Can someone help me configure Mullvad VPN for wifi interface?
-
This is driving me insane.
Guide: https://mullvad.net/en/help/using-pfsense-mullvad/ is worthless. It doesn't explain what it's trying to do..set up VPN for all interfaces, or just one. Whenever I get to setup about NAS, click Outbound, and Save, , internet access is shut down for ALL interfaces! I had to reinstall pfsense a dozen times now because of this.
Easy steps: Creating CA certificate, creating VPN client.
Cannot figure out: How to apply VPN to only SOME interfaces (wired or not wired)See image. I want to run VPN for ONLY ONE wifi, and ensure that f VPN connection breaks down, there is a kill switch for that interface only.
Does anyone know how to do this?
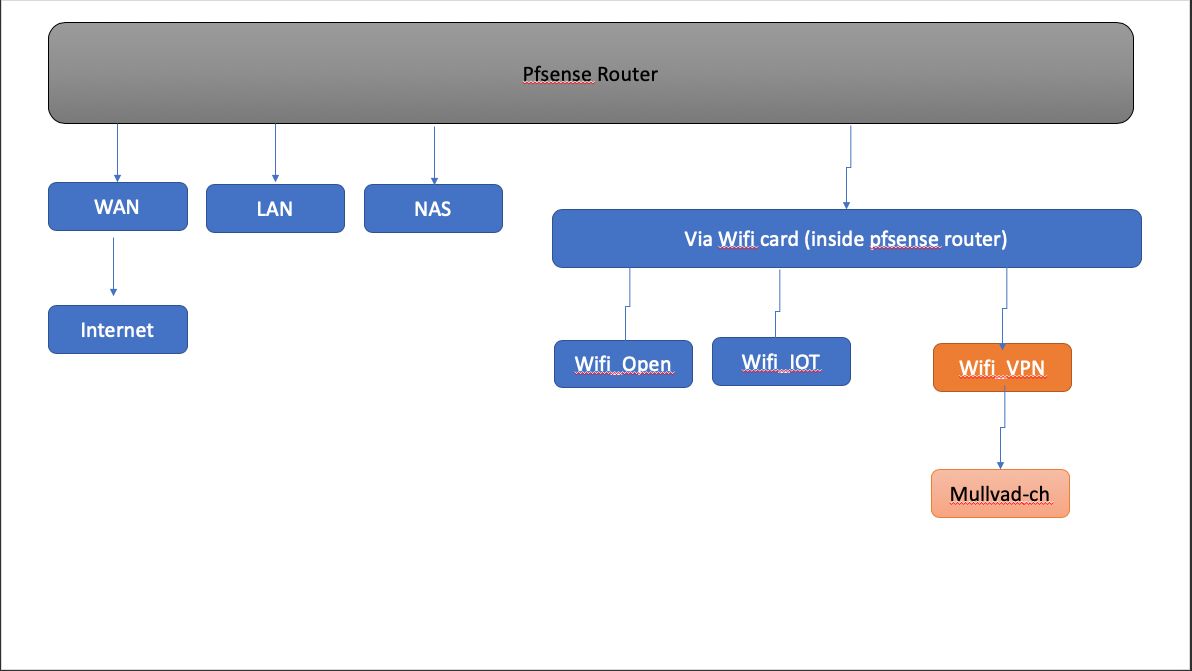
-
Have you created a gateway group?
Link : https://docs.netgate.com/pfsense/en/latest/routing/multi-wan.htmlAccording to that link, you will need to create a gateway group with Tier 1 -VPN gateway and Tier 2 WAN.
After that, you will need to set inside the advanced options of the firewall rule that permit internet access, to use as gateway the gateway group you created previously.Note that after setting this configuration, you will need to create a firewall rule for every access you do from the VLAN with the gateway group configured to the others vlan inside your network, these rules you leave the gateway as default.
Edit: Remember to add the VPN DNS servers in System / General Setup, each gateway needs to have a DNS.
