Best way to separate IOTs from main LAN?
-
I am using HP T620 plus with 4-port intel ethernet. First port is for pfsense and second port for my on wifi access point. I have 3 unused ethernet ports (2 intel, 1 builtin RTL). I have a number of IOTs, e.g. Google Home Mini, Echo Dot, 3 Wifi switches, wifi printer, smart tv, etc.
What is the best way to separate these IOT devices from my LAPTOP/PC/Phone?
My pfsense now is running pfblockerng, snort, openvpn server. I also run Home Assistant on one of my mini PC; HA integrates with these IOTs.
If VLAN is needed, how should I proceed without having to reconfig all pfsense packages.Thanks.
-
Put them on a different subnet using a different NIC. Add firewall rules to prevent them accessing the LAN subnet.
It won't affect anything currently installed but you might want to add new config to use the new subnet. Add it to Snort as a new interface to monitor for example.
You might have an issue with physical connectivity setting up a completely separate subnet. VLANs would usually be employed to solve that issue, your switch(es) would need to support that.
With a completely separate subnet the biggest issue you will likely see is 'discovering' devices from clients in the LAN. Unfortunately there are many applications that for some unknown reason only allow auto discovery. DLNA media streaming tools are common offenders.
Steve
-
Thank you Steve.
If I connect another wifi access point to another port on pfsense box for a different subnet, and connect my iots to this new subnet. Would that be sufficient? I still wonder, for example, how my pc/laptop can communicate with my wifi printer if it is now connected to a different subnet. -
