Does anyone have a link to a good site for Multi WAN
-
multiple wans via what interfaces and dhcp address on these?
You can not do static IPs on interface in the same netblock..
-
@lucndevr said in Does anyone have a link to a good site for Multi WAN:
can you link me ...
-
The firewall must serve multiple customers
The firewall must give each customers their own external IP
The firewall must prevent each of the customers from seeing each others’ networks
The firewall must allow us to configure network services for each customer (DHCP, DNS, etc)Can I accomplish this with pfsense?
-
Yes to all your questions..
The simple solution would be if you had a routed public network.. And then sub net that down for each tenants to their own vlan... This will cost you some loss of address space as you break up the larger network into smaller vlans.. But makes it really simple to manage.
If you say have a /24 routed to you, you can break that up into 64 /30's or 32 /29's to give the tenants the number of IPs they require.. And how many tenants you have?
Other method would be to just use a private vlan.. This is a vlan that where all clients are in the same L2/L3 space but you control at the switch infrastructure which Ports can talk to which others or none at all.
Control of dhcp and or dns can be handled via reservations for the tenants devices via reservations where you could hand out dns XYZ to mac address ABC, while other info is given to mac address DFG, etc.
Or you just use different local vlans for each tenant say 192.168.1/24 for A, 192.168.2/24 for B tenant.. And then just use 1:1 natting for their stuff from your public IP space with VIPs, etc. etc..
There are many ways to skins this specific cat - just need to know the breed and the full details and the skill set of the persons going to run this whole thing along with the other equipment going to be used to know the best way..
Are the tenants going to have their own firewall/router connected to you? Or are their devices going to be connected to pfsense without any firewall/router between?
-
@johnpoz
Still not sure if the public addresses are routed to me or not. I want 4 separate networks and on different port on my server/pfsense firewall so when a costumer comes in I can just plugin a utp cable to a switch and than they have there own separate lan and public network.sorry for calling them tenants their customers.
BTW sorry for my English im a Dutch trainee, thanks for helping though.
-
I already have suricata running on it could that be a problem its not blocking hosts. only some packets
-
Why would you be running IPS out of the gate is beyond me...
If you don't even know if your IP space is routed to you are directly attached even - why are you even involved in such a project?
Is the public IPv4 space assigned to you and you have 1 of these IPs on pfsense wan itself? Then its most likely NOT routed... If you have a different IPv4 network on your wan then this IPv4 space you have with the IPs you want to give to your clients/customers/tenants then its routed..
Yes you can create 4 different networks/vlans be they directly connected to a physical port on pfsense or a vlan that is tagged, etc.
The EASY!!! Solution is to your problem is if the IP space is routed to you! How many IPs do you have? What is the mask /??
@lucndevr said in Does anyone have a link to a good site for Multi WAN:
in I can just plugin a utp cable to a switch and than they have there own separate lan and public network.
So these customers are going to run their own routers? If they are going to have their own lan?
How many public IPs do the customers need each? How many public IPs do you have? You know you can hand them as many as you need with simple VIP and 1:1 nat to what their rfc1918 network is..
So
Customer 1 = 192.168.1/24
Customer 2 = 192.168.2/24
Customer 3 = 192.168.3/24
etc..Then on your public IPs which you create vips And do 1:1 nat for each IP to customer IP(s)
1.2.3.100 VIP 1:1 nat to 192.168.1.100
1.2.3.101 VIP 1:1 nat to 192.168.2.100
1.2.3.102 VIP 1:1 nat to 192.168.2.100
etc..There are many ways to skin this cat - but you have not provided the details to help you further.. But what I would suggest is you remove the IPS package.. Is only going to cause you grief and is a HUGE learning curve and lots of time and effort to setup where it doesn't bomb you with log spam and false positives and if in blocking mode going to cause you pain blocking stuff...
What do you currently have setup?
-
Ok its not routed to me.
Do I need a separate router from my customers because they do not bring a router or firewall. I already had 1:1 nat and vips but my trainer said he wanted the public ip linked to a network not a single hosts. I am probably missing the point here. -
This post is deleted! -
@lucndevr said in Does anyone have a link to a good site for Multi WAN:
a software company and there's no real network operator
What, are you kidding? A software company and no-one who cares about the infrastructure?
That's like Nascar racing without someone who prepared the track beforehand...@lucndevr said in Does anyone have a link to a good site for Multi WAN:
what they do now is for every public ip these use a different firewall
So you have a lot of separate networks at the moment, right?
Are those DSL or fiber lines that arrive at your door and each with its own, single public IP? -
@lucndevr said in Does anyone have a link to a good site for Multi WAN:
my trainer said he wanted the public ip linked to a network not a single host
What does he mean?
Do your clients use this internet connection only for outgoing traffic or do they have own servers that need to be reached at the public IP from the outside (aka internet)? Like their own web or e-Mail server.If they need outgoing traffic only then it's easy to set each ISP connection as gateway for the specific client network.
You could describe this as "public IP linked to a network" but it's more the other way round.If they have servers on-premise that need to be reached from the internet then your trainer's demand is wrong. You cannot link an IP to a network (aka multiple devices) for incoming traffic. You can only forward traffic from public IP 1.2.3.4 to one server at a local IP address. Like one web server.
What do they want to gain with a single firewall and a couple of completely separated networks?
And how many ISP links will there be in total? -
This post is deleted! -
Seems like the blind leading the blind here...
You do understand you could do a whole subnet with 1:1 nat right??
