Want to Block 1IP from using Internet when VPN goes down
-
here is rules 2.. I enabled Floating No Wan Egress and re ran that debug cat thing you told me to do... hopefully you find my error as your smarter then me at this stuff
-
so 5 min after i enabled the No Wan Egreess Tag under floating options to do the rules2 for you
i lost internet to 100 percent loss
so its still loading it some how
-
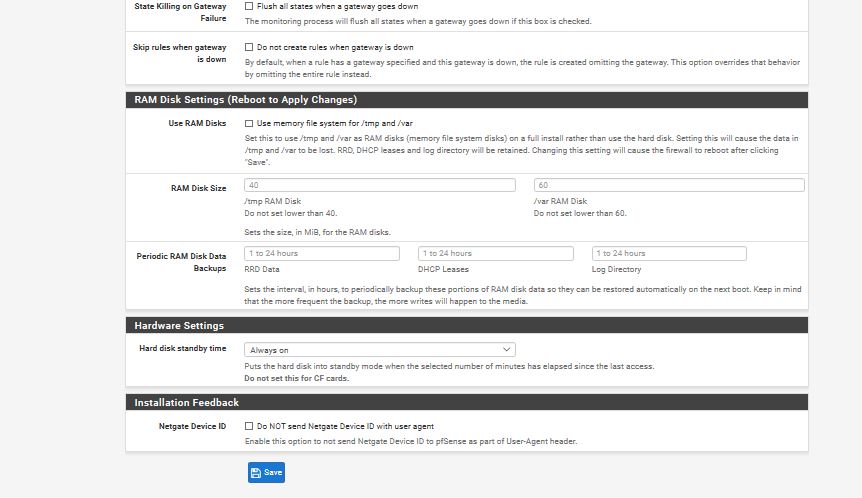
What do you have set for this:
System > Advanced, Miscellaneous, Skip rules when gateway is down
Look. This stuff is extremely complicated. You really have to know exactly what you are doing to pull this kind of policy routing off. You have multiple OpenVPN clients and you want certain LAN hosts to behave one way and certain LAN hosts to behave another.
The NO_WAN_EGRESS rules I sent will not do ANYTHING to connections that do not originate from that source host.
You are refusing my suggestion of starting over from the beginning.
You are policy routing everything from LAN to the OpenVPN gateway. is gateway monitoring enabled there? Does the system even recognize the OpenVPN is down? If not, it will continue to send the traffic out the OpenVPN.
"100 percent loss" is not a trouble description. I understand you are frustrated. More details might be necessary.
-
and sorry if the screen shots are irrevelent to the settings
as i been told i have to post screen shots of the settings i do.. as you guys arent willing to watch videos... and i got blasted last year for not posting screen shots of what i was doing..was only trying to show you the settings i set... didnt mean to make it irrvelent.. to me they were relevent as its the stuff you told me to set..
sorry about that -
It would help if you followed my instructions exactly.
Derelict about 19 hours ago
Make a rule for that specific source host above the NORDVPN rules.
Make it just like the other rule, but with a source of that host address instead of LAN net, policy routing to NORDVPN.
