pfSense on Hyper-V Home Setup questions.
-
You do understand pfsense can have multiple lan side interfaces right, and VM switches can be tied to physical network a well.. Maybe your issue is you don't actually get how VM Hosts work?
Your drawing is tied to both physical and virtual networks - so not sure why your confused?
-
I know how Hyper-V works..The actual reason that I am confused, is that I can't ping pfsense from my physical PC nor I can admin it.
Physical PC : 192.168.2.108
Pfsense Internal side : 192.168.2.10both on the same LAN/VLAN.
-
Well then you have something setup wrong. Or not connected how you think its connected, etc.
-
@johnpoz Yeah I guess so. I will try to find the reason. There is no reason to bother you with that kind of questions but I will come back if I cant make it work.
Thank you ALL for your precious help! This community seems to be totally ALIVE!
-
For this, both your LAN and WAN switches should be External.
Private - allows VM to VM comms
Internal - allows VM to VM comms plus comms to Host
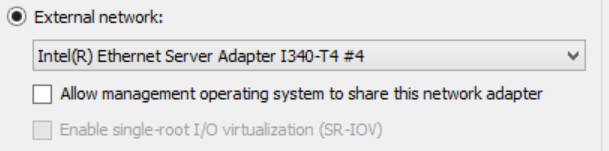
External - As above, plus outside worldOn the LAN v-switch, you can select the sharing checkbox below (I don't on mine because i have a 4-port NIC where I assign the host a port of its own). Then you can manage the VM from the host OS.
I just run a flat network with no VLANs. I don't really see the point in a home setup, just more complexity.Internet--Modem--Host--pfSense--Switches--Access Points--Clients
Only reason I'd use a VLAN would be it I was trying to use a single NIC board as a pfSense hardware firewall (Router-on-a-stick). You could use your Asus as an AP by just plugging one of the LAN (not WAN) ports into your network as long as the LAN side is configured as the same network as the rest of your LAN, but you'd still need to buy a modem. HTH
-
@provels said in pfSense on Hyper-V Home Setup questions.:
I don't really see the point in a home setup, just more complexity.
Do you have more things on this flat network than just your PC or a couple of devices - iot, stuff that is serving up to the internet, etc.. You would use vlans or other network segments as a means to secure your network..
He doesn't need a modem - he needs an AP he can use his current device as just the modem and turn off its wifi.. Or use it as well as different non filtered wifi network that is on the "wan" side of pfsense.
-
@johnpoz No IoT, even though my refrigerator and dishwasher could talk to the world if I desired it. No Alexa or other because I would want an always-on mic in my house..., why? I have no desire to talk to any device unless it is a phone and there is a live body on the other end. Several network receivers, couple phones, Hyper-V host that is also my main workstation with pfSense and several other workstation OS, smart TV, and a lappy for RDP. I even run G wireless with MAC filtering and hidden SSIDs (the horror!) And it's just me, so.... no need for guest nets. And no FB or Twitter even, because that is just largely the toilet of the Internet. anyway. So there.
Agreed, I know he doesn't need a modem, but he will have to buy something to do what he wants. Frankly I'd just ditch the gateway on EBay and buy discreet components. Kind of depends how many of his clients are in use simultaneously as well.
-
@provels said in pfSense on Hyper-V Home Setup questions.:
I even run G wireless with MAC filtering and hidden SSIDs
Because that is pointless ;) And you like added pain for no reason?
-
@johnpoz Point? I have trusted devices in family, anyone else can pay for their own data.
-
None - its pointless to do such a thing.. You just added complexity for ZERO reason other than your own grief.. But someone segmenting out their network for actually security reasons is pointless complexity?
If you don't want someone on your wifi - then don't give them the PSK.. There is zero reason for mac filtering or not broadcasting the SSID.
-
@johnpoz Well, if you can find me, feel free to hack my wireless. At any rate, it still depends WHY he wants to do it. Just because you CAN doesn't mean you SHOULD. Sort of how I feel about running a DC on a home net...
-
So, for my pfsense, to be able to "talk" to the physical workstations on the network, there must be two external virtual switches on the hyperv hosts right?
