HEADS UP: Be aware of Trusted Recursive Resolver (TRR) in Firefox
-
@kiokoman said in HEADS UP: Be aware of Trusted Recursive Resolver (TRR) in Firefox:
An application switching to DoH should ensure that this switch does not undermine choices that have been previously made by the user
All of which just SCREAMS this can not be opt-out, but MUST be OPT-IN to switch...Where the users has to specifically do something to actually use it, vs just using the OS already set dns..
edit:
I think the thought process has gone something like this.
Q: How can we mine more data from our users without logging and sending the info where they go.. "telemetry" they don't seem to like that.A: Lets have them use us for dns, so that we know everywhere they they go.
Q: How can we get them to do that?
A: We will tell them its for their own security, from the bad isp they are paying every month for internet.Q: Well they are not switching over fast enough, and we don't want to actually spend any money on PR to have them think this is best option for their "security/privacy"
A: Lets just switch them over, and state that is for their own good if they complain, because they are just too stupid anyway.
-
https://apple.news/AREysIdXnROWCIANTguz06A
Not sure if the link will work, they are trying a personal vpn now..
-
They can offer whatever they want - just don't freaking make something like that default... If the user has to turn it on, and make an effort to use it..
-
So I found this listing of known doh servers
https://github.com/curl/curl/wiki/DNS-over-HTTPS#publicly-available-serversI have a pm out of @BBcan177 asking if he plans on easy way of blocking these in pfblocker, if not will be working my own listing of them to use in firewall rules and host overrides to block queries for them.
Will prob have dns queries for their fqdn point to a specific IP that I block and log, and any hits to that rule get attention and any devices doing it will if not easy to disable be off the network..
-
I'd also use
local-zone: "use-application-dns.net" staticin the DNS Resolver "custom options" box so to answer with an NXDOMAIN to the canary domain Mozilla uses. Won't help if they switch their approach or simply use a service manually entered but at least the "automagic switch" should be off then.
-
Yeah been in place for some time already ;)
Notice I posted how to do it like 8 days ago ;) Look back over the thread..
-
@johnpoz said in HEADS UP: Be aware of Trusted Recursive Resolver (TRR) in Firefox:
I have a pm out of @BBcan177 asking if he plans on easy way of blocking these in pfblocker, if not will be working my own listing of them to use in firewall rules and host overrides to block queries for them.
Some more details here for now until I add this officially to pfBlockerNG:
https://www.reddit.com/r/pfBlockerNG/comments/d3p1gf/doh_server_blocklist/
-
Thanks - but you the have the
use-application-dns.netIn there - that would not return an NX, so it wouldn't work per my understanding of how the firefox canary is suppose to work.. It has to get back a NX to not enable it from my understanding.
I threw this together real quick this morning from list linked to earlier.
local-data: "dns.adguard.com. 120 IN A 172.19.19.19" local-data: "dns-family.adguard.com. 120 IN A 172.19.19.19" local-data: "dns.google. 120 IN A 172.19.19.19" local-data: "cloudflare-dns.com. 120 IN A 172.19.19.19" local-data: "dns.quad9.net. 120 IN A 172.19.19.19" local-data: "dns9.quad9.net. 120 IN A 172.19.19.19" local-data: "dns10.quad9.net. 120 IN A 172.19.19.19" local-data: "doh.opendns.com. 120 IN A 172.19.19.19" local-data: "doh.cleanbrowsing.org. 120 IN A 172.19.19.19" local-data: "dns.nextdns.io. 120 IN A 172.19.19.19" local-data: "dns.dnsoverhttps.net. 120 IN A 172.19.19.19" local-data: "doh.crypto.sx. 120 IN A 172.19.19.19" local-data: "doh.powerdns.org. 120 IN A 172.19.19.19" local-data: "doh-ch.blahdns.com. 120 IN A 172.19.19.19" local-data: "doh-jp.blahdns.com. 120 IN A 