TLS certificate--can I make a fake CA?
-
When connecting to my SG-1100, I prefer to use TLS. However, since the certificate it is using is self-signed, all browsers show warnings, alarms, etc. I also hear the Google is thinking about/planning on blocking access outright to webpages using such certs in the future.
Is there a way for me to get around this? What comes to mind for me is manually adding a root cert./internal CA to my device(s). Can the SG-1100 run its own CA for this purpose? Is there another good way to deal with this issue?
Yes, I know, doing so will not really improve security--it will just hide the problem and just possibly take my headache with it.
Thanks!
-
RTFM:
https://docs.netgate.com/pfsense/en/latest/certificates/index.html
https://docs.netgate.com/pfsense/en/latest/book/certificates/index.html -
@cyberminion said in TLS certificate--can I make a fake CA?:
What comes to mind for me is manually adding a root cert./internal CA to my device(s)
pfSense generated a cert when it was installed. Or make your own one with your own details. Export it, and import it into your browser's cert store.
You're done.Or get some 'real' certs - even a wildcard for all your LAN devices, trusted by all browsers. It's free, pfSense can do so it for you (see the acme package) but their might we a initial headache.
-
Create your own CA in the cert manager.
Then you can create whatever certs you want, with what ever SANs you want on them.. And you can make them for whatever length you want.. Normally I do 10 years.
Then yes any browser you can add the CA so it trust certs... You can do this for all your things that can use ssl.
I do it for my cisco switches, I do it for my unifi controller software. I do it for my nas.
So you get your pretty green icon
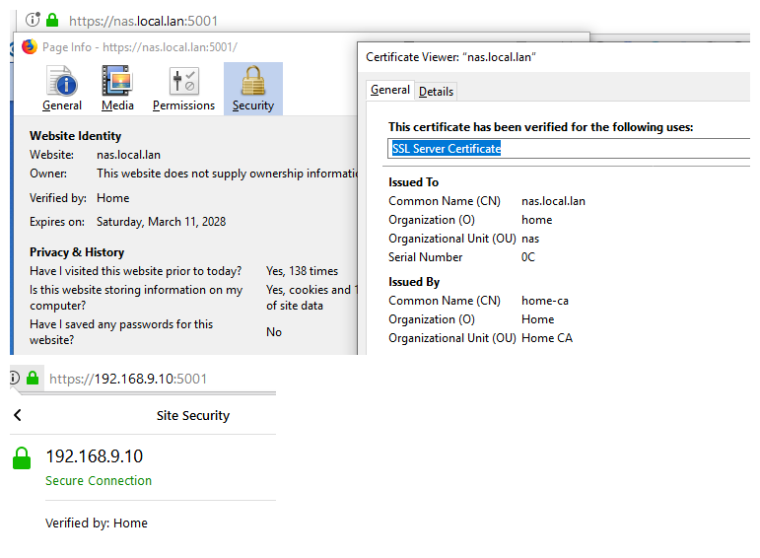
And you can even access direct IP and still be trusted because you just add that as SAN when you create the crt..
ACME is nice if you need the public to trust your cert.. But why have to go through the hassle of renew cert every 90 days when your the only one that accesses the interface anyway.
-
+1 for ACME from me.
Once you have ACME going it's all automated, the 90 day limit means squat. :-)
You can certainly make your own CA + Server certs and import the CA where needed, but that can be a bit of a management pain if you access the GUI from a variety of devices, especially from mobile devices.
-
@jimp said in TLS certificate--can I make a fake CA?:
Once you have ACME going it's all automated, the 90 day limit means squat. :-)
Not true - since its a failure point... And hard to run acme on a cisco switch or on unifi controller or plex, etc.
Only place amce makes any sense at all is if you need the world to trust you... If its you admining then its pointless to use acme.. And do it once and your done.. Nothing to fail ever on some update every X days.
And acme doesn't do non public domains, nor rfc1918, etc.
-
It may be a failure point but I have it going on a couple dozen systems here, including some wildcard certs, and the only time it's failed is when I've accidentally disabled the cron job for one reason or another.
