DNS crashing every ~ 36 hours or so and unbound has to be restarted.
-
@gawainxx said in DNS crashing every ~ 36 hours or so and unbound has to be restarted.:
@bmeeks
That's how I swore it worked on one of my previous pfsense instances.. I wonder why it's having issues that are requiring me to throw stuff in the unbound.conf.Without throwing that crap into the unbound config I was getting errors such as clients being unable to resolve _ldap._tcp.Default-First-Site-Name._sites.britannia2.local
Does my screenshot look correct?
No, you don't need to enter that host information. Simply put the AD domain name in the override and then optionally any reverse pointer records if you also want to be able to resolve IP addresses back to hosts.
Also remove that "_msdcs" entry. You do not need to let pfSense be where your AD clients try to find AD services! Let the AD domain controller handle all of that. You only would put AD overrides in pfSense if you wanted, as I did, certain logging information on pfSense to have resolved host names from your AD domain.
-
@johnpoz said in DNS crashing every ~ 36 hours or so and unbound has to be restarted.:
- if you forward to something in unbound - it will fall under rebind if rfc1918 is returned.
True, but in my case there is no forwarding to Unbound. The only thing in my network that uses Unbound is pfSense itself. I do have the "DNS Rebind Check" disabled on the SYSTEM > ADVANCED tab and forgot to mention that.
-
Without the stuff in unbound.conf present and just the domain override I get the following error on clients. If I plug in the IPv4 of the ADDS into the TCP/IP properties on the client it works though (however that's a shitty fix)
ote: This information is intended for a network administrator. If you are not your network's administrator, notify the administrator that you received this information, which has been recorded in the file C:\WINDOWS\debug\dcdiag.txt.
The following error occurred when DNS was queried for the service location (SRV) resource record used to locate an Active Directory Domain Controller (AD DC) for domain "britannia2.local":
The error was: "DNS name does not exist."
(error code 0x0000232B RCODE_NAME_ERROR)The query was for the SRV record for _ldap._tcp.dc._msdcs.britannia2.local
Common causes of this error include the following:
- The DNS SRV records required to locate a AD DC for the domain are not registered in DNS. These records are registered with a DNS server automatically when a AD DC is added to a domain. They are updated by the AD DC at set intervals. This computer is configured to use DNS servers with the following IP addresses:
192.168.50.1
- One or more of the following zones do not include delegation to its child zone:
britannia2.local
local
. (the root zone)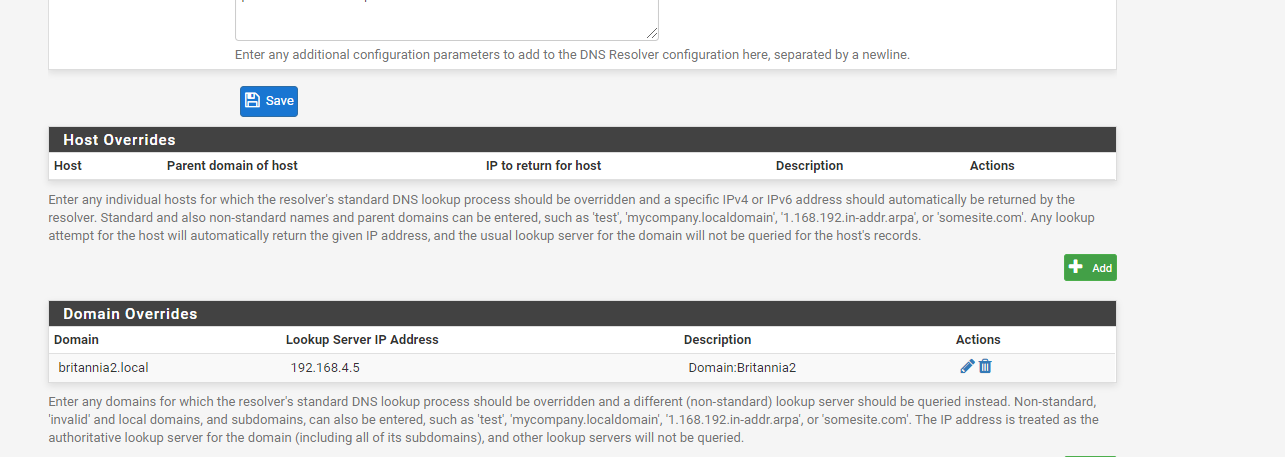
-
You are not understanding what I am saying. NO CLIENTS AT ALL should be asking pfSense for anything related to AD. The only reason the domain override should be there is for pfSense itself to resolve hostnames for logging purposes. Unbound does not understand how to serve up DNS service records for Active Directory. That's what AD DNS is for.
