I made a WireGuard package for pfSense
-
@alirz I've had some issues with DNS occasionally not working after a reboot. Try restarting the DNS service; I believe that's what I've had to do the last few times.
-
@Ascrod OK that fixed it..thats strange though. Ive done several reboots and it didnt do anything. So is there some sort of race condition going on here that the DNS service on pfsense needs to restarted once more after a reboot? Sucks as this kind of makes it a bit unreliable!!
i am also running openvpn server on the pfsense...Does that show affect this?
Any fix for this DNS issue? perhaps add a startup script to restart DNS shortly after a reboot is done? -
ok so i used the "shellcmd" package that can launch commands during/after boot.
I added the following command in there to run after reboot.sleep 30 && pfSsh.php playback svc restart unboundHad to put a sleep because restarting dns right after reboot doesnt fix the issue.
Wish this get resolved eventually when this whole thing makes it into PFsense officially. I dont like these patchy fixes that i lived with for years when i was suing dd-wrt/openwrt years ago. -
Do we know of the dns issue is related to the unbind DNS server or to the wireguard models? If later, is there a newer build of wireguard available?
-
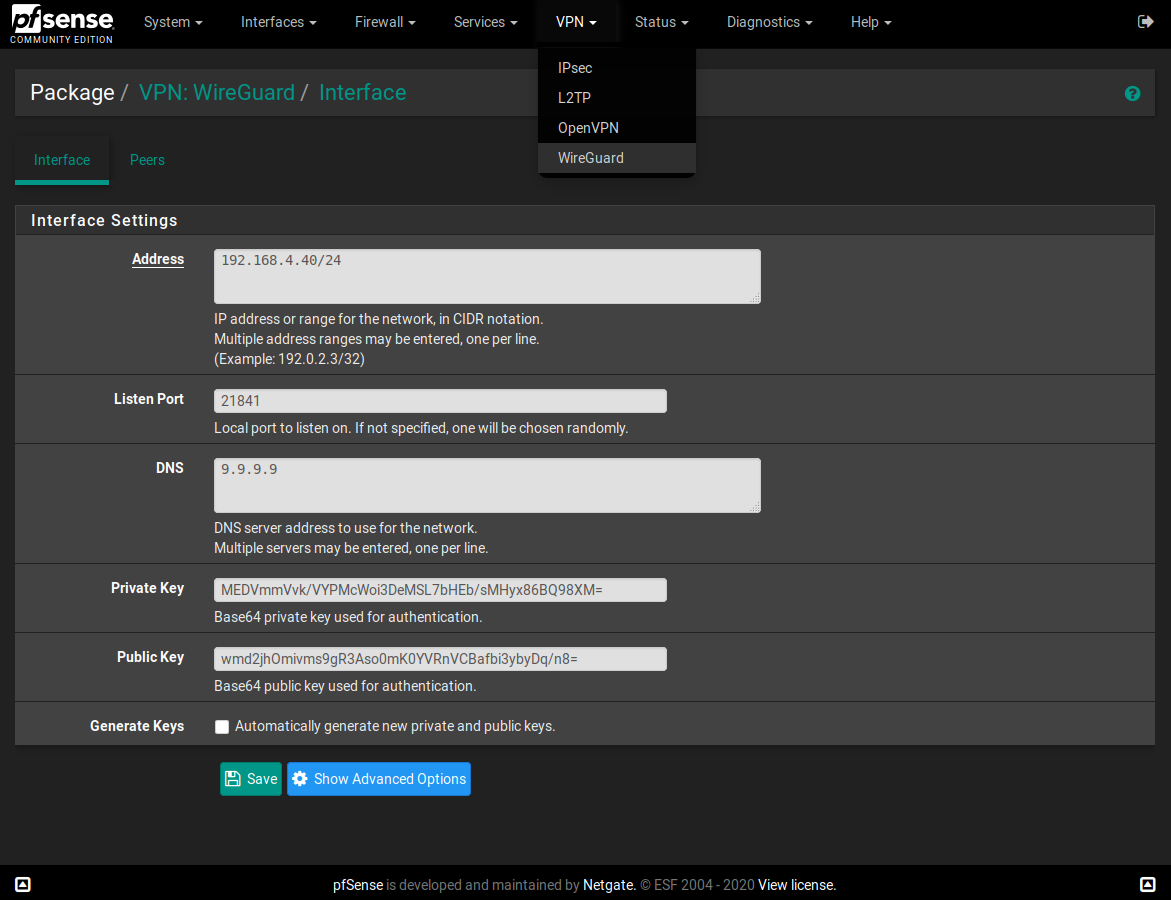
Thanks for your work on this @Ascrod !! I've just set it up and working nicely. I also had the DNS issue after reboot. I suspect it is because the wireguard interface IP address is not set when the DNS resolver is started. pfSense's Unbound defaults to only responding to internal subnets. See this setting;

I suspect adding the wiregaurd subnet on the Access list tab of the DNS resolver will work as a acceptable workaround (haven't tried this yet). -
@Ascrod echoing what @S762 said, suggest you add "pkg install bash" and reorder the above (wireguard-go needs to go before the wireguard package). Otherwise, these steps worked well for me to set up.
