opening ports on firewall
-
@johnpoz I've already asked for screens and told him to do a packet capture but that advice was ignored.
-
Your post stated lan, which sure is step 2... But he needs to actually validate the traffic gets there before anything.
-
List of things to check here:
https://docs.netgate.com/pfsense/en/latest/nat/port-forward-troubleshooting.html
-
@johnpoz said in opening ports on firewall:
@richardlhughes said in opening ports on firewall:
I called them and they told me they are not blocking any ports.
1st step in troubleshooting any port forward issues is actually validate the traffic gets to your wan... There is nothing pfsense can do if traffic never gets there.
So this should always be step one... its as easy as going to say can you see me .org and testing for port 80 while you sniff on your wan... Do you see it get there?
Doesn't matter what your ISP says.. they might not be blocking it, but maybe something else is - say a nat router in front of pfsense for example..
Another way to figure out if the ISP is not blocking ports is to use GRC service port scan.
https://www.grc.com/x/ne.dll?rh1dkyd2
They basically suggest running the All service port scan on a device not behind a NAT and with software firewall disabled (unprotected). Any ports that come up as stealth are most likely being blocked by your ISP. After running the test if you scroll down the Service Ports Scan Application Guide, you'll see more details on that. Of course don't forget to reenable the firewall after the test. -
That does not guarantee that something upstream is not responding on your behalf.
The only way to be 100% sure the traffic is arriving on your WAN is to packet capture on your WAN. If it does not arrive there, pfSense cannot forward it.
