XG-7100 redundant connections to external switches
-
You just have to add the ports to a new lagg group on the Ports tab i the switches config:
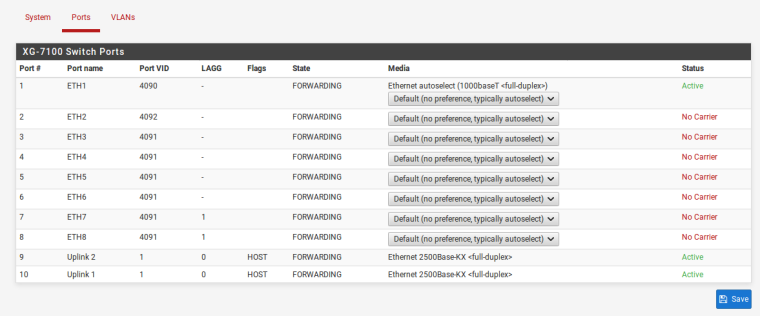
So here ports 7 and 8 are a lagg to another switch or another pfSense box carrying the LAN subnet.
Steve
-
That make sense.
Any plans or ability to provide STP or LACP support on the internal switch in the future? I'm not sure if this is a driver or hardware limitation.
-
Both are being looked at. We would love to have them on the 7100 switch.
I have not heard anything definite though.Steve
-
@stephenw10 actually you give wrong instruction. If you will do change LAGG on ETHn Ports from "-" to anything else yours pfSense WILL STUCK. I tried many cases how configure LAGG on XG-7100 Switch lagg0 and in end:
 I loose my network connectivity. So please could you explain how it can work?
I loose my network connectivity. So please could you explain how it can work? -
Not sure I understand.
You definitely can configure additional lagg groups on the switch as I showed there.
They can't be lagg group 0 as that is already used on the internal ports 9 and 10 to connect to ix2 and ix3.
The ports you set that on will be inaccessible until you connect them to a load-balance lagg so don't change it on ports you're using. to access the gui.
Steve
-
@stephenw10 I changed "-" to 1 on two disconnected ports, click "save" and after this all connectivity to xg-7100 brokes. If connect to com port and run ifconfig no second lagg1 will be showed. Only restore to previous configuration with reboot fix issue. I have one xg-7100 not in production and have one cisco sb200fe 48ports to tests.
-
Could you bee so kind and share with me working XG-7100 pfSense configuration backup with factory defaults and configured switch ports:
untagged port 3 and 4 to lagg1 on vlan 4091
untagged port 5 and 6 to lagg2 on vlan 4091
I want connect 3-4 port to #1 cisco switch on lagg. And 5-6 to #2 cisco switch on lagg. -
Configuring and additional lagg group in the switch does not create a new lagg in pfSense Interfaces. It's a lagg only between the switch and whatever is on those ports.
The internal switch can only do load-balance lagg. The Cisco switch must also support that.
Steve
-
@stephenw10 yes I know that only LB can be done. No LACP. But still, when I have default hardware and clean OS/config changing "-" to something like 1 on port and click "save" destroy connectivity. So I don't know... Help pls.
-
Hmm, I see. That was an old config I have on that box.
Try running at the console after making the change:
etherswitchcfgThat will show the current switch settings. Do you see, for example?:
laggroup0: members 5,6,9,10 laggroup1: members 5,6There I added ports 5 and 6 to lagg group 1 but they have been added to group 0 also.
If so as a workaround you can set that back to just 9 and 10 using:
etherswitchcfg laggroup0 members 9,10Steve
-
@stephenw10 ok, thanks. I will try maybe on monday, and will reply. but if I remove 5,6 ports from lagg0 this will be mean that pfSense can't reach them and clients on 5,6 will doesn't reach pfSense. This will be isolated switch, no?
And if not remove 5,6 from lagg0 before add to lagg1 it will be collizion? That's why my pfSense was sticking previously... -
@stephenw10 about that you said:
etherswitchcfg laggroup0 members 9,10
I see that this is a BIG
 in pfSense Switch WebConfigurator.
in pfSense Switch WebConfigurator.
Configuring laggs over shell works fine.
I created bugreport about it - hope they will fix it soon, before this I will use shell for it
-
It is already fixed in 2.5 snapshots if you're able to try those. It was in fact fixed in 2.4.5 snaps too.
Steve
-
https://redmine.pfsense.org/issues/9447 :( wasted time. Ok. Thanks. I better wait for Stable release. I'm now on Latest Base 2.4.4_2. There is known date of 2.4.5 or 2.5 release?
