StrongSwan user authentication failed on Android
-
Thanks @Konstanti
I got this after I refreched the pageAug 8 14:59:23 charon 16[IKE] <2431> received cert request for unknown ca with keyid 6e:11:58:71:ad:6d:27:6f:f9
 93:30:c2:47:dd:f7:40:4e:e4:7f
93:30:c2:47:dd:f7:40:4e:e4:7f
Aug 8 14:59:23 charon 16[IKE] <2431> received cert request for unknown ca with keyid d3:94:8a:4c:62:13:2a:19:2e:cc:af:72:8a:7d:36:d7:9a:1c:dc:67
Aug 8 14:59:23 charon 16[IKE] <2431> received cert request for unknown ca with keyid c8:95:13:68:01:97:28:0a:2c:55:c3:fc:d3:90:f5:3a:05:3b:c9:fb
Aug 8 14:59:23 charon 16[IKE] <2431> received cert request for "CN=internal-ca, C=SA, L=Riyadh, O=International"
Aug 8 14:59:23 charon 16[IKE] <2431> received cert request for unknown ca with keyid bd:ff:8d:1d:59:4d:83:2b:a7:da:e3:87:6e:63:68:1c:13 a6:c0
a6:c0
Aug 8 14:59:23 charon 16[IKE] <2431> received cert request for unknown ca with keyid 14:8d:b3:54:ed:9b:2f:13:08:7c:c3:8b:4b:c1:5b:96:8a:c5:53:78
Aug 8 14:59:23 charon 16[IKE] <2431> received cert request for unknown ca with keyid ee:e5:9f:1e:2a:a5:44:c3:cb:25:43:a6:9a:5b:d4:6a:25:bc:bb:8e
Aug 8 14:59:23 charon 16[IKE] <2431> received cert request for unknown ca with keyid c4:52:72:20:a9:58:c0:6e:9d:4b:f2:0b:21:12:3c:eb:3a:0b:6b:6f
Aug 8 14:59:23 charon 16[IKE] <2431> received cert request for unknown ca with keyid f8:f6:fa:6b:26:1b:cc:64:62:12:46:30:d1:c5:99:15:cd:01:1f:cb
Aug 8 14:59:23 charon 16[IKE] <2431> received cert request for unknown ca with keyid 95:a3:72:ff:cd:41:d7:e9:fd:dd:3f:39:ac:27:0b:24:78:1e:d6:54
Aug 8 14:59:23 charon 16[IKE] <2431> received cert request for unknown ca with keyid 3e:b7:48:eb:57:13:1d:b9:02:47:3d:5c:8d:b4:38:1e:1b:69:f0:ef
Aug 8 14:59:23 charon 16[IKE] <2431> received cert request for unknown ca with keyid a8:e3:02:96:70:a6:8b:57:eb:ec:ef:cc:29:4e:91:74:9a:d4:92:38
Aug 8 14:59:23 charon 16[IKE] <2431> received cert request for unknown ca with keyid 62:af:b7:5c:2a:a7:0d:ad:0d:3d:8d:cf:fb:10:9e:65:c6:16:c3:0b
Aug 8 14:59:23 charon 16[IKE] <2431> received cert request for unknown ca with keyid c2:4e:45:22:d1:c3:2f:86:80:f7:4d:38:48:4b:74:e5:71 17:cf
17:cf
Aug 8 14:59:23 charon 16[IKE] <2431> received cert request for unknown ca with keyid 22:60:a7:83:31:ee:a4:c8:11:65:c3:b9:da:51:85:74:42:39:06:c5
Aug 8 14:59:23 charon 16[IKE] <2431> received cert request for unknown ca with keyid c4:9c:12:7e:4b:e9:e5:5e:f4:64:77:26:2c:b6:d9:c9:34:2b:7c:38
Aug 8 14:59:23 charon 16[IKE] <2431> received cert request for unknown ca with keyid a7:e9:c8:0c:8c:4b:56:d6:37:fa:9e:0d:6c:69:58:1d:32:4e:91:c0
Aug 8 14:59:23 charon 16[IKE] <2431> received cert request for unknown ca with keyid dd:00:92:e0:16:8e:ba:57:c2:67:d6:7d:0a:0a:4e:57:b6:cb:c6:c8
Aug 8 14:59:23 charon 16[IKE] <2431> received cert request for unknown ca with keyid 3d:9f:4e:e4:17:1d:e9:cc:8c:cb:6b:ee:84:03:c2 d7:bc:0b:9f
d7:bc:0b:9f
Aug 8 14:59:23 charon 16[IKE] <2431> received cert request for unknown ca with keyid 27:04:fa:e0:a6:32:eb:18:4b:51:e4:c6:39:e1:35:10:6b:b5:ff:61