-
@johnpoz I tend to do it the other way around because in my experience, the traffic almost always gets to WAN. The problem is usually with the NAT itself or some other PEBKAC thing.
-
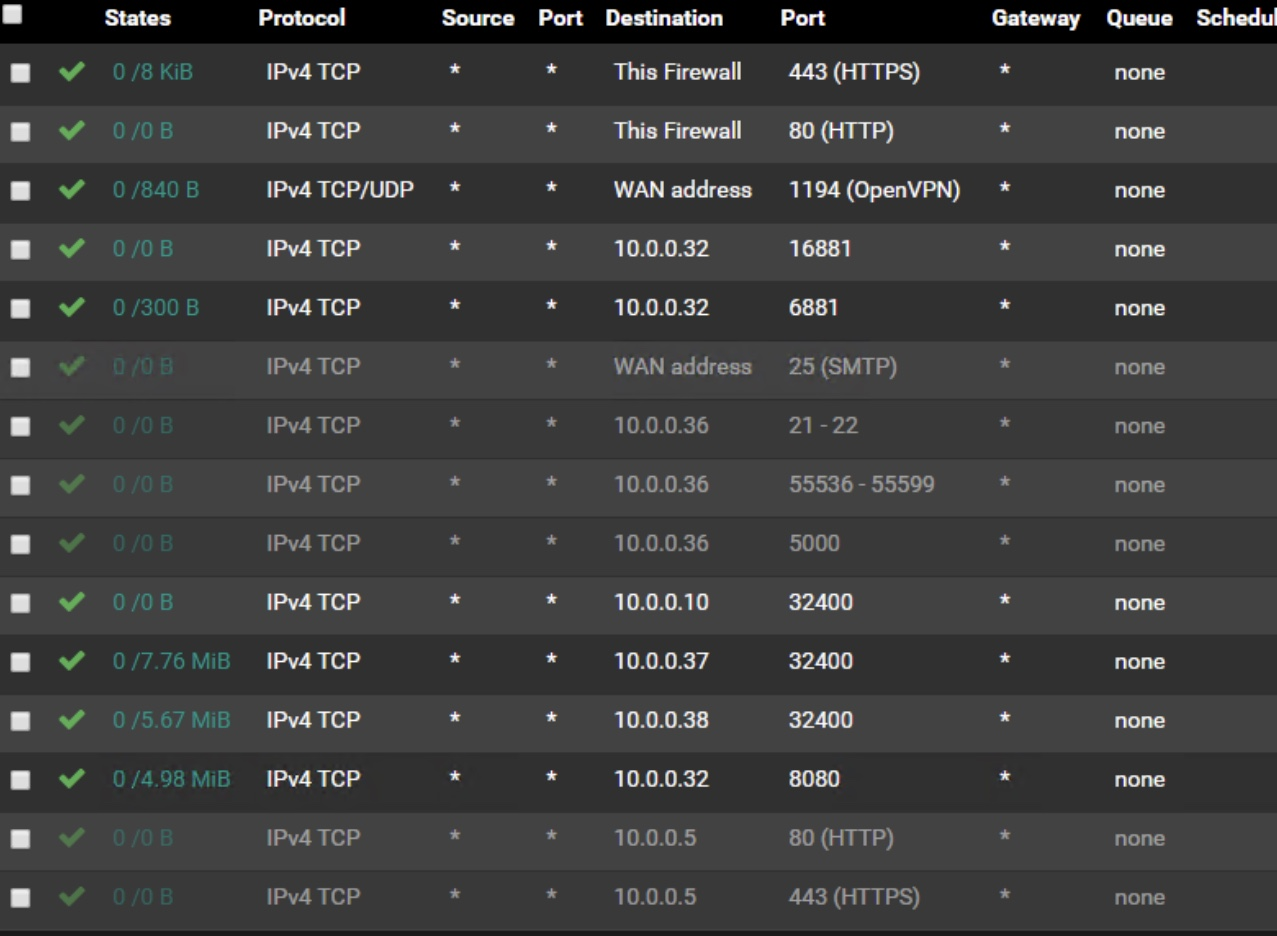
Wan Rules
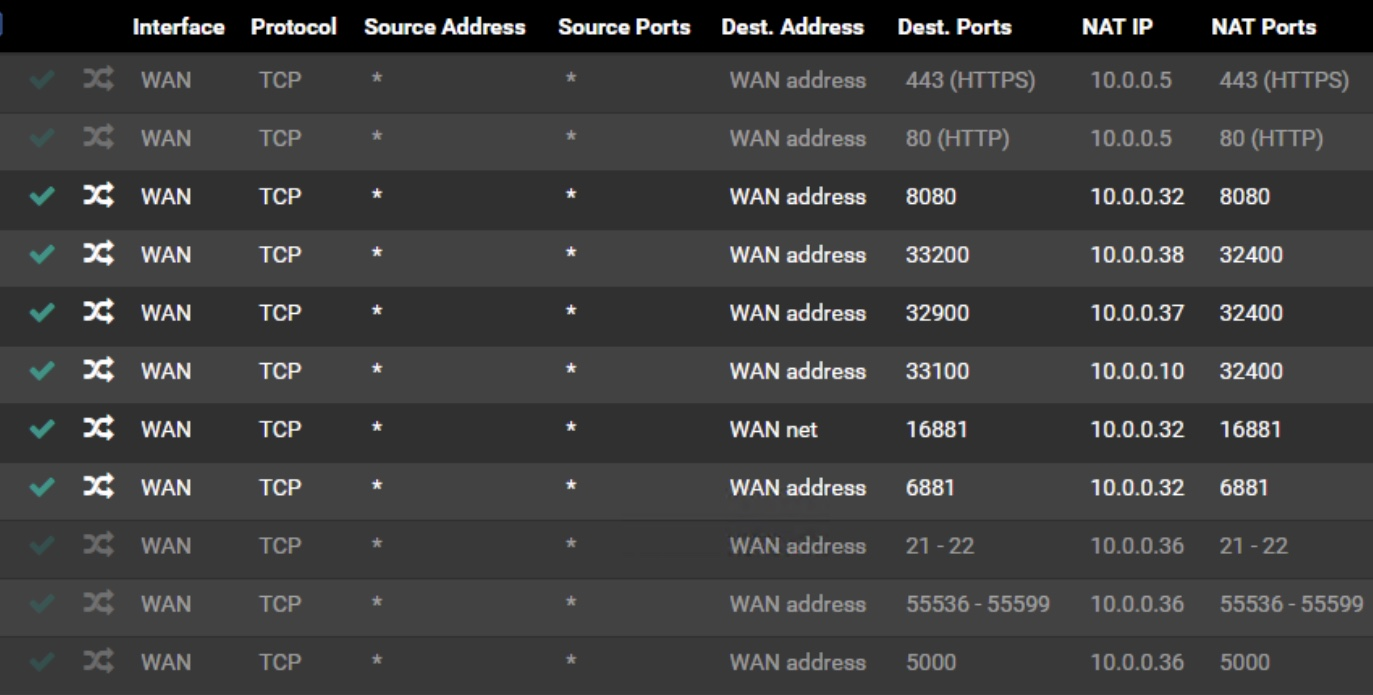
NAT Rules
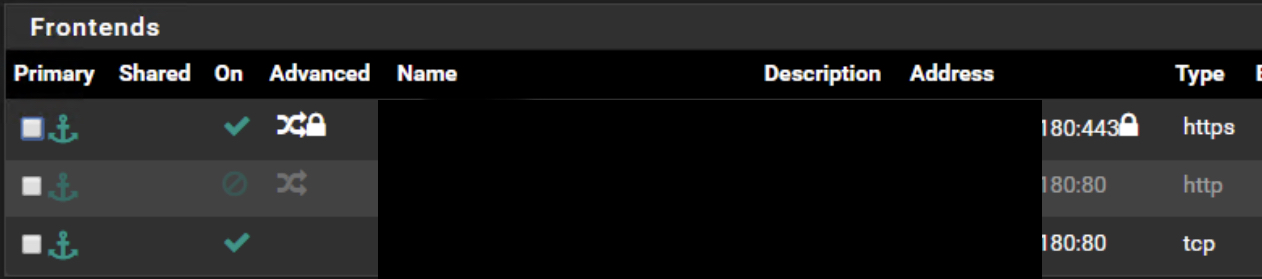
HAPROXY (I've tried http and tcp for port 80 and cannot get port 80 open)
-
@Derelict I have checked this list a couple times now. Didn't see anything standing out.
-
Alright, your NAT rules look correct, might want to make the protocol both TCP/UDP, and not just TCP.
Your WAN rules are incorrect. Your FIRST set of 443 and 80 allow traffic to just your firewall, not another LAN machine. If you move these two new bottom rules to the very TOP of your firewall rule list, the traffic should move like you are expecting/hoping.
Firewall rules are evaluated top down, first to match wins. That's why nothing is hitting 10.0.0.5, 80 and 443 are bouncing around inside the firewall itself, due to the first 2 top rules.
Jeff
-
I don't know what didn't see anything standing out means. Did you see the SYN arrive or not?
If you packet capture on WAN for port 32900 and test from the outside, you should see the SYN packet arrive.
If you see it, then move your capture to the inside interface for port 32400, you should see the SYN packet sent to 10.0.0.37.
If there is no response, look at the server (10.0.0.37) and see why.
-
@akuma1x said in opening ports on firewall:
Alright, your NAT rules look correct, might want to make the protocol both TCP/UDP, and not just TCP.
Pet peeve of mine. You shouldn't just randomly forward traffic. You should know if you need TCP, UDP, or both and forward what is required.
If he pcaps filtering on just the port, it will show both.
