New User to pfSense - some doubts
-
@HansSolo said in New User to pfSense - some doubts:
My only two complaints at this point would be the difficulty in blocking Outbound traffic and the lack of native auto-blocking.....such as for port probes or other potentially nefarious activity.
Outbound traffic is managed just as easily as inbound. You can even copy rules and change one drop-down to apply that rule to outbound traffic.
If you want pfSense to respond to malicious or suspicious activity, it's really easy to do. Download Snort to start with. If you're anything like me, your pfSense installation will block your computer from the entire network when you start testing to see if Snort works. And then you'll have to go over to another computer to get Snort to unblock your testing computer. I had Snort block every device on the network once. With great power comes great responsibility. Works great, just don't set it too aggressively to begin with.
Oh, and I need to find a way to at least see some blinking lights that represent active traffic across the Interfaces.
I see no reason this could not have been done on the Console and viewed onscreen same as with pftop etc.
I don't like the options of adding additional cards just to get blinking activity LEDsWhat about the bandwidth graphs? I use those all the time to monitor traffic. It's usually "good enough". There are other ways to check on traffic activity down to the port if need be.
-
@tim-mcmanus said in New User to pfSense - some doubts:
@HansSolo said in New User to pfSense - some doubts:
My only two complaints at this point would be the difficulty in blocking Outbound traffic and the lack of native auto-blocking.....such as for port probes or other potentially nefarious activity.
Outbound traffic is managed just as easily as inbound. You can even copy rules and change one drop-down to apply that rule to outbound traffic.
If you want pfSense to respond to malicious or suspicious activity, it's really easy to do. Download Snort to start with. If you're anything like me, your pfSense installation will block your computer from the entire network when you start testing to see if Snort works. And then you'll have to go over to another computer to get Snort to unblock your testing computer. I had Snort block every device on the network once. With great power comes great responsibility. Works great, just don't set it too aggressively to begin with.
Oh, and I need to find a way to at least see some blinking lights that represent active traffic across the Interfaces.
I see no reason this could not have been done on the Console and viewed onscreen same as with pftop etc.
I don't like the options of adding additional cards just to get blinking activity LEDsWhat about the bandwidth graphs? I use those all the time to monitor traffic. It's usually "good enough". There are other ways to check on traffic activity down to the port if need be.
Yeah, there are "ways" to do it..but my complaint is that it shouldn't be a process.
-
@johnpoz said in New User to pfSense - some doubts:
@akuma1x said in New User to pfSense - some doubts:
I'm thinking he's looking for visual confirmation that his firewall is actually working and moving traffic.
your on the console - hit #9 (pftop)
Can you not just use the BlinkLED package? If you want something to be blinking at you ;)
Not what I'm looking for. The BlinkLED package requires an add on card. I just want to be able to look over and see Activity lights blinking when traffic is moving through the Interfaces. This could EASILY be done via the console. I may have to write my own code to do it.
JohnPoz understands
-
@HansSolo said in New User to pfSense - some doubts:
@tim-mcmanus said in New User to pfSense - some doubts:
@HansSolo said in New User to pfSense - some doubts:
My only two complaints at this point would be the difficulty in blocking Outbound traffic and the lack of native auto-blocking.....such as for port probes or other potentially nefarious activity.
Outbound traffic is managed just as easily as inbound. You can even copy rules and change one drop-down to apply that rule to outbound traffic.
If you want pfSense to respond to malicious or suspicious activity, it's really easy to do. Download Snort to start with. If you're anything like me, your pfSense installation will block your computer from the entire network when you start testing to see if Snort works. And then you'll have to go over to another computer to get Snort to unblock your testing computer. I had Snort block every device on the network once. With great power comes great responsibility. Works great, just don't set it too aggressively to begin with.
Oh, and I need to find a way to at least see some blinking lights that represent active traffic across the Interfaces.
I see no reason this could not have been done on the Console and viewed onscreen same as with pftop etc.
I don't like the options of adding additional cards just to get blinking activity LEDsWhat about the bandwidth graphs? I use those all the time to monitor traffic. It's usually "good enough". There are other ways to check on traffic activity down to the port if need be.