So pubicIP 1.2.3.X would be mapped to rfc1918.X
publicIP.Y would go to rfc1918.Y
publicIP.Z would go to rfc1918.ZIf your trainer thinks you can see traffic to port 80 to publicIP 1.2.3.4 on pfsense wan and send that to ALL rfc1918 behind.. It doesn't work that way!!!
-
@lucndevr said in Does anyone have a link to a good site for Multi WAN:
There is 1 ISP with a series of public IPs and they want to be reached from outside.
-
How many IPs/connections are we talking about?
-
Specify "want to be reached from outside" - what's the plan?
-
what kind of service do you get/have: DSL, fiber, LTE, ...
-
what's the bandwidth for each ISP link?
How often do your clients/tenants/whatever change? Will this be on a, say, monthly/yearly basis or is the plan for a longer stay? There are multiple ways to configure this. Just trying to find the one that fits your demands best.
PS: obviously, we are happy to help. We just need some info to work with. Throwing pieces of information at us or not answering questions at all raises frustration for everyone who volunteers with your problem.
-
-
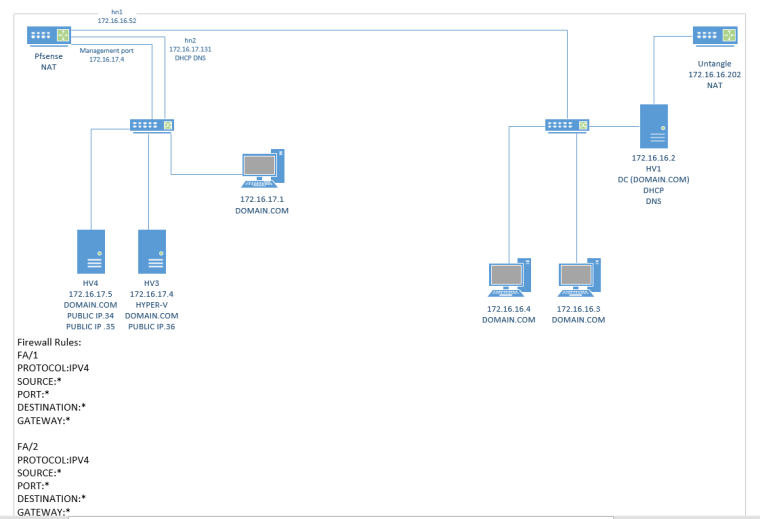
I got the 1:1 NAT working with public ip's
but is it possible to have the domain controller in a different subnet I need it to authenticate HV4 and HV3. see attachment -
@luc1231122 Is that regular behaviour in 2019 - demanding information but not giving answers? Instead posting an (incomplete at best) graphic and asking unrelated questions. Wow!
@luc1231122 said in Does anyone have a link to a good site for Multi WAN:
...domain controller in a different subnet...
Why a different subnet? Aren't they all in 172.16.0.0 /16 ?

Just a quick look at your diagram:
172.16.16.2 is double
172.16.17.131 is double or whatever you wanted to show
FA/1 is double (whatever FA/1 & FA/2 are)
FA/2 is missing
IPv6 is missing completely in the diagram (but is allowed by FW rules!?)
... -
@jahonix Yeah sorry but some questions I do not have the answers.
-
@jahonix
we got 1 ISPI do not know what I have to port forward
We got DSL
I think they are all around 90mbps
I used subnetmask /24
And I re uploaded the diagram hopes it makes anymore more sense now
-
I am just wondering do these 2 routers need to have a static route between each other?
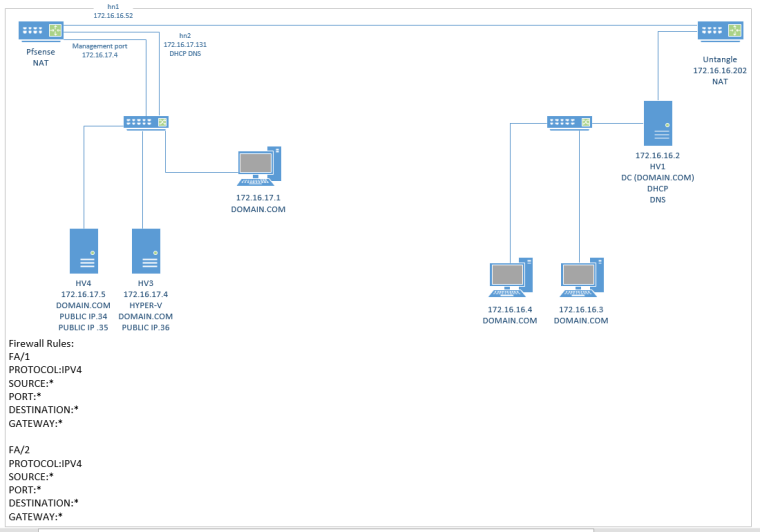
-
Now we have another firewall in the mix? Why?
No that diagram makes no sense at all.. There is no masks on the diagram, So your using /24
So you have network 172.16.16/24 and 172.16.17/24
So you have managment port of pfsense on 17.4 and then another interface on 17.131? So a VIP? You can not put address in the same network on multiple ports.. Pfsense won't let you do that even.
And what the hell is untangle doing out there? Doing Nat to what? That is another internet connection? Your not trying to use untangle with the freaking arp spoofing/poisoning shit it does?? OMG!!
How are you people touching anyone's network in the first place???
If your going to connect two routers, you would use a transit network... And then yes there would need to be routes between the networks.. If your throwing that untangle POS into your network with its arp nonsense it does... Good freaking luck to you - go have fun over on their forums.