Aug 8 14:59:23 charon 16[IKE] <2431> received cert request for unknown ca with keyid 3a:28:44:64:9f:20:e8:b1:05:bf:e9:d7:f5:66:33:61:51:ae:eb:51
Aug 8 14:59:23 charon 16[IKE] <2431> received cert request for unknown ca with keyid 9c:a9:8d:00:af:74:0d:dd:81:80:d2:13:45:a5:8b:8f:2e:94:38:d6
Aug 8 14:59:23 charon 16[IKE] <2431> received cert request for unknown ca with keyid ab:30:d3:af:4b:d8:f1:6b:58:69:ee:45:69:29:da:84:b8:73:94:88
Aug 8 14:59:23 charon 16[IKE] <2431> received cert request for unknown ca with keyid e0:8c:9b:db:25:49:b3:f1:7c:86:d6:b2:42:87:0b:d0:6b:a0:d9:e4
Aug 8 14:59:23 charon 16[IKE] <2431> received cert request for unknown ca with keyid c4:30:28:c5:d3:e3:08:0c:10:44:8b:2c:77:ba:24:53:97:60:bb:f9
Aug 8 14:59:23 charon 16[IKE] <2431> received cert request for unknown ca with keyid 69:c4:27:db:59:69:68:18:47:e2:52:17:0a:e0:e5:7f:ab:9d:ef:0f
Aug 8 14:59:23 charon 16[IKE] <2431> received cert request for unknown ca with keyid 28:a4:ba:ee:61:3e:0a:b8:15:83:95:65:4e:4f:cc:13:c1:70:e3:e3
Aug 8 14:59:23 charon 16[IKE] <2431> received cert request for unknown ca with keyid fd:da:14:c4:9f:30:de:21:bd:1e:42:39:fc 63:23:49:e0:f1:84
63:23:49:e0:f1:84
Aug 8 14:59:23 charon 16[IKE] <2431> received cert request for unknown ca with keyid b3:86:36:7d:bc:e5:f8:4e:e2:8c:15:37:81:b2:1d:f5:3d:2c:15:cd
Aug 8 14:59:23 charon 16[IKE] <2431> received cert request for unknown ca with keyid 7b:6d:b8:b0:b5:e5:85:0d:10:61:51:f0:3d:b0:f4:ff:40:8d:9e:a4
Aug 8 14:59:23 charon 16[IKE] <2431> received cert request for unknown ca with keyid 80:fc:a2:0c:56:d9:5b:d9:71:c1:35:ed:24:60:13:6f:78:46:a9:2a
Aug 8 14:59:23 charon 16[IKE] <2431> received cert request for unknown ca with keyid 4f:9c:7d:21:79:9c:ad:0e:d8:b9:0c:57:9f:1a:02:99:e7:90:f3:87
Aug 8 14:59:23 charon 16[IKE] <2431> received cert request for unknown ca with keyid 8d:f0:0a:ad:7c:3f:4c:f3:42:75:e2:ec:19:bd:f3:28:e2:24:69:22
Aug 8 14:59:23 charon 16[IKE] <2431> received 136 cert requests for an unknown ca
Aug 8 14:59:23 charon 16[CFG] <2431> looking for peer configs matching x.x.x.x[%any]...y.y.y.y[user@domain.com]
Aug 8 14:59:23 charon 16[CFG] <2431> candidate "bypasslan", match: 1/1/24 (me/other/ike)
Aug 8 14:59:23 charon 16[CFG] <2431> candidate "con-mobile", match: 1/1/1052 (me/other/ike)
Aug 8 14:59:23 charon 16[CFG] <2431> ignore candidate 'con-mobile' without matching IKE proposal
Aug 8 14:59:23 charon 16[CFG] <bypasslan|2431> selected peer config 'bypasslan'
Aug 8 14:59:23 charon 16[IKE] <bypasslan|2431> peer requested EAP, config unacceptable
Aug 8 14:59:23 charon 16[CFG] <bypasslan|2431> no alternative config found
Aug 8 14:59:23 charon 16[IKE] <bypasslan|2431> processing INTERNAL_IP4_ADDRESS attribute
Aug 8 14:59:23 charon 16[IKE] <bypasslan|2431> processing INTERNAL_IP6_ADDRESS attribute
Aug 8 14:59:23 charon 16[IKE] <bypasslan|2431> processing INTERNAL_IP4_DNS attribute
Aug 8 14:59:23 charon 16[IKE] <bypasslan|2431> processing INTERNAL_IP6_DNS attribute
