Transparently Intercept and Redirect DNS Traffic to an Internal DNS
-
It seems to be something to do with using aliases in the rule that's causing that particular issue, I've submitted a bug report on redmine
I have two pihole's behind a VIP, so the DNS alias contains 192.168.1.250 (VIP), 192.168.1.2 (pihole 1), 192.168.1.3 (pihole 2) and 192.168.1.1 (pfsense). The piholes forward the request to pfsense, pfsense forwards to my ISP DNS resolvers.
So I have ! DNS to ensure that requests to any of these IP's don't get affected by the NAT rule. I want all clients in the DHCP ranges to use pihole's or pfsense's DNS only, for situations where devices e.g. NVidia Shield TV hardcode google DNS in certain places and apps.
I'm not sure why all interfaces are specified in the NAT rule in /tmp/rules.debug, as I only have 3 NAT rules, 1 for each interface LAN, GWN and IOT.
Anyway, what you've described above is mostly the same as what I've done including the outbound NAT rule so everything is working good for me atm

-
This post is deleted! -
Not sure why you deleted the question.. But I will tell you - I trust the authoritative NS for the domain I am looking for something in.. Nobody else - why would I ask X for Y, when I can just ask Z directly hey what is the IP of host.domain.tld that you are authoritative for..
Better yeah when they sign said info with dnssec. I would never forward all my dns request to anyone and "trust" them.. When I can just get the info direct from the horses mouth..
When you resolve you ask roots, hey who is authoritative for tld, (signed) hey NS for tld who is authoritative for domain.tld (hope signed).. Ok thanks hey NS for domain.tld what is IP of host.yourdomain.tld (again hope signed).
Why would I not do that vs asking hey billy what is ip of xyz.domain.tld - how do you trust that???
-
This has been a great source of info for best practice ways to setup a pi-hole with pfSense.
For my homelab, I'm migrating away from a flat network and have been using what I've learned here to apply to my network.
One issue that I'm having is that I would like to us the dns forwarder option because I don't want to edit my rules for things like IOT and Guest from knowing the IP range of another internal VLAN.
My plan was to use the DNS forwarder but it points to the DNS IPs in System/General Setup/DNS.
My issue is that I have all of my internal traffic ran through a VPN_GatewayGroup, including the pi-hole. The only thing I have coming out locally is the General Setup DNS to allow pfSense to be able to build the domain based vpn tunnels.
The recommendation here with the rules and NAT looks good but no matter which VLAN I put the pi-hole there will be local services that need it. Is there a way to override the DNS Forward DNS address and let the pfSense itself continue to use the System/General settings?
Thanks a bunch
-
@cyrus104 said in Transparently Intercept and Redirect DNS Traffic to an Internal DNS:
I would like to us the dns forwarder option because I don't want to edit my rules for things like IOT and Guest from knowing the IP range of another internal VLAN.
Huh?? What does that have to do with using the forwarder or resolver?
-
If I just do as other suggest and put the pi-hole DNS server (on a different VLAN) in the DHCP than IOT / Guest devices will not only know the IP range they are placed into by dhcp but will also know about another network segment.
So I would like to use forwarder / resolver but it seems like these require the use of the the System / General Setup / settings. If I make the pi-hole server the number one option here I think I have an issue on full reboot because all LAN traffic is forced out of VPN connection that aren't yet established and won't be due to the pi-hole dns being needing to go out of the LAN interface.
-
@cyrus104 said in Transparently Intercept and Redirect DNS Traffic to an Internal DNS:
Guest devices will not only know the IP range they are placed into by dhcp but will also know about another network segment.
No they wont - since your doing an intercept of the dns traffic - they have no freaking idea where it got sent, for what they know is it answer from who they sent it too 8.8.8.8
I even posted a screenshot showing that the query was to 8.8.8.8..
What your pihole will know is the IP of the source who did the query.. But to the client he sent query to 8.8.8.8 and got answer, he has no idea it came pihole or any other internal dns server. Or what network pihole/dns was on..
-
Hey your the man, you've got 24k posts here and know more than probably anybody. I would ask that before you get your panties in a twist you read what people are asking. That sentence was specific to listing the DNS in the DHCP server section. In my limited understanding and testing of how DHCP works, when I put a DNS address in the DHCP it gets passed directly to the client.
Both of my latest posts highlight that your method is probably best... but I still need a DNS solution for the VLAN / subnet that the pi-hole DNS solution is put on. I'm not putting it on my DMZ as you suggested but on a management vlan and need the other servers / services to have access to that vlan without hardcoding it into them.
-
You can redirect traffic from pfsense on same segment, you just have to source nat it.. And now your pihole will not know that client X asked or client Y asked... Since it will all look like it came from pfsense.
Is there a way to override the DNS Forward DNS address and let the pfSense itself continue to use the System/General settings?
