-
(and Draytek is set to Dial Out, always on)
-
I assume the Draytek logs are in reverse order again?
Did you change to IKEv2 and DH group2 at both ends? pfSense will use IKEv2 if it is initiating and it's set to auto.
The pfSense failure log will probably be more useful here, obviously we are far more familiar with it.
However I would say it's most likely an identifier mismatch looking at those logs. IKEv2 has a much larger choice of identifier types. It looks like the Draytek has accepted whatever pfSense is sending as it's showing SA established but pfSene then sends an authentication failure message.
Since you're using public IPs at both ends if the identifiers are still set to 'my IP' and 'peer IP' that should work.
Steve
-
Yes both ends were changed, whilst I had the Draytek guy remoted into my Mac
(The Draytek is set to dial out, not both, if that matters)Latest pfsense log entries are:
Feb 27 16:23:01 charon 11[CFG] <30980> found matching ike config: 81.143.205.132...88.97.12.47 with prio 3100
Feb 27 16:23:01 charon 11[IKE] <30980> 88.97.12.47 is initiating an IKE_SA
Feb 27 16:23:01 charon 11[IKE] <30980> IKE_SA (unnamed)[30980] state change: CREATED => CONNECTING
Feb 27 16:23:01 charon 11[CFG] <30980> selecting proposal:
Feb 27 16:23:01 charon 11[CFG] <30980> proposal matches
Feb 27 16:23:01 charon 11[CFG] <30980> received proposals: IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
Feb 27 16:23:01 charon 11[CFG] <30980> configured proposals: IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
Feb 27 16:23:01 charon 11[CFG] <30980> selected proposal: IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
Feb 27 16:23:01 charon 11[ENC] <30980> generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(MULT_AUTH) ]
Feb 27 16:23:01 charon 11[NET] <30980> sending packet: from 81.143.205.132[500] to 88.97.12.47[500] (312 bytes)
Feb 27 16:23:01 charon 11[NET] <30980> received packet: from 88.97.12.47[500] to 81.143.205.132[500] (204 bytes)
Feb 27 16:23:01 charon 11[ENC] <30980> parsed IKE_AUTH request 1 [ IDi AUTH SA TSi TSr ]
Feb 27 16:23:01 charon 11[CFG] <30980> looking for peer configs matching 81.143.205.132[%any]...88.97.12.47[88.97.12.47]
Feb 27 16:23:01 charon 11[CFG] <30980> candidate "bypasslan", match: 1/1/24 (me/other/ike)
Feb 27 16:23:01 charon 11[CFG] <30980> candidate "con3000", match: 1/20/3100 (me/other/ike)
Feb 27 16:23:01 charon 11[CFG] <30980> ignore candidate 'bypasslan' without matching IKE proposal
Feb 27 16:23:01 charon 11[CFG] <con3000|30980> selected peer config 'con3000'
Feb 27 16:23:01 charon 11[IKE] <con3000|30980> tried 1 shared key for '%any' - '88.97.12.47', but MAC mismatched
Feb 27 16:23:01 charon 11[ENC] <con3000|30980> generating IKE_AUTH response 1 [ N(AUTH_FAILED) ]
Feb 27 16:23:01 charon 11[NET] <con3000|30980> sending packet: from 81.143.205.132[500] to 88.97.12.47[500] (76 bytes)
Feb 27 16:23:01 charon 11[IKE] <con3000|30980> IKE_SA con3000[30980] state change: CONNECTING => DESTROYING -
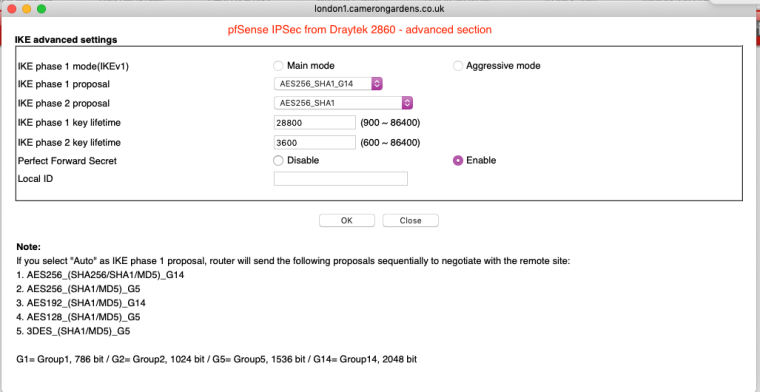
Here is the draytek end - there appears to be no peerID setting that end if that might be relevant?
