-
Sorry - missed your key length Q; no - previous psk was testtest - the last logs were 12345
-
Hmm, curious.
Is this the only tunnel at each end?
Does either end have more than one WAN?
Can we see the config at the pfSense end?
Steve
-
@orangehand said in Has anyone got a VPN to a Draytek working?:
looking for peer configs matching 81.143.205.132[%any]...88.97.12.47[88.97.12.47]
Ok in fact this could be an identifier issue. It looks like the Draytek is sending 'any' as the identifier for pfSense. What is it actually set to in pfSense?
I don't see a place to specify a peer ID in the Draytek settings other than the 'dial-in' section but you might try adding it there.
Steve
-
-
In dial in settings you mean the username field? What would I put there please?
-
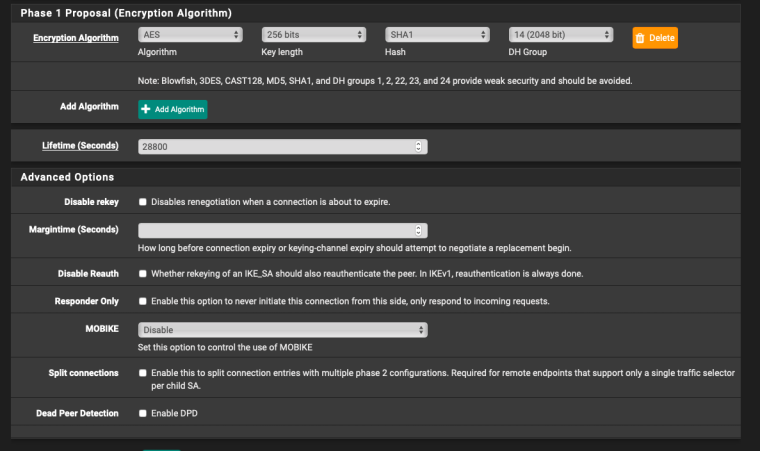
Ok the Draytek is sending it's own IP as an identifier but 'any' for the pfSense end. So in pfSense it should be the opposite; 'any' for My Identifier and 'peer IP' for Peer Identifier.