Yes, that would be fine.
pfSense will route between the subnets no problem. As long as you have rules on LAN allowing your PC to connect to your printer on a different subnet it will work fine. It just won't be able to auto-discover so you will have to give the printer a static DHCP lease, so it always has the same IP, and then set it up by IP in the client to print from.
Steve
-
Thanks Steve. Will the same solution can be applied to my ios devices too?
-
Yes probably, though I've never tried to do that personally. Add a printer by IP in IOS that is.
Steve
-
This post is deleted! -
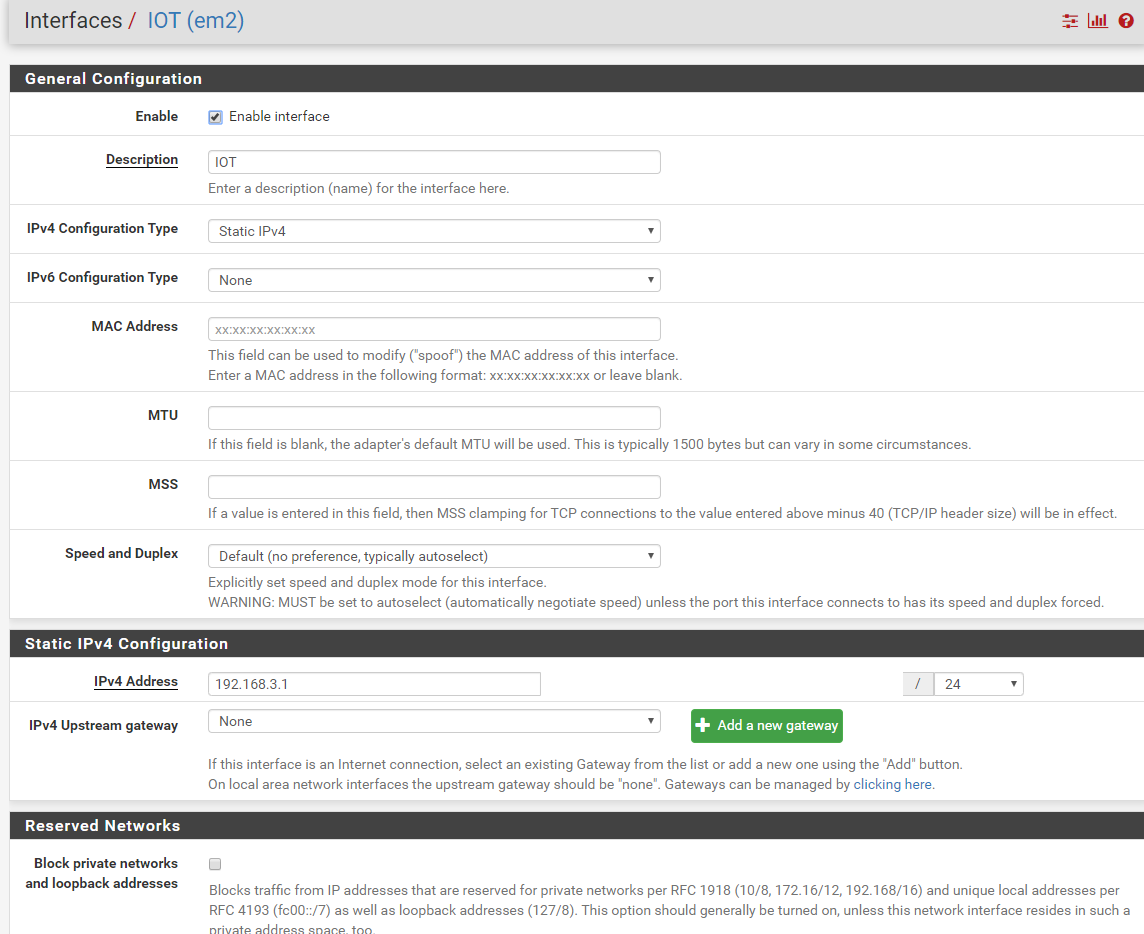
I followed this guide to add another wifi access point to another ethernet port with different subnet.
existing subnet: 192.168.2.x
new subnet: 192.168.3.xhttps://netosec.com/protect-home-network/
The problem is devices connected to this new subnet cannot connect to internet. The gateway IP when connected is 192.168.3.1.
The devices from existing subnet can access the devices in the new subnet, but not the other way round, as intended.
I need another help. Thanks.
-
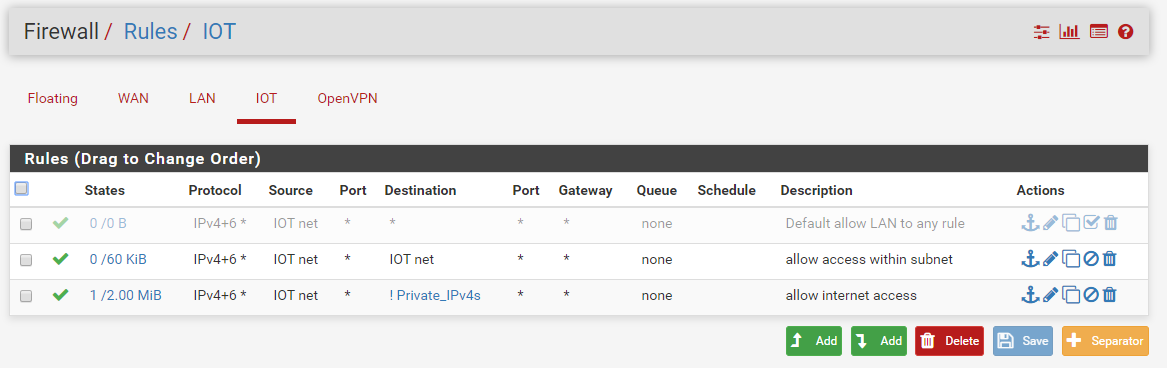
When you add the new interface there will not be any firewall rules present which means everything will be dropped inbound.
It looks like that guide covers adding firewall rules but you will need to have added a pass rule at a minimum to allow devices to connect out.
Can we see a screenshot of your rules on the new subnet?