Yeah, there are "ways" to do it..but my complaint is that it shouldn't be a process.
Which part?
It's actually better that it is a process. You have very acute control over nearly every aspect of pfSense, and many of the packages take advantage of the extensibility of the platform to bring significant enhancements to it.
pfSense can be monitored by many different monitoring platforms that excel at generating these reports. pfSense is not a reporting tool, and it has some excellent reporting capabilities. In order for pfSense to focus on what it does best (routing, etc.) a lot of the reporting capabilities are handled by more powerful 3rd party reporting tools. I rely on pfSense's internal reports but also have everything being pushed to a syslog server where I can do event correlation and other activities with the reported data.
It's a very powerful tool, but it is not a Swiss army knife.
-
Hmm, are you saying thr actual NIC LEDs do not blink to show activity?
That is a configurable setting on many NICs but rarely actually gets changed. No way to change it in pfSense (from the GUI).
Steve
-
@johnpoz said in New User to pfSense - some doubts:
@HansSolo said in New User to pfSense - some doubts:
My only two complaints at this point would be the difficulty in blocking Outbound traffic
What it takes like 2 freaking seconds to block anything you need to block outbound - like .2 seconds.
native auto-blocking.....such as for port probes or other potentially nefarious activity.
What? Dude out of the box all inbound unsolicited traffic is dropped anyway.. So your worried that you have port 80 forwarded, and you want to block IP xyz that starts checking ports at 1 and moves up 2,3,4 before he gets to your 80.. That doesn't stop just bot that hits you direct 80 without other ports being checked first... Its NONSENSE smoke and mirror security magic that does nothing.. Your service you open to the public is either secure or its not, trying to "hide" is not security!!
I don't like the options of adding additional cards just to get blinking activity LEDs
Again WHAT??
You get so excited over new user questions.

-
@tim-mcmanus said in New User to pfSense - some doubts:
@HansSolo said in New User to pfSense - some doubts:
@tim-mcmanus said in New User to pfSense - some doubts:
@HansSolo said in New User to pfSense - some doubts:
My only two complaints at this point would be the difficulty in blocking Outbound traffic and the lack of native auto-blocking.....such as for port probes or other potentially nefarious activity.
Outbound traffic is managed just as easily as inbound. You can even copy rules and change one drop-down to apply that rule to outbound traffic.
If you want pfSense to respond to malicious or suspicious activity, it's really easy to do. Download Snort to start with. If you're anything like me, your pfSense installation will block your computer from the entire network when you start testing to see if Snort works. And then you'll have to go over to another computer to get Snort to unblock your testing computer. I had Snort block every device on the network once. With great power comes great responsibility. Works great, just don't set it too aggressively to begin with.
Oh, and I need to find a way to at least see some blinking lights that represent active traffic across the Interfaces.
I see no reason this could not have been done on the Console and viewed onscreen same as with pftop etc.
I don't like the options of adding additional cards just to get blinking activity LEDsWhat about the bandwidth graphs? I use those all the time to monitor traffic. It's usually "good enough". There are other ways to check on traffic activity down to the port if need be.
Yeah, there are "ways" to do it..but my complaint is that it shouldn't be a process.
Which part?
It's actually better that it is a process. You have very acute control over nearly every aspect of pfSense, and many of the packages take advantage of the extensibility of the platform to bring significant enhancements to it.
pfSense can be monitored by many different monitoring platforms that excel at generating these reports. pfSense is not a reporting tool, and it has some excellent reporting capabilities. In order for pfSense to focus on what it does best (routing, etc.) a lot of the reporting capabilities are handled by more powerful 3rd party reporting tools. I rely on pfSense's internal reports but also have everything being pushed to a syslog server where I can do event correlation and other activities with the reported data.
It's a very powerful tool, but it is not a Swiss army knife.
Some of my comments are predicated on the fact that I've used certain other firewalls for so long and have grown accustomed to certain things and therefor naturally "expect" them in other firewalls whether a valid expectation or not.
As time passes and I get more learned with pfSense I'm sure some of the things I ask now will clear themselves up.