But better would be to set an Identifier in the Draytek. The only place in the screenshot I see to do that is the 'Peer ID' filed in the dial-in settings. Try that. See if it changes what is shown in the pfSense logs. You want it to show:
looking for peer configs matching 81.143.205.132[81.143.205.132]...88.97.12.47[88.97.12.47]Then set My IP and Peer IP as the identifiers in pfSense to match.
Steve
-
That worked, many many thanks Steve
-
Ah, great. Were you able to get the Draytek to send an IP as identifier or did you have to stick with 'any' as the local identifier in pfSense?
Steve
-
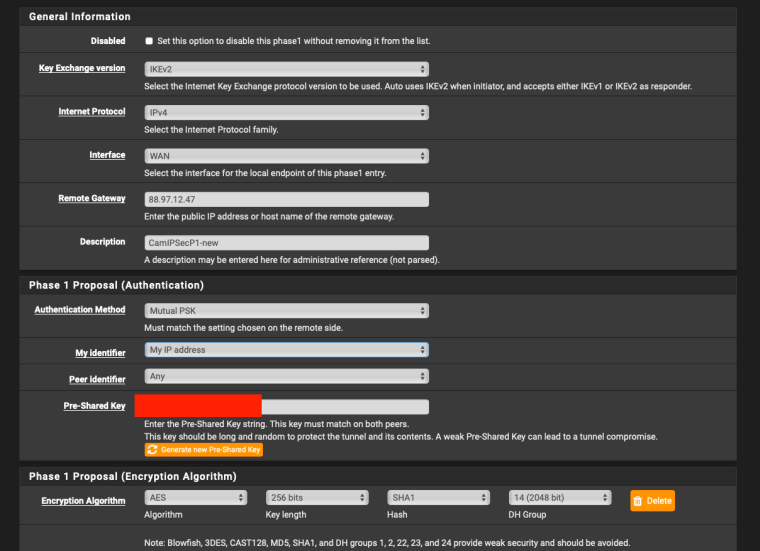
pfSense (my) end I used My identifier: My IP Address and Peer Identifier: Peer IP address
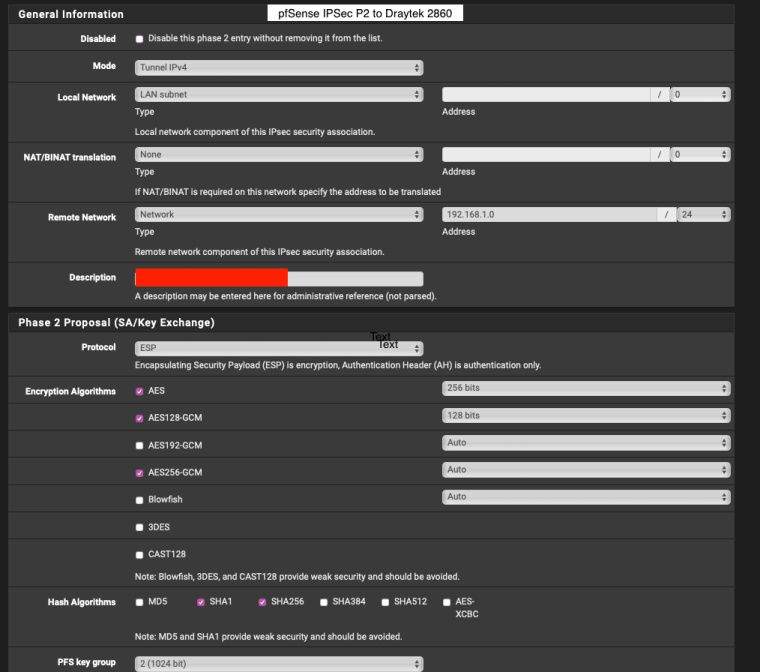
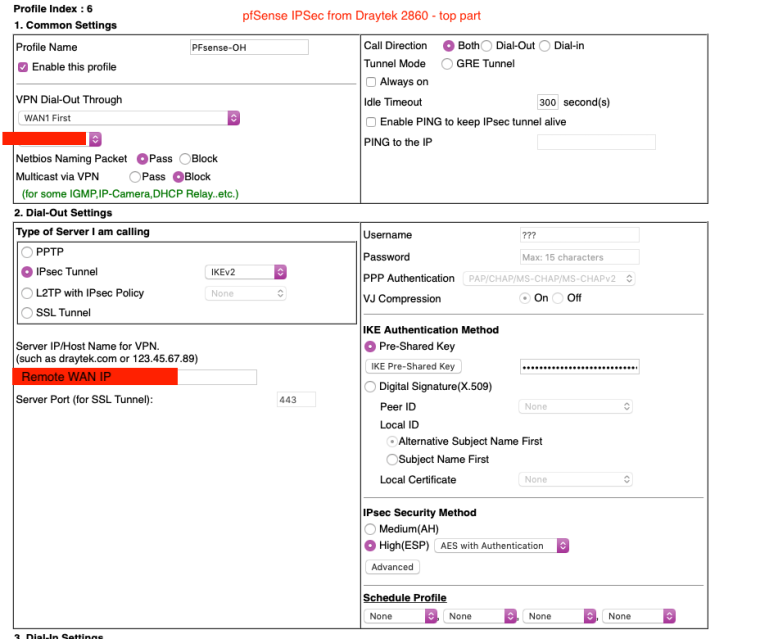
Would you like full screenshots for reference? -
Yes please. Might be helpful for someone else in the future.