You could export and automate the cert deployment as well to other devices, it's just not as easy.
And it isn't about the world trusting you, it's about leveraging the built-in chain of trust in devices that support SSL. You can override that, certainly, but some things take that better than others, and you have to get things imported just right into all the clients. With ACME all the work is on the firewall and everyone else picks it up automatically.
To say it is "pointless" is demonstrably false. I know you don't like it, but it's very useful for those that know how to use it properly.
-
I am using it for my ssl offload on my ombi request server for my plex with ha-proxy... It works sure.. But what I don't see is why I would use that for something like a switch or standalone box that is only access by limited admins..
Now my ombi box is accessed by friends and family - so yeah not going to ask them to trust my ca.. So the acme makes more sense.
And I get how with the certbot and the package its come down to be idiot proof sort of setup.. But it still makes no sense to me to add that failure point for something that is going to be accessed by a limited client user base.. That is a one time trust of the CA.. And then a 10 year cert.. Because that hardware will be replaced before have to update the cert ;)
Don't get me wrong my use of the acme package and haproxy was freaking drop dead simple.. And worked with a few clicks - it was freaking amaze balls ;) But it makes no sense to for use case on isolated devices that are only accessed by a limited admin staff, etc.
-
Thanks for all the information!
No more than 6 devices "need" to trust the cert. However, I'm trying to soak up as much knowledge as possible, so I'd like to try both ways. I figured adding the cert manually would be easy, once I found where it was hiding on pfsense. However, I was surprised to find how much things have changed since I last did this--it has been awhile. How do I actually add the CA to my system? I thought it was in the browser settings, but although I could view a specific site's cert., I could not find in either Firefox or Chromium how to view or edit CAs.Secondly, where should I start for setting up Acme? Is it hiding in some menu somewhere, or is it a separate package? I honestly have no clue what acme is or how it works, but I figure I'll give it a try.
For the record, this is a home network that I can afford to mess up a little bit.
Thank you!
-
acme : This forum : Home => pfSense Packages => ACME
This package generates certificates using protocol called 'acme', and the certificate authority is https://letsencrypt.org/ I guess Lets Encrypt is number one today - and raising.
Certificates are stored in Firefox here : Menu => Tools => Options => Private live and security => Show the certificates. Over there you import certificates you trust. You'll see that the certificate list of your browser is already populated with public trusted certificates.
The certificate that you have to import into your browser can be found here :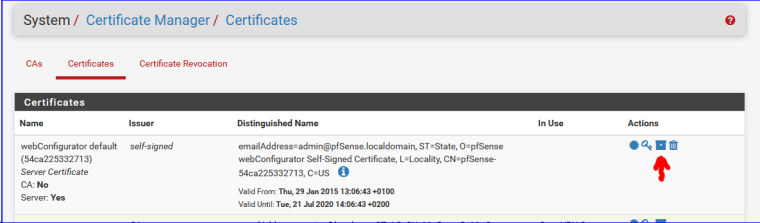
Use the icon pointed to by the red arrow.
This will give you a file with the "p12" extension to download. Import that file in your browser. -
I have installed the ACME package, and will start playing with it. Let's Encrypt certainly is popular...certs for free--who can argue with that?
The path to my CA/cert list in FF is a bit different for me, using FF v65. It is Menu>Privacy & Security>Certificates>View certificates
In there, I can supposedly import my cert, but when I attempt to do so, it demands a decryption key for the certificate...which I don't happen to know. I tried the pfsense admin password, the cert's private key, and almost anything else i could think of...no luck. -
@cyberminion said in TLS certificate--can I make a fake CA?:
it demands a decryption key for the certificate...which I don't happen to know. I tried the pfsense admin password, the cert's private key, and almost anything else i could think of...no luck.
When you had the password generated, you did not supply a password.
So there is : none. (nothing).@cyberminion said in TLS certificate--can I make a fake CA?:
Let's Encrypt certainly is popular...certs for free--who can argue with that?
Not exactly free.
You need to have a 'real' domain name. Not something like pfsense.local but something like yourhomenetwork.tld and only a registrar can give you one for a small annual fee.