-
This post is deleted! -
@mcury
Hi, I updated desired configuration, see pic.
I followed your steps for gateway groups, see pic.
I don't understand other instructions.
Under Edit: I cannot add mutlipl DNS for Mullvad client...and for the oen I do, I have to select a specific Mullvadd OpenVPN client, in picture the one for with letters CH (for region)here are Pics first then questions.
Updated desired end-state:
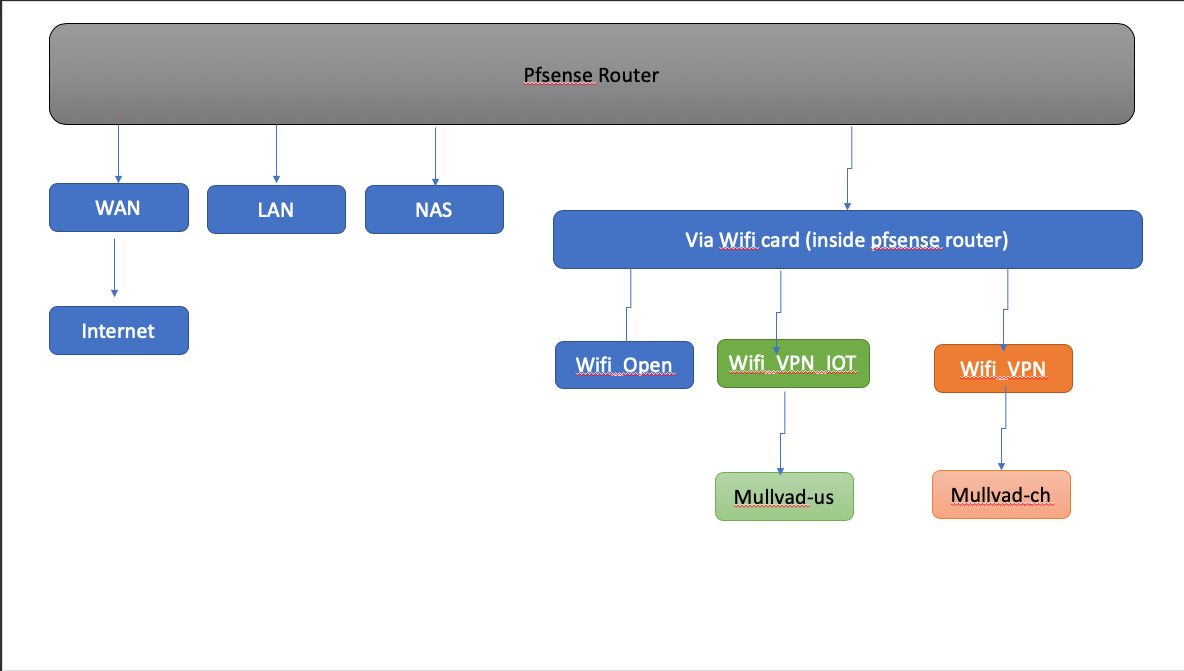
"According to that link, you will need to create a gateway group with Tier 1 -VPN gateway and Tier 2 WAN."