Steve
-
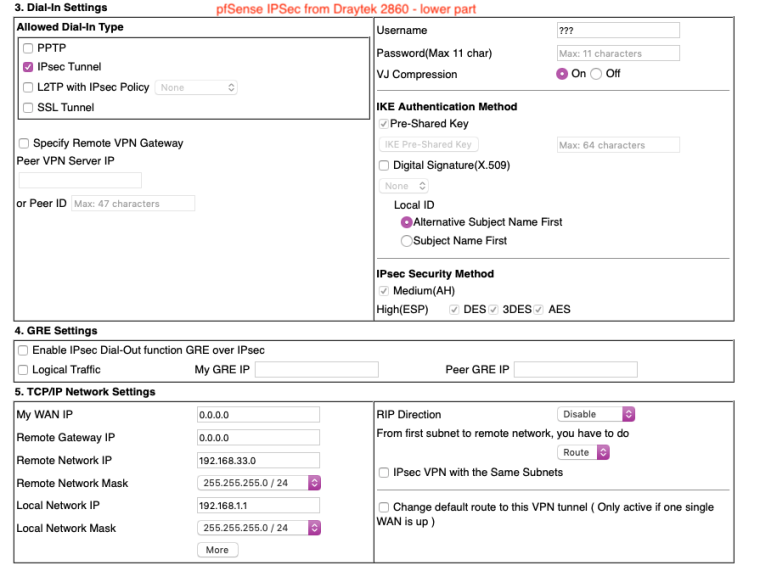
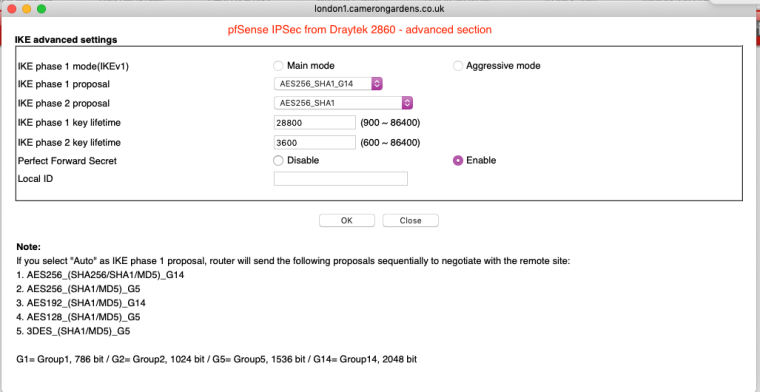
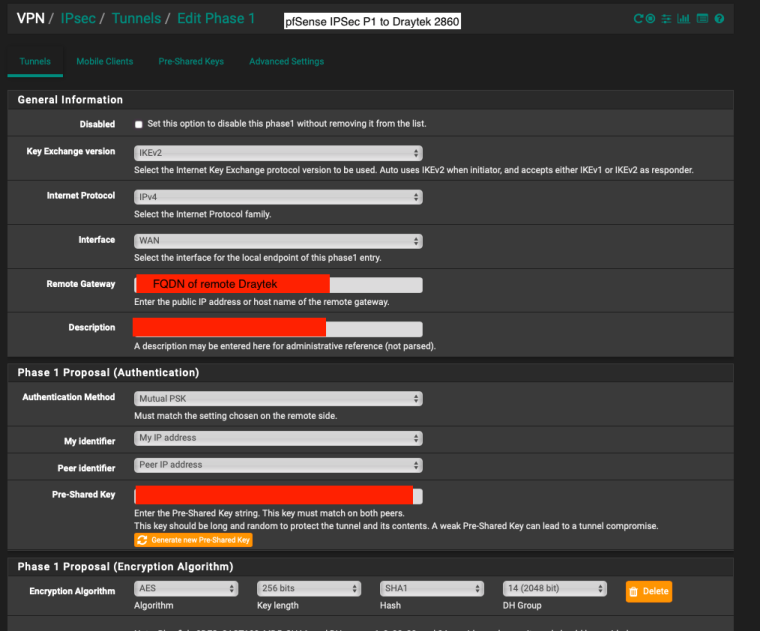
-
Hi all
I'm trying to setup a lan-to-lan VPN between Draytek and pfsense using IPSec, but I can't get it to work
I've copied the configuration suggested by orangehand on both ends, with no luck.
The only differences with orangehand's setup is that on the Draytek side I've set the call direction to dial-out, as I need the channel constantly on, and on the pfsense side, in the 'remote gateway' field I've set the external IP of the Draytek, not the FQDN, as I don't have a DDNS set up.Is there a complete guide on how to set this up, as I can't find a great deal on it online?
Thanks
Log details:
Dec 31 11:52:02 charon 10[IKE] <bypasslan|255> IKE_SA bypasslan[255] state change: CONNECTING => DESTROYING
Dec 31 11:52:02 charon 10[NET] <bypasslan|255> sending packet: from (pfsense_wan) [4500] to 1(draytek_wan)[7440] (76 bytes)
Dec 31 11:52:02 charon 10[ENC] <bypasslan|255> generating IKE_AUTH response 1 [ N(AUTH_FAILED) ]
Dec 31 11:52:02 charon 10[CFG] <bypasslan|255> no alternative config found
Dec 31 11:52:02 charon 10[CFG] <bypasslan|255> selected peer config 'bypasslan' unacceptable: non-matching authentication done
Dec 31 11:52:02 charon 10[CFG] <bypasslan|255> constraint requires public key authentication, but pre-shared key was used
Dec 31 11:52:02 charon 10[IKE] <bypasslan|255> authentication of '(draytek_lan)' with pre-shared key successful
Dec 31 11:52:02 charon 10[CFG] <bypasslan|255> selected peer config 'bypasslan' -
If you see it selecting bypasslan like that it's because no other config matches. You have a mismatch there. Do you have a more complete log?