The thing is : Letenscrypt, and any other certificate authority can only give you a real cert for real domain names, because you can prove that you own that domain name. To make this even more clear : you can not ask a cert authority to give you a certificate for example biggest-us-bank.com because you do not own that domain. Read https://letsencrypt.org/getting-started/
Proving that you own a domain name can be done by setting up some DNS sub domain for that domain, or placing a file in the webroot, on the server where the A (AAAA) record points to, etc.
You have to read and learn what it is all about, choose your way of "proving" , and set things up. Many domain registrars have a way that Letsenscrypt can use to check that your are the owner.
Also checkout pfSense Packages => ACME for many questions, answers and common pitfalls.Remember the words of @johnpoz said : maybe home made certs will do just fine ^^
I had to use a real cert, not for accessing the pfSense web GUI, but for my captive portal users.
@cyberminion said in TLS certificate--can I make a fake CA?:
I'm trying to soak up as much knowledge as possible
Ready to enter the cert dimension ? ;)
-
@cyberminion said in TLS certificate--can I make a fake CA?:
I could not find in either Firefox or Chromium how to view or edit CAs.
So since like 64 of firefox it can be set to trust the Windows cert store... But you still can import them the same as before..
Options
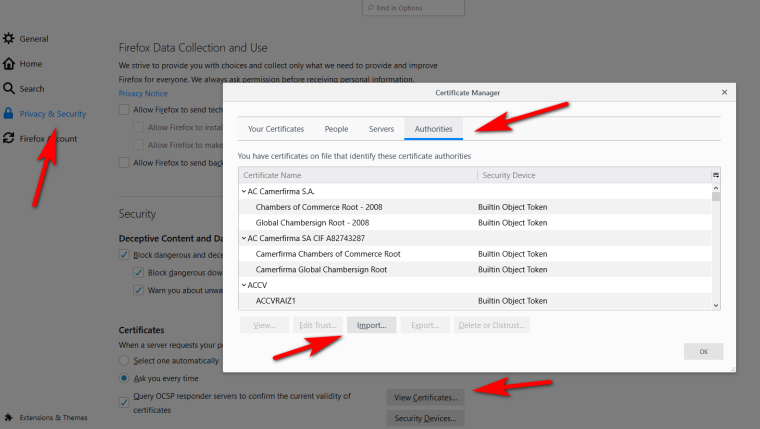
Chrome has always just used the OS cert store.. So just install the CA into windows.
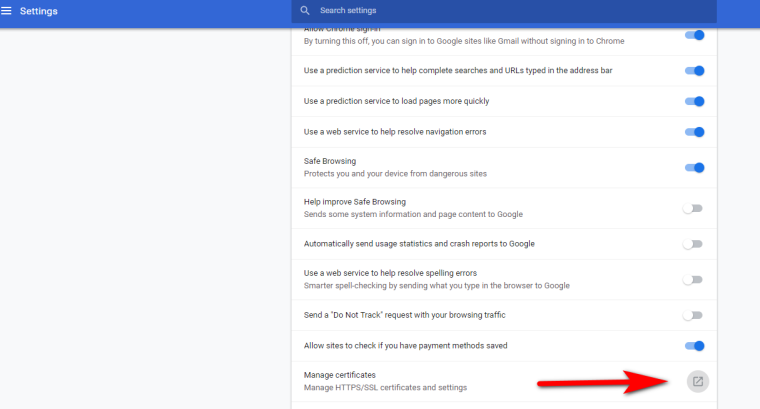
You can also get there from chrome settings advanced...
-
I added the cert. to Firefox's certificate store. However, FF now complains that it is self-signed (duh!) And still requires an exception.
Error:
x.x.x.x uses an invalid security certificate.
The certificate is not trusted because it is self-signed.
The certificate is only valid for pfSense-5xxxxxxxxxxxx.Error code: MOZILLA_PKIX_ERROR_SELF_SIGNED_CERT
(IPs and IDs changed to protect the guilty)I tried using the domain name also, but of course, that is only in the local DNS resolver. I do have a proper domain name I could potentially use for ACME, at least, but I doubt there's a way for it to help with this. It looks rather like I am not going to be able to get a fuss-free connection using local setup only, unless as I originally asked, I can set up my own CA.
