How to create IPv6 firewall rules?
-
Hi,
I'm trying to get my feet wet with IPv6 as my ISP has native support now. I
configured it on two interfaces, so far so good. But I struggle to create firewall rules. I just don't know how.E.g. in IPv4 I had an alias like
internal_nets = 10.0.0.0/8, 192.168.0.0/16So I could allow external traffic with a rule “allow !internal_nets”. But in IPv6 the addresses are dynamic. A new address every other day or so (domestic
connection).- How to create an alias for the internal nets (IPv6)?
- How to create firewall rules if I don't know the address of the hosts?
Very basic questions, but I couldn't find anything relevant in the pfSense documentation. A nudge in the right direction would be much appreciated.
2.4.5-RELEASE-p1
-
@zjgn I don't think it is possible yet.
Somewhat workarounds are to make the IPv6-address live longer like so:
@JKnott said in DDNS IPv6 Cloudflare:
Also, there's a setting you want to ensure is selected. It's "Do not allow PD/Address release" on the WAN page. If that's not selected, the address might change. I found all it took was to disconnect/reconnect the WAN Ethernet cable.
Or to get a IPv6-tunnel from HE with their addresses not changing at all.
But still, you have to watch closely for Temporary IPv6 Addresses, SLAAC and such, it is a pain in the a...

-
@Bob-Dig said in How to create IPv6 firewall rules?:
But still, you have to watch closely for Temporary IPv6 Addresses,
It's nice to be quoted.

As for the temporary addresses, they're normally used only for outgoing connections, so you generally don't need to create rules for them. However, if you want to allow incoming connections, you use the consistent address, often MAC based, and create the rules for it.
-
@JKnott said in How to create IPv6 firewall rules?:
It's nice to be quoted.

You deserved it.
@JKnott said in How to create IPv6 firewall rules?:
As for the temporary addresses, they're normally used only for outgoing connections, so you generally don't need to create rules for them.
Unless you want to block connections from that host.
In the end, I created multiple interfaces to get back control, one of them has no IPv6 at all. If your gear supports vlans, you can go with that, but mine didn't.
-
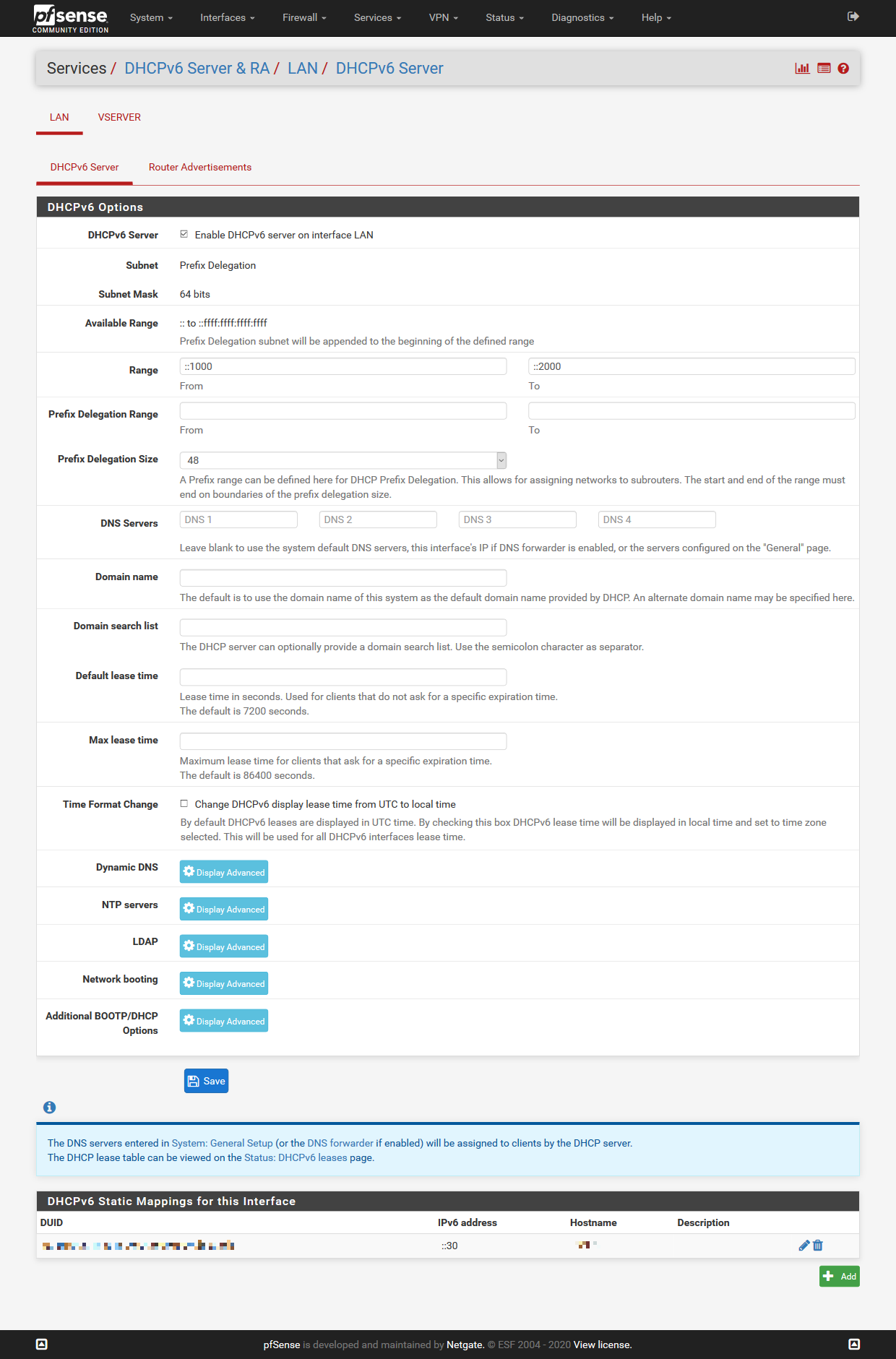
One last thing, you can define Static Mappings within the DHCPv6 Server & RA to set hostnames, like with ipv4, so at least incoming firewall rules will then work just fine using aliases containing these hostnames, even with a dynamic IPv6-prefix on that interface.