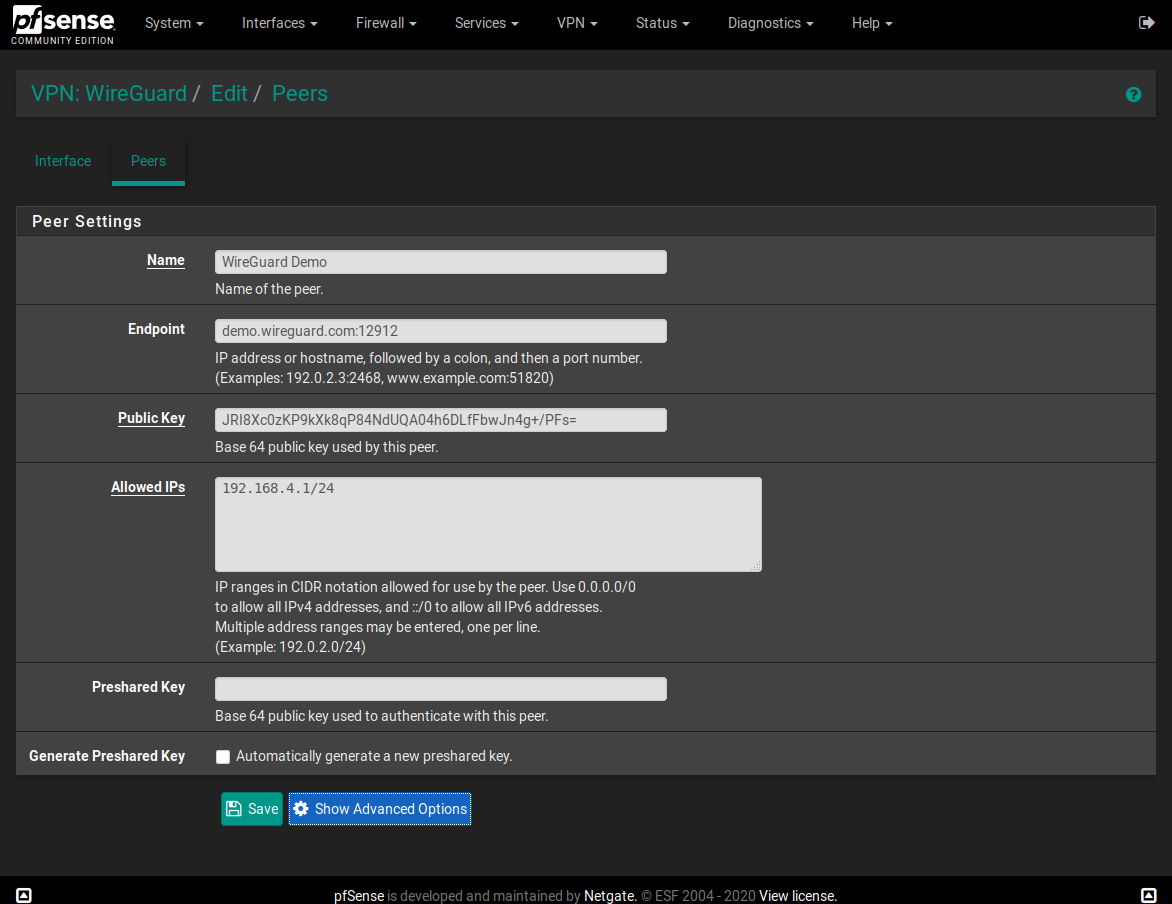
I wonder if we could auto-detect an unused (RFC1918) subnet, select a random port and generate server keys on first install. This would make the initial set up much easier :) -
@lucas_nz said in I made a WireGuard package for pfSense:
Thanks for your work on this @Ascrod !! I've just set it up and working nicely. I also had the DNS issue after reboot. I suspect it is because the wireguard interface IP address is not set when the DNS resolver is started. pfSense's Unbound defaults to only responding to internal subnets. See this setting;

I suspect adding the wiregaurd subnet on the Access list tab of the DNS resolver will work as a acceptable workaround (haven't tried this yet).Hi,
I tired your suggestion of adding the wireguard subnet in the dnsresolver access list. RebootEd, but still had no dns until I restarted the service.
