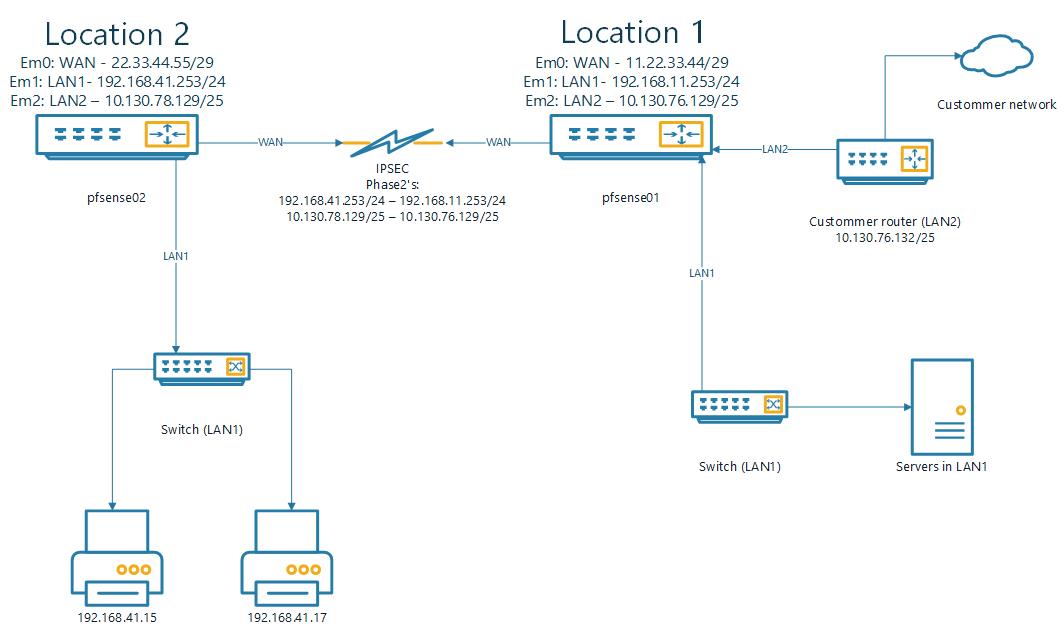
Access printer from foreign network over IPSEC (multiple locations)
-
@bashuis said in Access printer from foreign network over IPSEC (multiple locations):
Should i disconnect and reconnect the whole IPSEC connection?
if the down time isn't going to bother you probably best.
-
@conor said in Access printer from foreign network over IPSEC (multiple locations):
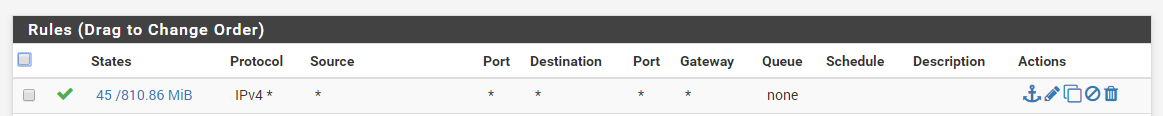
sake of testing goto Firewall > Rules > IPSEC
add an allow all rule for this interface, you can fine tune it later this is just for testingthis rule was already active (for testing) on the IPSEC interface
-
send a ping from the 172 network to the the printer ip in the 192 network, I'm half expecting this to fail, if it does check that you can still ping the 10.130.76.136 ip address.
-
@conor said in Access printer from foreign network over IPSEC (multiple locations):
@bashuis said in Access printer from foreign network over IPSEC (multiple locations):
Should i disconnect and reconnect the whole IPSEC connection?
if the down time isn't going to bother you probably best.
@conor
that is not possible now, people are working over the other P2'sif it is needed i can shedule this later today/tonight
-
@conor said in Access printer from foreign network over IPSEC (multiple locations):
send a ping from the 172 network to the the printer ip in the 192 network, I'm half expecting this to fail, if it does check that you can still ping the 10.130.76.136 ip address.
that is an problem, i have no access to the 172 network.
they started an permanent ping to 10.130.76.136 that i can use to debug.