-
Not for 2.5 release. I'm not aware of any particular issue with running 2.5 on it currently but things are changing there everyday.
You can set that command to run via the shellcmd package if you wish do you don't have to manually run it boot.
https://docs.netgate.com/pfsense/en/latest/development/executing-commands-at-boot-time.htmlSteve
-
@stephenw10 you mean that etherswitchcfg laggroup1 members 5,6 is not permanent? Ok.
-
The config is actually correct. The bug is how it gets applied to the switch so when you reboot and that gets applied....
Let me test that quickly...
-
@stephenw10 yes I test it, on reboot is same as like configuration from Web:
laggroup0:
members 3,4,5,6,9,10
laggroup1:
members 3,4
laggroup2:
members 3,4,5,6
I will wait stable release thanks, topic done -
Sorry I was called away. That does work though:
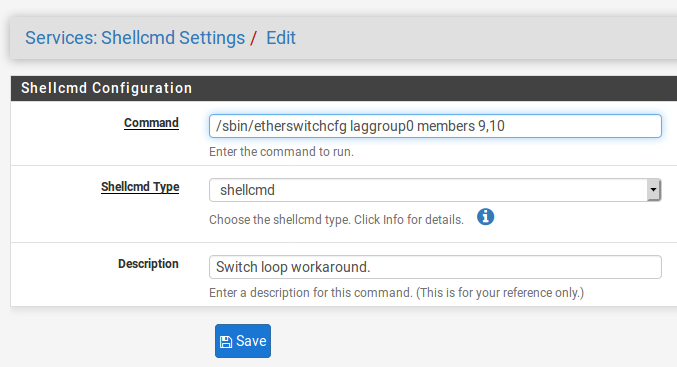
I'll see if we can get a patch you can apply directly to 2.4.4p2 via the patches package. That would be cleaner.
Steve
-
Ok here's a patch you apply against 2.4.4p2. You can use the system patches package to do it which removes most of the scope for error.
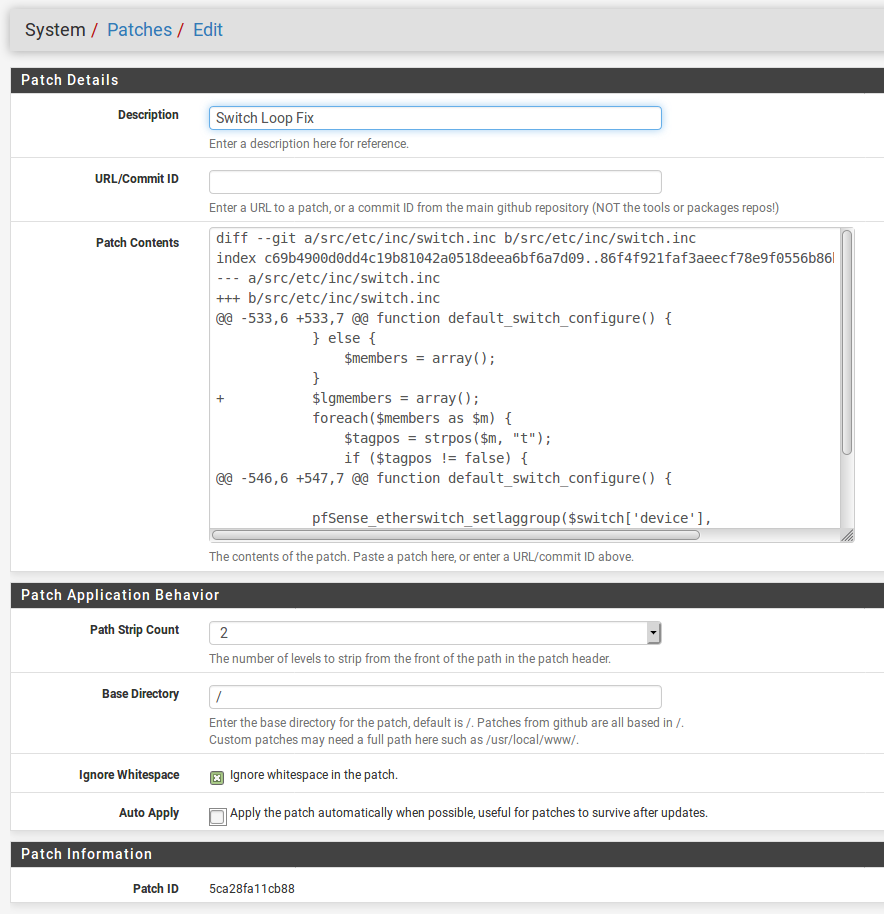
Steve