Using Open VPN service on XG-7100, prevent LAN clients connecting
-
I have a funny issue. If I attempt to connect to the VPN endpoint on the firewall, from inside the LAN, I am not rejected. Is this normal for Open VPN, what did I miss? I thought about a firewall rule, but the Open VPN interface is not an option for source or destination.
-
Please rephrase your question. It doesn't make any sense.
If you have an OpenVPN server listening on the WAN it is not designed to be connected to from the inside. It is designed to be connected to from the outside.
-
@Derelict You're right it doesn't make any sense. I've never worked with a VPN endpoint that allows internal connections.
I am using the Open VPN service on the XG-7100, VPN/Open VPN menu. The firewall is hosting the VPN server via the built in service. And yes, it allows connections from inside. Don't ask me how, because that's what I'm asking you.

-
Why connect from the inside? Why not just route the traffic?
You can do it but if you are looking to be connecting from the inside, the network you are connecting from can't be one of the networks you expect to access over the VPN.
You will see the same problems connecting from a remote site that uses the same IP numbering scheme as the protected network.
So give more details:
Subnet and IP address you are connecting from
Subnet you expect to be routing over the VPN (The Local Networks in the server)
The host IP address you are having trouble accessing.It is completely normal to be able to connect to services running on the WAN address from the inside. If you do not want that to happen you need to block connections to This firewall (self) on that interface. (Be sure the web gui is passed before that if you do or you will lock yourself out)
-
@Derelict To be clear, I'm trying to disable connecting from the inside. We discovered this quite by accident.
-
My expectation when using a VPN endpoint on the firewall is that this endpoint will only accept traffic inbound from the WAN interface. How do I manually restrict the traffic that the Open VPN service will accept?
-
Your expectation is erroneous.
Block the traffic on the interface(s) that are receiving the traffic you want blocked, such as the LAN interface.
A "guest" interface would look something like this:
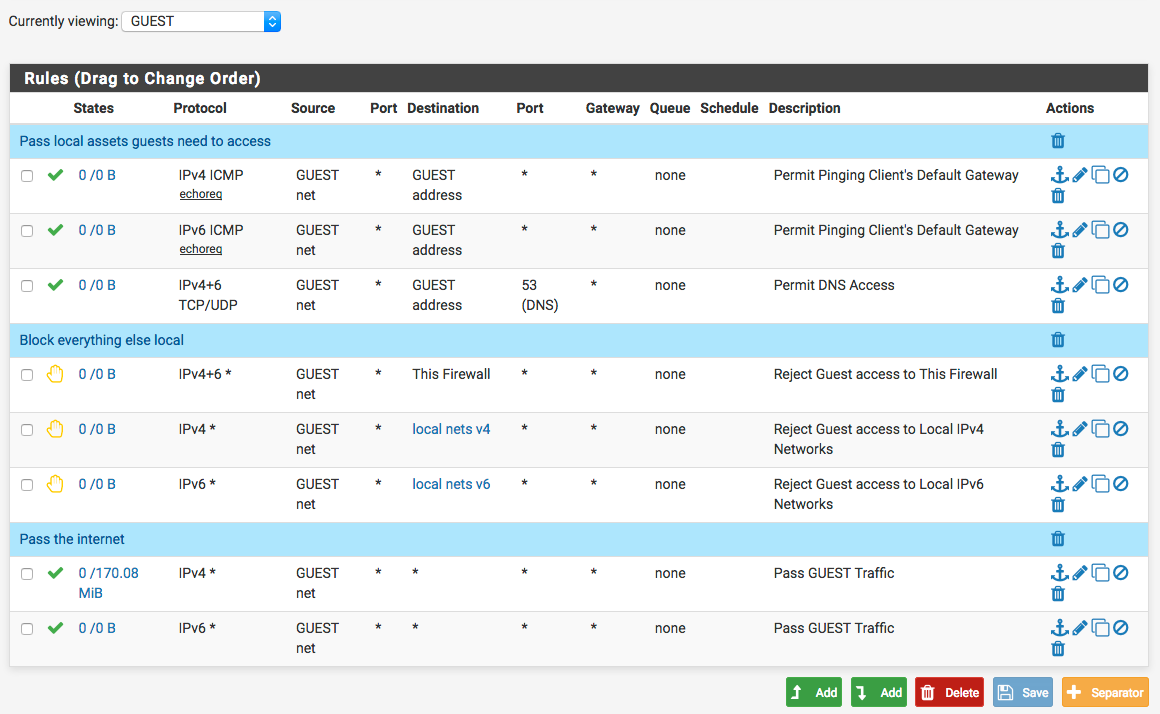
-
@Derelict I'm not sure I've done a good job of expressing my concern. Can you repeat back to me what you understand my issue to be? I want to make sure that we are harmonized, because it seems like this should be very simple to solve.
-
Okay, so here's my beef: a VPN is designed to securely encapsulate private traffic to traverse a public network. Public and private are on opposite sides of the WAN interface. Since the Open VPN service accepts inbound connections from private interfaces, it is not working correctly.
Why does the PFSense implementation of Open VPN go against sane networking theory?
How do I stop the Open VPN from being naughty? Are you really saying I have to implement a ton of firewall rules to make the endpoint behave properly?
-
It is simple to solve. If you don't want users on an interface to connect to a service running on the firewall, make a block rule there.
-
@Derelict The endpoint should be accepting connections from private subnets by default. Why is it doing that?
-
Because that WAN address is just another IP address. You need to block traffic from the inside to it if that's what your requirements are.
-
@Derelict well, I'm not trying to block access to the WAN. I'm trying to prevent private subnets from connecting to the Open VPN service.
-
That is WAN address. That is not the internet. See the rule set I already posted.
Connections to the OpenVPN server would be blocked by the Reject Guest access to This Firewall rule.
-
If you have an OpenVPN server listening on the WAN it is not designed to be connected to from the inside. It is designed to be connected to from the outside.
Actually, that's normal. You can reach any address on the box from any interface, unless you have rules to block it. Don't forget, pfSense is a router, so if it, for example receives a packet with the WAN interface as destination, on the LAN interface, it will forward it appropriately through 0.0.0.0.
-
I know it's completely normal. It's @shapelytraffic that is having trouble grasping that concept.
-
@Derelict I saw your rules, what are you representing with "guest" network?
If I block LAN access to the WAN then I assume this will have global impact.
-
@shapelytraffic said in Using Open VPN service on XG-7100, prevent LAN clients connecting:
@Derelict To be clear, I'm trying to disable connecting from the inside. We discovered this quite by accident.
That behaviour is normal. If you don't want it, create a rule on the LAN interface to block it.
-
No. It won't have global impact. Global addresses are not covered in any of those block rules. Traffic that is not specifically blocked will be passed to the internet by the bottom rules passing traffic to destination any. Guest Network in that example is the IP network of the GUEST interface.
-
@JKnott my issue is that any other router on the market which provides a VPN endpoint and client install will only accept client traffic from the public side of the WAN. You cannot go in through the outdoor, as it were. So, if this is "a feature" then I ask, why is it that the feature goes against networking standards? But also, do I really need to implement a ton of firewall rules to make the endpoint behave?