-
About Firefox and your own CA : https://www.google.com/search?client=firefox-b-d&q=firefox+self+signed+certificate+problem
So, it's possible - but some steps are needed. Check also, because you'll discover while reading there their might be huge risks. And that's why home-baken certs are out of business these days.
-
@cyberminion said in TLS certificate--can I make a fake CA?:
The certificate is only valid for pfSense-5xxxxxxxxxxxx.
You called your pfsense that? Or you are just using the out of the box self signed cert it creates..
That is not the same as creating a CA in pfsense, then creating a cert to use for your webgui - and trusting the CA... Those are not "self signed"
I have gone over this with multiple posts with pictures of exactly how to do this over the years... Its possible the posts images did not come through when moved to new forum software. If you like I can walk you through this yet again.. With pictures ;)
-
No, I did not name my pfsense that, I was obscuring the unique ID it currently uses. I am using a netgate box, which came with a predefined name. I have not changed it, so I didn't want to be posting the ID openly.
I am interested, but not finding your posts to which you are referring. Do you have a link to one such post, so you don't need to repost the whole thing?
-
The ID on the initial GUI cert isn't anything secret, it's only randomized so that your browser sees a unique certificate subject. Firefox especially dislikes having multiple certificates with the same subject line. The randomness helps keep that from being a problem.
-
@CyberMinion said in TLS certificate--can I make a fake CA?:
, so you don't need to repost the whole thing?
I don't think the images would of survived the forum update... I will put one together in the morning.. Only take a couple of minutes.
-
Ok here you go..
So create a new CA.
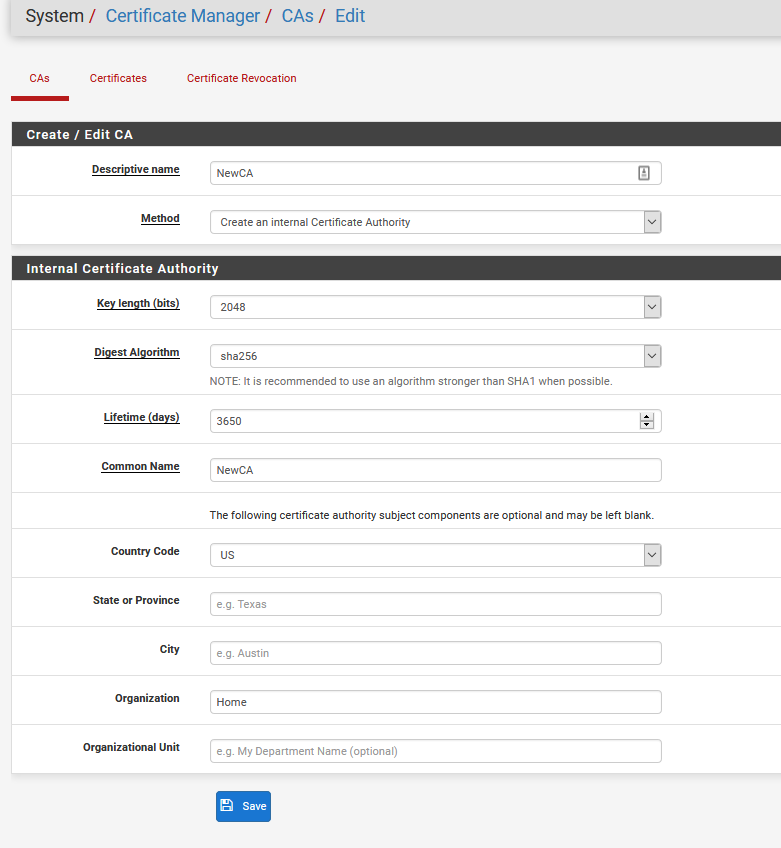
Download the CA cert to your machine.