Steve
-
Dec 31 12:23:34 charon 10[IKE] <bypasslan|373> IKE_SA bypasslan[373] state change: CONNECTING => DESTROYING
Dec 31 12:23:34 charon 10[NET] <bypasslan|373> sending packet: from (pfsense-wan)[4500] to (draytek-wan)[7440] (76 bytes)
Dec 31 12:23:34 charon 10[ENC] <bypasslan|373> generating IKE_AUTH response 1 [ N(AUTH_FAILED) ]
Dec 31 12:23:34 charon 10[CFG] <bypasslan|373> no alternative config found
Dec 31 12:23:34 charon 10[CFG] <bypasslan|373> selected peer config 'bypasslan' unacceptable: non-matching authentication done
Dec 31 12:23:34 charon 10[CFG] <bypasslan|373> constraint requires public key authentication, but pre-shared key was used
Dec 31 12:23:34 charon 10[IKE] <bypasslan|373> authentication of '(draytek-lan)' with pre-shared key successful
Dec 31 12:23:34 charon 10[CFG] <bypasslan|373> selected peer config 'bypasslan'
Dec 31 12:23:34 charon 10[CFG] <373> candidate "bypasslan", match: 1/1/24 (me/other/ike)
Dec 31 12:23:34 charon 10[CFG] <373> looking for peer configs matching (pfsense-wan)[%any]...(draytek-wan)[192.168.100.12]
Dec 31 12:23:34 charon 10[ENC] <373> parsed IKE_AUTH request 1 [ IDi AUTH SA TSi TSr ]
Dec 31 12:23:34 charon 10[NET] <373> received packet: from (draytek-wan)[7440] to (pfsense-wan)[4500] (204 bytes)
Dec 31 12:23:34 charon 10[NET] <373> sending packet: from (pfsense-wan)[500] to (draytek-wan)[7244] (440 bytes)
Dec 31 12:23:34 charon 10[ENC] <373> generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(MULT_AUTH) ]
Dec 31 12:23:34 charon 10[IKE] <373> remote host is behind NAT
Dec 31 12:23:34 charon 10[CFG] <373> selected proposal: IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048
Dec 31 12:23:34 charon 10[CFG] <373> configured proposals: IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048
Dec 31 12:23:34 charon 10[CFG] <373> received proposals: IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048
Dec 31 12:23:34 charon 10[CFG] <373> proposal matches
Dec 31 12:23:34 charon 10[CFG] <373> selecting proposal:
Dec 31 12:23:34 charon 10[IKE] <373> IKE_SA (unnamed)[373] state change: CREATED => CONNECTING
Dec 31 12:23:34 charon 10[IKE] <373> (draytek-wan) is initiating an IKE_SA
Dec 31 12:23:34 charon 10[CFG] <373> found matching ike config: (pfsense-wan)...(draytek-wan) with prio 3100
Dec 31 12:23:34 charon 10[CFG] <373> candidate: (pfsense-wan)...(draytek-wan), prio 3100
Dec 31 12:23:34 charon 10[CFG] <373> candidate: %any...%any, prio 24
Dec 31 12:23:34 charon 10[CFG] <373> looking for an IKEv2 config for (pfsense-wan)...(draytek-wan)
Dec 31 12:23:34 charon 10[ENC] <373> parsed IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) ]
Dec 31 12:23:34 charon 10[NET] <373> received packet: from (draytek-wan)[7244] to (pfsense-wan)[500] (416 bytes)
Dec 31 12:23:32 ipsec_starter 36044 'con1000' routed
Dec 31 12:23:32 charon 06[CHD] CHILD_SA con1000{2651} state change: CREATED => ROUTED
Dec 31 12:23:32 charon 06[CFG] configured proposals: ESP:AES_CBC_256/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_256_128/NO_EXT_SEQ, ESP:AES_GCM_16_128/NO_EXT_SEQ, ESP:AES_GCM_16_256/NO_EXT_SEQ, ESP:AES_GCM_12_256/NO_EXT_SEQ, ESP:AES_GCM_8_256/NO_EXT_SEQ