-
@Bob-Dig said in How to create IPv6 firewall rules?:
@zjgn I don't think it is possible yet.
?? I'm very surprised that this isn't possible in pfsense. I assume many people use it on domestic connections with changing IPs. But apparently not many people bothered setting up IPv6, though.
Somewhat workarounds are to make the IPv6-address live longer like so:
@JKnott said in DDNS IPv6 Cloudflare:
Also, there's a setting you want to ensure is selected. It's "Do not allow PD/Address release" on the WAN page. If that's not selected, the address might change. I found all it took was to disconnect/reconnect the WAN Ethernet cable.
I tried that. Didn't work. After a reboot the address changed. And even it it worked for a while, I don't want my firewall rules get outdated after a while, out of my control. That's not a robust design.
Or to get a IPv6-tunnel from HE with their addresses not changing at all.
Getting an IPv4 to IPv6 tunnel on a native IPv6 connection seems like a crutch. I just checked, my ISP only offers static IPs on business connections, not on domestic ones.
But still, you have to watch closely for Temporary IPv6 Addresses, SLAAC and such, it is a pain in the a...
So far (with IPv4) I use DHCP and registered the host names in DNS. Then the aliases and rules are based on the host name. I don't know how to do that with IPv6 and SLAAC. As far as I found out so far, SLAAC addresses don't register in DNS, so one has to use DHCPv6 to create rules based on the hostname. But this doesn't work with Android devices. This IPv6 stuff looks very messy still (or it's my lack of understanding, or a mix of both).
-
@Bob-Dig said in How to create IPv6 firewall rules?:
One last thing, you can use Static Mappings with the DHCPv6 Server & RA to create firewall rules for hostnames, like with ipv4, so at least incoming firewall rules will work just fine using aliases, even with dynamic IPv6-address-prefixes on that interface.
I'll look into that. Thanks.
But does this help creating a default outbound rule? Basically most of my VLANs have a rule stating “allow all outgoing traffic to the internet but not other vlans” (as mentioned in the OP). For that I use an alias “internal_nets”.
I fail to see how static mappings would help creating such a rule. Is there another approach creating such a rule? I need to allow outgoing traffic somehow.
