Another IGMP proxy post
-
So I did that. I don't know where it is outputting to but this is what happens when I do a pcap on full for the interface that the server is on.
10:17:44.128444 00:18:dd:32:28:1b > 01:00:5e:00:00:16, ethertype IPv4 (0x0800), length 60: (tos 0xc0, ttl 1, id 0, offset 0, flags [DF], proto IGMP (2), length 40, options (RA)) 192.168.10.142 > 224.0.0.22: igmp v3 report, 1 group record(s) [gaddr 239.255.255.250 is_ex { }] 10:17:44.377428 00:18:dd:32:28:1b > 01:00:5e:00:00:16, ethertype IPv4 (0x0800), length 60: (tos 0xc0, ttl 1, id 0, offset 0, flags [DF], proto IGMP (2), length 40, options (RA)) 192.168.10.142 > 224.0.0.22: igmp v3 report, 1 group record(s) [gaddr 239.255.255.250 is_ex { }]Is the TTL being "1" going to cause an issue with forwarding it to the interface/vlan with the client on it?
-
It should be outputting the debug stuff at the command line where you started it. That should tell us if it's doing anything useful at all.
Steve
-
The only output is what is below:
Searching for config file at '/var/etc/igmpproxy.conf' Config: Quick leave mode enabled. Config: Got a phyint token. Config: IF: Config for interface igb1.10. Config: IF: Got upstream token. Config: IF: Got ratelimit token '0'. Config: IF: Got threshold token '1'. Config: IF: Got altnet token 192.168.10.0/24. Config: IF: Altnet: Parsed altnet to 192.168.10/24. Config: IF: Got altnet token xxxxxxxxxx. Config: IF: Altnet: Parsed altnet to xxxxxxxxx. IF name : igb1.10 Next ptr : 0 Ratelimit : 0 Threshold : 1 State : 1 Allowednet ptr : e25000 Config: Got a phyint token. Config: IF: Config for interface igb1.90. Config: IF: Got downstream token. Config: IF: Got ratelimit token '0'. Config: IF: Got threshold token '1'. Config: IF: Got altnet token 192.168.90.0/24. Config: IF: Altnet: Parsed altnet to 192.168.90/24. IF name : igb1.90 Next ptr : 0 Ratelimit : 0 Threshold : 1 State : 2 Allowednet ptr : e25020 Config: Got a phyint token. Config: IF: Config for interface igb0. Config: IF: Got disabled token. IF name : igb0 Next ptr : 0 Ratelimit : 0 Threshold : 1 State : 0 Allowednet ptr : 0 Config: Got a phyint token. Config: IF: Config for interface igb1. Config: IF: Got disabled token. IF name : igb1 Next ptr : 0 Ratelimit : 0 Threshold : 1 State : 0 Allowednet ptr : 0 Config: Got a phyint token. Config: IF: Config for interface igb1.99. Config: IF: Got disabled token. IF name : igb1.99 Next ptr : 0 Ratelimit : 0 Threshold : 1 State : 0 Allowednet ptr : 0 Config: Got a phyint token. Config: IF: Config for interface ovpnc2. Config: IF: Got disabled token. IF name : ovpnc2 Next ptr : 0 Ratelimit : 0 Threshold : 1 State : 0 Allowednet ptr : 0 Config: Got a phyint token. Config: IF: Config for interface ovpns1. Config: IF: Got disabled token. IF name : ovpns1 Next ptr : 0 Ratelimit : 0 Threshold : 1 State : 0 Allowednet ptr : 0 Config: Got a phyint token. Config: IF: Config for interface vmx0. Config: IF: Got disabled token. IF name : vmx0 Next ptr : 0 Ratelimit : 0 Threshold : 1 State : 0 Allowednet ptr : 0 Config: Got a phyint token. Config: IF: Config for interface igb1.60. Config: IF: Got disabled token. IF name : igb1.60 Next ptr : 0 Ratelimit : 0 Threshold : 1 State : 0 Allowednet ptr : 0 Config: Got a phyint token. Config: IF: Config for interface igb1.55. Config: IF: Got disabled token. IF name : igb1.55 Next ptr : 0 Ratelimit : 0 Threshold : 1 State : 0 Allowednet ptr : 0 buildIfVc: Interface igb0 Addr: xxxxx, Flags: 0xffff8843, Network: xxxxxxx buildIfVc: Interface igb1 Addr: 192.168.1.177, Flags: 0xffff8a43, Network: 192.168.1/24 buildIfVc: Interface vmx0 Addr: 192.168.66.1, Flags: 0xffff8843, Network: 192.168.66/24 buildIfVc: Interface lo0 Addr: 127.0.0.1, Flags: 0xffff8049, Network: 127/8 buildIfVc: Interface igb1.99 Addr: 192.168.99.1, Flags: 0xffff8843, Network: 192.168.99/24 buildIfVc: Interface igb1.10 Addr: 192.168.10.1, Flags: 0xffff8a43, Network: 192.168.10/24 buildIfVc: Interface igb1.90 Addr: 192.168.90.1, Flags: 0xffff8a43, Network: 192.168.90/24 buildIfVc: Interface igb1.60 Addr: 192.168.60.1, Flags: 0xffff8843, Network: 192.168.60/24 buildIfVc: Interface igb1.55 Addr: 192.168.55.1, Flags: 0xffff8843, Network: 192.168.55/24 buildIfVc: Interface ovpns1 Addr: 192.168.91.1, Flags: 0xffff8051, Network: 192.168.91/24 buildIfVc: Interface ovpnc2 Addr: xxxxxxx, Flags: 0xffff8051, Network: xxxxxxxx Found config for igb0 Found config for igb1 Found config for vmx0 Found config for igb1.99 Found config for igb1.10 Found config for igb1.90 Found config for igb1.60 Found config for igb1.55 Found config for ovpns1 Found config for ovpnc2 MC-Router API already in use; Errno(48): Address already in use -
@pr3dict said in Another IGMP proxy post:
Errno(48): Address already in use
Doesn't look good.