Aug 8 14:59:23 charon 16[IKE] <bypasslan|2431> received ESP_TFC_PADDING_NOT_SUPPORTED, not using ESPv3 TFC padding
Aug 8 14:59:23 charon 16[IKE] <bypasslan|2431> peer supports MOBIKE
Aug 8 14:59:23 charon 16[ENC] <bypasslan|2431> generating IKE_AUTH response 1 [ N(AUTH_FAILED) ]
Aug 8 14:59:23 charon 16[NET] <bypasslan|2431> sending packet: from x.x.x.x[4500] to y.y.y.y[40450] (80 bytes)
Aug 8 14:59:23 charon 16[IKE] <bypasslan|2431> IKE_SA bypasslan[2431] state change: CONNECTING => DESTROYING -
@Alanesi said in StrongSwan user authentication failed on Android:
ignore candidate 'con-mobile' without matching IKE proposal
Check the phase-1 settings on both sides of the tunnel . If the Windows client is working perfectly , it is possible that an error occurred in the Android client settings.
P.S. I would recommend selecting the CA certificate manually in the client settings
-
I did the manual selection for the CA. I'll see what else I can change.
-
The user [user@domain.com] created ?
Aug 8 14:59:23 charon 16[CFG] <2431> looking for peer configs matching x.x.x.x[%any]...y.y.y.y[user@domain.com]
Aug 8 14:59:23 charon 16[CFG] <2431> ignore candidate 'con-mobile' without matching IKE proposal -
Yes, and its working on windows
-
@Alanesi
Then you need to check the settings of the Android client
There may be an error in the username/password field -
@Konstanti
Unfortunately still the same issue but with different log
This is from pfSense:Aug 8 17:01:25 charon 16[CFG] <2464> looking for IKEv2 configs for x.x.x.x...y.y.y.y
Aug 8 17:01:25 charon 16[CFG] <2464> candidate: %any...%any, prio 24
Aug 8 17:01:25 charon 16[CFG] <2464> candidate: x.x.x.x...%any, prio 1052
Aug 8 17:01:25 charon 16[IKE] <2464> no matching proposal found, trying alternative config
Aug 8 17:01:25 charon 16[CFG] <2464> selecting proposal:
Aug 8 17:01:25 charon 16[CFG] <2464> proposal matches
Aug 8 17:01:25 charon 16[CFG] <2464> received proposals: IKE:AES_CBC_128/AES_CBC_192/AES_CBC_256/3DES_CBC/HMAC_SHA2_256_128/HMAC_SHA2_384_192/HMAC_SHA2_512_256/HMAC_SHA1_96/AES_XCBC_96/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048, IKE:AES_GCM_16_128/AES_GCM_16_192/AES_GCM_16_256/CHACHA20_POLY1305/AES_GCM_12_128/AES_GCM_12_192/AES_GCM_12_256/AES_GCM_8_128/AES_GCM_8_192/AES_GCM_8_256/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048
Aug 8 17:01:25 charon 16[CFG] <2464> configured proposals: IKE:AES_CBC_128/AES_CBC_192/AES_CBC_256/CAMELLIA_CBC_128/CAMELLIA_CBC_192/CAMELLIA_CBC_256/3DES_CBC/HMAC_SHA2_256_128/HMAC_SHA2_384_192/HMAC_SHA2_512_256/HMAC_SHA1_96/AES_XCBC_96/AES_CMAC_96/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_AES128_CMAC/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048, IKE:AES_GCM_16_128/AES_GCM_16_192/AES_GCM_16_256/AES_GCM_12_128/AES_GCM_12_192/AES_GCM_12_256/AES_GCM_8_128/AES_GCM_8_192/AES_GCM_8_256/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_AES128_CMAC/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048
