DNS Resolver/Forwarder host overrides not working
-
@johnpoz
I have no idea how that got set, or how. I was fooling with google.com and test.google.com overrides to see if they were broke too and the answer is yes.So then, what do you suggest? I have a test version of pfsense running in a VM. Maybe I can restore it to defaults, configure host overrides and see if it works there. If so, then I'll one by one load the same packages I have on my production box and see if pfblocker breaks it.
-
I can tell you for fact out of the box host overrides just work.. So yeah you got something odd going on..
Click on your custom options box in your unbound config - what do you have in there?
Do you have anything set in your port forwards on your lan interface?
I would set unbound to log queries, you can do that with
server:
log-queries: yesIn your custom option box and then sure up the logging level in the setting.
Now when you do a query for your host override you will see it in the log
Mar 1 10:45:03 unbound 7669:0 info: 192.168.9.100 aaatest.google.com. A IN
$ dig @192.168.9.253 aaatest.google.com ; <<>> DiG 9.12.3-P1 <<>> @192.168.9.253 aaatest.google.com ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 21606 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;aaatest.google.com. IN A ;; ANSWER SECTION: aaatest.google.com. 3600 IN A 11.11.11.11 ;; Query time: 0 msec ;; SERVER: 192.168.9.253#53(192.168.9.253) ;; WHEN: Fri Mar 01 10:45:03 Central Standard Time 2019 ;; MSG SIZE rcvd: 63 -
I have nothing in the custom options box. No lan port forwards.
Nothing extra is showing in the dns resolver log. Where exactly is this log?
-
Its in where all the other logs are ;)
There where did the customs stuff for google come from?
Seems to me you got something tweaked up!!
Did you put in the setting for query logs?
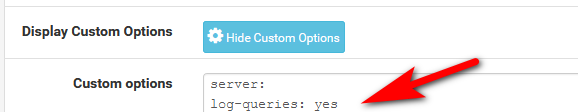
If you want to see the queries for logs.. Is anything happening there - all your other clients asking for stuff that you say is being done by unbound?
-
@johnpoz
Yes sir. I did that exactly as you show. Yes clearly this system isn't working. I'm gonna do as I explained with my VM install of pfsense. Take it to defaults with no addon packages and see if the host overrides work there. -
@johnpoz
So some progress has been made. pfblocker and suricata are not effecting my problem. I also had BIND installed but not running. I uninstalled the package and now my DNS resolver host overrides return this:
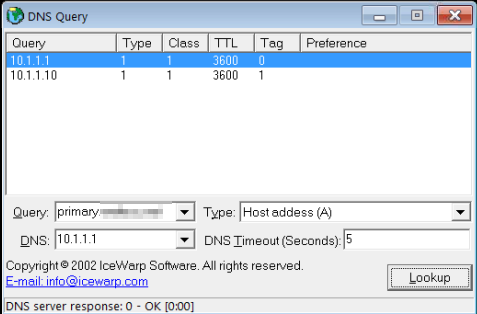
The second IP is the correct one. Now how do I get rid of the 10.1.1.1? -
So you had bind running would be my guess.. And unbound wasn't running.. That completely explains the problem!!!
And your not going to get rid of the 2nd one.. if pfsense is called primary.domain.tld that it will return the IP of its lan IP..
You can not just create another primary.domain.tld and not return that address.
Call pfsense something else!!! like pfsense.domain.tld vs primary.domain.tld - then you can create your host override pointing to what you want.
-
@johnpoz
No, I verified that unbound was indeed running. BIND was installed, but disabled.
Ok I can do that. I will give pfsense a different host name and that problem should be solved.On another topic, I have another problem. Do you know how I can make the windows OpenVPN clients actually run in service mode so that they will connect without any user needing to be logged on? I've tried everything I've searched for online but nothing works.
-
Why would you want / need windows to run openvpn... You can just run your vpn client on pfsense and policy route.
If you want support on how to do XYZ with windows - then you could ask in the general section... But pretty sure its going to be a bunch of crickets.. Your best hope is actual windows support forum.
So you want your windoows box to be connected to vpn service, while nobody is logged into? Why would you not just do that on pfsense - no any box you want on your whole network can be routed out your vpn, or multiple different vpns.. With ZERO to do on the client. Be it they logged in, be it they just booted, be it they are shutting down, etc.