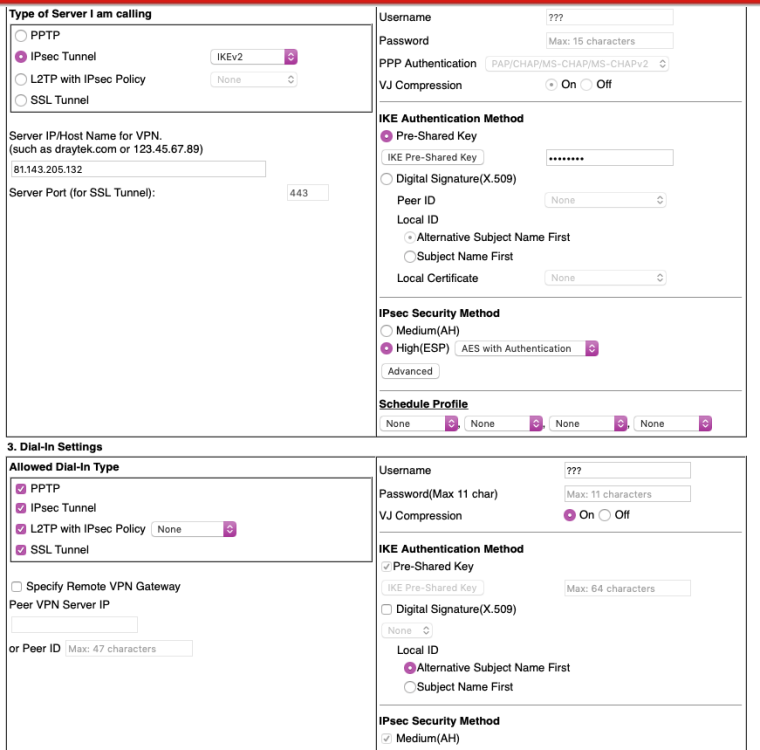
-
The top and bottom of the previous screenshot:
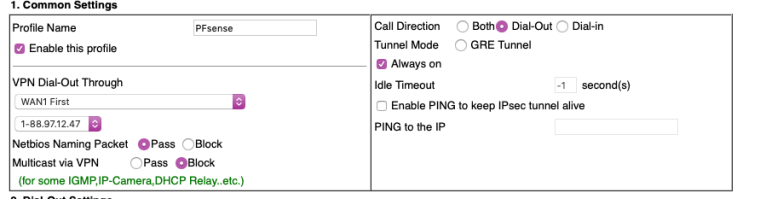
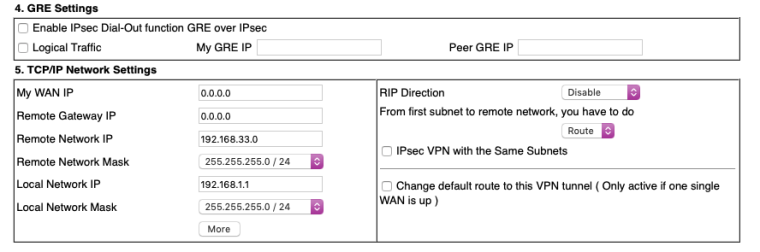
-
Ok so not an identifier mismatch, thay are sending their IP as identifier shown in [ ]
looking for peer configs matching 81.143.205.132[%any]...88.97.12.47[88.97.12.47]It still looks like the preshared key is wrong:
tried 1 shared key for '%any' - '88.97.12.47', but MAC mismatchedI would test it by using a super simple key that cannot me typo'd or translated like
12345. Move to a better key once it connects with that.We can't see the actual encryption settings there, I assume they are under that advanced button. If the HMAC didn't match there I would expect it to fail with a proposal error. It was matching previously for IKEv1 but worth checking.
Steve
-
Are you using an especially long PreSharedKey? The maximum ley length is related to auth hash used and you are using SHA1 which limits it to 64B (I think).
