Trying to configure IPsec for IOS 13.3.1, fails with "Negotiation with the VPN server failed"
-
Okay, after making the group changes (and rebooting), I now get a longish delay and finally get "Negotiation with the VPN server failed." I was going to post all of my WWW pages, but I can't see how you're doing that? What steps are you doing to post pfSense WWW configuration pages here in this forum?
I've gone through all the screens you posted, and I'm pretty sure I have everything correct. It doesn't seem to matter if I put the IPsec Pre-Shared Key in the user record or not, it fails both ways (although I did note that you didn't have it there).
I'm wondering if there's some other screen that I'm missing? Perhaps VPN->IPsec, Mobile Clients tab?
I'll include the current log here, in case that helps. If you can tell me how to post pfSense setting screens to this forum, I'll be happy to copy my exact configuration.
Thanks so much for your patience and hand holding in getting me going here!
Mar 2 13:04:43 charon 05[IKE] <con-mobile|1> IKE_SA con-mobile[1] state change: ESTABLISHED => DELETING Mar 2 13:04:43 charon 05[IKE] <con-mobile|1> IKE_SA con-mobile[1] state change: DELETING => DELETING Mar 2 13:04:43 charon 05[IKE] <con-mobile|1> IKE_SA con-mobile[1] state change: DELETING => DESTROYING Mar 2 13:04:43 charon 05[NET] <2> received packet: from 174.216.20.149[7712] to 50.47.113.45[500] (775 bytes) Mar 2 13:04:43 charon 05[ENC] <2> parsed AGGRESSIVE request 0 [ SA KE No ID V V V V V V V V V V V V V V ] Mar 2 13:04:43 charon 05[CFG] <2> looking for an IKEv1 config for 50.47.113.45...174.216.20.149 Mar 2 13:04:43 charon 05[CFG] <2> candidate: %any...%any, prio 24 Mar 2 13:04:43 charon 05[CFG] <2> candidate: 50.47.113.45...%any, prio 1052 Mar 2 13:04:43 charon 05[CFG] <2> found matching ike config: 50.47.113.45...%any with prio 1052 Mar 2 13:04:43 charon 05[IKE] <2> received FRAGMENTATION vendor ID Mar 2 13:04:43 charon 05[IKE] <2> received NAT-T (RFC 3947) vendor ID Mar 2 13:04:43 charon 05[IKE] <2> received draft-ietf-ipsec-nat-t-ike vendor ID Mar 2 13:04:43 charon 05[IKE] <2> received draft-ietf-ipsec-nat-t-ike-08 vendor ID Mar 2 13:04:43 charon 05[IKE] <2> received draft-ietf-ipsec-nat-t-ike-07 vendor ID Mar 2 13:04:43 charon 05[IKE] <2> received draft-ietf-ipsec-nat-t-ike-06 vendor ID Mar 2 13:04:43 charon 05[IKE] <2> received draft-ietf-ipsec-nat-t-ike-05 vendor ID Mar 2 13:04:43 charon 05[IKE] <2> received draft-ietf-ipsec-nat-t-ike-04 vendor ID Mar 2 13:04:43 charon 05[IKE] <2> received draft-ietf-ipsec-nat-t-ike-03 vendor ID Mar 2 13:04:43 charon 05[IKE] <2> received draft-ietf-ipsec-nat-t-ike-02 vendor ID Mar 2 13:04:43 charon 05[IKE] <2> received draft-ietf-ipsec-nat-t-ike-02\n vendor