Aug 8 17:01:25 charon 16[CFG] <2464> selected proposal: IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/ECP_256
Aug 8 17:01:25 charon 16[CFG] <2464> received supported signature hash algorithms: sha256 sha384 sha512 identity
Aug 8 17:01:25 charon 16[IKE] <2464> remote host is behind NAT
Aug 8 17:01:25 charon 16[CFG] <2464> sending supported signature hash algorithms: sha256 sha384 sha512 identity
Aug 8 17:01:25 charon 16[IKE] <2464> sending cert request for "CN=internal-ca, C=SA, L=Riyadh, O=International"
Aug 8 17:01:25 charon 16[ENC] <2464> generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) CERTREQ N(FRAG_SUP) N(HASH_ALG) N(CHDLESS_SUP) N(MULT_AUTH) ]
Aug 8 17:01:25 charon 16[NET] <2464> sending packet: from x.x.x.x[500] to y.y.y.y[40538] (305 bytes)
Aug 8 17:01:25 charon 16[NET] <2464> received packet: from y.y.y.y[51903] to x.x.x.x[4500] (448 bytes)
Aug 8 17:01:25 charon 16[ENC] <2464> parsed IKE_AUTH request 1 [ IDi N(INIT_CONTACT) CPRQ(ADDR ADDR6 DNS DNS6) N(ESP_TFC_PAD_N) SA TSi TSr N(MOBIKE_SUP) N(NO_ADD_ADDR) N(MULT_AUTH) N(EAP_ONLY) N(MSG_ID_SYN_SUP) ]
Aug 8 17:01:25 charon 16[CFG] <2464> looking for peer configs matching x.x.x.x[%any]...y.y.y.y[user@domain.com]
Aug 8 17:01:25 charon 16[CFG] <2464> candidate "bypasslan", match: 1/1/24 (me/other/ike)
Aug 8 17:01:25 charon 16[CFG] <2464> candidate "con-mobile", match: 1/1/1052 (me/other/ike)
Aug 8 17:01:25 charon 16[CFG] <2464> ignore candidate 'con-mobile' without matching IKE proposal
Aug 8 17:01:25 charon 16[CFG] <bypasslan|2464> selected peer config 'bypasslan'
Aug 8 17:01:25 charon 16[IKE] <bypasslan|2464> peer requested EAP, config unacceptable
Aug 8 17:01:25 charon 16[CFG] <bypasslan|2464> no alternative config found
Aug 8 17:01:25 charon 16[IKE] <bypasslan|2464> processing INTERNAL_IP4_ADDRESS attribute
Aug 8 17:01:25 charon 16[IKE] <bypasslan|2464> processing INTERNAL_IP6_ADDRESS attribute
Aug 8 17:01:25 charon 16[IKE] <bypasslan|2464> processing INTERNAL_IP4_DNS attribute
Aug 8 17:01:25 charon 16[IKE] <bypasslan|2464> processing INTERNAL_IP6_DNS attribute
Aug 8 17:01:25 charon 16[IKE] <bypasslan|2464> received ESP_TFC_PADDING_NOT_SUPPORTED, not using ESPv3 TFC padding
Aug 8 17:01:25 charon 16[IKE] <bypasslan|2464> peer supports MOBIKE
Aug 8 17:01:25 charon 16[ENC] <bypasslan|2464> generating IKE_AUTH response 1 [ N(AUTH_FAILED) ]
Aug 8 17:01:25 charon 16[NET] <bypasslan|2464> sending packet: from x.x.x.x[4500] to y.y.y.y[51903] (80 bytes)
Aug 8 17:01:25 charon 16[IKE] <bypasslan|2464> IKE_SA bypasslan[2464] state change: CONNECTING => DESTROYING -
do you have set dns sec on your android?
-
No, but to wich server?
-
okay, did you set the user identity under advance settings on the strongswan app?
-
@Alitai
Yes its the same username. -
okay, on the android part there is not much more to todo.
Normally this is the easy part.Now, I think it's time for pictures from your pfsense and android. but don't forget to deleted the sensitive Infos.
