New User to pfSense - some doubts
-
@HansSolo said in New User to pfSense - some doubts:
I wonder if it's because our configurations are different? Are you running a server behind your pfSense?
What version pfsense are you running?Yes I have ports forwarded, I run ntp server to the world via ntp pool.. I have friends and family access to my plex server.
As to what version of pfsense I run - its in my signature.. And yes I would be running current, as any sane person should be.
That you think an any any rule is ok on your wan - even IF some tool created it.. Is just beyond nuts...
-
They are created by pfBlocker but only because of how it's configured.
pfBlocker can create firewall rules but does not have to. It depends what you have set the list action to.
Typically it is set to add block rules to prevent LAN side clients reaching out to, for example, known malware sites.
However I recommend setting the list action to Native Alias only and then using those aliases in rules you add yourself.
Also worth noting the pfBlocker setup wizard is only in the dev version I believe.
Steve
-
While the wizard might be only in dev... The older version doesn't create rules like that without being told to do it..
You don't install any version of pfblocker and next thing without doing anything have any any rules on your wan... That would be insane!!
-
@johnpoz said in New User to pfSense - some doubts:
While the wizard might be only in dev... The older version doesn't create rules like that without being told to do it..
You don't install any version of pfblocker and next thing without doing anything have any any rules on your wan... That would be insane!!
ok ok...I'm probably not insane (or nuts). and no, I do not think ANY rule is "ok". Not sure where you assumed that. Just not familiar with pfsense and pfSenseBlockerNG. Day 3 with pfSense so I can't possibly know everything about how it and the blocker works under the hood. I thought it was some kind of fancy proxying of the lists and DNS manipulation.
I did check with my cell phone and no access was granted to any unauthorized part of the network so no harm done.
-
@HansSolo said in New User to pfSense - some doubts:
I do not think ANY rule is "ok". Not sure where you assumed that
Because you had them on your wan ;) And then asked if they were ok...
-
@johnpoz said in New User to pfSense - some doubts:
@HansSolo said in New User to pfSense - some doubts:
I do not think ANY rule is "ok". Not sure where you assumed that
Because you had them on your wan ;) And then asked if they were ok...
Well think about it.....
If I was "insane" or "nuts", I probably wouldn't have even asked.
Let's not beat up the noobs just because they are not totally familiar with pfsense yet and don't know right off the bat if automated configurations that they didn't put there are legit or not (even if they look odd)
Thanks for all the great advice everyone !

-
Where exactly are you seeing that rule that doesn't allow you dest port in it.. What version of pfblocker are you running the older or dev version?
-
@johnpoz said in New User to pfSense - some doubts:
Where exactly are you seeing that rule that doesn't allow you dest port in it.. What version of pfblocker are you running the older or dev version?
by the time I reply, you will probably have discovered that that was answered above

as for the pfBlocker version.....3 days in, so I downloaded it probably yesterday. latest, I assume ?
Let me check and see if I can find that version.....
-
@HansSolo said in New User to pfSense - some doubts:
pfSenseBlockerNG
what version does it say.. that tells me not the old one... But maybe you have not updated your packages? Can not tell if you mean non dev or dev version.
its listed right in your package manager
example
pfBlockerNG-devel 2.2.5_22there should be really screaming red flags on the pfblocker gui that its going to create an any any rule.. If that is what its doing.
Where exactly did you go in pfblocker to create said rule.
Paging @BBcan177 if pfblocker creates any any rules on the wan without huge warnings to the user.. That really should be changed..
-
@johnpoz said in New User to pfSense - some doubts:
@HansSolo said in New User to pfSense - some doubts:
pfSenseBlockerNG
what version does it say.. that tells me not the old one... But maybe you have not updated your packages? Can not tell if you mean non dev or dev version.
its listed right in your package manager
example
pfBlockerNG-devel 2.2.5_22there should be really screaming red flags on the pfblocker gui that its going to create an any any rule.. If that is what its doing.
Where exactly did you go in pfblocker to create said rule.
Paging @BBcan177 if pfblocker creates any any rules on the wan without huge warnings to the user.. That really should be changed..
pfBlockerNG net 2.1.4_16
Agreed. Unless......that rule doesn't actually give said access.
Let's hope the developer will reply regardless of the outcome.I KNOW I didn't create those rules intentionally.....but maybe they got created some how that I'm not aware of other than by pfBlockerNG ?
My gut feeling is that they were created intentionally and do not allow the access it appears.
That said...I've changed them all as suggested.....to be safe. (And I have not yet reconnected pfsense, still using WG)And as mentioned, I DID CHECK WITH MY CELL PHONE and was not able to find any compromised connections.
-
@HansSolo said in New User to pfSense - some doubts:
Agreed. Unless......that rule doesn't actually give said access.
It DOES!! since its a rule on your WAN...
-
@johnpoz said in New User to pfSense - some doubts:
@HansSolo said in New User to pfSense - some doubts:
Agreed. Unless......that rule doesn't actually give said access.
It DOES!! since its a rule on your WAN...
But in the source it lists a pfBlockerNG file, NOT a network location. What do you interpret that to mean?
OTOH...I can't speak for anyone else, but there's so much information to absorb in such a short time, brain farts do occur.
And it's possible I experienced a real winner. -
Doesn't matter if it only allows source IPs.. it is allowing to ANY ANY as dest.. So if user had a port forward to say 443 behind pfsense.. And it created a any any rule above that even if locked down to only NA... It now allows access to pfsense web gui and anything else that listens on pfsense wan, say dns, etc. etc.
Which is BAD!!! I just installed that version, enabled it and did an update.. No rules on the WAN, only the rule on my lan blocking outbound access to stuff.
-
@johnpoz said in New User to pfSense - some doubts:
Doesn't matter if it only allows source IPs.. it is allowing to ANY ANY as dest.. So if user had a port forward to say 443 behind pfsense.. And it created a any any rule above that even if locked down to only NA... It now allows access to pfsense web gui and anything else that listens on pfsense wan, say dns, etc. etc.
Which is BAD!!! I just installed that version, enabled it and did an update.. No rules on the WAN, only the rule on my lan blocking outbound access to stuff.
Ok.
Then I have no clue how that rule got there and where it came from.
I may have to chalk it up to trying to learn too much too fast over the last 3 days. -
pfBlocker just by itself can be pretty confusing IMO. There's a LOT there to take it.
I like to have full control of what rules are where which is why I recommend the Native Aliases approach. It's easier to understand the resulting ruleset when you have added everything yourself.
pfSense is guilty of that in other areas, you have to add firewall rules to allow OpenVPN traffic but IPSec traffic is passed by default by rules added automatically. You can disable that at least. If we changed that now it would break hundreds of thousands of VPNs though!