ID Mar 2 13:04:43 charon 05[IKE] <2> received XAuth vendor ID Mar 2 13:04:43 charon 05[IKE] <2> received Cisco Unity vendor ID Mar 2 13:04:43 charon 05[IKE] <2> received DPD vendor ID Mar 2 13:04:43 charon 05[IKE] <2> 174.216.20.149 is initiating a Aggressive Mode IKE_SA Mar 2 13:04:43 charon 05[IKE] <2> IKE_SA (unnamed)[2] state change: CREATED => CONNECTING Mar 2 13:04:43 charon 05[CFG] <2> selecting proposal: Mar 2 13:04:43 charon 05[CFG] <2> no acceptable DIFFIE_HELLMAN_GROUP found Mar 2 13:04:43 charon 05[CFG] <2> selecting proposal: Mar 2 13:04:43 charon 05[CFG] <2> no acceptable INTEGRITY_ALGORITHM found Mar 2 13:04:43 charon 05[CFG] <2> selecting proposal: Mar 2 13:04:43 charon 05[CFG] <2> no acceptable ENCRYPTION_ALGORITHM found Mar 2 13:04:43 charon 05[CFG] <2> selecting proposal: Mar 2 13:04:43 charon 05[CFG] <2> no acceptable ENCRYPTION_ALGORITHM found Mar 2 13:04:43 charon 05[CFG] <2> selecting proposal: Mar 2 13:04:43 charon 05[CFG] <2> no acceptable ENCRYPTION_ALGORITHM found Mar 2 13:04:43 charon 05[CFG] <2> selecting proposal: Mar 2 13:04:43 charon 05[CFG] <2> no acceptable ENCRYPTION_ALGORITHM found Mar 2 13:04:43 charon 05[CFG] <2> selecting proposal: Mar 2 13:04:43 charon 05[CFG] <2> no acceptable ENCRYPTION_ALGORITHM found Mar 2 13:04:43 charon 05[CFG] <2> selecting proposal: Mar 2 13:04:43 charon 05[CFG] <2> no acceptable ENCRYPTION_ALGORITHM found Mar 2 13:04:43 charon 05[CFG] <2> received proposals: IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:AES_CBC_256/HMAC_MD5_96/PRF_HMAC_MD5/MODP_1024, IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:AES_CBC_128/HMAC_MD5_96/PRF_HMAC_MD5/MODP_1024, IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:3DES_CBC/HMAC_MD5_96/PRF_HMAC_MD5/MODP_1024, IKE:DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:DES_CBC/HMAC_MD5_96/PRF_HMAC_MD5/MODP_1024 Mar 2 13:04:43 charon 05[CFG] <2> configured proposals: IKE:AES_CBC_256/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_2048 Mar 2 13:04:43 charon 05[IKE] <2> no proposal found Mar 2 13:04:43 charon 05[IKE] <2> queueing INFORMATIONAL task Mar 2 13:04:43 charon 05[IKE] <2> activating new tasks Mar 2 13:04:43 charon 05[IKE] <2> activating INFORMATIONAL task Mar 2 13:04:43 charon 05[ENC] <2> generating INFORMATIONAL_V1 request 2858304773 [ N(NO_PROP) ] Mar 2 13:04:43 charon 05[NET] <2> sending packet: from 50.47.113.45[500] to 174.216.20.149[7712] (56 bytes) Mar 2 13:04:43 charon 05[IKE] <2> IKE_SA (unnamed)[2] state change: CONNECTING => DESTROYING -
If you can tell me how to post pfSense setting screens to this forum, I'll be happy to copy my exact configuration.
Take a screenshot and drag it into the message window.
-
Hi @NogBadTheBad Thanks for the suggestion!