-
@Alitai
This the P1 on pfSense.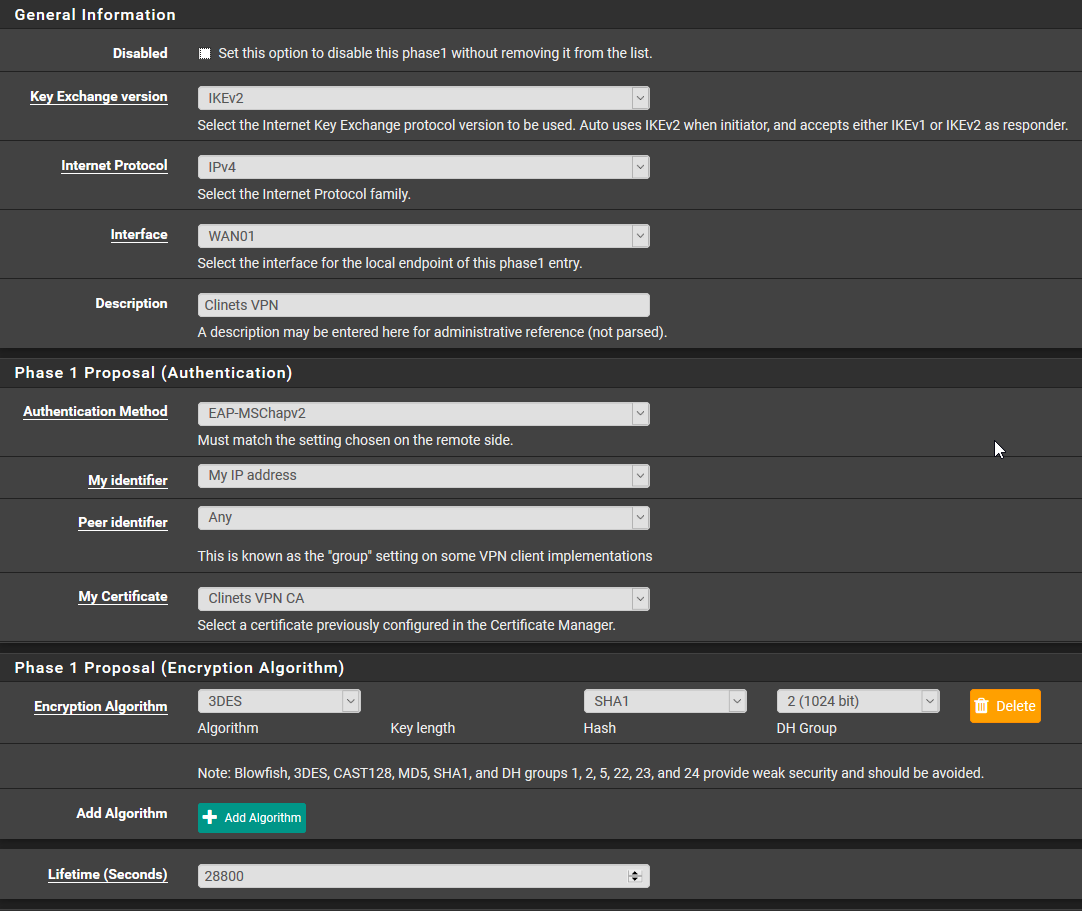
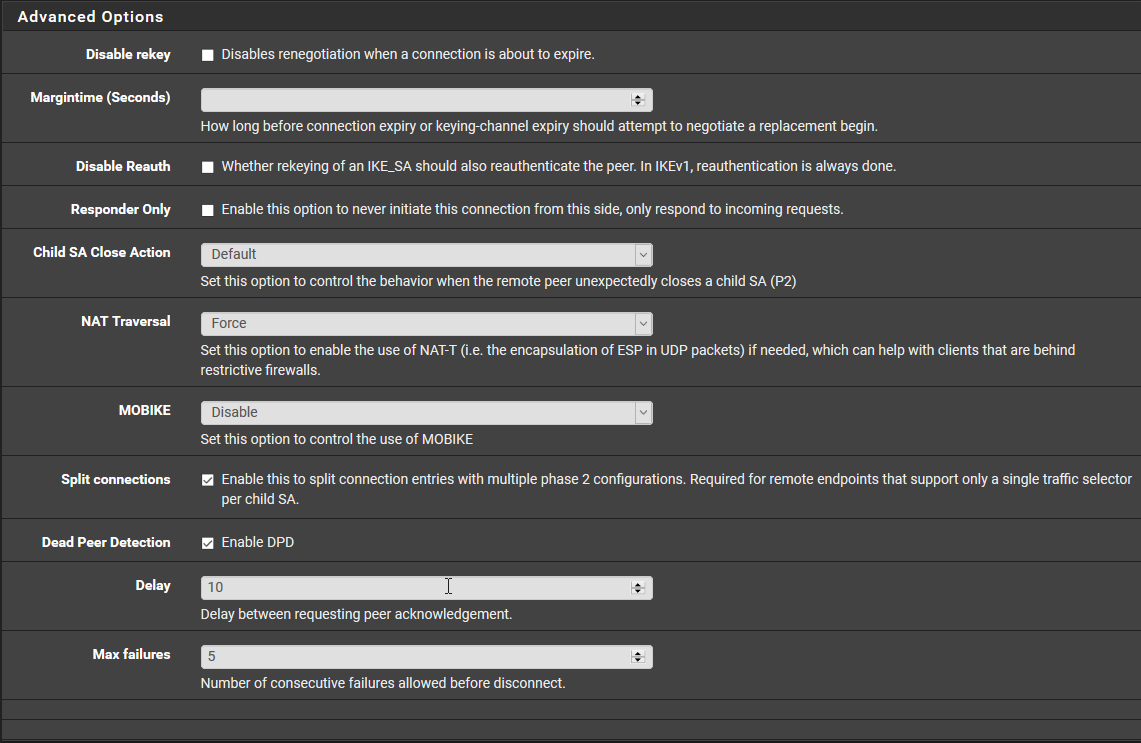