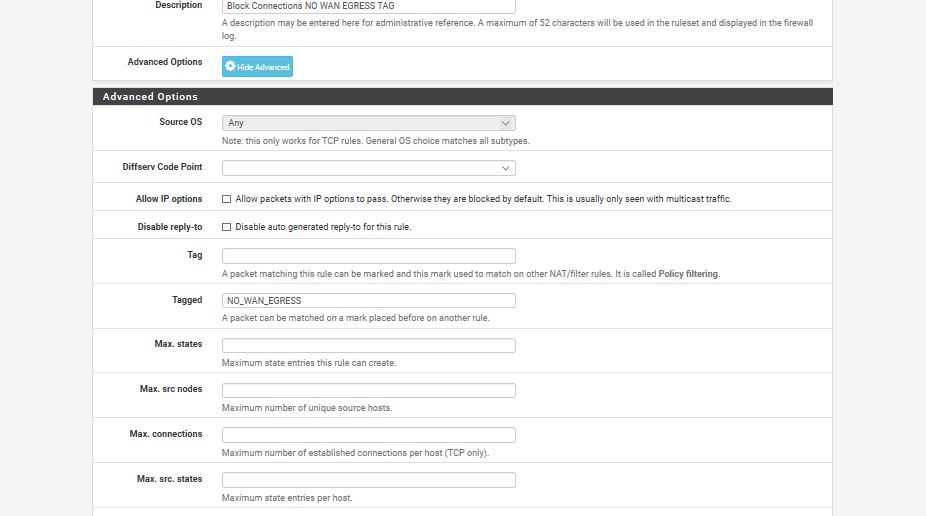
Add the following advanced option:
Tag: NO_WAN_EGRESS
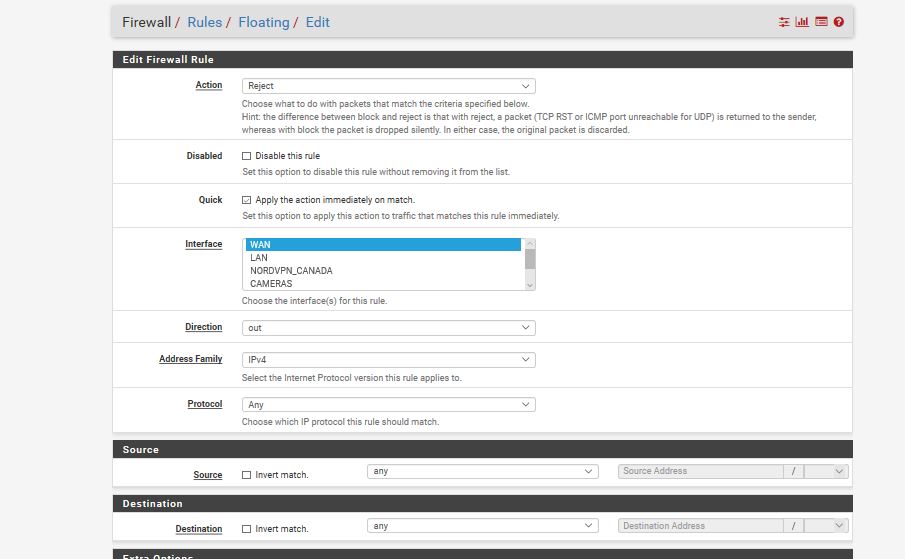
Make a floating rule in Firewall > Rules, Floating
Action: Reject
Quick: Checked
Interface: WAN
Direction: Out
Source: Any
Destination: AnyDisplay Advanced
Tagged: NO_WAN_EGRESS
TAG on LAN
TAGGED on WANThe former SETS the tag
The latter MATCHES the tag previously set by the LAN rules. -
i get that t he No Wan Egree rule only to that
but ill make a video and prove your wrong its not doing that.. its doing it on its own cuz your not believing me..
and i didnt refuse of starting over.. i told you ok in the one reply i said i didnt wanna cuz thats alot of typing and figuring where all the settings god..
yes I got different openVPNs
so what i have is
WAN ----> Only For Game Consoles
NORDVPN USA for entire Network
NORDVPN CANADA for entire Network these 2 is when i wanna be in usa or in canada
OPENVPNSERVEr ---->> so i can Remote access my network from away from the homeand i wouldnt know if gateway monitoring enabled..
and ya the system knows when NordVPN goes down... either i get a email from my ISP my son did something bad which i told him to stop ... or my internet goes down and then im using my WAN IP address so it falls over
i only had issues because you told me i had the rules set wrong for when VPN goes down and to make sure no Internet leaking happens..
and then i find out now that the Floating rule seems to automaticlly load ...
if i disable all the rules minus that lock out rule Floating Rule No Wan Still gets loaded and 100% packet lossbut there is monitoring as there is a monitoring IP when i showed the Gateway images
but here the pics of the misc's
-
i think i found the error on floating
i put TAG NO_WAN_EGRESSnot TAGGED NO_WAN_EGRESS
guess thats the reason it automaticlly Blocks because i put NO_WAN_EGRESS under TAG
i really hate dislexia i read Tagged as Tag... ill try that
So Tag means anything on the Local Network... and TAGGED means anything going out on the internet
ill re try again thank you for being patient
-
nope didnt work
having TAG No Wan EGress for the 192.168.0.11 Under NordVPN one
and having TAGGED No Wan Eggress under Floating
just lets the 192.168.0.11 get WAN internet instead of blocked..
shouldnt the Rule be also set to TAGGED not TAG?