I'll include all of my configuration screens (let me know if I missed anything), in case this helps to diagnose my issue":
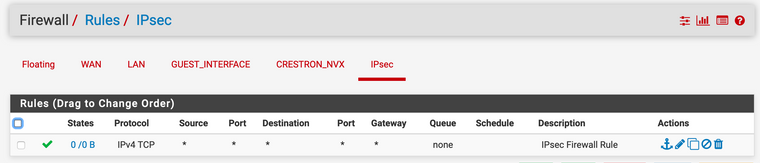
- Firewall screen:
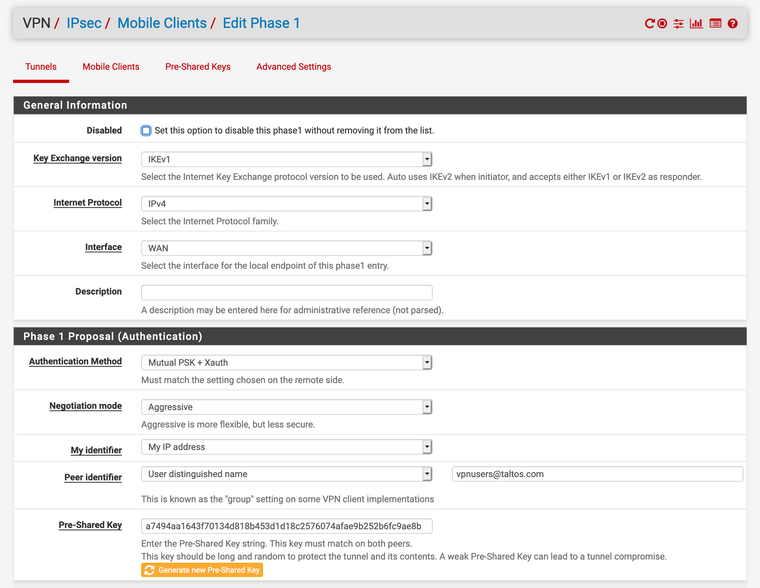
- IPsec Settings, Phase 1: (Note that I did change the pre-shared key)
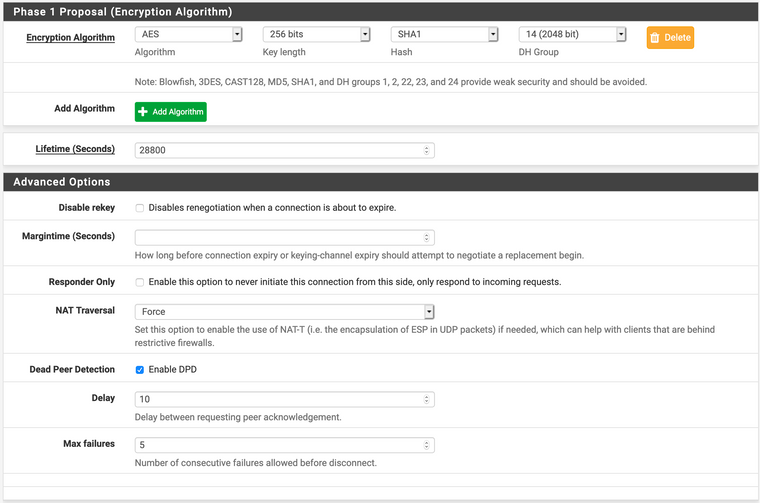
- IPsec Settings, Phase 2:
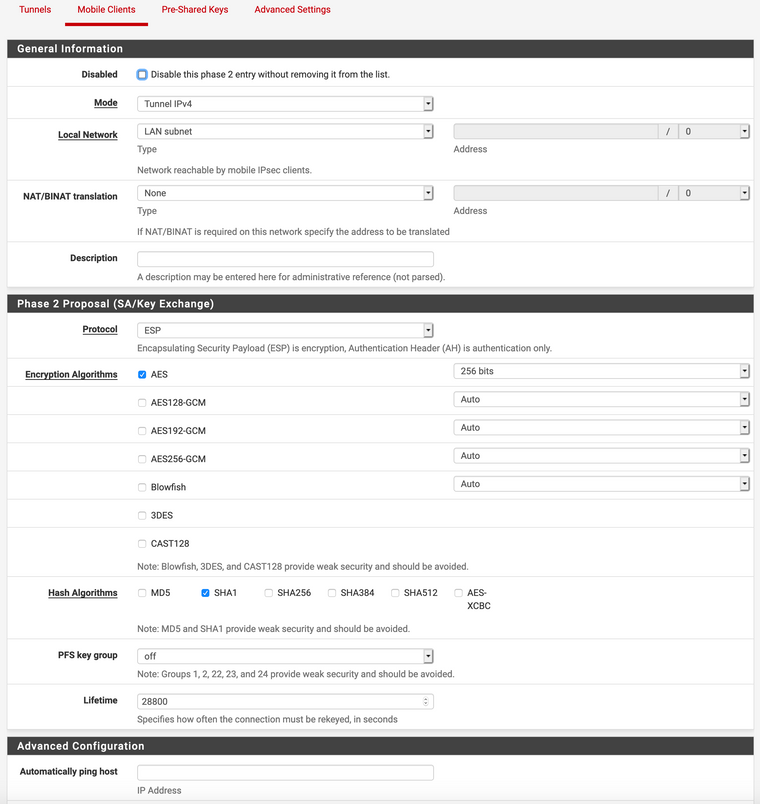
- IPsec Settings, Mobile Clients:
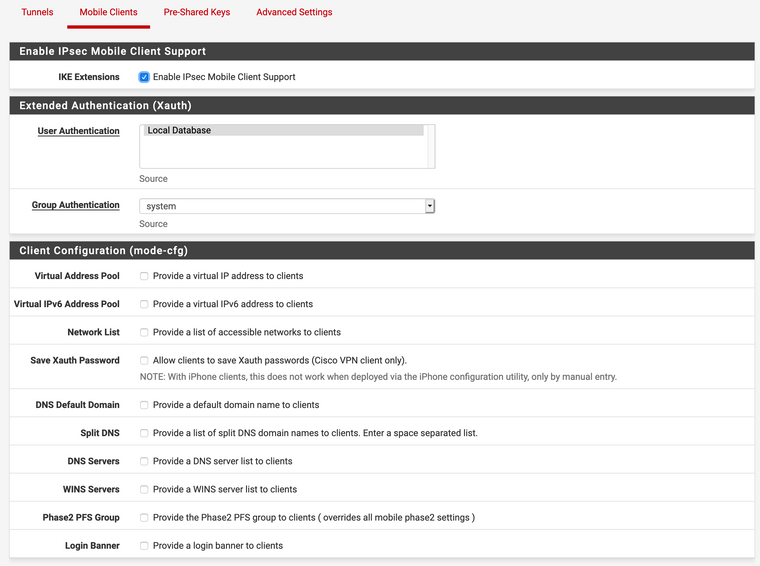
- User Settings:
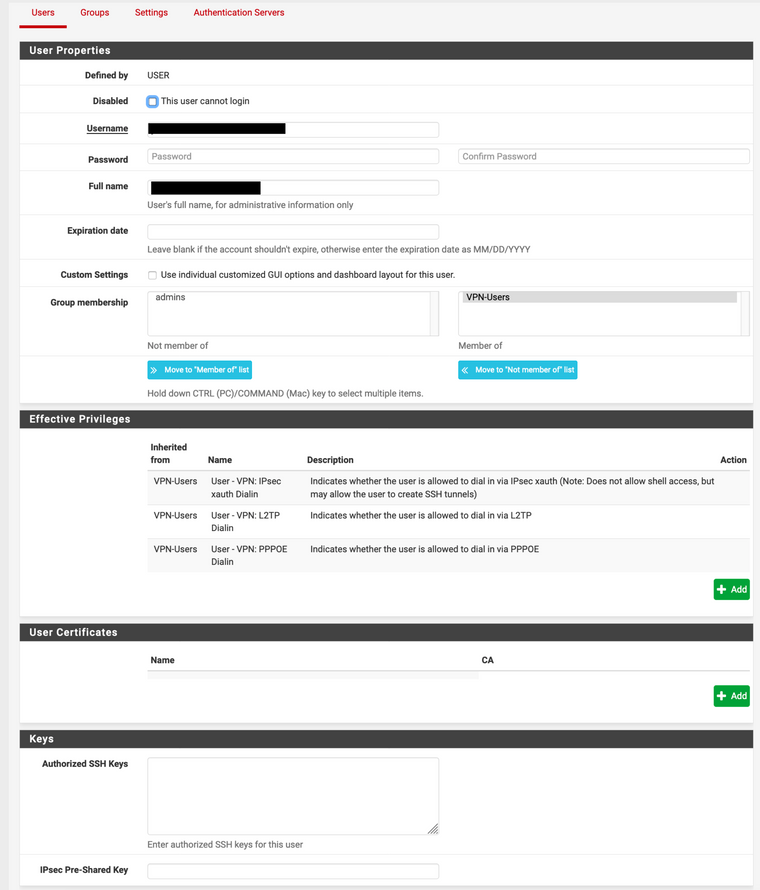
- And finally, Group Settings:
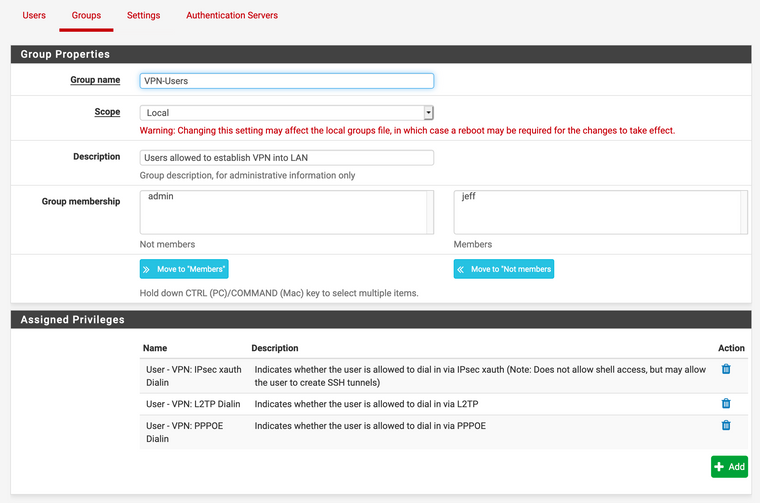