Created gateway groups (works):
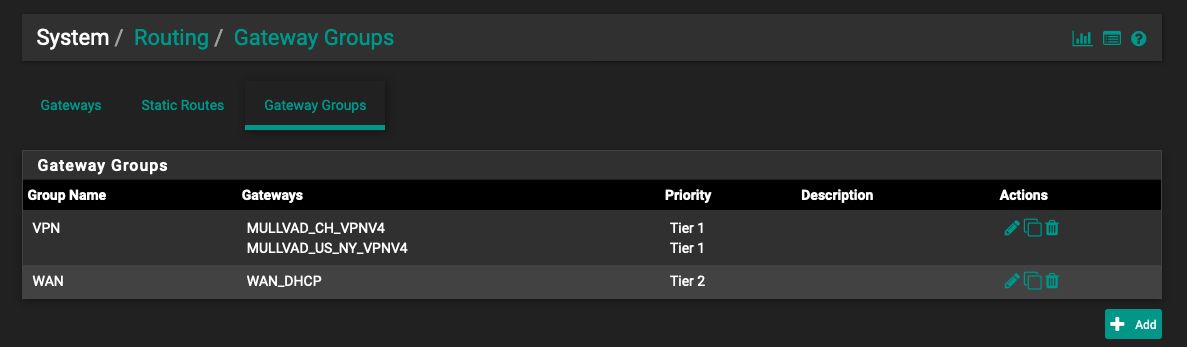
"After that, you will need to set inside the advanced options of the firewall rule that permit internet access, to use as gateway the gateway group you created previously."
Advanced options in firewall rule - I don't know which interface to select to do so. I know that when I select an interface, and scroll down, then click "Display Avdanced" I can see "Gateway"....but which interface do I select? WIFI_VPN or MULLVADD_US_NY?
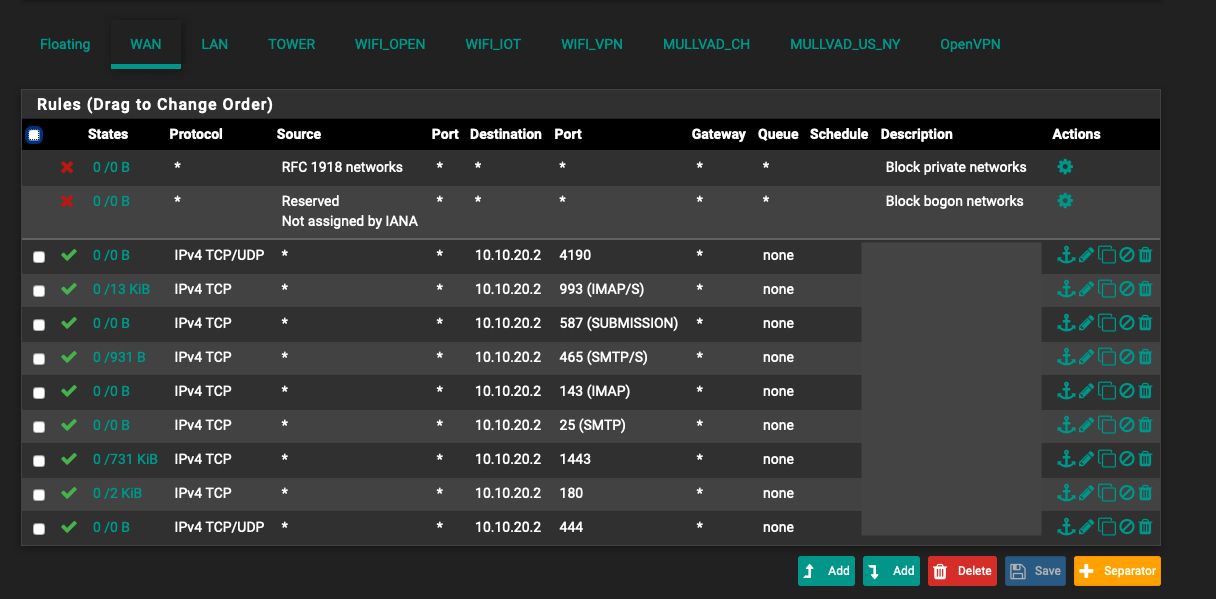
"Note that after setting this configuration, you will need to create a firewall rule for every access you do from the VLAN with the gateway group configured to the others vlan inside your network, these rules you leave the gateway as default."
I'm not sure how to do that. VLAN? I don't have VLANs set up.??
For which interface do I need to defined rules. And what are the rules I need t set up?
"Edit: Remember to add the VPN DNS servers in System / General Setup, each gateway needs to have a DNS."