Dec 31 12:23:32 charon 06[CFG] received stroke: route 'con1000'
Dec 31 12:23:32 charon 07[CFG] added configuration 'con1000'
Dec 31 12:23:32 charon 07[CFG] keyexchange=ikev2
Dec 31 12:23:32 charon 07[CFG] mediation=no
Dec 31 12:23:32 charon 07[CFG] sha256_96=no
Dec 31 12:23:32 charon 07[CFG] dpdaction=3
Dec 31 12:23:32 charon 07[CFG] dpdtimeout=60
Dec 31 12:23:32 charon 07[CFG] dpddelay=10
Dec 31 12:23:32 charon 07[CFG] esp=aes256-sha1-modp1024,aes256-sha256-modp1024,aes128gcm128-sha1-modp1024,aes128gcm128-sha256-modp1024,aes256gcm128-sha1-modp1024,aes256gcm128-sha256-modp1024,aes256gcm96-sha1-modp1024,aes256gcm96-sha256-modp1024,aes256gcm64-sha1-modp1024,aes256gcm64-sha256-modp1024!
Dec 31 12:23:32 charon 07[CFG] ike=aes256-sha1-modp2048!
Dec 31 12:23:32 charon 07[CFG] rightid=(draytek-wan)
Dec 31 12:23:32 charon 07[CFG] rightauth=psk
Dec 31 12:23:32 charon 07[CFG] rightsubnet=(draytek-lan)/24
Dec 31 12:23:32 charon 07[CFG] right=(draytek-wan)
Dec 31 12:23:32 charon 07[CFG] leftid=(pfsense-wan)
Dec 31 12:23:32 charon 07[CFG] leftauth=psk
Dec 31 12:23:32 charon 07[CFG] leftsubnet=(pfsense-lan)/24
Dec 31 12:23:32 charon 07[CFG] left=(pfsense-wan)
Dec 31 12:23:32 charon 07[CFG] conn con1000
Dec 31 12:23:32 charon 07[CFG] received stroke: add connection 'con1000'
Dec 31 12:23:32 ipsec_starter 36044 'bypasslan' shunt PASS policy installed
Dec 31 12:23:32 charon 06[CFG] received stroke: route 'bypasslan'
Dec 31 12:23:32 charon 08[CFG] added configuration 'bypasslan'
Dec 31 12:23:32 charon 08[CFG] mediation=no
Dec 31 12:23:32 charon 08[CFG] sha256_96=no
Dec 31 12:23:32 charon 08[CFG] dpdtimeout=150
Dec 31 12:23:32 charon 08[CFG] dpddelay=30
Dec 31 12:23:32 charon 08[CFG] rightsubnet=(pfsense-lan)/24
Dec 31 12:23:32 charon 08[CFG] right=%any
Dec 31 12:23:32 charon 08[CFG] leftsubnet=(pfsense-lan)/24
Dec 31 12:23:32 charon 08[CFG] left=%any
Dec 31 12:23:32 charon 08[CFG] conn bypasslan
Dec 31 12:23:32 charon 08[CFG] received stroke: add connection 'bypasslan'
Dec 31 12:23:32 charon 06[CFG] deleted connection 'con1000'
Dec 31 12:23:32 charon 06[CFG] received stroke: delete connection 'con1000'
Dec 31 12:23:32 ipsec_starter 36044 trap policy 'con1000' unrouted
Dec 31 12:23:32 charon 08[CHD] CHILD_SA con1000{2650} state change: ROUTED => DESTROYING
Dec 31 12:23:32 charon 08[CFG] received stroke: unroute 'con1000'
Dec 31 12:23:32 charon 06[CFG] deleted connection 'bypasslan'
Dec 31 12:23:32 charon 06[CFG] received stroke: delete connection 'bypasslan'
Dec 31 12:23:32 ipsec_starter 36044 shunt policy 'bypasslan' uninstalled
Dec 31 12:23:32 charon 05[CFG] received stroke: unroute 'bypasslan'
Dec 31 12:23:32 charon 07[CFG] rereading crls from '/usr/local/etc/ipsec.d/crls'
Dec 31 12:23:32 charon 07[CFG] rereading attribute certificates from '/usr/local/etc/ipsec.d/acerts'
Dec 31 12:23:32 charon 07[CFG] rereading ocsp signer certificates from '/usr/local/etc/ipsec.d/ocspcerts'
Dec 31 12:23:32 charon 07[CFG] rereading aa certificates from '/usr/local/etc/ipsec.d/aacerts'
Dec 31 12:23:32 charon 07[CFG] rereading ca certificates from '/usr/local/etc/ipsec.d/cacerts'
