WebGUI access on all interfaces ?
-
I have 2 physical interfaces and OpenVPN server, say
LAN 192.168.90.1
WIFI 192.168.70.1
OpenVPN 192.168.20.1and DDNS name <blah.blah.blah>
I can access my router WebGUI via all of them.
What are the best practices to manage access to WebGUI access ?
One use case I am interested in - disallow all access to WebGUI on one interface, say WIFI?
Thx
-
This post is deleted! -
https://docs.netgate.com/pfsense/en/latest/firewall/restrict-access-to-management-interface.html
-Rico
-
@chudak said in WebGUI access on all interfaces ?:
I can access my router WebGUI via all of them.
That's NOT default.
pfSense, as it came out of the box, only accept WebGUI access from its LAN interface. All interfaces have no rules so the default firewall policy kicks in : block all **.The WebGUI is running on port 80 or port 443 - only you know which one it is, or what port other number it is.
The destination will be the 'pfSense' IP of that interface.
Like, in your case, use the alias "Wifi_address".On the interface where you want to block, put a block rule on top, TCP, port number, destination Wifi_address.
Leave the rest at default, and Save, Validate.** maybe an exception : when you use the OpenVPN server wizard, it will put a pass-all firewall rule on yhe OpenVPN interface, thus permitting to access the WebGUI.
-
Oh btw, you posted almost the same question here some days ago: https://forum.netgate.com/topic/154387/easy-way-to-restrict-webconfigurator-access-on-openvpn-only
The concept is always the same, no matter if it is a wire Interface, Wifi, VLAN, virtual Interface like OpenVPN, Interface Group, ...-Rico
-
@Rico said in WebGUI access on all interfaces ?:
Oh btw, you posted
I don't dare to look neither ask : I was answering there also ?
My memory said that the same question was ask a couple of days ago.
The answer wasn't clear ... ? -
Your answer there was clear as crystal.

-Rico
-
@Rico said in WebGUI access on all interfaces ?:
Your answer there was clear as crystal.

-Rico
Guess @chudak doesn't share that opnion.
-
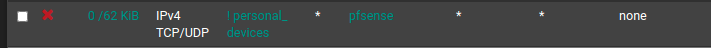
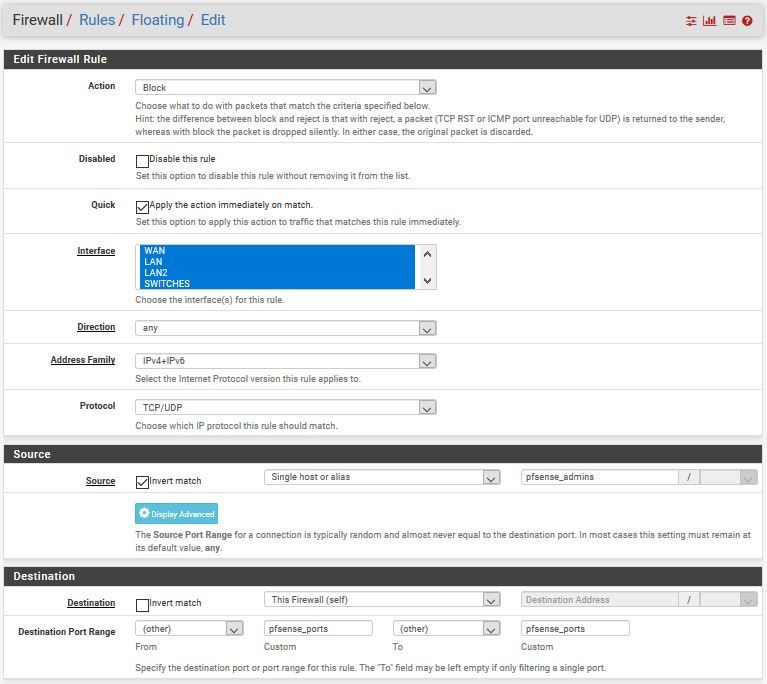
Hi. You can create an alias of "pfsense ports" (such as webgui port, ssh and etc.), and the ip address of admins and create a floating rule and select the interfaces that you want to allow or disallow.
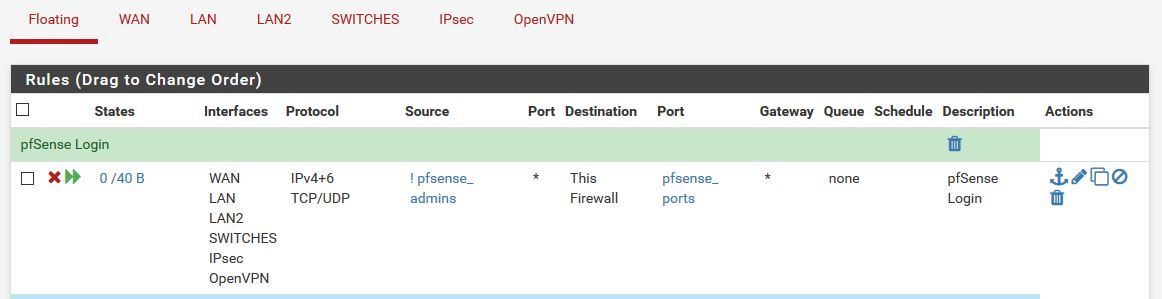
-
-
Check "Apply the action immediately on match".
-
@chudak : @emammadov proposed a rule that blocks the access to the webgui of pfSense.
You forgot to copy half of all settings, and created a rule that blocks the access to any web site on planet earth. -
-
Close to perfect

Instead of creating your own alais called pfSense - the one you forget to change when you change the IP of the LAN of pfSense == potential pitfall, use the alias that was designed for this "This firewall".
-
This is interesting.
The reason I have alias called pfSense because it lists LAN addresses like 192.168.90.1 etc as well as DDNS addresses.I did not see "This Firewall" blocking external DDNS IPs. Did you?
PS: Thinking about it I'd say it should block ANY IPs, maybe a good feature request ?
Thx