I tried to do that, but I cannot add Gateway groups to DNS, and when I try to add DNS for each of the two VPNs I get error message:
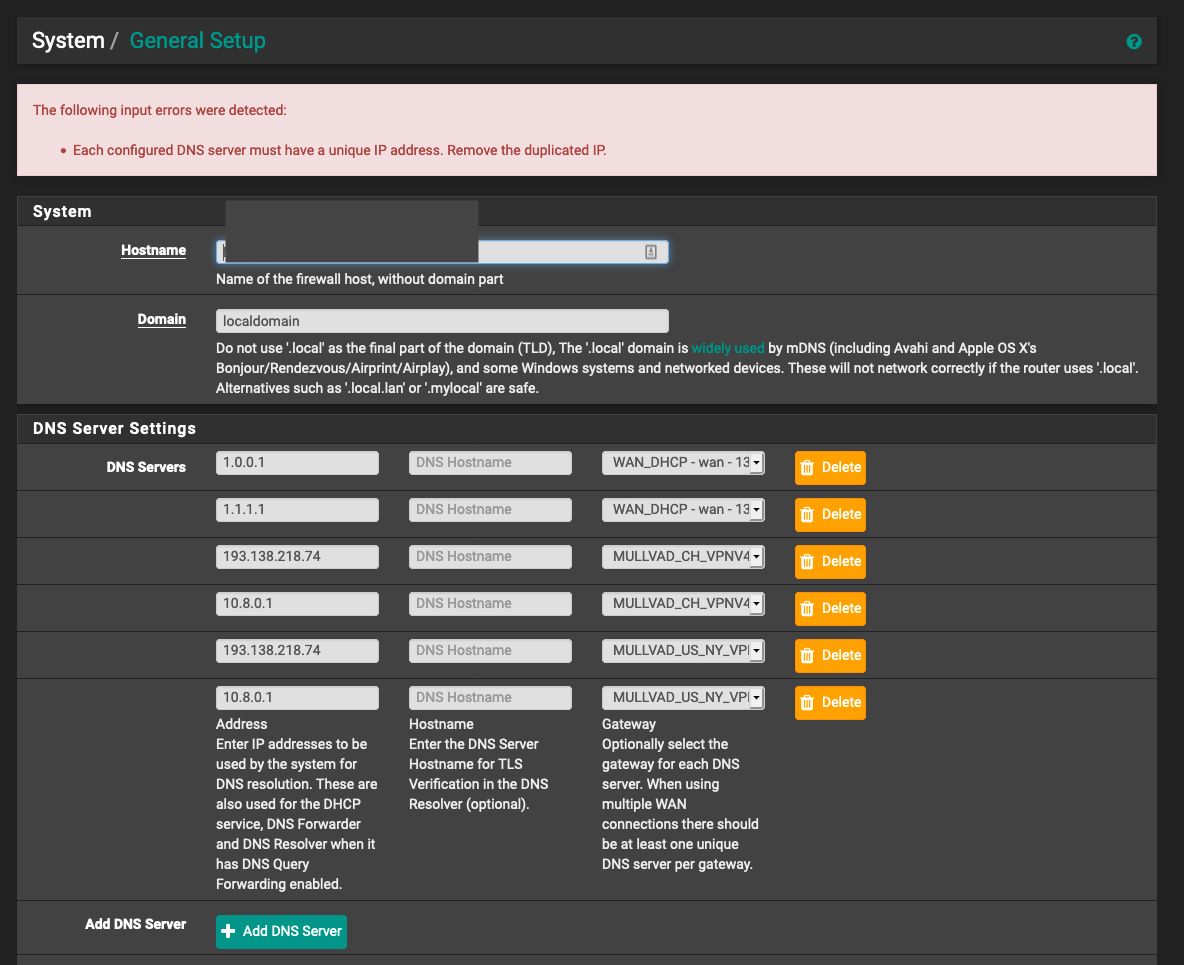
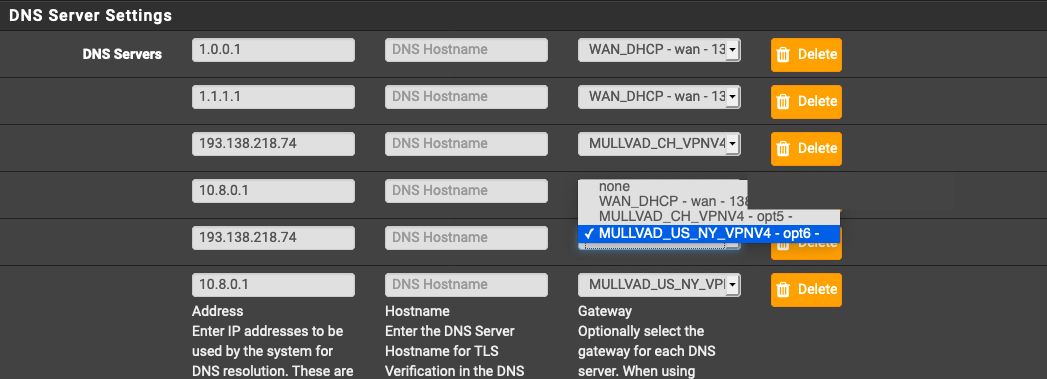
Any suggestions on next setps?
-
This post is deleted! -
In this case, where you have two tunnels from the same VPN provider, I guess it would be better to use one DNS server for each.
193.138.218.74 mullvad_ch
10.8.0.1 mullvad_usAlso, I've noticed that you have created 2 gateway groups, you should have created only one, what you did is even worse, because you would be load balancing between the VPNs and it would never fallback to WAN in case of a VPN outage.
What do you really need? Load balancing between China and US and in case of outage of both VPNs, fallback to WAN?
If that is the case, you create only one gateway group with the following:GW GROUP: VPN - TIER 1 - MULLVAD_CH
GW GROUP VPN - TIER 1 - MULLVAD_US
GW GROUP: VPN - TIER 2 - WANIn case you want to use CH as primary, US as secondary, and WAN in case both VPNs goes down:
GW GROUP: VPN - TIER 1 - MULLVAD_CH
GW GROUP VPN - TIER 2 - MULLVAD_US
GW GROUP: VPN - TIER 3 - WANQuestion:
Advanced options in firewall rule - I don't know which interface to select to do so. I know that when I select an interface, and scroll down, then click "Display Avdanced" I can see "Gateway"....but which interface do I select? WIFI_VPN or MULLVADD_US_NY?Answer: You need to edit the firewall rule where the SOURCE is coming from, in this case your WIFI VPN.
There, should be a rule to INTERNET access, edit that rule, go to advanced options, and set the gateway of that rule to GW GROUP VPN.Question:
'm not sure how to do that. VLAN? I don't have VLANs set up.??
For which interface do I need to defined rules. And what are the rules I need t set up?Answer: I supposed you were using VLANS, that is not case. Anyway, what I meant is that, in case you have connections from the WIFI VPN to the LAN for instance, and that connection is using your default rule to the Internet, it will use the GW GROUP and the connection won't reach the LAN side.
To resolve this, you will need to create a Firewall rule, above of the rule that contains the GW GROUP, that allows your WIFI VPN to reach LAN network, this rule will have the DEFAULT gatewayEdit: One more thing, in case you are using DNS resolver, enable DNS Query Forwarding.
Edit2 : Make sure the option "Do not pull routes" in Openvpn is selected. -
@mcury said in Can someone help me configure Mullvad VPN for wifi interface?:
Thanks for reply. So I'll go through your comments.
In this case, where you have two tunnels from the same VPN provider, I guess it would be better to use one DNS server for each.