-
@HansSolo said in New User to pfSense - some doubts:
@tim-mcmanus said in New User to pfSense - some doubts:
@HansSolo said in New User to pfSense - some doubts:
@tim-mcmanus said in New User to pfSense - some doubts:
@HansSolo said in New User to pfSense - some doubts:
My only two complaints at this point would be the difficulty in blocking Outbound traffic and the lack of native auto-blocking.....such as for port probes or other potentially nefarious activity.
Outbound traffic is managed just as easily as inbound. You can even copy rules and change one drop-down to apply that rule to outbound traffic.
If you want pfSense to respond to malicious or suspicious activity, it's really easy to do. Download Snort to start with. If you're anything like me, your pfSense installation will block your computer from the entire network when you start testing to see if Snort works. And then you'll have to go over to another computer to get Snort to unblock your testing computer. I had Snort block every device on the network once. With great power comes great responsibility. Works great, just don't set it too aggressively to begin with.
Oh, and I need to find a way to at least see some blinking lights that represent active traffic across the Interfaces.
I see no reason this could not have been done on the Console and viewed onscreen same as with pftop etc.
I don't like the options of adding additional cards just to get blinking activity LEDsWhat about the bandwidth graphs? I use those all the time to monitor traffic. It's usually "good enough". There are other ways to check on traffic activity down to the port if need be.
Yeah, there are "ways" to do it..but my complaint is that it shouldn't be a process.
Which part?
It's actually better that it is a process. You have very acute control over nearly every aspect of pfSense, and many of the packages take advantage of the extensibility of the platform to bring significant enhancements to it.
pfSense can be monitored by many different monitoring platforms that excel at generating these reports. pfSense is not a reporting tool, and it has some excellent reporting capabilities. In order for pfSense to focus on what it does best (routing, etc.) a lot of the reporting capabilities are handled by more powerful 3rd party reporting tools. I rely on pfSense's internal reports but also have everything being pushed to a syslog server where I can do event correlation and other activities with the reported data.
It's a very powerful tool, but it is not a Swiss army knife.
Some of my comments are predicated on the fact that I've used certain other firewalls for so long and have grown accustomed to certain things and therefor naturally "expect" them in other firewalls whether a valid expectation or not.
As time passes and I get more learned with pfSense I'm sure some of the things I ask now will clear themselves up.
Please keep asking the community questions. I've gained a wealth of knowledge thanks to the contributors here.
-
@stephenw10 said in New User to pfSense - some doubts:
Hmm, are you saying thr actual NIC LEDs do not blink to show activity?
That is a configurable setting on many NICs but rarely actually gets changed. No way to change it in pfSense (from the GUI).
Steve
Steve,
They do, but the way the computer sits on the shelf, they are not visible. I guess i "could" strategically place a mirror back there
But since the monitor that displays the console faces outward, it would be REALLY nice to be able to see them on the Console Screen itself.
Also in pfSense, the WAN Interface blinks pretty much ALL the time, I assume for both Outbound and inbound traffic. I only want it to blink for Inbound traffic.
-
Ah OK, I see.
Yes the WAN will blink all the time for the gateway monitoring pings at half-second intervals, by default.
Steve
-
New users Love to READ TONE Into stuff.. And it might be new to you - but to me these are the same freaking questions over and over again for 10 some years ;)
I only want it to blink for Inbound traffic.
This is just utterly moronic... To expect your firewall software to have any sort of control over how the freaking lights blink on you nic..
Name one firewall package that allows you to configure that!
-
@HansSolo said in New User to pfSense - some doubts:
Oh, and I need to find a way to at least see some blinking lights that represent active traffic across the Interfaces.
I see no reason this could not have been done on the Console and viewed onscreen same as with pftop etc.
I don't like the options of adding additional cards just to get blinking activity LEDsWe manage a lot of these devices across multiple sites, so we created a pkg to install allowing use to pull up stats over a vpn to our management system. This was to help us diagnose issues quickly for customers. Below is a screen show showing what is going through a device on my dashboard.