"BIND was installed, but disabled." -- Sure OK <rolleyes> I believe you <rolleyes> I have been doing DNS with bind since it came out.. I have been running Pfsense since it came out... I have been using unbound and bind on pfsense unbound was just a package and not built in, etc. etc. etc.. But sure OK -- your install of bind dicked up your host overrides ;) I have the bind package installed. And I turn it on and off all the time to help users with here.. The configs for these packages have zero to do with each other.. You have x service listening on 53 or you have y service listening on 53... If you have them both enabled then you run into a RACE condition on which service is actually going to bind to 53 and answer
You had to ask where the logs where... So sorry but have a hard time buying that story.. When bind answering vs unbound explains all your problems..
-
@johnpoz
I'm trying to get 2 remote windows PC's connected securely to my network via OpenVPN. I've got the tunnel and the client connections created and working. I can even have them auto connect when a user logs on. But I want to go one step further and have the vpn client operate as a service so that it will connect regardless if any user is logged on or not.Perhaps I should've taken a snippit of my services section. I'm telling you, BIND was installed but not in use. Resolver was in use.
I sense a little attitude. Now you've got me wanting to reinstall BIND, break my shit, and grab a snippit just to put your foot in your mouth. ;)
Thanks for your help though. Appreciate it.
-
@reddelpapa said in DNS Resolver/Forwarder host overrides not working:
Perhaps I should've taken a snippit of my services section.
First, I love pfSense.
But when multiple identical-service-types services are running on my system - any system, I ask the one that knows :
[2.4.4-RELEASE][admin@pfsense.mynet.net]/root: ps ax | grep 'named' 44896 0 S+ 0:00.00 grep namedNow I know bind isn't running - installed, activated, whatever. It isn't running.
Another this one :
sockstat -l | grep ":53"to see who is listening on port "53".
The usage of such command made me head-slapping more then ones.
GUI's are nice,
Knowing the absolute truth is better.Latest experience, last month : freeradius was running and not taken in account my new settings.
Found out that I managed to start multiple instances .... my head still hurts. -
Go ahead do that do reinstall it... I have it installed..
As Gertjan stated... Why did you not do that?
If unbound was running then it would of freaking answered the query, or logged it!! It did neither... So what does that tell you?
Just installing bind has zero to do with unbound... I have it installed on my own system - but guess what its NOT running!!
But unbound is!
[2.4.4-RELEASE][root@sg4860.local.lan]/root: sockstat -l | grep :53 unbound unbound 18353 3 udp4 192.168.9.253:53 *:* unbound unbound 18353 4 tcp4 192.168.9.253:53 *:* unbound unbound 18353 5 udp4 192.168.2.253:53 *:* unbound unbound 18353 6 tcp4 192.168.2.253:53 *:* unbound unbound 18353 7 udp4 192.168.4.253:53 *:* unbound unbound 18353 8 tcp4 192.168.4.253:53 *:* unbound unbound 18353 9 udp4 192.168.6.253:53 *:* unbound unbound 18353 10 tcp4 192.168.6.253:53 *:* unbound unbound 18353 11 udp4 192.168.7.253:53 *:* unbound unbound 18353 15 tcp4 192.168.7.253:53 *:* unbound unbound 18353 16 udp4 192.168.3.253:53 *:* unbound unbound 18353 17 tcp4 192.168.3.253:53 *:* unbound unbound 18353 18 udp6 2001:470:snipped:53 *:* unbound unbound 18353 19 tcp6 2001:470:snipped:53 *:* unbound unbound 18353 20 udp4 127.0.0.1:53 *:* unbound unbound 18353 21 tcp4 127.0.0.1:53 *:* unbound unbound 18353 22 udp6 ::1:53 *:* unbound unbound 18353 23 tcp6 ::1:53 *:* [2.4.4-RELEASE][root@sg4860.local.lan]/root: -
Well, maybe you're right. Because it does make sense that something else was getting in the way of unbound. I just know what I saw under system services because I thought of that several days ago and specifically looked to see if BIND was running or not. After I installed suricata and pfblocker on my test install and DNS resolver still worked as it should, that triggered me to go ahead and uninstall BIND because it was the only difference between my test and production pfsense units. But either way, the problem is solved, and I appreciate your help in doing so.
Have a great weekend,
Nate