I also thought and tried of assigning a static Ip to the wireguard interface under the interface assignment page to see if that made any difference. Nope. -
thanks @alirz. Good to know. Hmm - I wonder what the issue is then??
-
@alirz - hmm so, in the resolver config, I tried ticking the disable auto-added access control tick box and adding all RFC1918 (private) IP address ranges to the access tab then rebooted. This seemed to "fix" the DNS resolution issue. But My VPN firewall rule stopped working (it literally set to allow all IPv4). Editing the rule, and reapplying seemed to fix things. I wonder if this is still the same issue as the DNS issue, just another way of it occurring?
Following the rabbit down the hole (suspecting something funny happening with the interface), I tried adding a floating rule with my wiregaurd subnet as the source and anything as the destination. Rebooted (with the above DNS hack in place), and I have a working solution (sort of)... But it doesn't seem to source NAT my traffic out my WAN interface
 . I don't know if that helps us debug the issue or not, but I'm hopeful it points us in the right direction
. I don't know if that helps us debug the issue or not, but I'm hopeful it points us in the right direction 
-
@lucas_nz how do know that it doesn’t source not your traffic?
For me I’m only using a startup script to restart my dns after a 30 second delay after rebooting. That seems to fix the issue for me with no other hacks in place. -
@alirz, I could access LAN based resources but nothing on the internet and I see lots of TCP:S in the firewall log. I guess that isn't 100% confirmation that it's not NATing it, but it is a logical explanation given the lack of response from non-local IP ranges.
I just retested, I had both the floating rule and the VPN on in place, as soon as I disabled the floating one, everything sprung to life. In fact, as soon as I seem to commit any change, everything seems to come to life. -
See the diff below for /usr/local/etc/rc.d/wireguard.sh (added below the wg-quick up command). This has resolved my issues no need to restart unbound. I also added my VPN subnet to the DNS resolver (allowed) access list.
diff ./wireguard.sh /usr/local/etc/rc.d/wireguard.sh wireguard.sh 6a7 > /etc/rc.filter_configureLuke
-