Steve
-
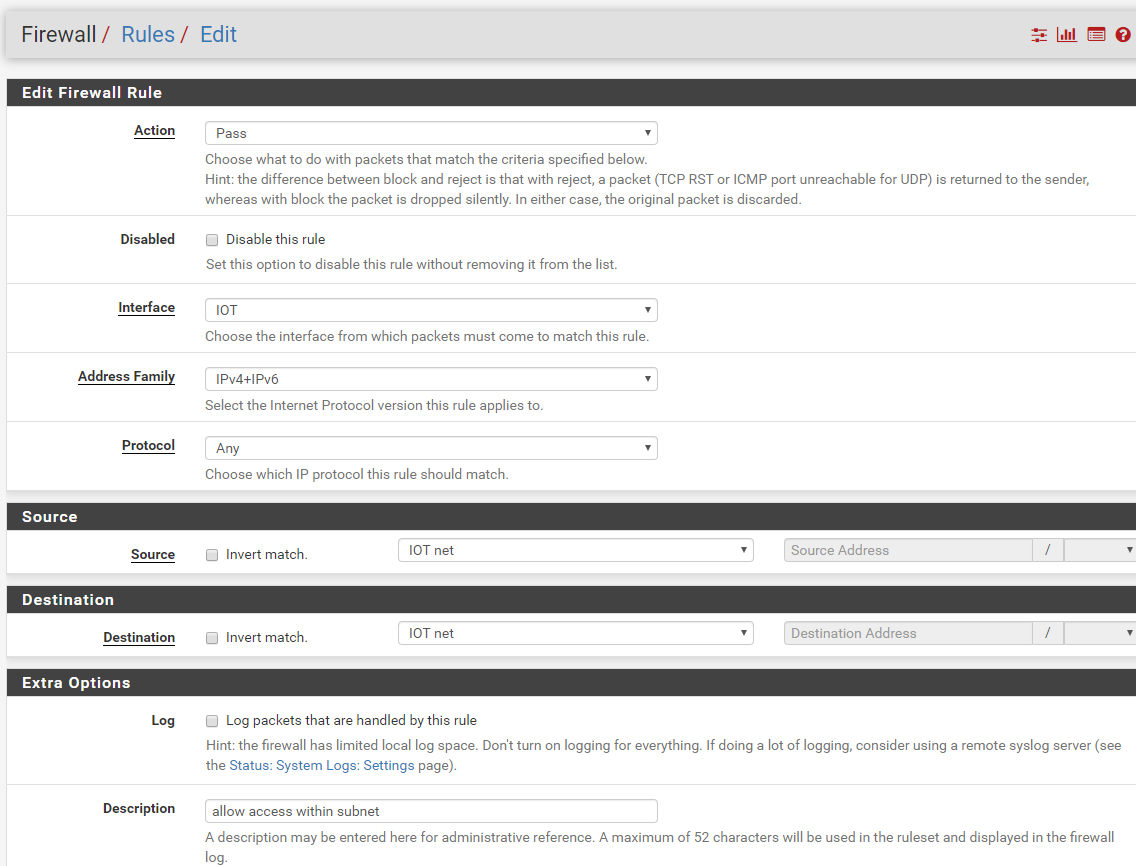
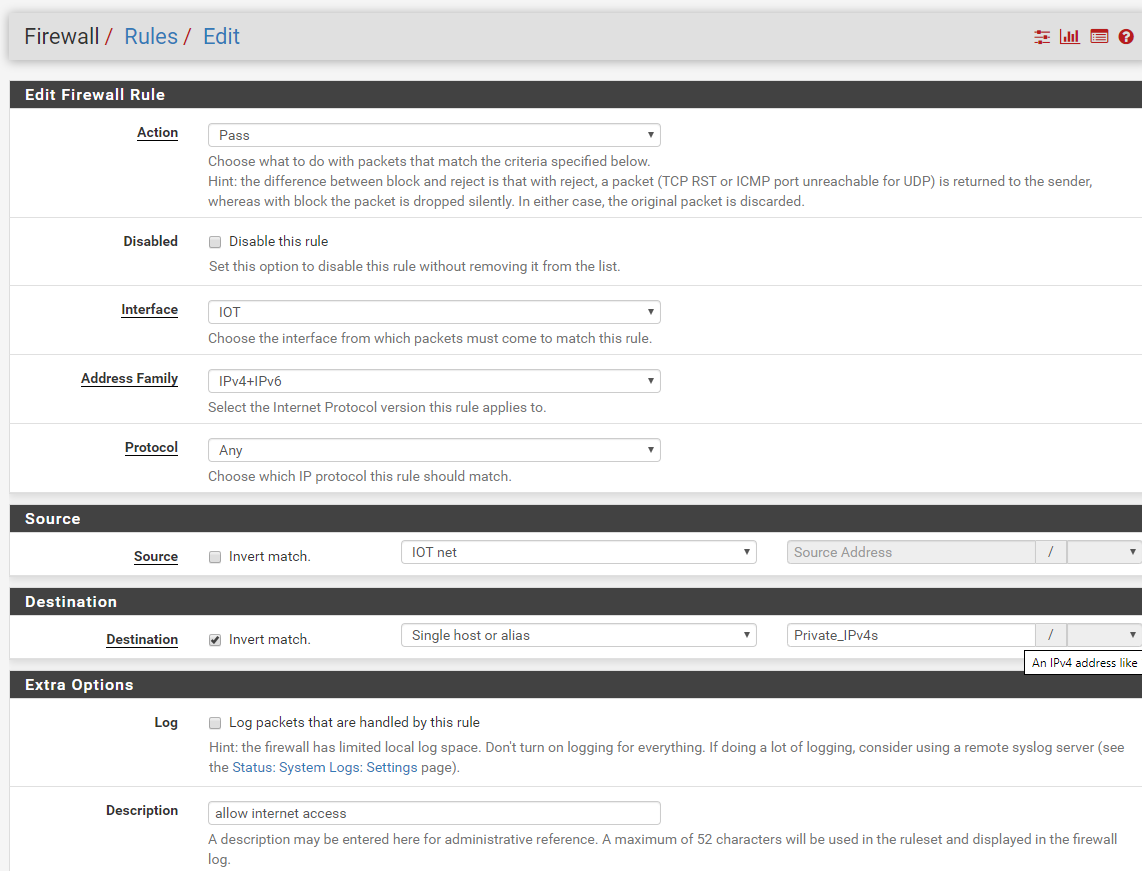
Here they are:
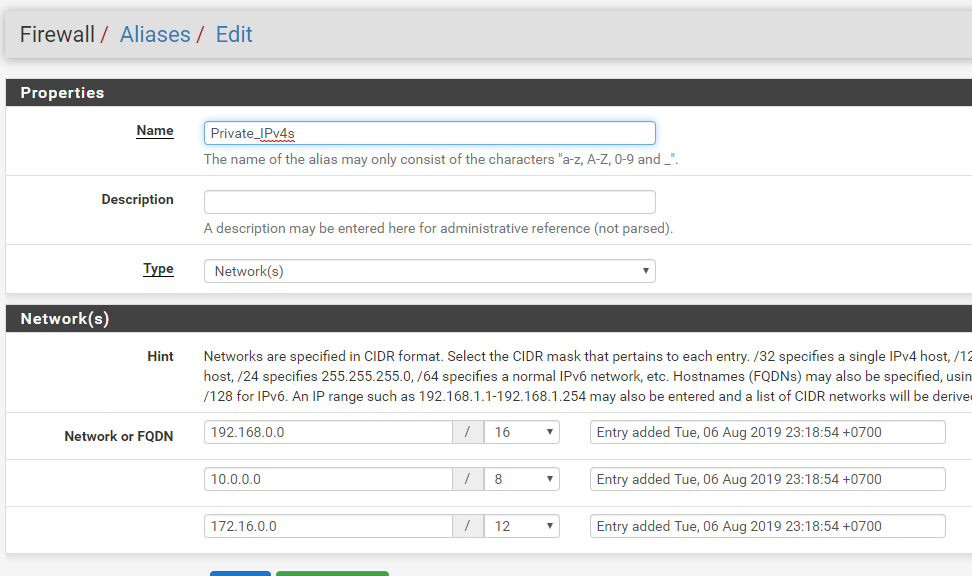
-
Also if your using a vpn client to send your traffic to a vpn, and followed most of the idiot guides out there and set your outbound nat to "manual" then pfsense would not have created the required outbound nat for your new network.
Your allow iot subnet rule is pointless.. Other than that would allow access to pfsense IP on that segment for dns.. But clients on this network don't talk to pfsense to talk to other devices on the network.
So the rule should really just allow access to the IOT address not the network.
Also using the bang allow, if your using a VIP, say for example the vip pfblocker creates.. That rule could have problems depending..
-
Thanks for your reply.