Dec 31 12:23:32 charon 07[CFG] loaded IKE secret for %any (draytek-wan)
Dec 31 12:23:32 charon 07[CFG] loading secrets from '/var/etc/ipsec/ipsec.secrets'
Dec 31 12:23:32 charon 07[CFG] rereading secrets
Dec 31 12:23:20 ipsec_starter 36044 'con1000' routed
Dec 31 12:23:20 charon 08[CHD] CHILD_SA con1000{2650} state change: CREATED => ROUTED
Dec 31 12:23:20 charon 08[CFG] configured proposals: ESP:AES_CBC_256/HMAC_SHA1_96/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_256_128/NO_EXT_SEQ, ESP:AES_GCM_16_128/NO_EXT_SEQ, ESP:AES_GCM_16_256/NO_EXT_SEQ, ESP:AES_GCM_12_256/NO_EXT_SEQ, ESP:AES_GCM_8_256/NO_EXT_SEQ
Dec 31 12:23:20 charon 08[CFG] received stroke: route 'con1000'
Dec 31 12:23:20 charon 07[CFG] added configuration 'con1000'
Dec 31 12:23:20 charon 07[CFG] keyexchange=ikev2
Dec 31 12:23:20 charon 07[CFG] mediation=no
Dec 31 12:23:20 charon 07[CFG] sha256_96=no
Dec 31 12:23:20 charon 07[CFG] dpdaction=3
Dec 31 12:23:20 charon 07[CFG] dpdtimeout=60
Dec 31 12:23:20 charon 07[CFG] dpddelay=10
Dec 31 12:23:20 charon 07[CFG] esp=aes256-sha1-modp1024,aes256-sha256-modp1024,aes128gcm128-sha1-modp1024,aes128gcm128-sha256-modp1024,aes256gcm128-sha1-modp1024,aes256gcm128-sha256-modp1024,aes256gcm96-sha1-modp1024,aes256gcm96-sha256-modp1024,aes256gcm64-sha1-modp1024,aes256gcm64-sha256-modp1024!
Dec 31 12:23:20 charon 07[CFG] ike=aes256-sha1-modp2048!
Dec 31 12:23:20 charon 07[CFG] rightid=(draytek-wan)
Dec 31 12:23:20 charon 07[CFG] rightauth=psk
Dec 31 12:23:20 charon 07[CFG] rightsubnet=(draytek-lan)/24
Dec 31 12:23:20 charon 07[CFG] right=(draytek-wan)
Dec 31 12:23:20 charon 07[CFG] leftid=(pfsense-wan)
Dec 31 12:23:20 charon 07[CFG] leftauth=psk
Dec 31 12:23:20 charon 07[CFG] leftsubnet=(pfsense-lan)/24
Dec 31 12:23:20 charon 07[CFG] left=(pfsense-wan)
Dec 31 12:23:20 charon 07[CFG] conn con1000
Dec 31 12:23:20 charon 07[CFG] received stroke: add connection 'con1000'
Dec 31 12:23:20 ipsec_starter 36044 'bypasslan' shunt PASS policy installed
Dec 31 12:23:20 charon 06[CFG] received stroke: route 'bypasslan'
Dec 31 12:23:20 charon 08[CFG] added configuration 'bypasslan'
Dec 31 12:23:20 charon 08[CFG] mediation=no
Dec 31 12:23:20 charon 08[CFG] sha256_96=no
Dec 31 12:23:20 charon 08[CFG] dpdtimeout=150
Dec 31 12:23:20 charon 08[CFG] dpddelay=30
Dec 31 12:23:20 charon 08[CFG] rightsubnet=(pfsense-lan)/24
Dec 31 12:23:20 charon 08[CFG] right=%any
Dec 31 12:23:20 charon 08[CFG] leftsubnet=(pfsense-lan)/24
Dec 31 12:23:20 charon 08[CFG] left=%any
Dec 31 12:23:20 charon 08[CFG] conn bypasslan
Dec 31 12:23:20 charon 08[CFG] received stroke: add connection 'bypasslan'
Dec 31 12:23:20 charon 06[CFG] deleted connection 'con1000'
Dec 31 12:23:20 charon 06[CFG] received stroke: delete connection 'con1000'
Dec 31 12:23:20 ipsec_starter 36044 trap policy 'con1000' unrouted
Dec 31 12:23:20 charon 08[CHD] CHILD_SA con1000{2649} state change: ROUTED => DESTROYING
Dec 31 12:23:20 charon 08[CFG] received stroke: unroute 'con1000'
Dec 31 12:23:20 charon 05[CFG] deleted connection 'bypasslan'
Dec 31 12:23:20 charon 05[CFG] received stroke: delete connection 'bypasslan'