@lucas_nz Cool, thank you for the update, but for me personally that would be one more change to track manually across upgrades and config-re saves that might overwrite that setting. I prefer to keep everything manageable from within the pfsense gui so that backups and restores take my changes into account.
I'll stick to my DNS restart at boot for now till this makes it way officially in pfsense with all the fixes etc.. -
@Ascrod said in I made a WireGuard package for pfSense:
If you're using pfSense 2.4.5 like I am, you can use these commands on the command line interface, or the Command Prompt page on the web interface:
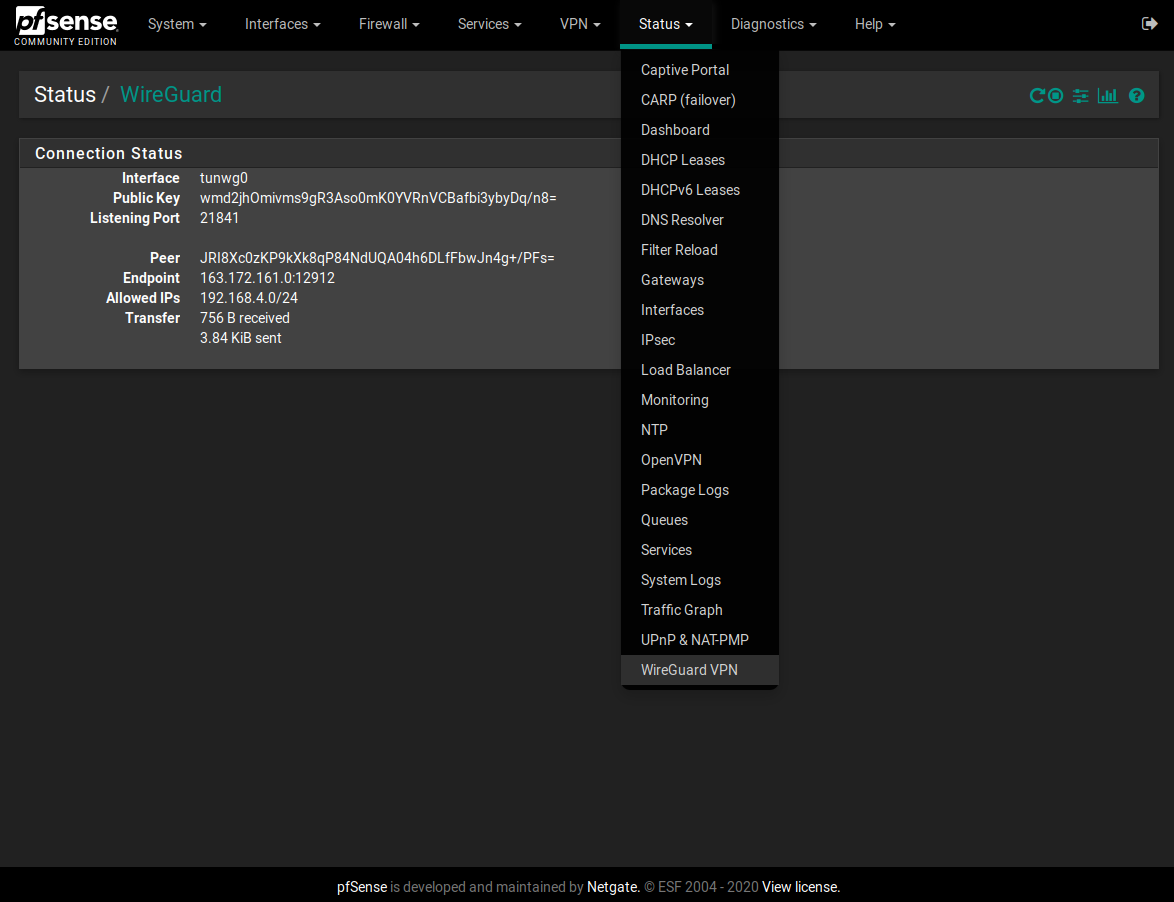
pkg add http://pkg.freebsd.org/FreeBSD:11:amd64/latest/All/wireguard-1.0.20200319_2.txz pkg add http://pkg.freebsd.org/FreeBSD:11:amd64/latest/All/wireguard-go-0.0.20200320.txz pkg add https://github.com/Ascrod/pfSense-pkg-wireguard/releases/download/v1.0.0/pfSense-pkg-wireguard-1.0.0.txzI'm on pfSense 2.4.5, and on the status page I can see only the interface and not the peer that I've correctly configured.
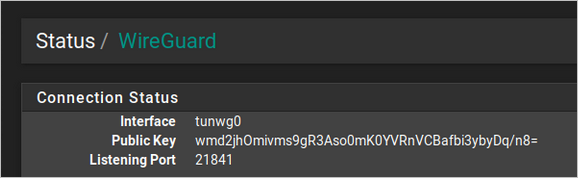
I've OpenVPN clients running but I've tried to disable every clients, disabled OpenVPN clients interfaces, rebooted but nothing. Only Interface tunwg0 is up and not the peer (WireGuard Mullvad Server).
Thank you so much,
-
Dear Ascrod,
Hello and I hope that you are safe and well during these trying days and times. I set this up on a VM and have it working well using TORGUARD WIREGUARD service. I tried my hand at this earlier on see here : https://forum.netgate.com/topic/145099/pfsense-wireguard-client-working-with-catch-22 - with albeit limited success. My question is - can you make an Ascrod pfSense-pkg-wireguard-1.0.0.txz package for pfSense 2.5.0 . You answered another on here who inquired about pfSense 2.5.0 that " Unfortunately I don't have a spare physical machine to use for testing 2.5, but I did install all three packages on a VM and did some preliminary testing." Well, I tried this on pfSense 2.5.0 and your current pfSense-pkg-wireguard-1.0.0.txz package - and I could not install it because it said that I had the wrong architecture. Overall, I wish to thank you for your outstanding work on building this package and advancing the development of WireGuard on pfsense. Peace - God Bless You and Yours - and stay Safe -
@dubatech I followed the guide and I think the tunnel towards Mullvad is up.
