 > ab.abc.6.228.56176: tcp 0 -
OK. View the existing capture again but set Level of detail to full before pressing view, do the same substitution, and post that.
You don't have to capture again, just go to Diagnostics > Packet capture, set the level of detail, and press view to see the last capture taken again.
The LAN capture will be the most informative there.