Sorry, I'm not quite sure what to amend. I do not have VPN client set up; only VPN Server for secured remote access.
Could you clarify more what I should set up. Even I copy the rule from LAN interface to my IOT interface, I got internet access status, but can't access any websites.
-
Is your Outbound NAT still set to the default 'automatic' in Firewall > NAT > Outbound?
Steve
-
here is the outbound
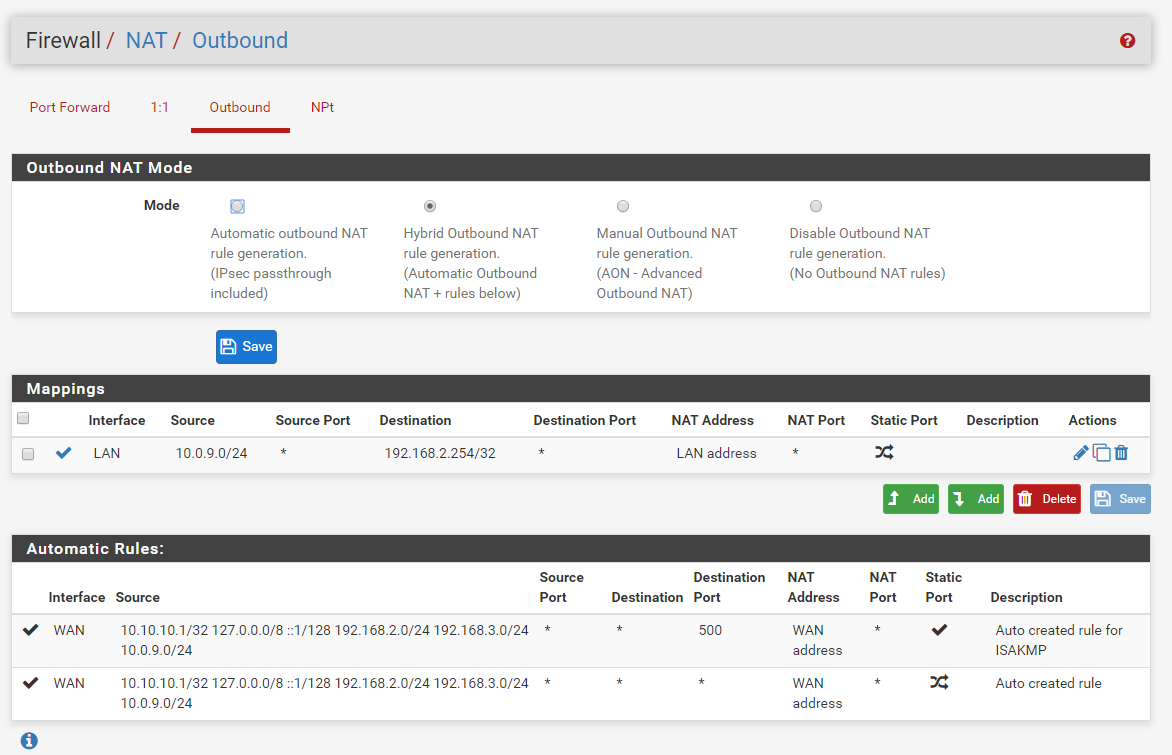
-
I'm not sure the DNS Resolver setting is relevant. Now in Network Interfaces, I can choose LAN and Local Host. When I tried to choose ALL ans save, pfsense seems to be quite busy and I have to wait a very long time before it came back, and the setting reverts to LAN and Local Host again. I tried selecting ALL 3 times, and got the same behavior.
Outgoing Network Interface: WAN only.