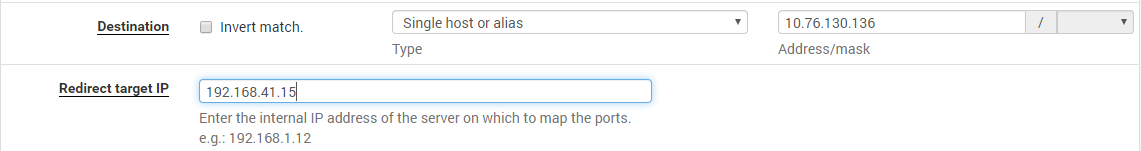
i think we should NAT? 10.130.76.136 to 192.168.41.15
packet capturing on LAN2 (pfsense01) give now:
11:52:17.648234 IP 172.16.0.26 > 10.130.76.136: ICMP echo request, id 250, seq 37518, length 36
11:52:17.648254 IP 10.130.76.132 > 172.16.0.26: ICMP time exceeded in-transit, length 36 -
@bashuis
correct, the customer router doesn't understand where the 192 is located, so a NAT is now needed, just enable the ICMP NAT first for testing. -
@bashuis said in Access printer from foreign network over IPSEC (multiple locations):
packet capturing on LAN2 (pfsense01) give now:
11:52:17.648234 IP 172.16.0.26 > 10.130.76.136: ICMP echo request, id 250, seq 37518, length 36
11:52:17.648254 IP 10.130.76.132 > 172.16.0.26: ICMP time exceeded in-transit, length 36is that with the NAT?
-
@conor said in Access printer from foreign network over IPSEC (multiple locations):
@bashuis said in Access printer from foreign network over IPSEC (multiple locations):
packet capturing on LAN2 (pfsense01) give now:
11:52:17.648234 IP 172.16.0.26 > 10.130.76.136: ICMP echo request, id 250, seq 37518, length 36