-
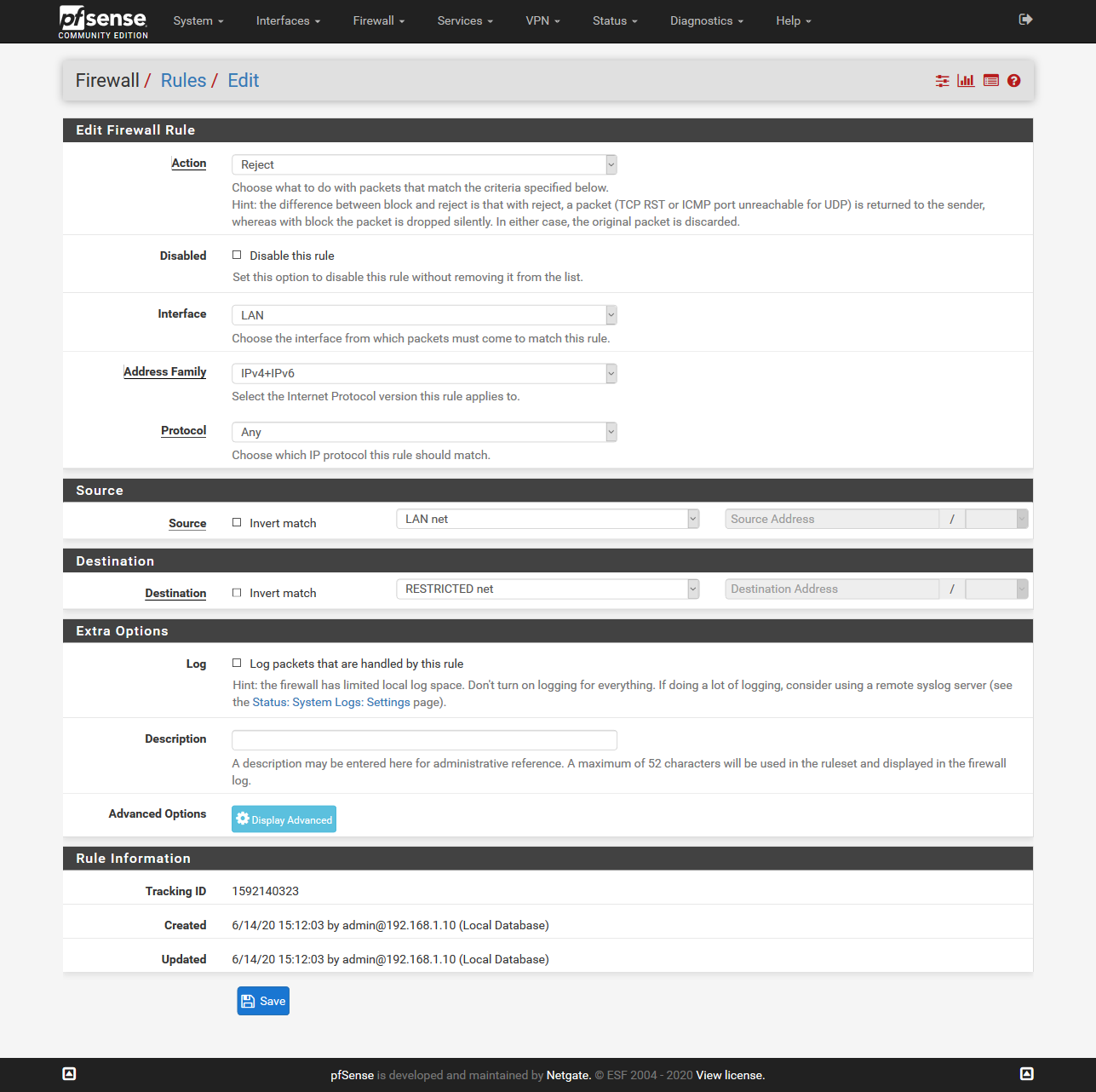
@zjgn Have you tried something like that (for every vlan, probalbly a lot of work)?
Also, I am guessing here, had no demand for that myself and haven't tested it.
-
And if you want to go to the extreme, you could deploy private IPv6-addresses and then use NPt, which works flawlessly.

(Edit: But not with a dynamic prefix. )
) -
@Bob-Dig said in How to create IPv6 firewall rules?:
@zjgn Have you tried something like that (for every vlan, probalbly a lot of work)?
I just tried, and a test rule seems to work. That would be very verbose, though. But it's a solution after all.
The big question is if the NET-based rules are automatically updated when the prefix changes? Otherwise the rules invalidate themselves after a short while.
If this works, I could at least get outgoing traffic flowing. That doesn't solve creating rules for individual hosts, though. But it's a step forward, thanks.
-
@Bob-Dig said in How to create IPv6 firewall rules?:
And if you want to go to the extreme, you could deploy private IPv6-addresses and then use NPt, which works flawlessly.
NPt is basically NAT, right? If so: Nope. Just no.