-
@Derelict I didn't do the packet capture on the WAN, the troubleshooting list.
How do I setup packet capturing on the WAN? is this something I can setup on my pfsense machine or what is the best method?
-
diagnostic menu, packet capture.. put in the port your wanting to check, wan and click start... Then send the test traffic to that port.
-
Diagnostics > Packet Capture:
Interface: WAN
Port: 32900Start, Test, Stop, Evaluate.
-
@akuma1x said in opening ports on firewall:
Alright, your NAT rules look correct, might want to make the protocol both TCP/UDP, and not just TCP.
Your WAN rules are incorrect. Your FIRST set of 443 and 80 allow traffic to just your firewall, not another LAN machine. If you move these two new bottom rules to the very TOP of your firewall rule list, the traffic should move like you are expecting/hoping.
Firewall rules are evaluated top down, first to match wins. That's why nothing is hitting 10.0.0.5, 80 and 443 are bouncing around inside the firewall itself, due to the first 2 top rules.
Jeff
Using the HA Proxy and not NAT the machine directly I don't think I need the firewall rule to the web server directly on the WAN. I have the NAT for port 80 and 443 disabled along with those firewall rules. I can put 2 new rules to wan to the webserver and see if that works.
-
Using HAproxy is a completely different thing. In that case you would need rules passing traffic to the frontend(s).
-
And we still don't have a 30 second sniff of wan..
-
The first two WAN rules should probably be "WAN Address" instead of "This Firewall".
Just a guess.
-
I have the wan packets capture what do you wan me to post here?
-
Just enough to show the traffic is hitting WAN.
If it is, then a pcap for the proper traffic on LAN.