Steve
-
Changed PSK to 12345, saved and applied at both ends
Draytek syslog (latest at top):
2019-02-27 17:41:02 ## IKEv2 DBG : INFORMATIONAL OUT : Sending IKEv2 Delete IKE SA request, deleting #3373
2019-02-27 17:41:02 [IPSEC][L2L][6:PFsense][@81.143.205.132] IKE link timeout: state linking
2019-02-27 17:40:54 IKE <==, Next Payload=ISAKMP_NEXT_HASH, Exchange Type = 0x5, Message ID = 0x12ad535f
2019-02-27 17:40:54 IKE ==>, Next Payload=ISAKMP_NEXT_HASH, Exchange Type = 0x5, Message ID = 0x77b5b4a4
2019-02-27 17:40:54 IKE <==, Next Payload=ISAKMP_NEXT_HASH, Exchange Type = 0x5, Message ID = 0x3977f965
2019-02-27 17:40:54 IKE ==>, Next Payload=ISAKMP_NEXT_HASH, Exchange Type = 0x5, Message ID = 0x371c750d
2019-02-27 17:40:49 ## IKEv2 DBG : IKESA inR2 : Can't decrypt message
2019-02-27 17:40:49 ## IKEv2 DBG : Missing payload : IKEv2_NP_v2SA+0x1848
2019-02-27 17:40:49 ## IKEv2 DBG : Received IKEv2 Notify IKEv2_AUTHENTICATION_FAILED[24]
2019-02-27 17:40:49 ## IKEv2 DBG : Recv IKEv2_AUTH[35] Reply from 81.143.205.132, Peer is IKEv2 Responder
2019-02-27 17:40:49 ## IKEv2 DBG : Process Packet : #3373 IKE SA Established, REPLACE after 21150 seconds
2019-02-27 17:40:49 ## IKEv2 DBG : IKESA inR1_outI2 : Create Child SA #3374, IKE SA is #3373
2019-02-27 17:40:49 ## IKEv2 DBG : IKESA inR1_outI2 : Receive Notify [16404], ignore it
2019-02-27 17:40:49 ## IKEv2 DBG : IKESA inR1_outI2 : Receive Notify IKEv2_NAT_DETECTION_DESTINATION_IP[16389]
2019-02-27 17:40:49 ## IKEv2 DBG : IKESA inR1_outI2 : Receive Notify IKEv2_NAT_DETECTION_SOURCE_IP[16388]
2019-02-27 17:40:49 ## IKEv2 DBG : Received IKEv2 Notify [16404]
2019-02-27 17:40:49 ## IKEv2 DBG : Received IKEv2 Notify IKEv2_NAT_DETECTION_DESTINATION_IP[16389]
2019-02-27 17:40:49 ## IKEv2 DBG : Received IKEv2 Notify IKEv2_NAT_DETECTION_SOURCE_IP[16388]
2019-02-27 17:40:49 ## IKEv2 DBG : Recv IKEv2_SA_INIT[34] Reply from 81.143.205.132, Peer is IKEv2 Responder
2019-02-27 17:40:49 ## IKEv2 DBG : IKESA outI1 : Create IKE SA #3373 Profile Index 0
2019-02-27 17:40:49 Dialing Node6 (PFsense) : 81.143.205.132
2019-02-27 17:40:46 ## IKEv2 DBG : INFORMATIONAL OUT : Sending IKEv2 Delete IKE SA request, deleting #3371
2019-02-27 17:40:46 [IPSEC][L2L][6:PFsense][@81.143.205.132] IKE link timeout: state linking
2019-02-27 17:40:33 ## IKEv2 DBG : IKESA inR2 : Can't decrypt message
2019-02-27 17:40:33 ## IKEv2 DBG : Missing payload : IKEv2_NP_v2SA+0x1848
2019-02-27 17:40:33 ## IKEv2 DBG : Received IKEv2 Notify IKEv2_AUTHENTICATION_FAILED[24]
2019-02-27 17:40:33 ## IKEv2 DBG : Recv IKEv2_AUTH[35] Reply from 81.143.205.132, Peer is IKEv2 Responder
2019-02-27 17:40:33 ## IKEv2 DBG : Process Packet : #3371 IKE SA Established, REPLACE after 21572 seconds
2019-02-27 17:40:33 ## IKEv2 DBG : IKESA inR1_outI2 : Create Child SA #3372, IKE SA is #3371pfSense log:
Feb 27 17:42:27 charon 15[CFG] <31333> looking for an IKEv2 config for 81.143.205.132...88.97.12.47
Feb 27 17:42:27 charon 15[CFG] <31333> candidate: %any...%any, prio 24
Feb 27 17:42:27 charon 15[CFG] <31333> candidate: 81.143.205.132...88.97.12.47, prio 3100
Feb 27 17:42:27 charon 15[CFG] <31333> found matching ike config: 81.143.205.132...88.97.12.47 with prio 3100
Feb 27 17:42:27 charon 15[IKE] <31333> 88.97.12.47 is initiating an IKE_SA
Feb 27 17:42:27 charon 15[IKE] <31333> IKE_SA (unnamed)[31333] state change: CREATED => CONNECTING
Feb 27 17:42:27 charon 15[CFG] <31333> selecting proposal:
Feb 27 17:42:27 charon 15[CFG] <31333> proposal matches
Feb 27 17:42:27 charon 15[CFG] <31333> received proposals: IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
Feb 27 17:42:27 charon 15[CFG] <31333> configured proposals: IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
Feb 27 17:42:27 charon 15[CFG] <31333> selected proposal: IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
Feb 27 17:42:27 charon 15[ENC] <31333> generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(MULT_AUTH) ]
Feb 27 17:42:27 charon 15[NET] <31333> sending packet: from 81.143.205.132[500] to 88.97.12.47[500] (312 bytes)
Feb 27 17:42:27 charon 15[NET] <31333> received packet: from 88.97.12.47[500] to 81.143.205.132[500] (204 bytes)
Feb 27 17:42:27 charon 15[ENC] <31333> parsed IKE_AUTH request 1 [ IDi AUTH SA TSi TSr ]
Feb 27 17:42:27 charon 15[CFG] <31333> looking for peer configs matching 81.143.205.132[%any]...88.97.12.47[88.97.12.47]
Feb 27 17:42:27 charon 15[CFG] <31333> candidate "bypasslan", match: 1/1/24 (me/other/ike)
Feb 27 17:42:27 charon 15[CFG] <31333> candidate "con3000", match: 1/20/3100 (me/other/ike)
Feb 27 17:42:27 charon 15[CFG] <31333> ignore candidate 'bypasslan' without matching IKE proposal
Feb 27 17:42:27 charon 15[CFG] <con3000|31333> selected peer config 'con3000'
Feb 27 17:42:27 charon 15[IKE] <con3000|31333> tried 1 shared key for '%any' - '88.97.12.47', but MAC mismatched
Feb 27 17:42:27 charon 15[ENC] <con3000|31333> generating IKE_AUTH response 1 [ N(AUTH_FAILED) ]
Feb 27 17:42:27 charon 15[NET] <con3000|31333> sending packet: from 81.143.205.132[500] to 88.97.12.47[500] (76 bytes)
Feb 27 17:42:27 charon 15[IKE] <con3000|31333> IKE_SA con3000[31333] state change: CONNECTING => DESTROYING
Feb 27 17:42:43 charon 15[NET] <31334> received packet: from 88.97.12.47[500] to 81.143.205.132[500] (288 bytes)
Feb 27 17:42:43 charon 15[ENC] <31334> parsed IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) ]
Feb 27 17:42:43 charon 15[CFG] <31334> looking for an IKEv2 config for 81.143.205.132...88.97.12.47
Feb 27 17:42:43 charon 15[CFG] <31334> candidate: %any...%any, prio 24
Feb 27 17:42:43 charon 15[CFG] <31334> candidate: 81.143.205.132...88.97.12.47, prio 3100