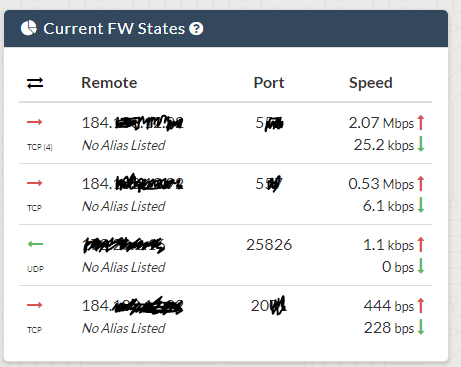
My point is this though, this information is available on the device via pfTop, traffic graphs or if you really want something you can build yourself. The later is really where pfSense beats all competitors. If you want to do something different you can build it, its a FreeBSD platform, create packages to your hearts content. You're not going to be able to do that from Sonicwall, Cisco or really most others.
From reading this thread I don't think you are seeing pfSense for its potential, rather you are just comparing it to what you have worked with in the commercial world.
-
@johnpoz said in New User to pfSense - some doubts:
New users Love to READ TONE Into stuff.. And it might be new to you - but to me these are the same freaking questions over and over again for 10 some years ;)
I only want it to blink for Inbound traffic.
This is just utterly moronic... To expect your firewall software to have any sort of control over how the freaking lights blink on you nic..
Name one firewall package that allows you to configure that!
You're funny.
Name one person who asked to change control over the network card LEDs
If you're getting tired of noobs asking the same questions,...hate to tell ya but...... welcome to being a freakin moderator. I've politely declined every time asked at a number of forums

-
@conor said in New User to pfSense - some doubts:
@HansSolo said in New User to pfSense - some doubts:
Oh, and I need to find a way to at least see some blinking lights that represent active traffic across the Interfaces.
I see no reason this could not have been done on the Console and viewed onscreen same as with pftop etc.
I don't like the options of adding additional cards just to get blinking activity LEDsWe manage a lot of these devices across multiple sites, so we created a pkg to install allowing use to pull up stats over a vpn to our management system. This was to help us diagnose issues quickly for customers. Below is a screen show showing what is going through a device on my dashboard.

My point is this though, this information is available on the device via pfTop, traffic graphs or if you really want something you can build yourself. The later is really where pfSense beats all competitors. If you want to do something different you can build it, its a FreeBSD platform, create packages to your hearts content. You're not going to be able to do that from Sonicwall, Cisco or really most others.
From reading this thread I don't think you are seeing pfSense for its potential, rather you are just comparing it to what you have worked with in the commercial world.
Thanks. Somewhat helpful. Your solution (FW States) is better (for my needs) than pftop. I suppose I could write something like that but I'd go a bit further and add my blinking lights to it. Care to share that code?
Believe it or not, I searched this forum high and low for a solution BEFORE I asked. I also searched Google. There were some solutions, but as I pointed out in the OP....they required add on cards to be installed or like pftop, didn't quite provide what I am looking for.
pftop is cumbersome for what I want.
I doubt I am seeing pftop for it's full potential....at this point. But yes, I realize I can modify it to my liking and that certainly IS a good thing. But, I do believe I also stated that in the OP or shortly thereafter (or maybe in another thread?)
Anyway...pfSense is getting better by the day.

-
@HansSolo said in New User to pfSense - some doubts:
Care to share that code?
Dude you can use any snmp monitoring you want, or use one of the agents that are supported.. Or even ones that are not - you can install netdata on pfsense if you want..
-
@johnpoz said in New User to pfSense - some doubts:
@HansSolo said in New User to pfSense - some doubts:
Care to share that code?
Dude you can use any snmp monitoring you want, or use one of the agents that are supported.. Or even ones that are not - you can install netdata on pfsense if you want..
Yeah, but dude, I like the one Conor posted ;-)
-
Well he stated he created a "package" if he wanted to give back to the community he should get it actually on the package list.
He didn't mention what management system he is using... What management system are you using? If all you want is a little widget on your desktop showing stats from firewall via snmp that is quite easy to whip together.
-
@johnpoz said in New User to pfSense - some doubts:
Well he stated he created a "package" if he wanted to give back to the community he should get it actually on the package list.