Interface tunwg0
Public Key --------------------------------------------------
Listening Port 51820Peer ---------------------------------------
Endpoint 185.65.135.222:51820
Allowed IPs 0.0.0.0/0
Latest handshake 12 seconds ago
Transfer 1.93 KiB received
9.66 KiB sentHowever. I the gateway is considered down, which means I cannot route any traffic through the tunnel. I have two redundant OpenVPN to Mullvad, and want to be able to select which traffic should be sent by wireguard. But since the gateway is considered down, I cannot get it to work.
And by the way. You Mullvad said you could upload your public key by:
curl https://api.mullvad.net/wg/ -d account=YOURMULLVADACCOUNTNUMBER --data-urlencode pubkey=YOURPUBLICKEY
I got it to work by:
curl https://api.mullvad.net/wg/ -d account=YOURMULLVADACCOUNTNUMBER -pubkey=YOURPUBLICKEY
I assume that the key alreay are URL-encoded. -
Interesting development, looks promising.
Just a small addition from me: I wasn't able to pull the mentioned packages on my Netgate SG-1100, as it isn't
amd64. As far as I see the wireguard-packages you depend on aren't yet available foraarch64Your command gives me:
pkg: wrong architecture: FreeBSD:11:amd64 instead of FreeBSD:11:aarch64then I browsed the repo at
http://pkg.freebsd.org/FreeBSD%3A11%3Aaarch64and could not find the mentioned packages for that architecture.No problem, no hurry here. I just wanted to mention that.
-
@Talisker said in I made a WireGuard package for pfSense:
However. I the gateway is considered down, which means I cannot route any traffic through the tunnel. I have two redundant OpenVPN to Mullvad, and want to be able to select which traffic should be sent by wireguard. But since the gateway is considered down, I cannot get it to work.
Leaving the monitored ip the same as the gw ip, also for me gateway appears to be offline.
But changing the monitor IP to an external IP, the gateway is up and running.Mine is pinging cloudflare ip:
Hope you can fix it.
-
I just tried this out for myself on an up-to-date 2.4.5 bare-metal install. I found I had to use the following components to get it to work, the original links are out-of-date:
1. pkg add pkg add http://pkg.freebsd.org/FreeBSD:11:amd64/latest/All/bash-5.0.17.txz 2. (opt.) pkg add pkg add http://pkg.freebsd.org/FreeBSD:11:amd64/latest/All/bash-completion-2.10,2.txz 3. pkg add http://pkg.freebsd.org/FreeBSD:11:amd64/latest/All/wireguard-go-0.0.20200320.txz 4. pkg add http://pkg.freebsd.org/FreeBSD:11:amd64/latest/All/wireguard-1.0.20200513.txz 5. pkg add https://github.com/Ascrod/pfSense-pkg-wireguard/releases/download/v1.0.0/pfSense-pkg-wireguard-1.0.0.txzBut now, I'm lost in how to configure it. The "?" link doesn't go to any sort of instructions. I trust the OP, I just don't know what to do after I get things set up.
-
@dubatech No, I just wont get it to work.
I have used ping.sunet.se = 192.36.125.18 and other IP addresses specificly intended to answer to ping, but cannot get the gateway to be considered up.
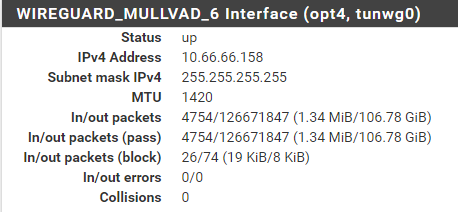
Apparently there are traffic through the interface, but I do not get a "gateway" IP for it:
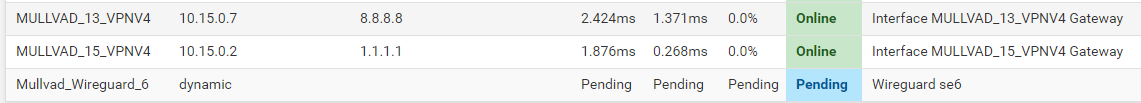
In OpenVPN the IP is has been given dynamically is the gateway, but the hardcoded IP in the Wireguard doesn't show up. I have tried to set is as fixed in the Interfaces-declaration, but it still only says dynamic on the status page.Finally. I got it to work. I dont really know why. I think it was because I changed the Public key by generating a new one and upload it like this:
curl https://api.mullvad.net/wg/ -d account=YOURMULLVADACCOUNTNUMBER -d pubkey=YOURPUBLICKEY
I assume that the key alreay are URL-encoded.
I then changed the IP address in the wireguard configuration to the IP I got as a reply on the curl command above!!!