Thanks in advance for help in diagnosing my issue! If you need the current log, the one I posted before this would still be relevant.
-
Can you try DH Group 2 (1024 bit) in Phase 1.
-
Sorry for the delay. I did try changing the DH group to 2 (1024 bit) in phase 1, and that has no obvious affect. I still get
Negotiation with the VPN server failed.Any other suggestions? Thanks again for your willingness to help me with this, I really appreciate it!
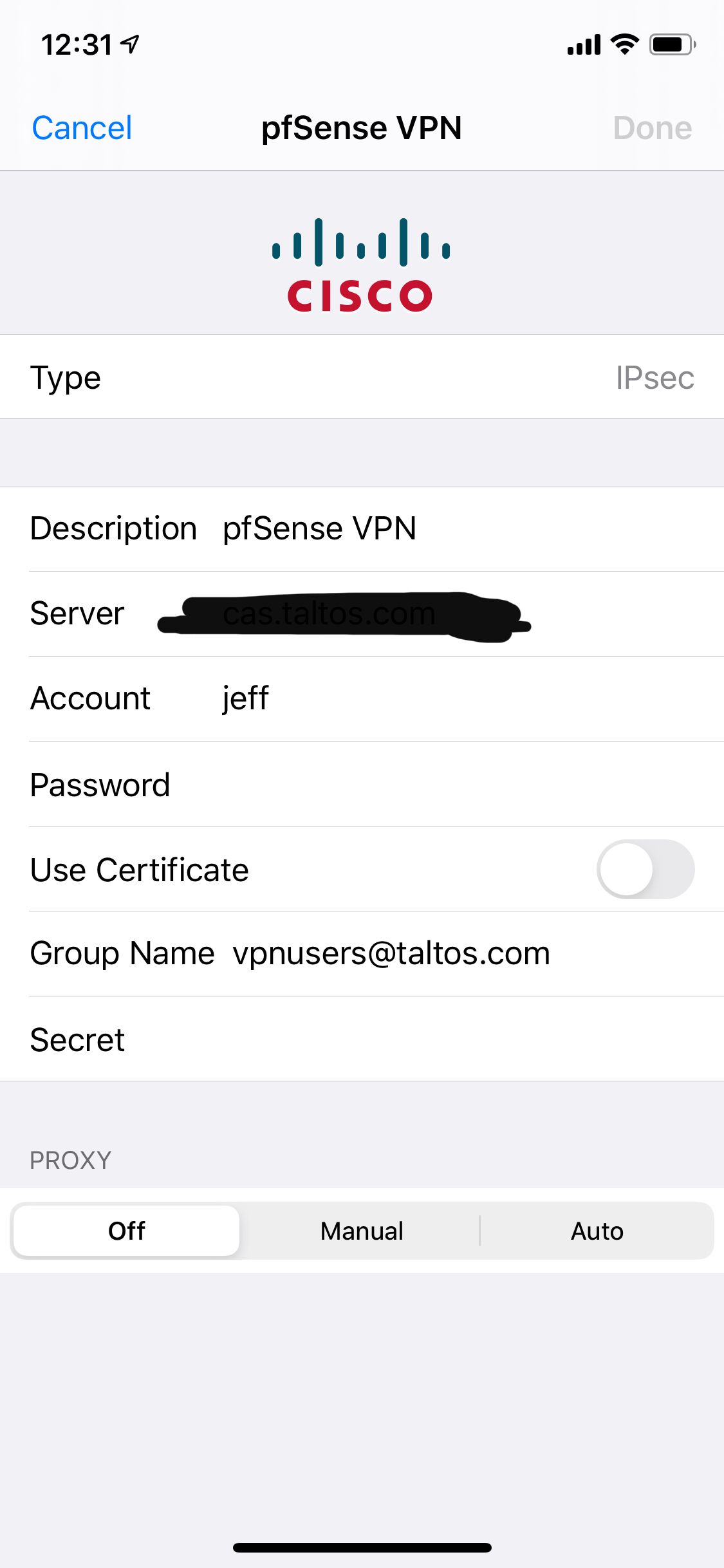
In case it helps, here's my settings screen on the iPhone:
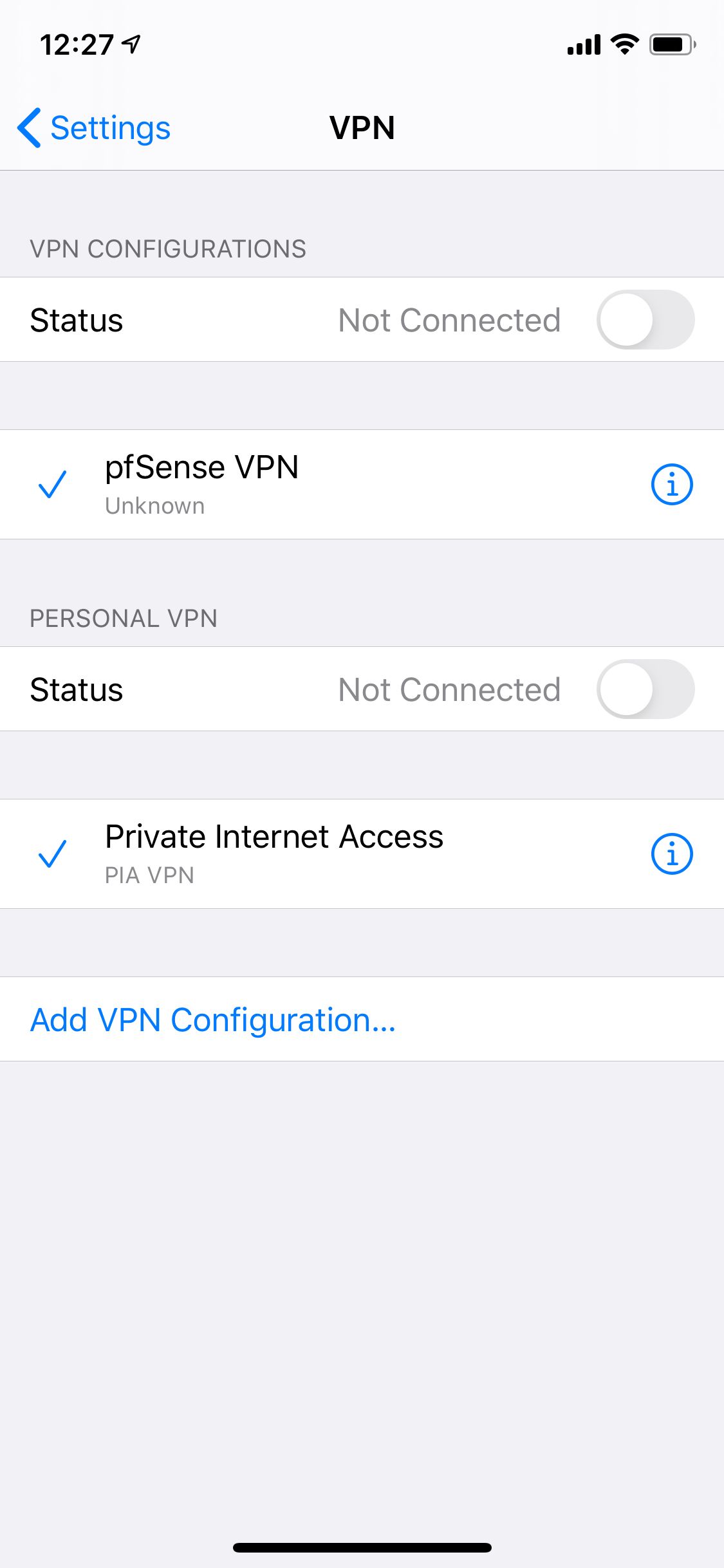
If I drill down into the pfSense VPN configuration:
And, finally, when I try and launch the VPN:
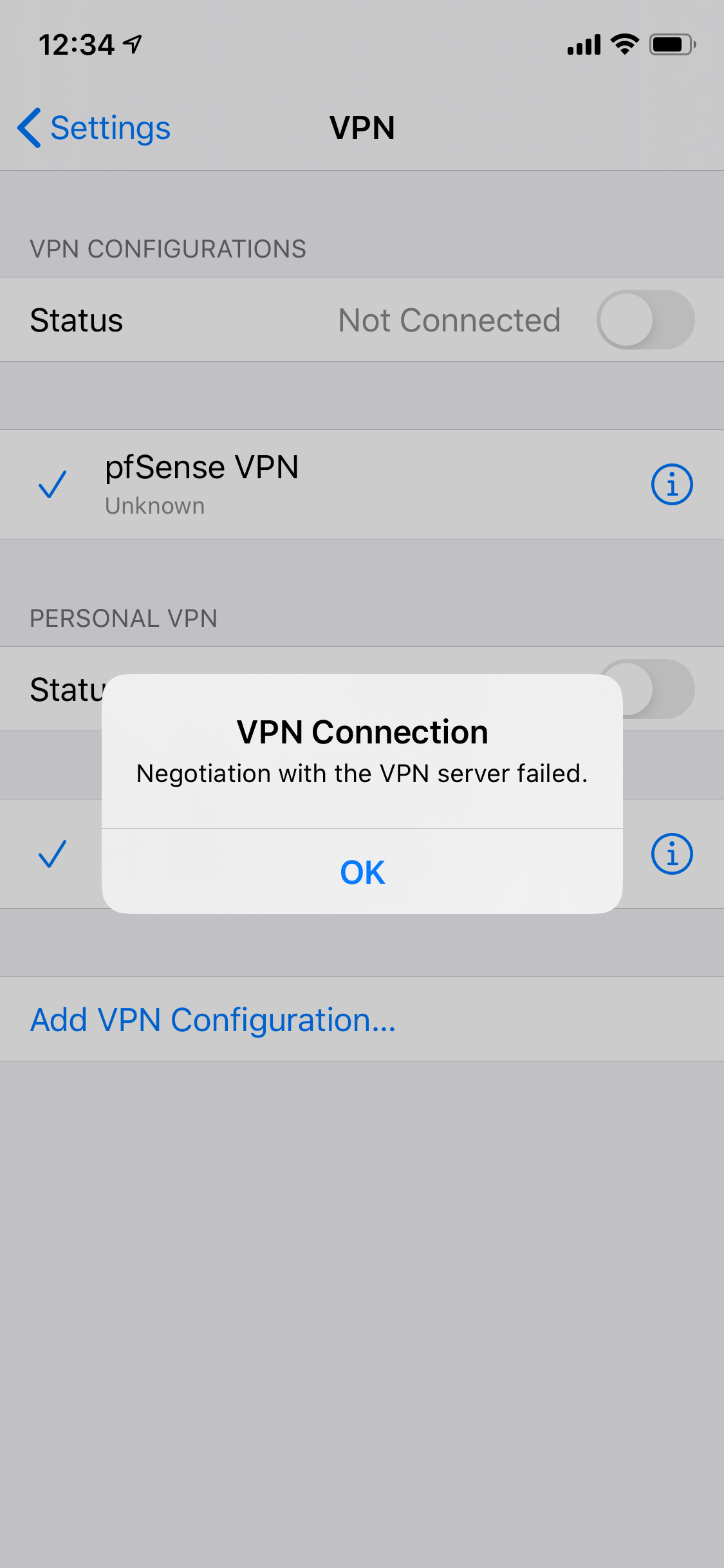
-