172.19.19.19" local-data: "doh-de.blahdns.com. 120 IN A 172.19.19.19" local-data: "dns.dns-over-https.com. 120 IN A 172.19.19.19" local-data: "doh.securedns.eu. 120 IN A 172.19.19.19" local-data: "dns.rubyfish.cn. 120 IN A 172.19.19.19" local-data: "doh-2.seby.io. 120 IN A 172.19.19.19" local-data: "doh.seby.ie. 120 IN A 172.19.19.19" local-data: "commons.host. 120 IN A 172.19.19.19" local-data: "doh.dnswarden.com. 120 IN A 172.19.19.19" local-data: "dns-nyc.aaflalo.me. 120 IN A 172.19.19.19" local-data: "dns.aaflalo.me. 120 IN A 172.19.19.19" local-data: "doh.appliedprivary.net. 120 IN A 172.19.19.19" local-data: "doh.captnemo.in. 120 IN A 172.19.19.19" local-data: "doh.tiar.app. 120 IN A 172.19.19.19" local-data: "doh.dns.sb. 120 IN A 172.19.19.19" local-data: "rdns.faelix.net. 120 IN A 172.19.19.19" local-data: "doh.li. 120 IN A 172.19.19.19" local-data: "doh.armadillodns.net. 120 IN A 172.19.19.19" local-data: "doh.netweaver.uk. 120 IN A 172.19.19.19" local-data: "jp.tiar.app. 120 IN A 172.19.19.19" local-data: "doh.42l.fr. 120 IN A 172.19.19.19"Here is sample query for one of those.
;; QUESTION SECTION: ;doh.dns.sb. IN A ;; ANSWER SECTION: doh.dns.sb. 120 IN A 172.19.19.19Simple add that to your custom box in unbound, then put a block log rule in place that logs anything that tries to go to my out of thin air IP that I do not use locally 172.19.19.19
This way I can see if anything is trying to resolve this by just looking if any hits in the firewall rules, and then look into the logs to which IP tried and investigate what its trying to do exactly.
Keep in mind, this could cause you some grief if any of those fqdn are serving up stuff other than doh that you might want to get to.. Some are on other ports other then 443, so I just made the block rule any..
-
bind9
$TTL 60 @ IN SOA localhost. root.localhost. ( 2019091601 3H ; refresh 1H ; retry 1W ; expiry 1H) ; minimum IN NS localhost. ; Make TRR unavailable dns.adguard.com 120 IN CNAME . dns-family.adguard.com 120 IN CNAME . dns.google 120 IN CNAME . cloudflare-dns.com 120 IN CNAME . dns.quad9.net 120 IN CNAME . dns9.quad9.net 120 IN CNAME . dns10.quad9.net 120 IN CNAME . doh.opendns.com 120 IN CNAME . doh.cleanbrowsing.org 120 IN CNAME . dns.nextdns.io 120 IN CNAME . dns.dnsoverhttps.net 120 IN CNAME . doh.crypto.sx 120 IN CNAME . doh.powerdns.org 120 IN CNAME . doh-ch.blahdns.com 120 IN CNAME . doh-jp.blahdns.com 120 IN CNAME . doh-de.blahdns.com 120 IN CNAME . dns.dns-over-https.com 120 IN CNAME . doh.securedns.eu 120 IN CNAME . dns.rubyfish.cn 120 IN CNAME . doh-2.seby.io 120 IN CNAME . doh.seby.ie 120 IN CNAME . commons.host 120 IN CNAME . doh.dnswarden.com 120 IN CNAME . dns-nyc.aaflalo.me 120 IN CNAME . dns.aaflalo.me 120 IN CNAME . doh.appliedprivary.net 120 IN CNAME . doh.captnemo.in 120 IN CNAME . doh.tiar.app 120 IN CNAME . doh.dns.sb 120 IN CNAME . rdns.faelix.net 120 IN CNAME . doh.li 120 IN CNAME . doh.armadillodns.net 120 IN CNAME . doh.netweaver.uk 120 IN CNAME . jp.tiar.app 120 IN CNAME . doh.42l.fr 120 IN CNAME .i can change the dot to some "out of thin air ip" if i want to log, reporting NX for the moment
laboratorio@server:/$ dig @127.0.0.1 doh.crypto.sx ; <<>> DiG 9.11.3-1ubuntu1.9-Ubuntu <<>> @127.0.0.1 doh.crypto.sx ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NXDOMAIN, id: 10547 ;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 2 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ; COOKIE: dda6e2c23949f6cda855e6485d7fa7fddeb8459af20d8f8b (good) ;; QUESTION SECTION: ;doh.crypto.sx. IN A ;; ADDITIONAL SECTION: overrides. 60 IN SOA localhost. root.localhost. 2019091601 10800 3600 604800 3600 ;; Query time: 4 msec ;; SERVER: 127.0.0.1#53(127.0.0.1) ;; WHEN: Mon Sep 16 17:19:25 CEST 2019 ;; MSG SIZE rcvd: 129 -
Only reason pointed it to an IP, is I normally don't log dns queries - there are so freaking many of them it can be information overload to weed through... I only enable dns query logs when wanting to troubleshoot a specific issue.