-
No.
TAG sets the mark. You set the mark on traffic from 192.168.0.11 when it arrives on the firewall using the LAN rule.
TAGGED matches the traffic that has that mark set so you are rejecting any traffic trying to go out WAN with that tag already set. It will only be set on traffic sourced from 192.168.0.11 because that's the only source address that matches the rule that sets the tag.
You must have done it wrong again or it would be working.
-
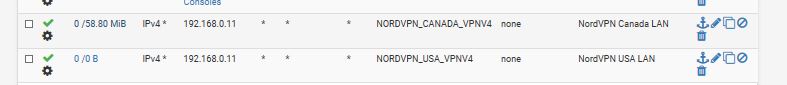
NORDVPN 192.168.011 TAG No WAN EGREE
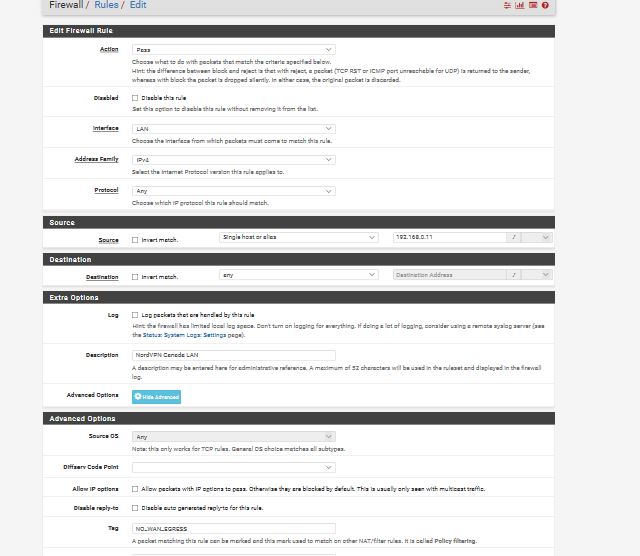
FLOATING TAGGED: NO WAN EGREE
im going to delete the rule and the float and re type it in
i frustrated i getting frustrated yes understand its not easy but stupid dislexia is kicking me too and i like pfsense better then an asus router
i appreciate the help i going to type it up again and see what happens in 30 min i need a break... wish i was in the IT field id know this program better then just only adjust when i find there a problem once a month or so.. set it and forget it kinda thing
thank you for being patient with me i really appreciate it
-
Don't touch anything.
Just post /tmp/rules.debug
That tells everyone everything they need to know about your rule sets.
-
Hi.
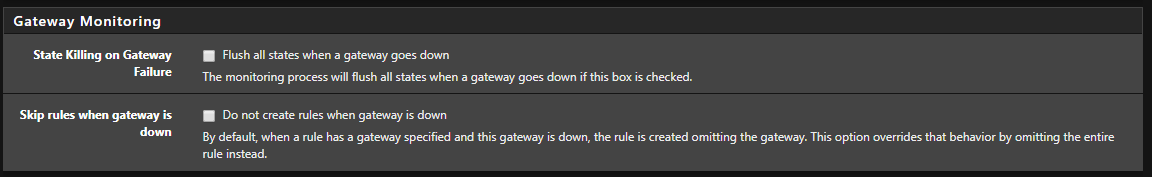
Go to System -> Advanced -> Miscellaneous
Scroll down to: Gateway Monitoring
Make sure it look like this.
