Can someone help me configure Mullvad VPN for wifi interface?
-
The 10.8.0.1 DNS server, will be accessed through VPN, it's in your VPN provider how to, so it should work through VPN, this IP will not be reached through Internet, but through VPN that probably has a DNS server with that IP.
The comments below will not work, your client won't know which DNS server to use, you will have timeouts and problems.
Leave the DHCP DNS settings at their default, clients will be using DNS resolver, which's responsible to route your DNS requests to the correct DNS server.Comments:
However, I could enter these two DNS IPs under:
Services->DHCP server-Wifi_VPN and
Services->DHCP server-Wifi_IOTKill switch:
In order to get your kill switch as you said, the correct method is to TAG the packets coming from the WIFI VPN SUBNET, let's say, NO_WAN_EGRESS for instance.
Then, create a WAN rule that matches that tag, and block it.Regarding the comments below: The default gateway of those WIFI vlans is your pfsense Firewall, right? So, just do as I said previously.
Comments:
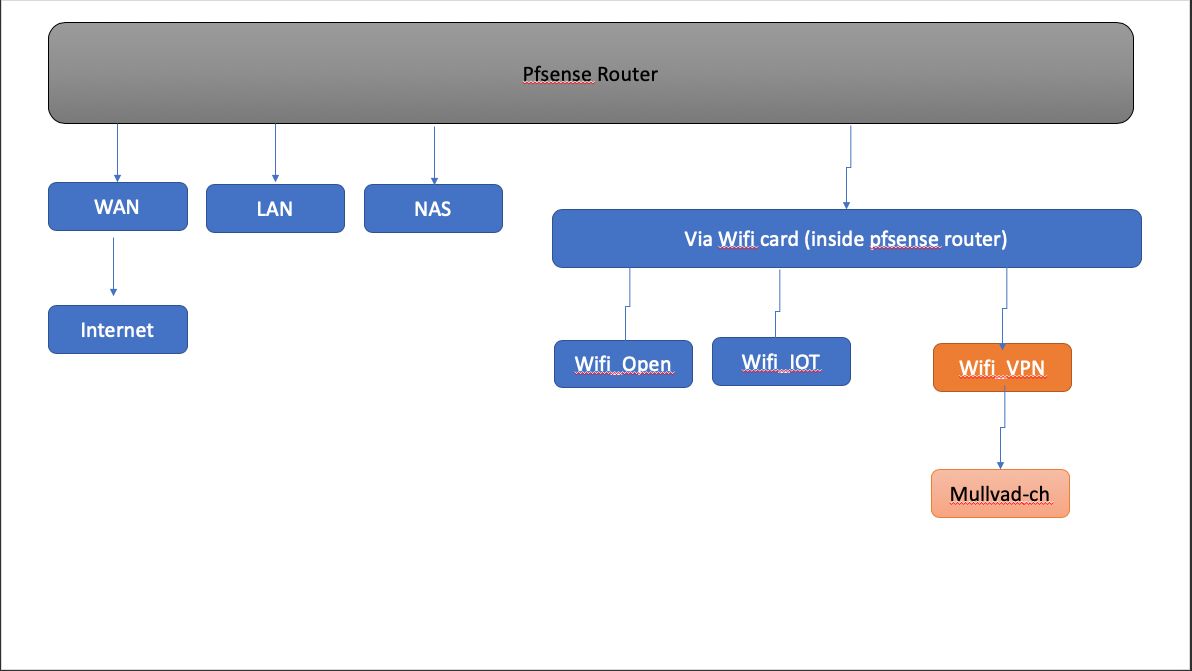
Ok, see diagram. Wifi connections arent going through LANs. Meaning, I do not have a wifi router plugged into one of pfsense's LANs. Wifi connections are set through embedded wifi card in pfsense device, and as such do not go through any LAN ports at the back of router.Comments:
Ok, if that means, that connecition that is on VPN would default to WAN, if VPN is down, then this is not desired.
Answer: You didn't understand, this has nothing to do with INTERNET access, it's just to allow your WIFI networks to communicate with the other WIFI networks, LAN or NAS networks.
-
I did exactly what you wrote.
It didn't work. -
@demo3 What exactly didn't work?
-
@mcury said in Can someone help me configure Mullvad VPN for wifi interface?:
@demo3 What exactly didn't work?
Well, logging onto a wifis with mobile device, and opening up gogle.com didn't work.
-
Was the DNS that didn't work?
Can you ping 8.8.8.8?Do you have a 10.8.0.0/24 network or a 10.0.0.0/16 network there? Note that one of the DNS servers is 10.8.0.1.
In this situation your pfsense wouldn't be able to route to that specific DNS server. -
@mcury
Yes, I can.
I don't use 10.8.x.x. -
So you can ping 8.8.8.8 but can't access google.com.
What DNS server the device you are testing is getting from the DHCP? Is it using the pfsense dns resolver?Did you set the DNS servers at the general setup tab for the VPN interface as I suggested?
What about the firewall rule to allow the device you are testing to communicate with the pfsense Firewall on port 53 UDP/TCP. Does that rule exist and if does, is it above your rule that has the GW GROUP VPN set?
-
@mcury
You meant ping through that wifi? Yes, I tried. It didn't work.
I am the only one with a pfsense router with wifi, in 5mile radius. I set 10.8.0.1 as you suggested.
Yes.
Yes, the rule exists, top floating level. -
Did you create the NAT rule?
What about the Firewall logs, what rule is that ping to 8.8.8.8 hitting?
Also: What DNS server the device you are testing is getting from the DHCP? Is it using the pfsense dns resolver?
One more question before I go to sleep, is the VPN up? lol -
Hi,I asked this morning my network guy to look at your comments. He stopped reading after your suggestions to default connection to WAN if VPN was down and suggested I google "Selective routing" instead. Thanks for trying though.
-
Great, if it's working, good.
-
i would use the following guide to force the correct DNS servers: https://www.techhelpguides.com/2017/06/12/ultimate-pfsense-openvpn-guide/
you also need to follow step 7 for each tunnel so the data flows properly.
just do you know depending on the tunnel you use. the 10.8.0.1 DNS will not resolve. depending on how you are connecting to mullvad the address may be 10.8.0.1 or possibly 10.7.0.1 ETC. i would suggest using their external resolver 193.138.218.74 and delete the nonsense on general DNS tab.
and its always a foolproof method to use aliases for the devices you want to go over the vpn
-
@bcruze
Hi, thanks for advice. Very useful. I set up VPN, actually I have 2VPNs for wifi, and one for landline. Yes for general DNS tab, deleted everything but cloudFlare DNS records. VPN-specific DNS servers were configured on Services->DHCP server->xyz interface (assuming Services-.DNS resolver-general settings: "DNS Query Forwarding" is checked. Killswitch was set up on NAT by deleting appropriate WAN-related records - interestingly nobody mentions that NAT entries for outbound port 500 are irrelevant and can be deleted, if one is not using anything but OpenVPN. Works perfectly well. The best simple video user guide was this: https://www.youtube.com/watch?v=8jYibgeAV0Y.