Dec 31 12:23:20 ipsec_starter 36044 shunt policy 'bypasslan' uninstalled
Dec 31 12:23:20 charon 06[CFG] received stroke: unroute 'bypasslan'
Dec 31 12:23:20 charon 08[CFG] rereading crls from '/usr/local/etc/ipsec.d/crls'
Dec 31 12:23:20 charon 08[CFG] rereading attribute certificates from '/usr/local/etc/ipsec.d/acerts'
Dec 31 12:23:20 charon 08[CFG] rereading ocsp signer certificates from '/usr/local/etc/ipsec.d/ocspcerts'
Dec 31 12:23:20 charon 08[CFG] rereading aa certificates from '/usr/local/etc/ipsec.d/aacerts'
Dec 31 12:23:20 charon 08[CFG] rereading ca certificates from '/usr/local/etc/ipsec.d/cacerts'
Dec 31 12:23:20 charon 08[CFG] loaded IKE secret for %any 1(draytek-wan)
Dec 31 12:23:20 charon 08[CFG] loading secrets from '/var/etc/ipsec/ipsec.secrets'
Dec 31 12:23:20 charon 08[CFG] rereading secrets -
@tech_support_ said in Has anyone got a VPN to a Draytek working?:
Dec 31 12:23:34 charon 10[CFG] <373> looking for peer configs matching (pfsense-wan)[%any]...(draytek-wan)[192.168.100.12]
The Draytek is sending it's internal IP as the indentifier. So if pfSense is set to use 'Peer IP Address' that will be the public IP and will not match. Either set the Draytek to send it's public IP as it's identifer or set pfSense to use 'IP Address (192.168.100.12)' as the peer identifier.
Steve
-
@stephenw10 said in Has anyone got a VPN to a Draytek working?:
192.168.100.12
That was it, you're a legend!
A happy new year to you Steve
-
And to you.

-
@stephenw10 ,
I have a similar issue when building a tunnel from ASA to Draytek 2862 with firmware version 3.9.4.1.Logs showing IKE link timeout: state linking.
Tunnel is IKEv1.
VPN configs are similar.
PSK confirmed multiple times. -
So not pfSense at either end?
Kinda limited in what we can do then. Have you considered using pfSense?

Or calling Cisco/Draytek support!But in general you need to check the logs on the end that is refusing the connection to why it is. Then correct that. There will be a config mismatch, IPSec is fairly standard across platforms especially IKEv1.
Steve
-
You should not really have an issue with a Draytek to ASA VPN, we have many of those running on multiple ASA firmwares and 2820s, 2860s (v3.9.4.1), 2862s, 29xx etc.
I can't specifically tell you how, as I am not the Cisco guy :-) If it helps most of ours run on IKEv1 with 3DES with auth, no PFS. We also run all the tunnels outbound on the Draytek to the Cisco., with P1 28800 and P2 3600, which is the Draytek default.
The solution is reasonably well documented on the Draytek knowledge bases and forums, and your Draytek reseller should have access to Draytek tech support, who are pretty helpful most of the time if you are clear on what the problem is.
Not wishing to undermine stephenw10 on the pfSense sell ;-), we have had no luck really in getting Draytek to play with pfSense running in Azure. Despite our best efforts we cannot get a stable solution. We can get pfSense to work with ASA all day long though, so it depends which end you might switch out for a pfSense.
Copyright 2025 Rubicon Communications LLC (Netgate). All rights reserved.