Figured if I point it to a specific IP, I can log any attempted access to that odd IP so can see at a glance in the firewall interface if any hits to it. And then investigate..
Multiple ways to skin the cat is best, so no matter what what users are using specific in there setups they have a easy way to skin this one..
These little devices could bypass these method with a direct query to the IP.. So prob need to put together an alias that lists the actual public IPs and blocks.. This is going to turn into such a shit show..
Uncontrolled circumvention of a local networks controls is not by any stretch of the imagination good for anyone!
-
Was just shown this by colleague: https://bsd.network/interact/102767562311572315
Had to laugh ;) -
This resolver now points to https://mozilla.cloudflare-dns.com/dns-query instead of https://cloudflare-dns.com/dns-query
-
@JeGr said in HEADS UP: Be aware of Trusted Recursive Resolver (TRR) in Firefox:
canary
But the canary stayed the same, so that should already disable it.
-
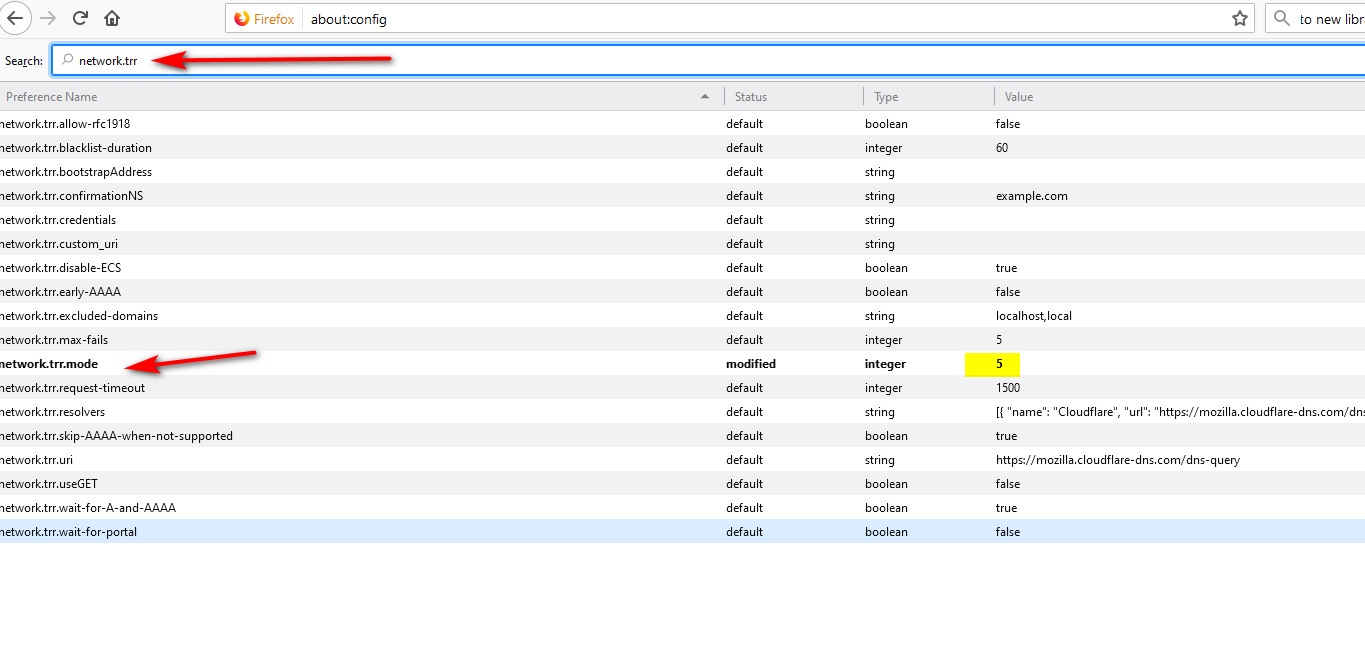
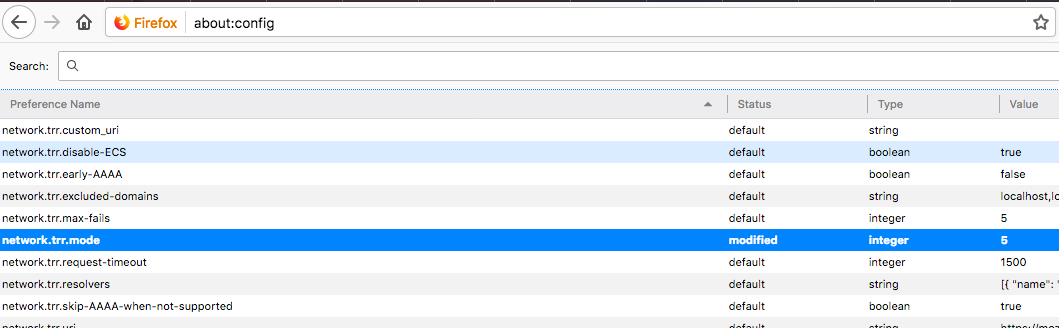
I have been reading this thread and have added the list found in the link that BBcan177 provided above to DNSBL. However, where is the about:config mentioned by Jim so I can set network.trr.mode to 5? This is what I saw in Firefox preference:
-
in the about:config section
-
@johnpoz Thanks John for responding...it seems that Macs don't have that options...I am using Firefox 69.0.2...
-
I don't have a mac to test with.. But your at about:preferences not about:config?
No you wouldn't find it there - see I went there in my windows firefox
-
@johnpoz Found it John...one has to type about:config in the URL bar and accept the risk...thank you!
-
I've just tried the unbound custom option... it seems Firefox keeps asking for its DoH stuff, Suricata seeing some associated traffic.
1 TCP A Network Trojan was Detected 10.X.X.X 51133 104.16.249.249 443 1:2027695 ET POLICY Observed Cloudflare DNS over HTTPS Domain (cloudflare-dns .com in TLS SNI) -
Did you set TRR in firefox to 5? Without some details of what you actually did there is little anyone can do to help you find out what you did wrong.
You need to make sure unbound return NX..
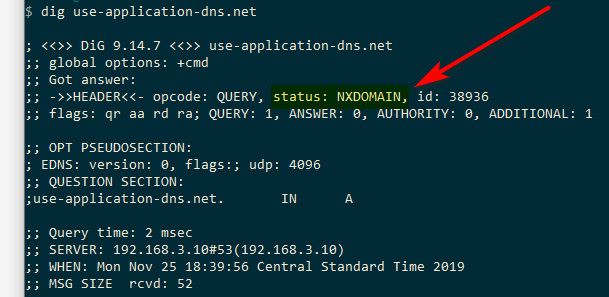
I watch this like a hawk and have rules in place to log any sort of doh to any of the know ns doing doh, and block tos - and have not seen any hits on the rules at all.