That's why I started looking into IPv6 in the first place. I want to get rid of NAT.
Regarding extreme: I just want a simple IPv6 config for my home network. A few vlans, voip/sip, web server dmz, guest vlan, etc. Nothing fancy. Basic standard stuff, I suppose. But apparently it's not so simple to implement in pfsense.
Thanks for the quick responses so far.
-
You understand that pfsense creates its own aliases for any network its attached to be it IPv4 or IPv6.. Just the name of that network, ie LAN Net, or VLAN Net, etc. etc..
So you can just use those in your rules..
-
@johnpoz Thanks for confirming.
-
@Bob-Dig said in How to create IPv6 firewall rules?:
Unless you want to block connections from that host.
Then you'd have to block every address for the prefix. While you know the consistent address, the privacy addresses can be anywhere with the 18.4 billion, billion addresses a /64 provides. The only way around this would be to filter on MAC addresses, which pfSense doesn't do.
In the end, I created multiple interfaces to get back control, one of them has no IPv6 at all. If your gear supports vlans, you can go with that, but mine didn't.
What is it you're trying to do?
-
@johnpoz said in How to create IPv6 firewall rules?:
So you can just use those in your rules..
But you can't use these in an alias and stack them, right?
-
@JKnott said in How to create IPv6 firewall rules?:
@Bob-Dig said in How to create IPv6 firewall rules?:
Unless you want to block connections from that host.
Then you'd have to block every address for the prefix. While you know the consistent address, the privacy addresses can be anywhere with the 18.4 billion, billion addresses a /64 provides. The only way around this would be to filter on MAC addresses, which pfSense doesn't do.
Or you can disable privacy extensions on that host. My ubunt servers don't use it in the beginning.
In the end, I created multiple interfaces to get back control, one of them has no IPv6 at all. If your gear supports vlans, you can go with that, but mine didn't.
What is it you're trying to do?
Getting back control is what I did. Some has to do with using the vpn-clients and defeat any leaks.
-
@Bob-Dig said in How to create IPv6 firewall rules?:
But you can't use these in an alias and stack them, right?
No AFAIK you can not stack them... Or join them into a parent alias sort of thing..
Just create distinct rules would be one option... The whole nonsense that is dynamic space is the only reason this is an issue.. Or you could just create the rules with whatever blocks of space you wanted. I have a /48 from HE, so my IPv6 address space never changes.. Had that same space for like 10+ years now..
-
@johnpoz said in How to create IPv6 firewall rules?:
@Bob-Dig said in How to create IPv6 firewall rules?:
But you can't use these in an alias and stack them, right?
No AFAIK you can not stack them... Or join them into a parent alias sort of thing..
That's unfortunate. It would make for much cleaner rules and be quicker to implement if there are many VLANs.
-
@zjgn I am just thinking about that: if the VLANs are more like DMZs, you could create one block rule for every VLAN (source = *, destination = vlan(x)) and then deploy those rules on all the vlans by using Interface Groups or floating rules. It should have no impact if the connection is on the same VLAN anyway.
Just some, maybe wrong, thoughts.
-
I have been trying out a lot with dynamic IPv6 and my conclusion was not to use IPv6 for internal communication for now (only for Internet communication), and only use IPv6 for one WAN of my Dual-WAN setup, there are just too many open topics for regarding dynamic IPv6 in pfSense. I currently mainly waiting for https://redmine.pfsense.org/issues/4881 and https://redmine.pfsense.org/issues/6880. Maybe also https://redmine.pfsense.org/issues/9536 and https://redmine.pfsense.org/issues/6626.
To prevent communication between my VLANs, I have basically done what @Bob-Dig suggested above, i.e. with block rules using "xxx net", as combined IPv4+IPv6 rules, so it blocks at least both.
My target scenario is going to be to use ULAs and (dynamic) NPt to be able use use fail-over between the WANs, but it also makes internal communication easier because the prefix stays static. In my opinion, NPt should not be directly compared with NAT in IPv4, because it works very very differently as the whole prefix is just translated 1:1 so you can still communicate directly without any port mapping or keeping any state. For incoming traffic the destination prefix is just mapped to the internal one and for outgoing traffic the source prefix is just mapped to the public one, but the host part, ports etc. stay the same.
For "DMZ stuff" and also for IPSec VPN from my iPhone, I have separate public IPv4 addresses and an IPv6 prefix independently of my ISPs from a dedicated "static IP provider", connected via OpenVPN, because this is crappy anyway with dynamic addresses.