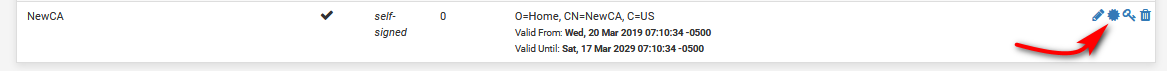
Now create new CERT using that CA.
Give it a desc name, pick your new CA, put in the common name for your pfsense box, ie its fqdn you use to access it.. Mine is sg4860.local.lan Any other optional stuff you want to fill out.
Make sure you change it to server cert vs user cert
And SAN (alternate names) for your pfsense box, or any other device your going to install this server cert on. Make sure you add the FQDN SAN.. Many browsers now require this not just the common name on the cert.
You can even put in your IP if you want to be able to hit the IP as trusted.
Install the newCA as trusted in your browser - this is firefox
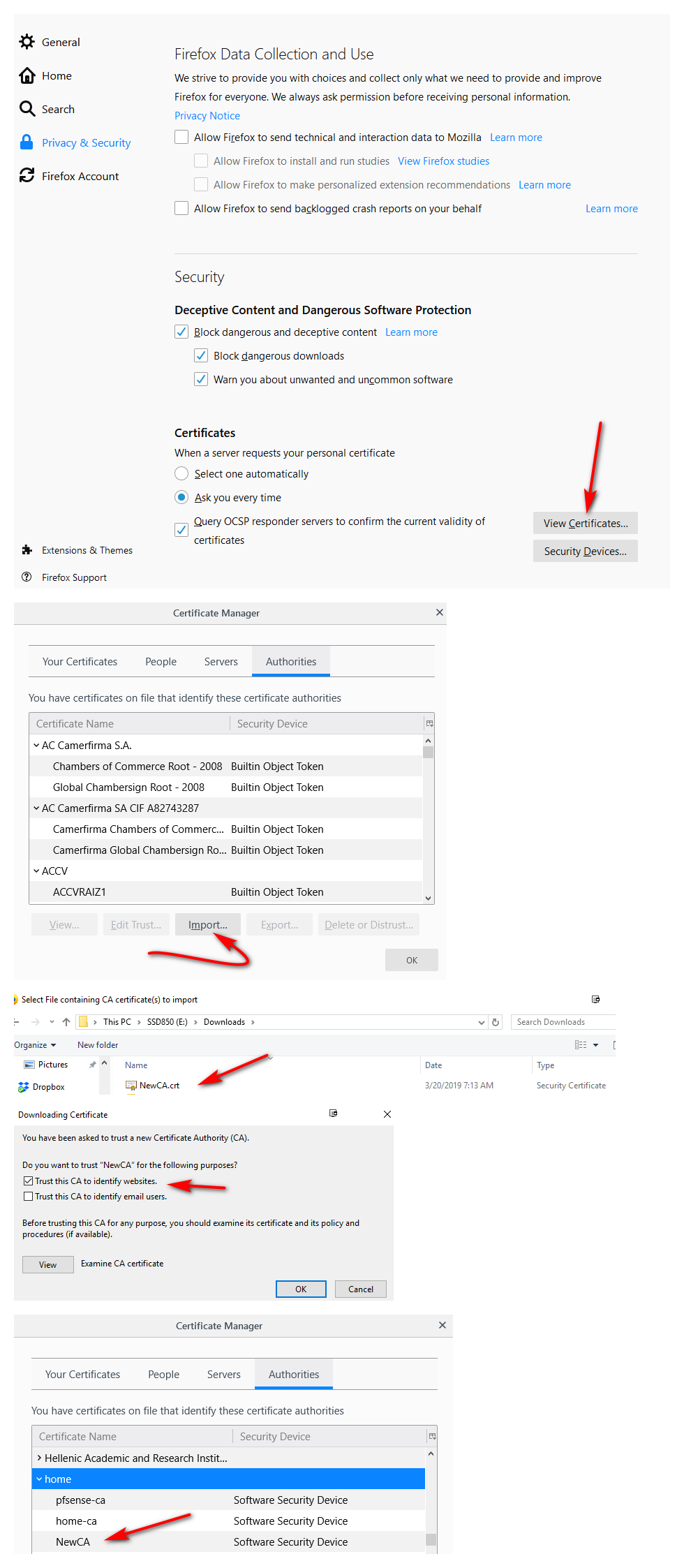
Change pfsense gui to use the new cert signed by your newca
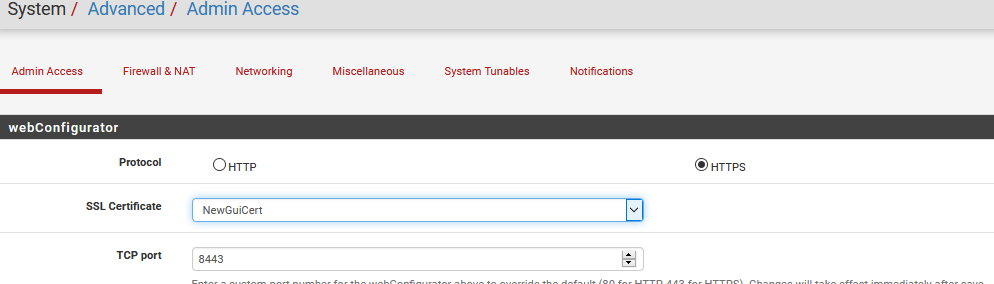
And there you go bing bang your trusting your pfsense gui, green and pretty.
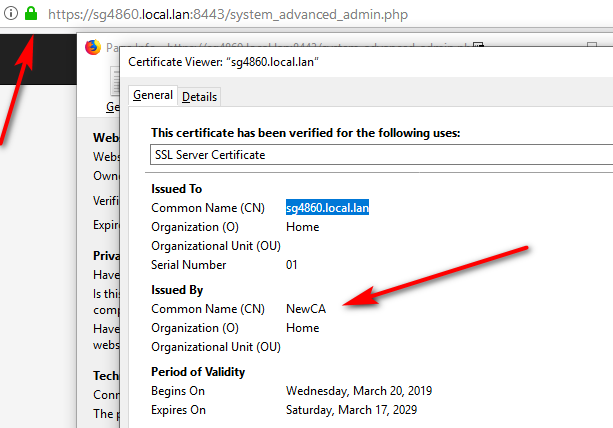
And you can even use the the IP to get to it still trusted and green
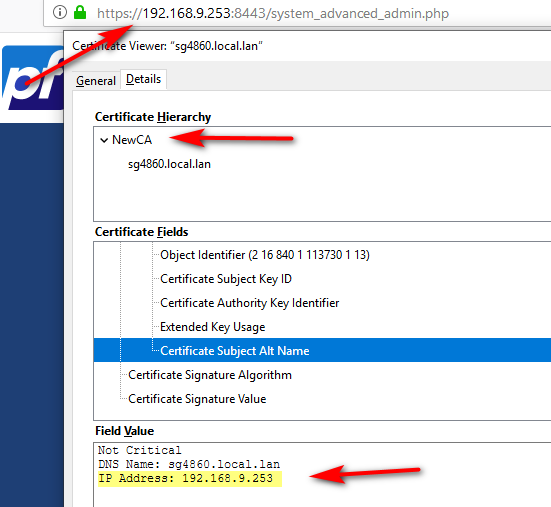
Now your good for as long as you made the cert for - 10 years should be good ;)
Any questions just ask..
While its a lot of pics and looks like a lot of steps.. Its really only couple of mins tops!
Now your shiny new CA, can sign off on any boxes you want to put certs... Any browser that trusts your CA will trust any certs signed by your ca, IE, FireFox, Chrome, Opera, etc.. Even your mobile devices browsers can trust your CA.
This one time thing for any devices that devices under your control will access. But this sort of setup is not good for when the public are large groups of devices/browsers you do not control - or are not willing to trust your CA, etc. But since say the pfsense gui should only be accessed by "admins" of your firewall.. Say YOU only then this is simple solution that is one time thing and then good for years and years.
-
 G Gertjan referenced this topic on
G Gertjan referenced this topic on
-
 J johnpoz referenced this topic on
J johnpoz referenced this topic on
-
 J johnpoz referenced this topic on
J johnpoz referenced this topic on