Yea set the forwarding in the custom option box vs using the checkbox.. Now you can point pfsense to whatever you want for dns
@cyrus104 said in Transparently Intercept and Redirect DNS Traffic to an Internal DNS:
eed the other servers / services to have access to that vlan without hardcoding it into them.
Already went over how to do this..
Here is what I would suggest, and why adding to OLD threads is problematic... Your ask or question really has ZERO to do with this thread.
You should start your OWN thread, laying out your exact questions and what your trying to accomplish..
-
@johnpoz said in Transparently Intercept and Redirect DNS Traffic to an Internal DNS:
You can do it when the dns server is on a different network.. Here I create a redirect on my lan network 192.168.9/24 to redirect to my pihole which is on my dmz or 192.168.3/24 network..
So you can see I did a query to 8.8.8.8 and was redirect to pihole, which logged it as my PC I did the query from I5-win box..
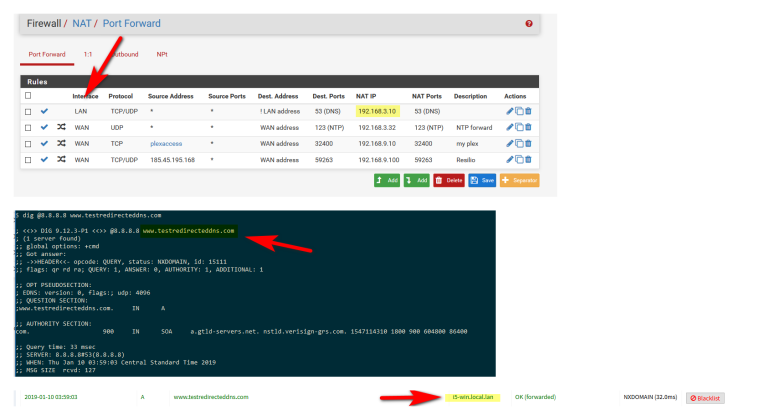
Where your going to have problems is trying to redirect traffic in and out the same interface with a port forward.
Move your pihole to its own segment and you will be fine.
As to unifi, not sure how they do it? Haven't look into it - but if you think they are out doing pfsense... Have at it ;) I had to run their USG for a while.. Their dns features are WAY behind... Well all their feature to be honest.. Creating a simple firewall rule was a PITA... Running multiple vlans, again PITA, etc..
I have the USG sitting on my self... Let you have it at pfsense forum users discount if you want it ;)
How can your PiHole see the Name of the Client? Mine only shows the IP :/
-
Because pfsense knows the name, and it does a PTR for it..
How pihole assigns name to an IP is via a PTR query for the IP..
-
@johnpoz I tried this setup and it works, as in I do get the right host name at the pihole end, but I get the following error as well:
❯ dig @8.8.8.8 dns-redirect-test.com ;; reply from unexpected source: 192.168.8.2#53, expected 8.8.8.8#53 ;; reply from unexpected source: 192.168.8.2#53, expected 8.8.8.8#53 ;; reply from unexpected source: 192.168.8.2#53, expected 8.8.8.8#53 ; <<>> DiG 9.10.6 <<>> @8.8.8.8 dns-redirect-test.com ; (1 server found) ;; global options: +cmd ;; connection timed out; no servers could be reached192.168.8.2is the IP of the pihole.
LAN1 (on which all devices sit) is192.168.7.x
LAN2 (on which pihole sits) is192.168.8.xProbably something to do with properly setting up an outbound NAT rule but I've tried diff configs, none seem to resolve the issue.
Any pointers are welcome.
-
@ibbetsion
The NAT Rule is only valid for the .7. net? -
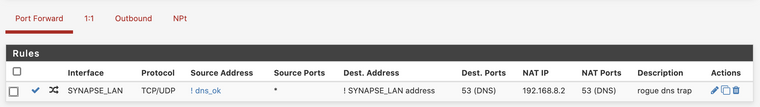
@Marv21 the redirect NAT rule is set up for the .7. net.
In the image below,SYNAPSE_LAN = .7.net.
-
@ibbetsion
dns_ok is 192.168.8.2 then - right? -
@ibbetsion
Where are you running this Dig command from?
A client from the 7 or the 8 Net? -
@Marv21 Sorry for omitting that,
dns_okis an alias that I use for those hosts that are allowed to make queries to external DNS servers. Any local host not in this alias/group should be re-routed to the local DNS server at192.168.8.2 -
@Marv21 the dig command is running from a host on the 7 Net.
-
@ibbetsion said in Transparently Intercept and Redirect DNS Traffic to an Internal DNS:
; reply from unexpected source: 192.168.8.2#53, expected 8.8.8.8#53
No shit what do you think was going to happen... This is why you put your NS your going to redirect to on a different vlan.. Or you have to forward it to loopback.. So pfsense does the query, and then sends the answer..
-
@johnpoz the NS is on a different subnet...