SMB - Windows share over vlans
-
Hello,
I have having a tough time trying to access a Windows share over vlans.
I have an Admin Vlan and I have a windows laptop connected to that vlan with an static IP of 10.0.0.51/24. I have another vlan called user_net which are wifi devices, mostly cellular phones. My android phone is connected with static IP of 10.0.3.26/24.
Both vlans have access to everything for the moment (testing purposes)On the Windows machine, I have configured a share called Test. It requires no password. If I connect the windows machine via wifi to the user_net vlan, with static IP of 10.0.3.27/24, I can access the share on my android phone with Solid File Explorer. No problem whatsoever.
However, when I switch my laptop back to the admin vlan, using the static IP 10.0.0.51/24, I am not longer able to access the share.
I am able to ping back and forth between vlans to both devices and am able to do a successful traceroute. The Windows machine has the firewall disabled and I have disabled any virus scanning programs. I also do not see anything in the pfsense firewall logs.
Any help would be appreciated.
-
When you say your no longer able to access it, do you mean it no longer appears? Or you can't access it via IP address or host name. SMB broadcasts the shares over the network, but those broadcasts are not passed by a router. However, if you know it's address, you should still be able to connect to it.
-
When I am connected to the 10.0.3.0/24 with my Android phone, I cannot see/not access the share on the Windows machine (10.0.0.51)
I am attempting to connect to it both by IP and hostname. Both hostname and IP work fine if Windows and Android are on the same network.
-
Do you allow smb on the firewall rule? Do the windows server firewall allow that vlan network?
-
Within pfsense, both vlans have no firewall rules other than access to any any on IPv4..
The Windows firewall is disabled. As well as all Antivirus.
-
Can you ping the IP?
What does the error you get exactly? Failed to auth, couldn't find host... Your not routing traffic out a vpn on your pfsense are you?
-
No VPN is involved here.
I am able to ping back and forth and do successful trace route. I don't get an errors at all, it just times out. No authentication is needed, this share is open to Everyone.
When both devices are on the same network, I simply put in the IP and it goes straight through and I can access the test folder.
If devices are on different networks, I put in the IP, and it just tries and tries, but never gets a connection.
-
@solaris81 Does that SMB server have two NICs?
It's possible that you don't have a return route to the correct NIC, packet could be going through your default route. -
Yeah does the server point to pfsense as it gateway?
I would suggest is sniff on pfsense on the interface on the server network -- do you see the smb traffic going to the server?
-
@mcury said in SMB - Windows share over vlans:
@solaris81 Does that SMB server have two NICs?