11:52:17.648254 IP 10.130.76.132 > 172.16.0.26: ICMP time exceeded in-transit, length 36is that with the NAT?
no before.
i added this NAT rule on interface LAN2 on pfsense01
now i see the same:
11:54:49.664412 IP 172.16.0.26 > 10.130.76.136: ICMP echo request, id 250, seq 41040, length 36
11:54:49.664433 IP 10.130.76.132 > 172.16.0.26: ICMP time exceeded in-transit, length 36 -
@bashuis
If the ping is failing before you add the NAT there still is the problem of pfsense01 to 172 to resolve, remove the NAT rule until that is resolved. -
can you send me the Routes for the pfsense01 please, Diagnostics > Routes
-
@conor said in Access printer from foreign network over IPSEC (multiple locations):
can you send me the Routes for the pfsense01 please, Diagnostics > Routes
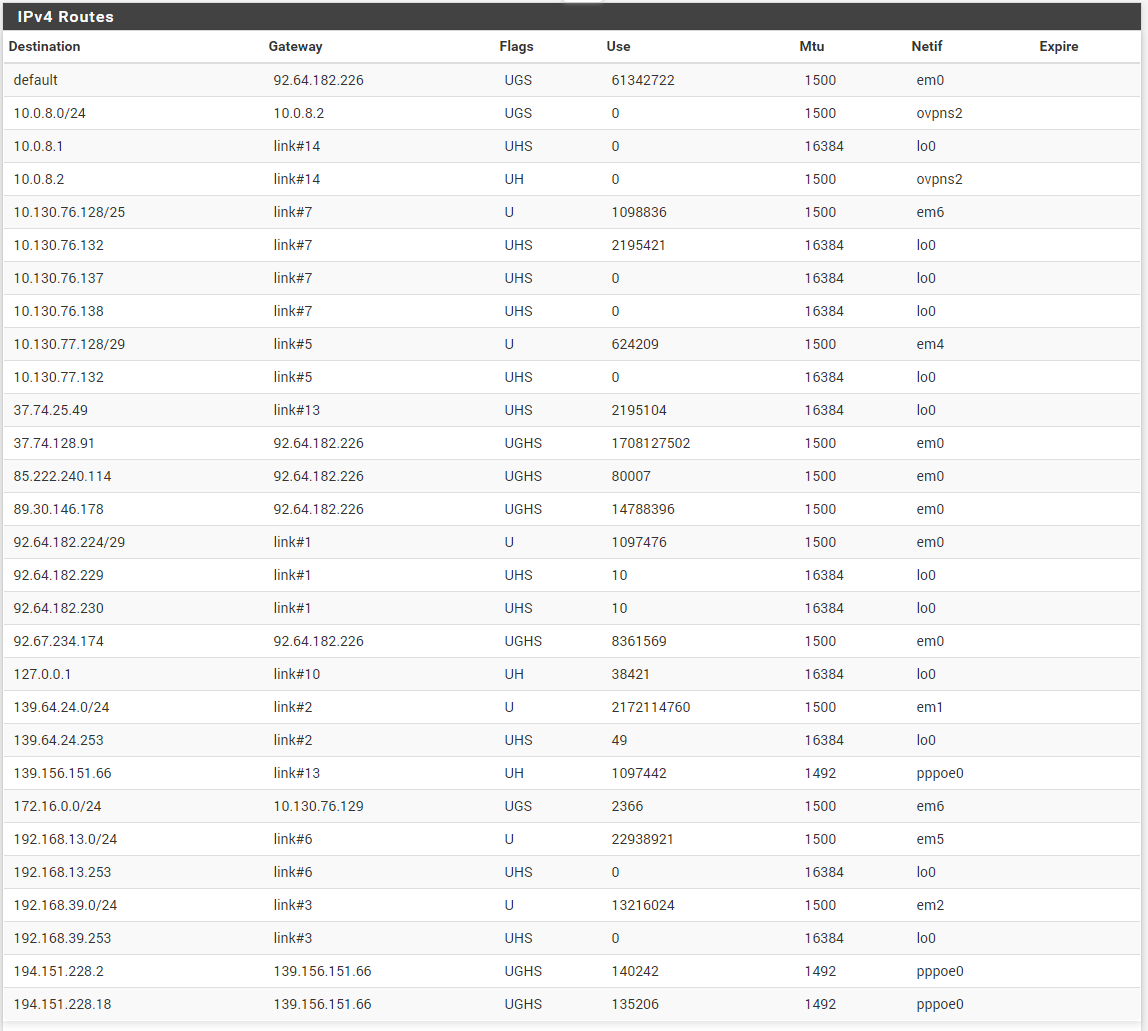
i see i have made an mistake in the ip's from the custommerrouter and LAN2 (switched, same lan). this is correct:
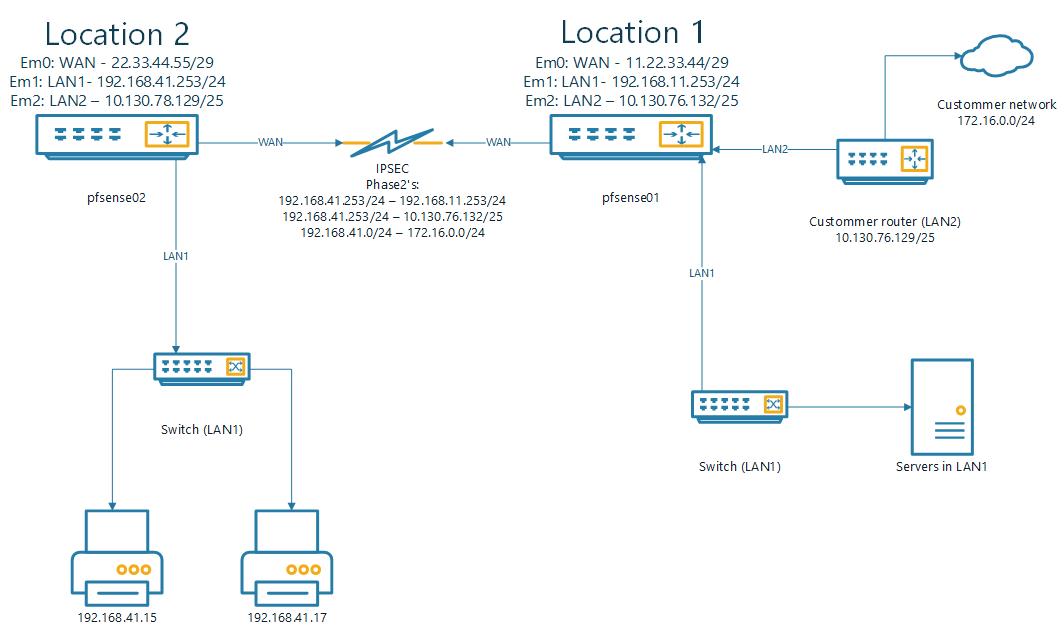
also added the new P2we could also have a look with teamviewer/telephone if you like?