The package is hosted in our own pkg repo as it contains a number of specific data capturing functions for our company that we need, also it expects to see a vpn back to us. So in short can't just list that package. However we could extract parts and package that up and get it listed.
-
He seems to want just a blinking light ;)
There are a billion ways to monitor your systems.. If all you want to see is that pfsense is doing something simple ssh to it and run either iftop or trafshow, etc..
Here this took all of 2 seconds to bring up, and have a little window on my desktop monitor traffic flows on pfsense
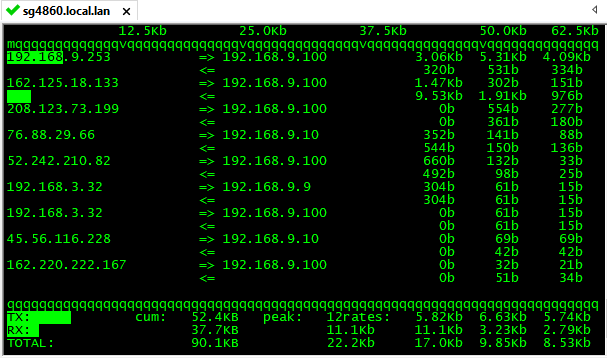
Or just fire up some simple snmp widget if you want to see a graph of wan traffic, etc. Or hits on your firewall - get really fancy and fire up a elkstack to monitor everything ;)
Or you could always just login into the gui and setup the widgets how you like to get a great overview of what is going on..
edit:
Here - 2 min of google and and simple snmpwalk to find index of wan interface on pfsense and bam little widget graphing my wan interface in/out on my windows machine.
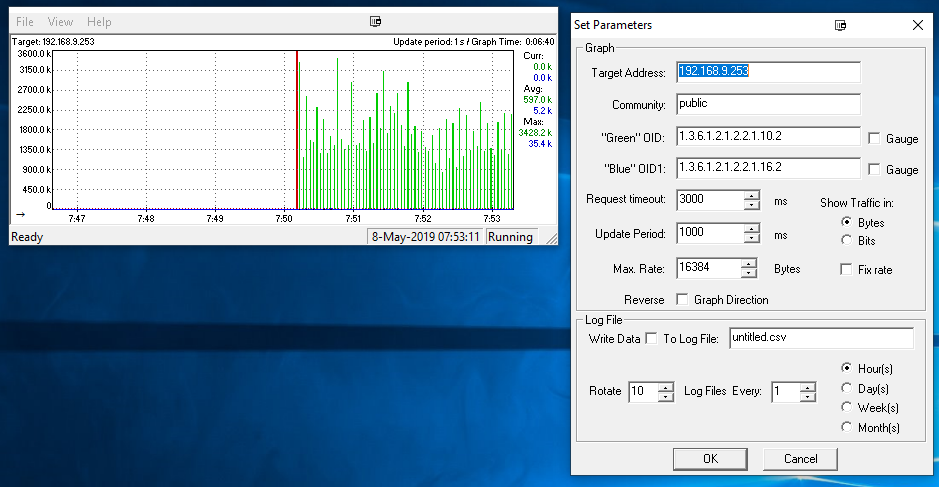
-
systat -ifstatseems to offer what you're looking for:/0 /1 /2 /3 /4 /5 /6 /7 /8 /9 /10 Load Average | Interface Traffic Peak Total bridge1 in 1.236 KB/s 1.576 KB/s 120.299 MB out 1.241 KB/s 1.353 KB/s 110.593 MB lagg0 in 0.561 KB/s 0.585 KB/s 51.941 MB out 0.577 KB/s 0.609 KB/s 51.340 MB lo0 in 0.000 KB/s 0.000 KB/s 2.756 MB out 0.000 KB/s 0.000 KB/s 2.756 MB ix3 in 0.071 KB/s 0.086 KB/s 7.092 MB out 0.515 KB/s 0.515 KB/s 42.757 MB ix2 in 0.488 KB/s 0.498 KB/s 44.849 MB out 0.062 KB/s 0.233 KB/s 8.583 MB ix0 in 0.830 KB/s 0.830 KB/s 71.975 MB out 0.816 KB/s 0.959 KB/s 69.503 MBSteve