-
so for the gate monitoring yes my 2 are also unchecked
as for the Floating its working now.. i had disabled them then just re typed them up and the float
and it worked... also found i had to add a
another No WAN Egress for the LAN.NET when a VPN isnt enabled when i was testing it by turning it off
so this is working now.. doesnt help my dislexia i read like TAG as TAGGED so thats all working... i dont dare ask about how do i route the USA VPN to the USA one in the Rules and the CANADA VPN to the CAnada one.. instead of both going to the first rule... as i dont wanna frustrate you more with my questions..i played with it i didnt wanna annoy you more with questions i stepped away from it a bit then re looked at it fresh eyes for setting that floating etc
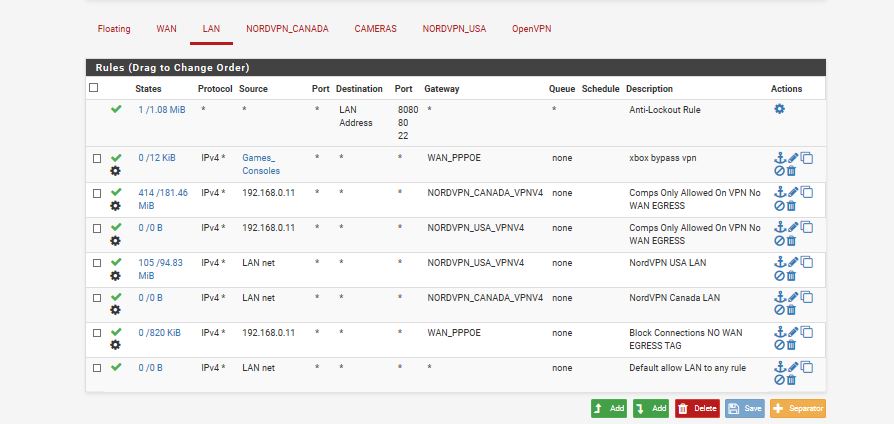
so this is working now in this order... i wont trouble you with my other question i jsut mentioned because i dont want you mad at me... but here is a pic of rules its working so i not going to touch it... it works when i shut off the vpn or if it goes down
i appreciate your patience with me
-
If you don't want traffic from 192.168.0.11 to go out WAN at all, why are you policy routing it out WAN?
-
if your talking about from the picture above the 2nd from the bottom
i dont... but if i dont put that rule in there... and i turn off both VPN's
the rules skip the 2 rules below Game Consoles and goes straight to the last Line..so i put rule just above it... and its TAG No WAN EGRESS so it blocks using WAN
-
figured that was better then saying Block 192.168.0.11 * * * in the rules
unless thats better then the TAG i just figured it was a better block if not ill change it -
is this more proper then
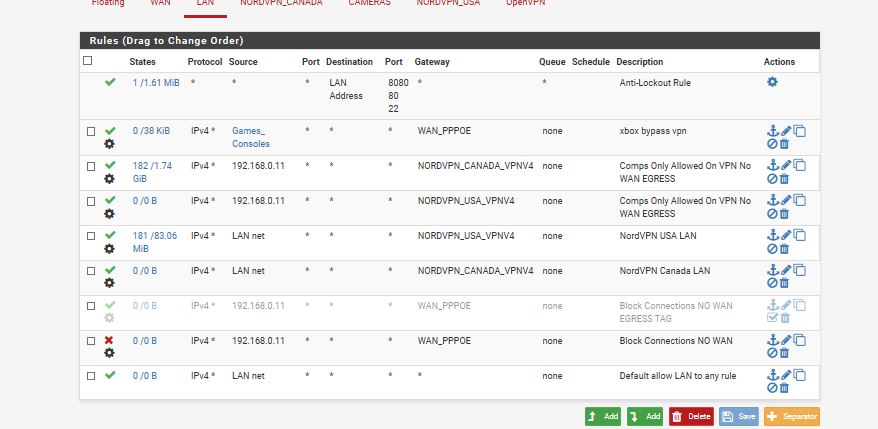
-
@Derelict
I have 1 more question if you might know..
the no_wan_egreess works as long as my vpn I don't check the box "Don't Pass Routes"
if I enable it... The IP Address I have Tag NO WAN EGRESS is automatically blocked yet should be using the VPNbut I notice I need to check Don't Pass Routes to get my XBOX to work bypass VPN
do you know how to get get the rule to work for the VPN and TAG No Wan Egress when you check "Don't Pass Routes"
and should I be using that check box or not... whats the difference I tried googling info but I didn't find info
if you have a link that explains the 2 be good toobut I figured I ask you about that since your very smart at this stuff
-
so having the check mark Dont Pass Routes... still leaks dns yet i dont see it...
i get email from my isp i done suspicious things but i didnt
i run www.dnsleaktest.com on the 192.168.0.11 and it shows 1 server my NordVPN
yet it must be leakingis there another program that runs on windows that securly checks this stuff?
as this No Wan Egress isnt working
least it seems to work only when "DO Not Pull Routes" is not Checked.
when its checked it seems to leak or not work rightis there a way to test this and i read some articles you want Do Not Pull Routes other times you do .. how do you know when
-
I'm not sure that people appreciate how complicated what you are trying to do is.