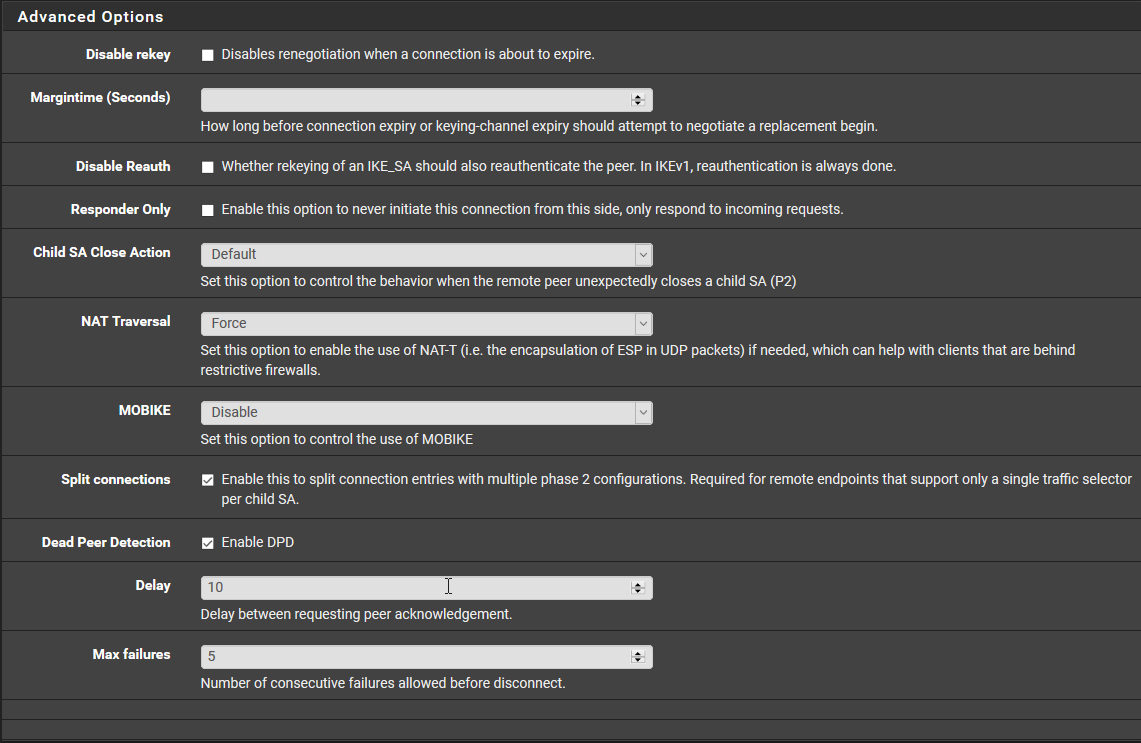
This Mobile Client
For the Pre-Shared Keys the secret type is EAP.