193.138.218.74 mullvad_ch
10.8.0.1 mullvad_usI see your point. However, the two IPs must go together. the former is the actual IP from VPN provider, the latter is proxy. Both must be associated with the same VPN network. Also, 10.8.0.1 is local IP address, so it wouldn't resolve on internet.
However, I could enter these two DNS IPs under:
Services->DHCP server-Wifi_VPN and
Services->DHCP server-Wifi_IOTThat should work?
Also, I've noticed that you have created 2 gateway groups, you should have created only one, what you did is even worse, because you would be load balancing between the VPNs and it would never fallback to WAN in case of a VPN outage.
If VPN falls back, the connection should never default to WAN, that would amount to a "leak", which defies the purpose of VPN. VPN should be all or nothing (in my case).
What do you really need? Load balancing between China and US and in case of outage of both VPNs, fallback to WAN?
wifi-IOT - VPN, for IOT devices, tunneled through VPN - absolutely no "fallback WAN", either VPN is on and works, or NO internet.
wifi-VPN- VPN, for smart phones to connect to, via VPN, absolutely no "fallback WAN", either VPN is on and works, or NO internet.If that is the case, you create only one gateway group with the following:
GW GROUP: VPN - TIER 1 - MULLVAD_CH
GW GROUP VPN - TIER 1 - MULLVAD_US
GW GROUP: VPN - TIER 2 - WANFrom your initial reaction, it seems I actually do need to gateways. No?
In case you want to use CH as primary, US as secondary, and WAN in case both VPNs goes down:
GW GROUP: VPN - TIER 1 - MULLVAD_CH
GW GROUP VPN - TIER 2 - MULLVAD_US
GW GROUP: VPN - TIER 3 - WANIf VPN goes down, internet access should be shut down, kill switch, no exceptions.
Question:
Advanced options in firewall rule - I don't know which interface to select to do so. I know that when I select an interface, and scroll down, then click "Display Avdanced" I can see "Gateway"....but which interface do I select? WIFI_VPN or MULLVADD_US_NY?Answer: You need to edit the firewall rule where the SOURCE is coming from, in this case your WIFI VPN.
There, should be a rule to INTERNET access, edit that rule, go to advanced options, and set the gateway of that rule to GW GROUP VPN.Ok, make sense.
Question:
'm not sure how to do that. VLAN? I don't have VLANs set up.??
For which interface do I need to defined rules. And what are the rules I need t set up?Answer: I supposed you were using VLANS, that is not case. Anyway, what I meant is that, in case you have connections from the WIFI VPN to the LAN for instance, and that connection is using your default rule to the Internet, it will use the GW GROUP and the connection won't reach the LAN side.
Ok, see diagram. Wifi connections arent going through LANs. Meaning, I do not have a wifi router plugged into one of pfsense's LANs. Wifi connections are set through embedded wifi card in pfsense device, and as such do not go through any LAN ports at the back of router.
But I can see in wifi_VPN setting for gateway, so I can use that.
To resolve this, you will need to create a Firewall rule, above of the rule that contains the GW GROUP, that allows your WIFI VPN to reach LAN network, this rule will have the DEFAULT gateway
Ok, if that means, that connecition that is on VPN would default to WAN, if VPN is down, then this is not desired.
Edit: One more thing, in case you are using DNS resolver, enable DNS Query Forwarding.
K.
Edit2 : Make sure the option "Do not pull routes" in Openvpn is selected.
k
Will try out, things now and see if it works.
-
The 10.8.0.1 DNS server, will be accessed through VPN, it's in your VPN provider how to, so it should work through VPN, this IP will not be reached through Internet, but through VPN that probably has a DNS server with that IP.
The comments below will not work, your client won't know which DNS server to use, you will have timeouts and problems.
Leave the DHCP DNS settings at their default, clients will be using DNS resolver, which's responsible to route your DNS requests to the correct DNS server.Comments:
However, I could enter these two DNS IPs under:
Services->DHCP server-Wifi_VPN and
Services->DHCP server-Wifi_IOTKill switch:
In order to get your kill switch as you said, the correct method is to TAG the packets coming from the WIFI VPN SUBNET, let's say, NO_WAN_EGRESS for instance.