So you have a whole number of interfaces besides what you mentioned initially. You should try to get this working just on those interfaces initially before adding anything further.
Steve
-
I have a bunch of interfaces but I only have 1 of them listed for downstream and upstream...
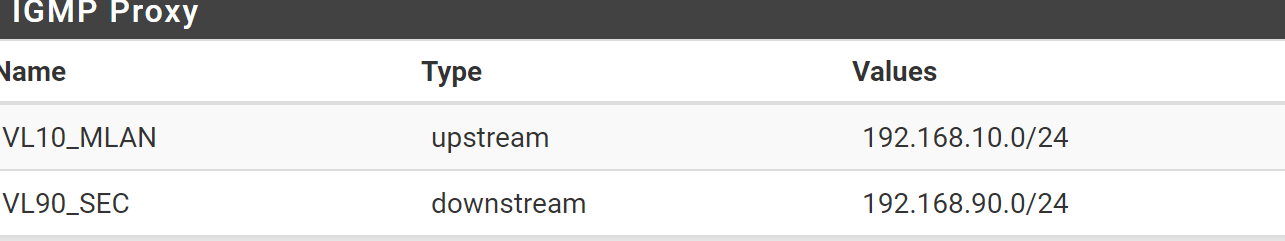
-
I restarted the router and was able to start it up.
but i cant give the output because the site thinks its spam...
About to call timeout 4 (#0) SENT Membership query from 192.168.90.1 to 224.0.0.1 Sent membership query from 192.168.90.1 to 224.0.0.1. Delay: 10 Created timeout 5 (#0) - delay 10 secs (Id:5, Time:10) Created timeout 6 (#1) - delay 115 secs (Id:5, Time:10) (Id:6, Time:115) RECV Membership query from 192.168.90.1 to 224.0.0.1 The IGMP message was local multicast. Ignoring. RECV V2 member report from 192.168.90.100 to 224.0.0.252 Should insert group 224.0.0.252 (from: 192.168.90.100) to route table. Vif Ix : 1 Updated route entry for 224.0.0.252 o ```n VIF #1Current routing table (Insert Route): ----------------------------------------------------- #0: Dst: 224.0.0.251, Age:2, St: I, OutVifs: 0x00000002 #1: Dst: 224.0.0.252, Age:2, St: I, OutVifs: 0x00000002 -
Post it on pastebin or similar and link to it.
-
Gooood idea!
https://pastebin.com/2j8MGRRF
-
Ok, so you moved the server from 192.168.55.125? Where is it now exactly?
-
@stephenw10 Yeah sorry about that. The .10 subnet is where a lot of other clients are so while I was testing this I didnt want to have ot keep switching between .55 and .10...
The server is now at 192.168.10.142
-
Also if I flip the downstream and upstream interfaces this is the output for that...
https://pastebin.com/uBpRFH9H
-
Your set up of igmp proxy and firewall rules seem to be the similar to mine. Nothing is blocked in my logs between these subnets and advanced ip options are enabled.on the igmp firewall rules. The guys on the unifi forum have installed and used socat on their edge router to get hdhomerun recognised across subnets.
https://community.ubnt.com/t5/EdgeRouter/Howto-HDHomerun-discovery-on-different-LAN-segment/m-p/2733241#M246671
I'm watching this thread in the hope you discover an answer that will also help me. If I find a solution to this problem I'll post it here too. Good luck.
-
@pr3dict
Thanks to meckhert on the unifi forum I've now managed to solve my hdhr problem by installing socat on a raspberry-pi that I already had on my private LAN. On the raspberry-pi I created and enabled a simple systemd service for socat so that it auto starts using the command meckhert listed.192.168.100.17 is the IP of my hdhr on my IoT network.
socathdhr.service:
[Unit]
Description=socat hdhr
After=network.target[Service]
Type=simple
User=root
ExecStart= /usr/bin/socat -d -d -v udp4-recvfrom:65001,broadcast,fork udp4-sendto:192.168.100.17:65001
Restart=on-failure
RestartSec=10[Install]
WantedBy=multi-user.targetI hope this helps.