Feb 27 17:42:43 charon 15[CFG] <31334> found matching ike config: 81.143.205.132...88.97.12.47 with prio 3100
Feb 27 17:42:43 charon 15[IKE] <31334> 88.97.12.47 is initiating an IKE_SA
Feb 27 17:42:43 charon 15[IKE] <31334> IKE_SA (unnamed)[31334] state change: CREATED => CONNECTING
Feb 27 17:42:43 charon 15[CFG] <31334> selecting proposal:
Feb 27 17:42:43 charon 15[CFG] <31334> proposal matches
Feb 27 17:42:43 charon 15[CFG] <31334> received proposals: IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
Feb 27 17:42:43 charon 15[CFG] <31334> configured proposals: IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
Feb 27 17:42:43 charon 15[CFG] <31334> selected proposal: IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
Feb 27 17:42:43 charon 15[ENC] <31334> generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(MULT_AUTH) ]
Feb 27 17:42:43 charon 15[NET] <31334> sending packet: from 81.143.205.132[500] to 88.97.12.47[500] (312 bytes)
Feb 27 17:42:43 charon 15[NET] <31334> received packet: from 88.97.12.47[500] to 81.143.205.132[500] (204 bytes)
Feb 27 17:42:43 charon 15[ENC] <31334> parsed IKE_AUTH request 1 [ IDi AUTH SA TSi TSr ]
Feb 27 17:42:43 charon 15[CFG] <31334> looking for peer configs matching 81.143.205.132[%any]...88.97.12.47[88.97.12.47]
Feb 27 17:42:43 charon 15[CFG] <31334> candidate "bypasslan", match: 1/1/24 (me/other/ike)
Feb 27 17:42:43 charon 15[CFG] <31334> candidate "con3000", match: 1/20/3100 (me/other/ike)
Feb 27 17:42:43 charon 15[CFG] <31334> ignore candidate 'bypasslan' without matching IKE proposal
Feb 27 17:42:43 charon 15[CFG] <con3000|31334> selected peer config 'con3000'
Feb 27 17:42:43 charon 15[IKE] <con3000|31334> tried 1 shared key for '%any' - '88.97.12.47', but MAC mismatched
Feb 27 17:42:43 charon 15[ENC] <con3000|31334> generating IKE_AUTH response 1 [ N(AUTH_FAILED) ]
Feb 27 17:42:43 charon 15[NET] <con3000|31334> sending packet: from 81.143.205.132[500] to 88.97.12.47[500] (76 bytes)
Feb 27 17:42:43 charon 15[IKE] <con3000|31334> IKE_SA con3000[31334] state change: CONNECTING => DESTROYING -
Sorry - missed your key length Q; no - previous psk was testtest - the last logs were 12345
-
Hmm, curious.
Is this the only tunnel at each end?
Does either end have more than one WAN?
Can we see the config at the pfSense end?
Steve
-
@orangehand said in Has anyone got a VPN to a Draytek working?:
looking for peer configs matching 81.143.205.132[%any]...88.97.12.47[88.97.12.47]
Ok in fact this could be an identifier issue. It looks like the Draytek is sending 'any' as the identifier for pfSense. What is it actually set to in pfSense?
I don't see a place to specify a peer ID in the Draytek settings other than the 'dial-in' section but you might try adding it there.
Steve
-
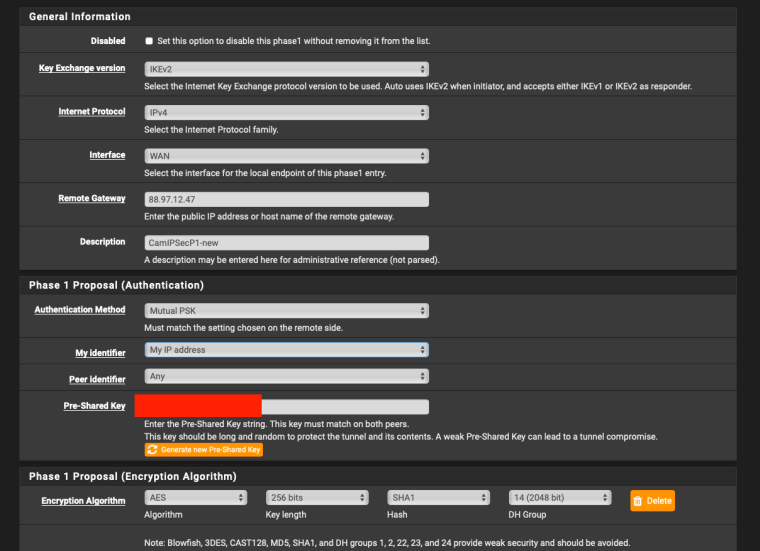
-
In dial in settings you mean the username field? What would I put there please?