@jeffc any reason your using IKEv1 ?
I followed https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/configuring-an-ipsec-remote-access-mobile-vpn-using-ikev2-with-eap-mschapv2.html but I'm using Freeradius.
-
@NogBadTheBad I'm using IKEv1 for two reasons:
- A doc that I found specified using that for mobile iPhone access,
- That was also recommended in @egoisst posts, so I didn't change that.
Given that it's not working, I'm happy to try something else. This requires certs, though? I guess I'm okay with that, but it's an extra step I haven't currently done. Is that mandatory for EAP-MSChapv2?
I'll give this a try in a bit and see if it helps ... thanks!
-
I just wanted to follow up on this (really old) topic.
I did finally get IPsec configured with the iPhone, and it works great. In the end, I found that the pfSense documentation had everything I needed, including:
- How to configure the router, and
- How to configure the iPhone with the VPN properly.
See pfSense IPsec documentation for full details. Hope this helps someone!
-
Please uses IKEv2.
With IPsec Export: Apple Profile you can easy setup your iOS Device.
But if you want to use PFS, you have to insert 2 lines in the Profile output from pfsense.<key>EnablePFS</key> <true/>My Setup:
P1:
EAP-MSChapv2
AES 256
SHA 256
DH 14
Responder only
NAT Auto
Mobike enableP2:
Tunnel IPv4
ESP
AES 256
SHA 256
PFS key group 14Rekey works well if you inser the 2 lines in the ios Profile file.
-
@NOCling Thanks for your feedback. After I got the IPsec VPN working (and posting to this topic), I did look more closely at negotiated protocols. The default protocols in the pfSense documentation does get you up and running, but the encryption is not nearly as strong as desired.
After looking at what was actually negotiated between pfSense and the iPhone, I picked identical settings to you in terms of encryption.
In Phase 1, I didn't change the defaults for "Responder Only", "NAT Auto", or "Mobike enable". So, for me, "Responder Only" is disabled and "Mobike" is disabled. The rest is identical.
Why did you specifically change "Responder Only" or "Mobike enable", since it doesn't affect the iPhone? Or did you enable those for other reasons?
Also, why do "Rekey", since that's not needed either (at least for the iPhone)?
Thanks!
-
I want a Tunnel that use PFS:
https://en.wikipedia.org/wiki/Forward_secrecyClient VPN is incomming, nerver use for outgoing connections, to i set responder only.
For Outgoing i use Side 2 Side IKEv2.Mobike is a nice feature, so I turned on this crazy shit.
At my point of view, Microsoft support it 7 and Apple up iOS 9 or newer this feature.
https://tools.ietf.org/html/rfc4555