Then, create a WAN rule that matches that tag, and block it.Regarding the comments below: The default gateway of those WIFI vlans is your pfsense Firewall, right? So, just do as I said previously.
Comments:
Ok, see diagram. Wifi connections arent going through LANs. Meaning, I do not have a wifi router plugged into one of pfsense's LANs. Wifi connections are set through embedded wifi card in pfsense device, and as such do not go through any LAN ports at the back of router.Comments:
Ok, if that means, that connecition that is on VPN would default to WAN, if VPN is down, then this is not desired.
Answer: You didn't understand, this has nothing to do with INTERNET access, it's just to allow your WIFI networks to communicate with the other WIFI networks, LAN or NAS networks.
-
I did exactly what you wrote.
It didn't work. -
@demo3 What exactly didn't work?
-
@mcury said in Can someone help me configure Mullvad VPN for wifi interface?:
@demo3 What exactly didn't work?
Well, logging onto a wifis with mobile device, and opening up gogle.com didn't work.
-
Was the DNS that didn't work?
Can you ping 8.8.8.8?Do you have a 10.8.0.0/24 network or a 10.0.0.0/16 network there? Note that one of the DNS servers is 10.8.0.1.
In this situation your pfsense wouldn't be able to route to that specific DNS server. -
@mcury
Yes, I can.
I don't use 10.8.x.x. -
So you can ping 8.8.8.8 but can't access google.com.
What DNS server the device you are testing is getting from the DHCP? Is it using the pfsense dns resolver?Did you set the DNS servers at the general setup tab for the VPN interface as I suggested?
What about the firewall rule to allow the device you are testing to communicate with the pfsense Firewall on port 53 UDP/TCP. Does that rule exist and if does, is it above your rule that has the GW GROUP VPN set?
-
@mcury
You meant ping through that wifi? Yes, I tried. It didn't work.
I am the only one with a pfsense router with wifi, in 5mile radius. I set 10.8.0.1 as you suggested.
Yes.
Yes, the rule exists, top floating level. -
Did you create the NAT rule?
What about the Firewall logs, what rule is that ping to 8.8.8.8 hitting?
Also: What DNS server the device you are testing is getting from the DHCP? Is it using the pfsense dns resolver?
One more question before I go to sleep, is the VPN up? lol -
Hi,I asked this morning my network guy to look at your comments. He stopped reading after your suggestions to default connection to WAN if VPN was down and suggested I google "Selective routing" instead. Thanks for trying though.
-
Great, if it's working, good.
-
i would use the following guide to force the correct DNS servers: https://www.techhelpguides.com/2017/06/12/ultimate-pfsense-openvpn-guide/
you also need to follow step 7 for each tunnel so the data flows properly.
just do you know depending on the tunnel you use. the 10.8.0.1 DNS will not resolve. depending on how you are connecting to mullvad the address may be 10.8.0.1 or possibly 10.7.0.1 ETC. i would suggest using their external resolver 193.138.218.74 and delete the nonsense on general DNS tab.
and its always a foolproof method to use aliases for the devices you want to go over the vpn
-
@bcruze
Hi, thanks for advice. Very useful. I set up VPN, actually I have 2VPNs for wifi, and one for landline. Yes for general DNS tab, deleted everything but cloudFlare DNS records. VPN-specific DNS servers were configured on Services->DHCP server->xyz interface (assuming Services-.DNS resolver-general settings: "DNS Query Forwarding" is checked. Killswitch was set up on NAT by deleting appropriate WAN-related records - interestingly nobody mentions that NAT entries for outbound port 500 are irrelevant and can be deleted, if one is not using anything but OpenVPN. Works perfectly well. The best simple video user guide was this: https://www.youtube.com/watch?v=8jYibgeAV0Y.