-
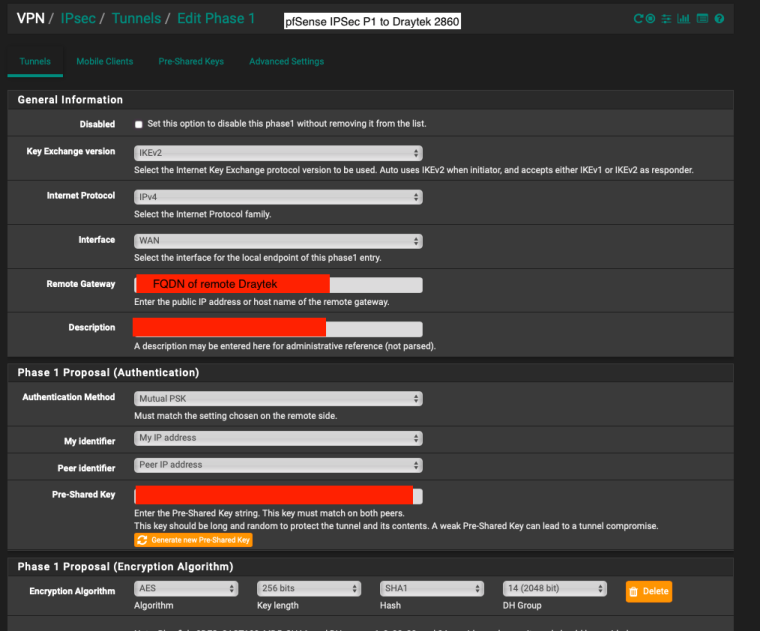
Ok the Draytek is sending it's own IP as an identifier but 'any' for the pfSense end. So in pfSense it should be the opposite; 'any' for My Identifier and 'peer IP' for Peer Identifier.
But better would be to set an Identifier in the Draytek. The only place in the screenshot I see to do that is the 'Peer ID' filed in the dial-in settings. Try that. See if it changes what is shown in the pfSense logs. You want it to show:
looking for peer configs matching 81.143.205.132[81.143.205.132]...88.97.12.47[88.97.12.47]Then set My IP and Peer IP as the identifiers in pfSense to match.
Steve
-
That worked, many many thanks Steve
-
Ah, great. Were you able to get the Draytek to send an IP as identifier or did you have to stick with 'any' as the local identifier in pfSense?
Steve
-
pfSense (my) end I used My identifier: My IP Address and Peer Identifier: Peer IP address
Would you like full screenshots for reference? -
Yes please. Might be helpful for someone else in the future.
Steve
-
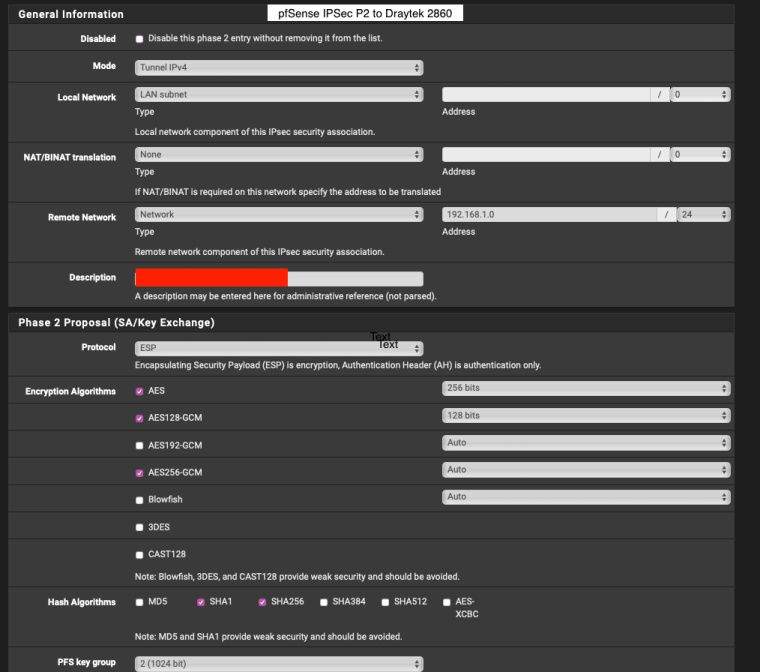
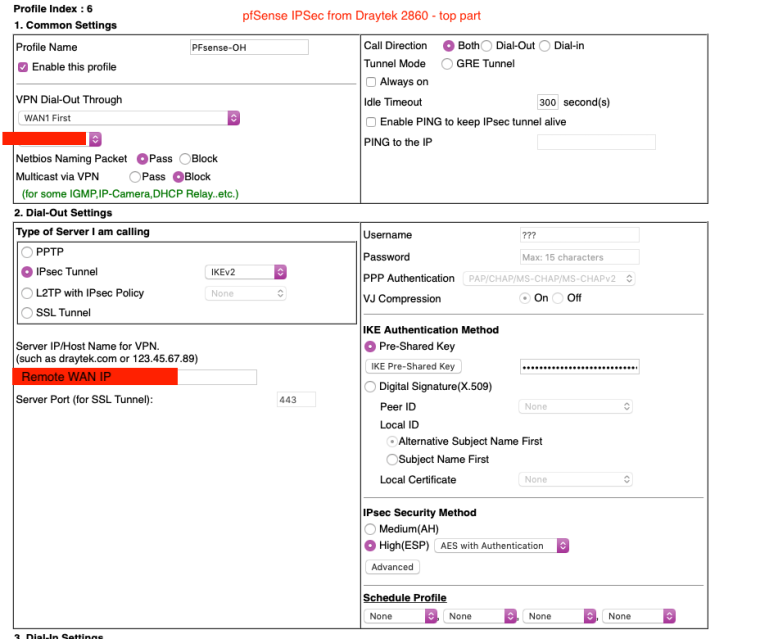
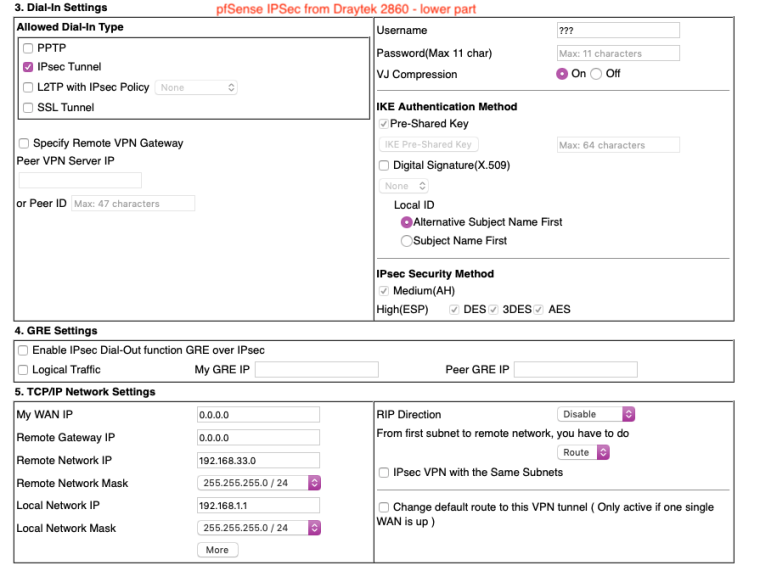
-
Hi all
I'm trying to setup a lan-to-lan VPN between Draytek and pfsense using IPSec, but I can't get it to work
I've copied the configuration suggested by orangehand on both ends, with no luck.