This P2
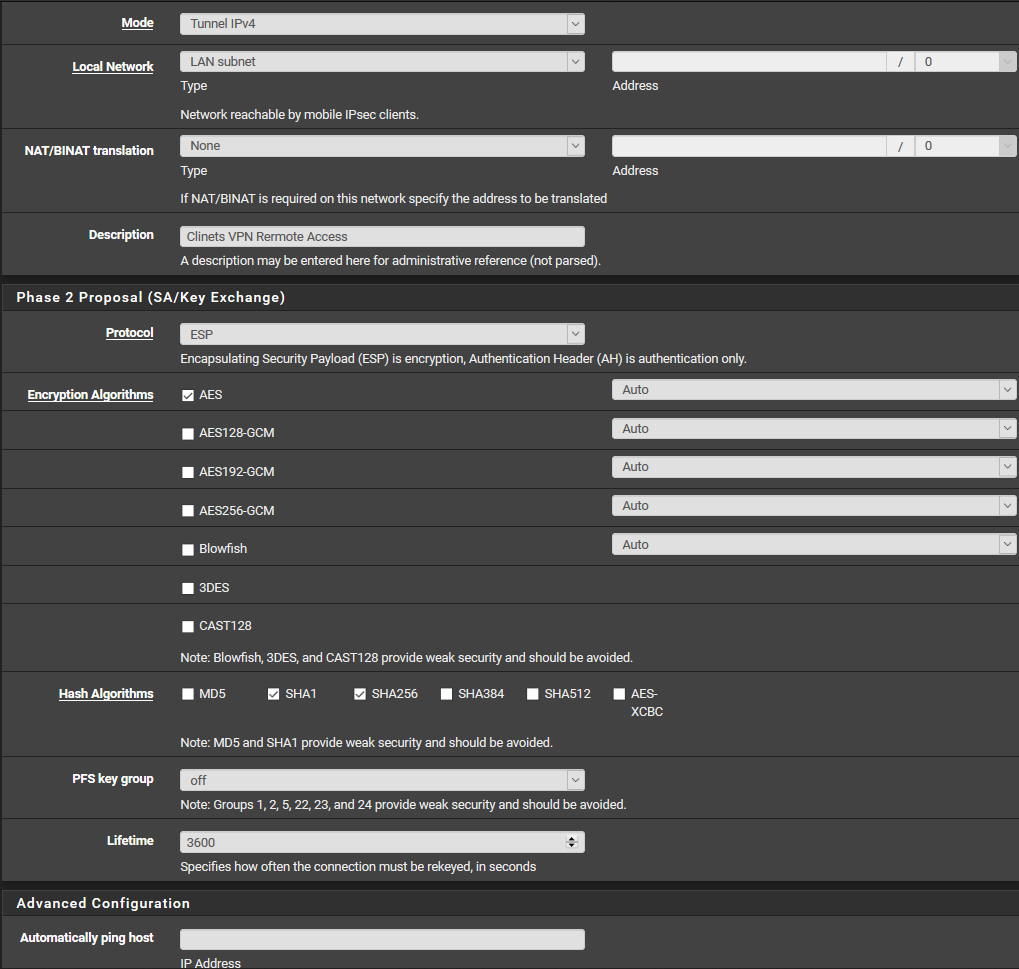
This on the Andriod
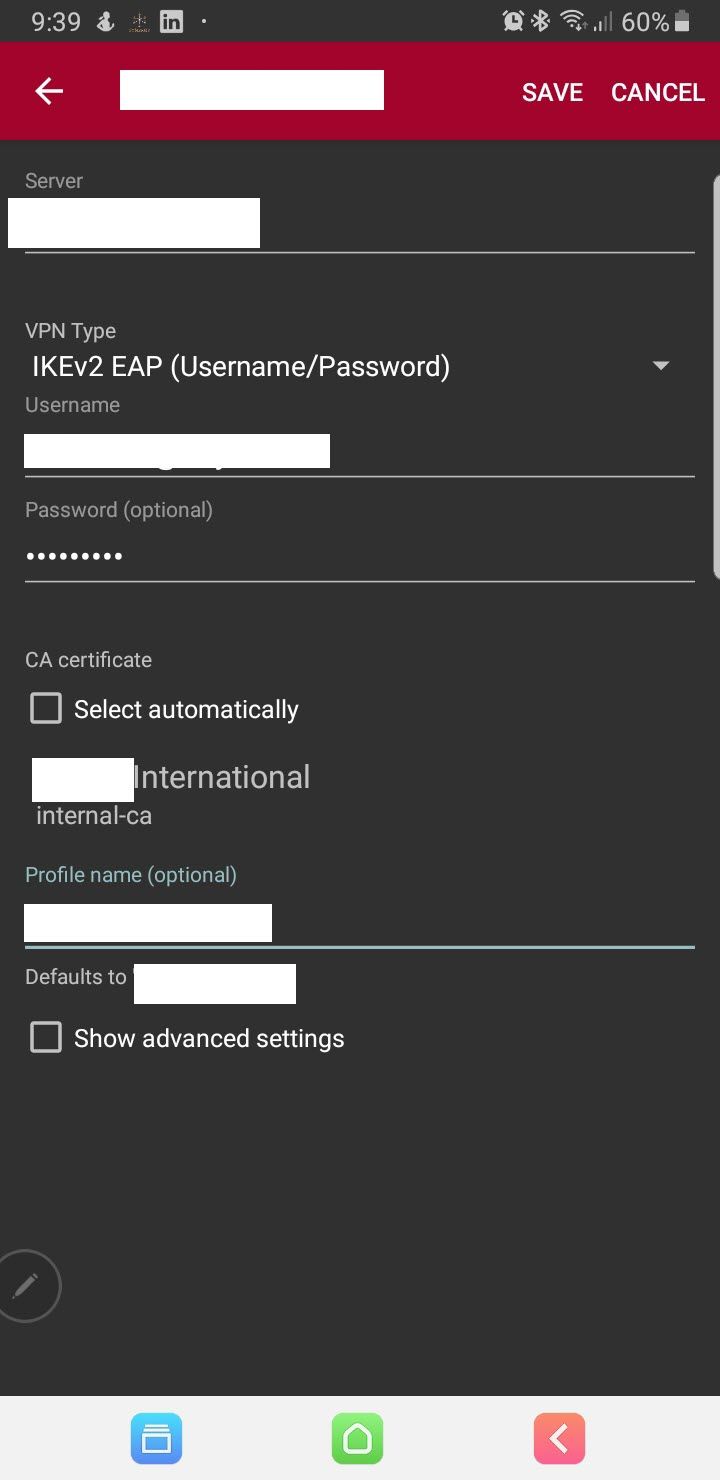
-
@Alanesi
Phase 1 - My identifier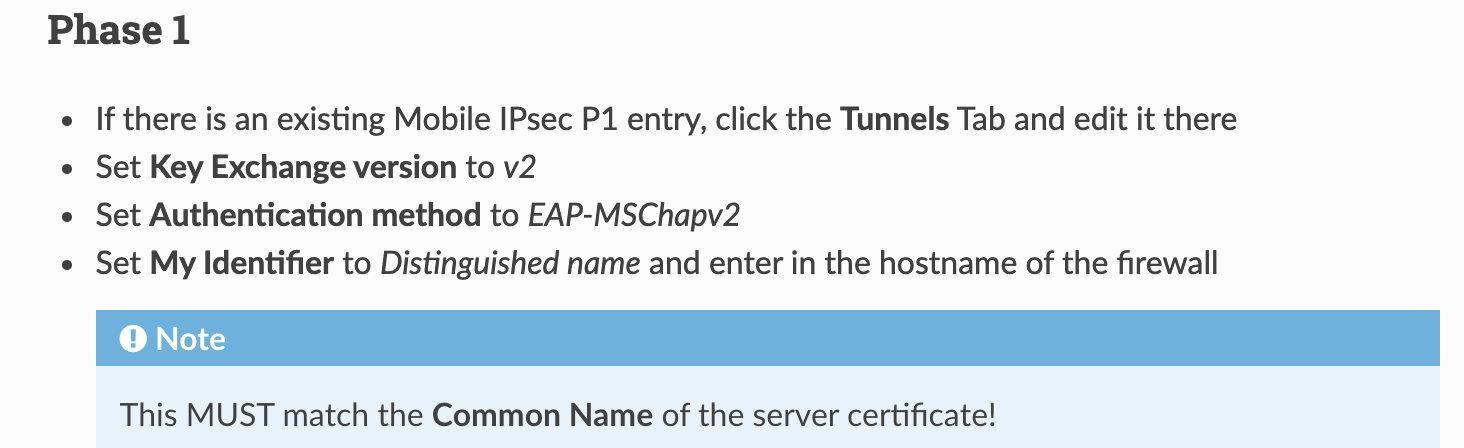
-
Thanks @Konstanti
I did that but it didnt make any diffreance still same error.
-
Phase 1:
Switch to:
AES / 256 bits / SHA256 / 14 (2048 bit)
and
Enable MOBIKEAndroid:
Don't forget the advanced settings (see above). -