-
@uxm said in pfSense on Hyper-V Home Setup questions.:
So, for my pfsense, to be able to "talk" to the physical workstations on the network, there must be two external virtual switches on the hyperv hosts right?
Yep, and one pf interface min hooked to each.
-
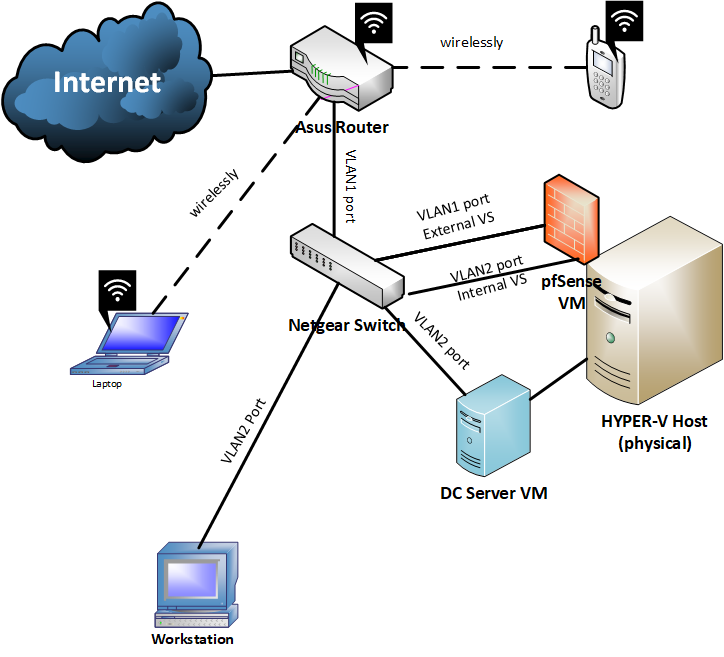
Sorry for returning back after so long. I had some personal issues and didnt have the time for pfsense. I will try to continue this project. So, I have a Hyper-V with 2 VMs. One is the pfsense VM and the other is my DC (for my Active Directory) with Windows 2012 R2 installed. The Hyper-V host has three NICs. I gave two nics for the pfsense (lan and wan) and one nic to my Windows 2012 R2 DC Server.
I have a netgear manageable switch. How many VLANs I have to create? Two right? One is the "wan side VLAN" and the other is the "LAN side VLAN" right?
Can you help me please?..
-
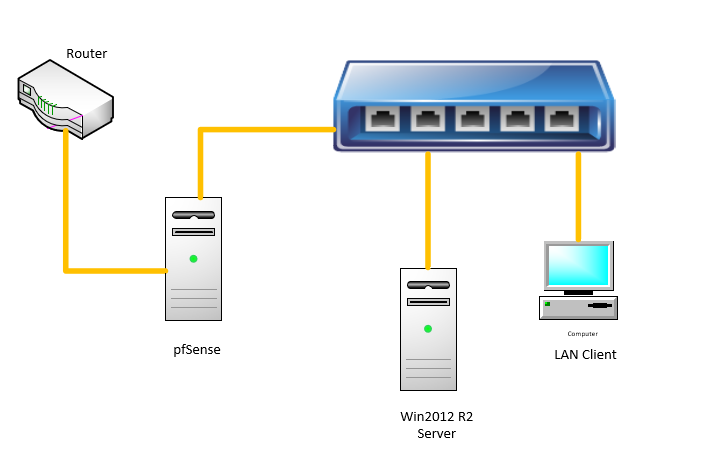
@uxm As you have drawn this, you need no extra VLANS. Two External v-switches (WAN, LAN) created in Hyper-V and assigned to 2 of your physical NICs. WAN, LAN interfaces on pfSense assigned to the corresponding v-switch. The WAN v-switch NIC wired to your router's LAN interface and the LAN v-switch NIC hooked to your switch. Run through the web setup on pfSense and BANG! Internet! Add an AP off your switch for your phones and laptop, use the Asus's wireless as a guest net.
-
Thank you very much! Im starting right away! Thanks @provels !