The only differences with orangehand's setup is that on the Draytek side I've set the call direction to dial-out, as I need the channel constantly on, and on the pfsense side, in the 'remote gateway' field I've set the external IP of the Draytek, not the FQDN, as I don't have a DDNS set up.Is there a complete guide on how to set this up, as I can't find a great deal on it online?
Thanks
Log details:
Dec 31 11:52:02 charon 10[IKE] <bypasslan|255> IKE_SA bypasslan[255] state change: CONNECTING => DESTROYING
Dec 31 11:52:02 charon 10[NET] <bypasslan|255> sending packet: from (pfsense_wan) [4500] to 1(draytek_wan)[7440] (76 bytes)
Dec 31 11:52:02 charon 10[ENC] <bypasslan|255> generating IKE_AUTH response 1 [ N(AUTH_FAILED) ]
Dec 31 11:52:02 charon 10[CFG] <bypasslan|255> no alternative config found
Dec 31 11:52:02 charon 10[CFG] <bypasslan|255> selected peer config 'bypasslan' unacceptable: non-matching authentication done
Dec 31 11:52:02 charon 10[CFG] <bypasslan|255> constraint requires public key authentication, but pre-shared key was used
Dec 31 11:52:02 charon 10[IKE] <bypasslan|255> authentication of '(draytek_lan)' with pre-shared key successful
Dec 31 11:52:02 charon 10[CFG] <bypasslan|255> selected peer config 'bypasslan'
Copyright 2025 Rubicon Communications LLC (Netgate). All rights reserved.