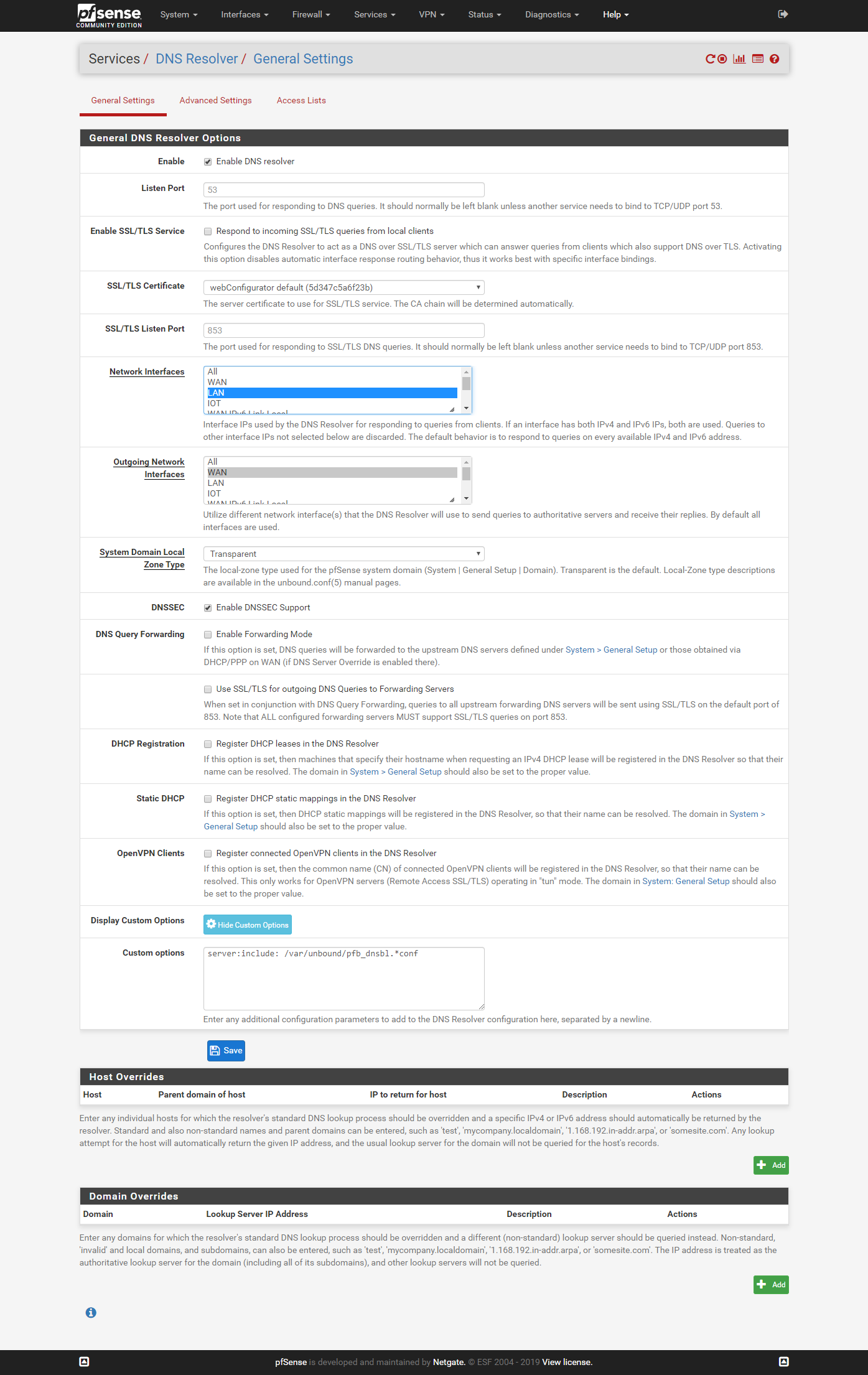
-
Ah, Ok you won't have internet without DNS. You need at least Localhost, LAN and IOT set there for it to listen on.
By default it runs on all though so that should work. Check the system and resolver logs are setting all for errors.
Steve
-
Thanks. I add IOT to Network Interface, press save, and it is now running.................same symptom as when I selected ALL........still waiting..............
-
I waited for almost 10 mins and it came back without IOT selected in the Network Interface (DNS Resolver); and the Resolver stopped.
-
You have to allow your clients to talk to dns if you want internet to work.. Be it the iot interface of pfsense, the lan interface... Or something external - but no internet is not going to work if you don't have dns. Unless you just going to IP address for everything ;)
-
If unbound fails to apply that change there should be some error logged either in the system or resolver logs, or both.
Do you have pfBlocker enabled with DNS-BL? If not that advanced option could be left over cruft.
Steve