All of your AD clients MUST have the IP address of the AD domain controller for the DNS server. Anything else and it won't work -- as you are seeing.
Your clients in AD should all have their addresses (if not static) assigned by the AD DHCP server and that server should give them the AD domain controller for DNS resolutions.
Set your AD domain controller's DNS service to forward to Unbound if you want Unbound to resolve external (non-AD) hosts or domains.
-
@bmeeks said in DNS crashing every ~ 36 hours or so and unbound has to be restarted.:
I do have the "DNS Rebind Check" disabled on the SYSTEM > ADVANCED tab and forgot to mention that.
Why??? Just set the domain your forwarding with your override set as private..
-
@johnpoz said in DNS crashing every ~ 36 hours or so and unbound has to be restarted.:
@bmeeks said in DNS crashing every ~ 36 hours or so and unbound has to be restarted.:
I do have the "DNS Rebind Check" disabled on the SYSTEM > ADVANCED tab and forgot to mention that.
Why??? Just set the domain your forwarding with your override set as private..
No reason other than it was an old leftover setting that migrated with upgrades over the years. I actually had forgotten about it until I was looking after being reminded by your earlier replies.
It's been a long time, but I think that came along with the old DNS Forwarder many moons ago. I switched over to Resolver earlier this year just to stay more current. My old setting hid (or actually overrides) the need to set the particular domain as private. It would be better security practice for me to alter the setting and switch off the rebind override for all domains and instead just mark my AD domain as private.
-
What's best practice in this case were this a business network, would the scope of subnets with domain clients be configured something like below?
DNS Server #1 (PFsense Router)
DNS Server #2 (AD DC), obviously the DC would differ depending upon the site if there is more then one controller. -
@gawainxx said in DNS crashing every ~ 36 hours or so and unbound has to be restarted.:
What's best practice in this case were this a business network, would the scope of subnets with domain clients be configured something like below?
DNS Server #1 (PFsense Router)
DNS Server #2 (AD DC), obviously the DC would differ depending upon the site if there is more then one controller.No, you should never hand out any DNS server to Windows AD clients except the AD domain controller. Otherwise, they will randomly fail depending on whether they choose the pfSense Router or a real AD DNS server.
Nothing in my network gets the pfSense firewall as its "DNS server" (save the actual firewall itself) The firewall does not need to lookup AD stuff other than I like to be able to see my AD hostnames in logging entries and/or when looking at the ARP table. That's why I point pfSense to my AD DNS server. And I could just as easily tell pfSense to use my AD DNS servers for everything and never run Unbound on pfSense at all.
-
So in my particular case I should do one of the following?
Set the DHCP scope of network segments that have my test clients in them to hand out the domain controller's IP address for DNS.
OR for one-offs such as test servers I could modify their DHCP reservation to include the DNS address of the AD DC? -
@gawainxx said in DNS crashing every ~ 36 hours or so and unbound has to be restarted.:
So in my particular case I should do one of the following?
Set the DHCP scope of network segments that have my test clients in them to hand out the domain controller's IP address for DNS.
OR for one-offs such as test servers I could modify their DHCP reservation to include the DNS address of the AD DC?Yes, especially if those one-off servers would need to know about any AD-related things. Mostly likely if they are Windows servers then they will need to see an AD DNS server so they can locate the various domain services.
-
Thanks, makes sense.