It's possible that you don't have a return route to the correct NIC, packet could be going through your default route.Only one NIC involved
-
@solaris81 So return traffic shouldn't be a problem, unless you SMB server doesn't have a default gateway configured.
It's better to sniff as john suggested. -
@mcury said in SMB - Windows share over vlans:
@solaris81 Does that SMB server have two NICs?
It's possible that you don't have a return route to the correct NIC, packet could be going through your default route.The server points to its own gateway, the 10.0.0.1 address. Diff from LAN
-
@solaris81 So probably nothing related to return traffic.
Check if the packets from the other network are hitting the server, you should sniff as john suggested.
You could do it using tcpdump, wireshark, also pfsense packet capture to confirm if it's delivering the packets to the server. -
So here are 2 different examples...
First is me hitting a box where smb not running the 2.11 and it telling me to F off with RST..
Second is me accessing my nas via vpn connection and you can see the smb connecting..So lets see what you get when you try and connect.
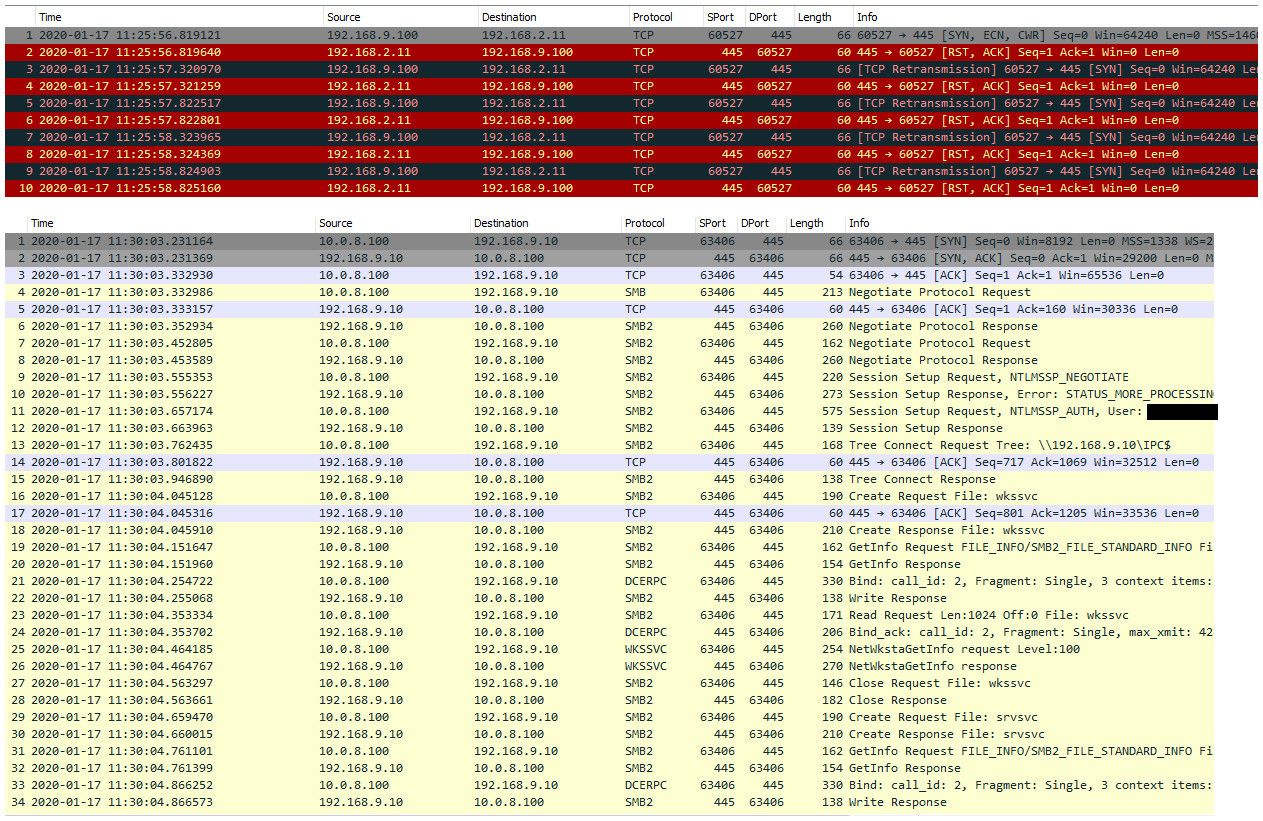
-
I am using packet capture in pfsense and then opening it with wireshark. Is there a good way to filter within packet capture so I can get rid of all the other traffic?
-
In order to get real time capture, you could use tcpdump directly in pfsense cli.
tcpdump -i INTERFACE tcp and port 445 and host HOST_IPWhere, interface is the interface name you want to sniff, ifconfig lists all the interfaces.
HOST_IP would be the client IP, if you filter by the server IP, you would get a lot of stuff too.The filter "tcp and port 445 and host HOST_IP" could be modified as you wish, you can use OR instead of AND too.
Second method is to wireshark directly to the pfsense, but that would require ssh keys.
In case you want this method, just let me know and I will paste here a procedure for you. -
@mcury said in SMB - Windows share over vlans:
tcpdump -i INTERFACE tcp and port 445 and host HOST_IP
I did a capture capture from the 10.0.0.0/24 network where the Win system resides. Here are my findings. First attempted to connect to the Windows machine and then did a ping to show I am able to reach it.
Followed with another attempt to connect to the share.
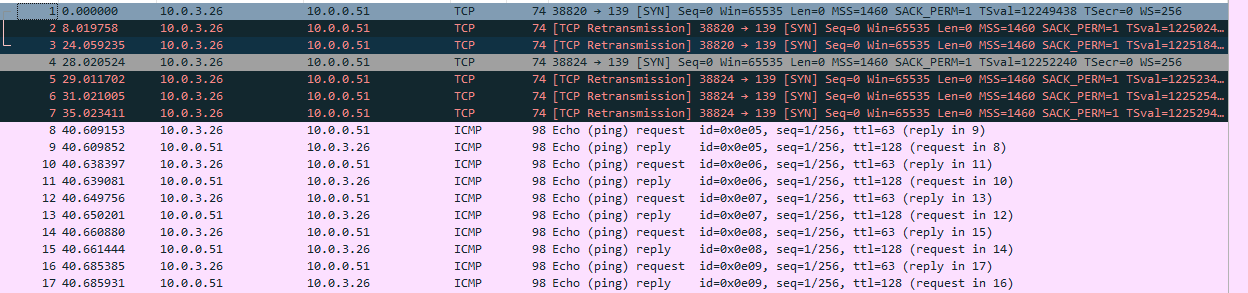
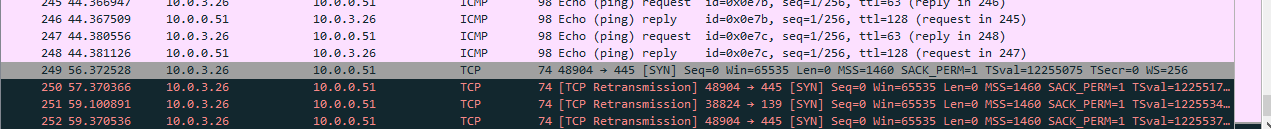
-
Good, as we can see, your server never replied the SYN request from the client.
Can you set the capture now in the interface that has the IP 10.0.0.1 ?
Let's confirm if your pfsense is sending this SYN to the server. -
The capture was from the em1_vlan10 interface where the 10.0.0.1 exists. Are you talking about running a capture on the 10.0.0.51 interface/ Windows machine?
-
Yes, run in the server, or in pfsense interface connected to the server.
I presume those 10 networks are /27, /28 /29 right?A /26 or less would give you routing issues due to network overlap.