Steve
-
So I see this warning
Also consider protecting just the specific open WAN ports and it's just as important to protect the outbound LAN traffic.
And if you open the advanced, you can limit to specific ports..
But yeah if just set to inbound us, it creates this rule
===[ Aliastables / Rules ]================================ Firewall rule changes found, applying Filter ReloadYeah this is a HORRIBLE implementation... Just freaking HORRIBLE!!
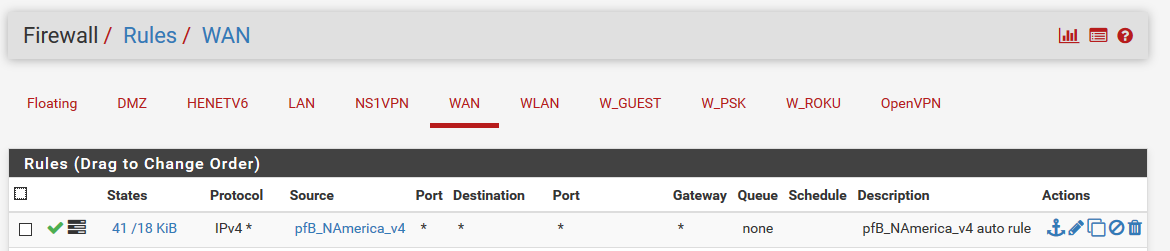
That should be limited to wan address on specific PORTS, unless the user changes it... Then that would be on them.. But I can see how new users might just open wide their wan... Arrrgghhh!!
Or anything behind pfsense if they had a routed netblock, etc. etc.
paging @BBcan177 again, I don't see how such a thing would be ok... Ultimately its on the admin of the firewall to understand what they are doing, and what is set... But pfsense does try and keep the users from shooting themselves in the foot.. This is not doing that at all..
-
@johnpoz said in New User to pfSense - some doubts:
So I see this warning
Also consider protecting just the specific open WAN ports and it's just as important to protect the outbound LAN traffic.
And if you open the advanced, you can limit to specific ports..
But yeah if just set to inbound us, it creates this rule
===[ Aliastables / Rules ]================================ Firewall rule changes found, applying Filter ReloadYeah this is a HORRIBLE implementation... Just freaking HORRIBLE!!

That should be limited to wan address on specific PORTS, unless the user changes it... Then that would be on them.. But I can see how new users might just open wide their wan... Arrrgghhh!!
So I'm not nuts or insane?......

I gave the system the benefit of the doubt that it was performing some kind of "magic" on the back end.Then checked to see if my system was compromised in any way from outside my network and couldn't find any compromises or openings etc. I agree those settings could be dangerous but again, it didn't seem to allow the access it appears it would. maybe because of redundant filters I had setup on the Opt1 and LAN interfaces.
I ALSO changed the port on which the WebConfigurator resides early on. I didn't like it on port 80 at all.

-
In the past when I had played with this, I had always just used the aliases in my own rules.. This really needs to be changed to force the user to easy select their wan address as destination or the any, vs forcing them to use an alias. And it should WARN them about ANY as destination especially above all other rules on the wan,
-
@johnpoz said in New User to pfSense - some doubts:
In the past when I had played with this, I had always just used the aliases in my own rules.. This really needs to be changed to force the user to easy select their wan address as destination or the any, vs forcing them to use an alias. And it should WAN them about ANY as destination especially above all other rules on the wan,
Totally agree.
But would still like to hear from the developer to make sure there is no "back end" magic going on here.Seems to write something like this they would know better, right?
-
also, Jon....this is probably a totally different topic but....
You said you have no WAN rules, only outgoing LAN rules.....correct?If you have no WAN rules, then everything inbound at least (probably outbound as well) "should" be blocked by default, right? WAN is your "gateway" to external ie the Internet.
So how then does anyone get to your server?
Only way a server is available to the public that I know of is specific WAN rules that allow traffic inbound.Such as ALLOW from * * TO 'server address' 'server port'
And most often, it involves Natting from your Public IP address to the server's IP (which is usually Opt1)
Just curious. Always ready and eager to learn something new.