how do you setup users with restricted access
-
@comet424 said in how do you setup users with restricted access:
to say User Group (LandonsVMS) has access to this range
but when you look under the access they can have its just the pfense pages access control.. not like restricted accessThe pfSense user access :
determines what users - can access the web GUI of pfSense, and what parts.
It doesn't handle network access.Your choice to have two OpenVPN servers with dedicated firewall rules seems a good solution to me.
-
@Gertjan ah ok to groups is just editing the pfsense.. figured you only want an admin to edit it
so that also means users can log in to either openvpn then with there login pass
i come across another issue with the openvpn to make that 2nd openvpn i did the wizard where you create a new cert new ca i did the 192.168.0.0/24 etc i chose the assignment and gave that openvpnvm link... but when i goto to Export the clients are not shown.. its there for the main one i have for full access
so i get "If a client is missing from the list it is likely due to a CA mismatch between the OpenVPN server instance and the client certificate, the client certificate does not exist on this firewall, or a user certificate is not associated with a user when local database authentication is enabled."
now today first time running 2 openvpn servers and its been a year since i even touched my openvpn server since i set it and forget it.. and dont work with this everyday..
i did the wizard but what could gone wrong.. where would i look what screen shots would you need
-
gonna try... delete cas certs openvpn server firewall settings it creates and do a reboot so its clean to see if it fixe's it
when in doubt do a reboot lol
-
well that didnt work
deleted all saved rebooted.
then ran wizard still says that issue on exportupdate..
figured it out had to choose user and the bottom the certs linked and had to link exisit cert... now i can test it at home depot lolhopefully it all works (:
-
@
@Gertjan
ok so i cant seem to connect,,, i was able to connect to my orginal openvpnthe 2nd one with my other account its stuck on connecting.. i was able to download the opvn file but when connecting its jus stuck connecting... is there something to check.. i checked that it was basiclly exactly same as the admin one i have setup and i did run the wizard.. but its stuck at connecting.... even if i make up a user using the client software it stays connecting.. if i make up a user on my orginal open vpn it tells me invalid
so its not getting to authenticating or what not
-
@Gertjan
so i got it to log in using the landon account i had to delete the user and re add it then create cert button instead of add cert and then add exisiting cert..but there is issue.. i was getting full access to the network.. so when i got home.. LandonsVM Open VPN didnt get really access.. but it went to the OPENVPN Firewall rules.. it didnt go to the correct firewall rule.. where do i look
also everytime i delete the openvpn server, certs,ca, and do the wizard again.. it always saves the rule under OPENVPN not the LandonsVMOpenVPN..
but interface is set for it so its going to the wrong firewall rule
what do i look for that its going to the wrong rules?interfaces
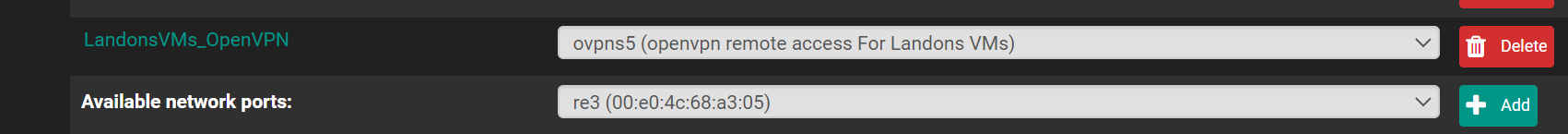
rules
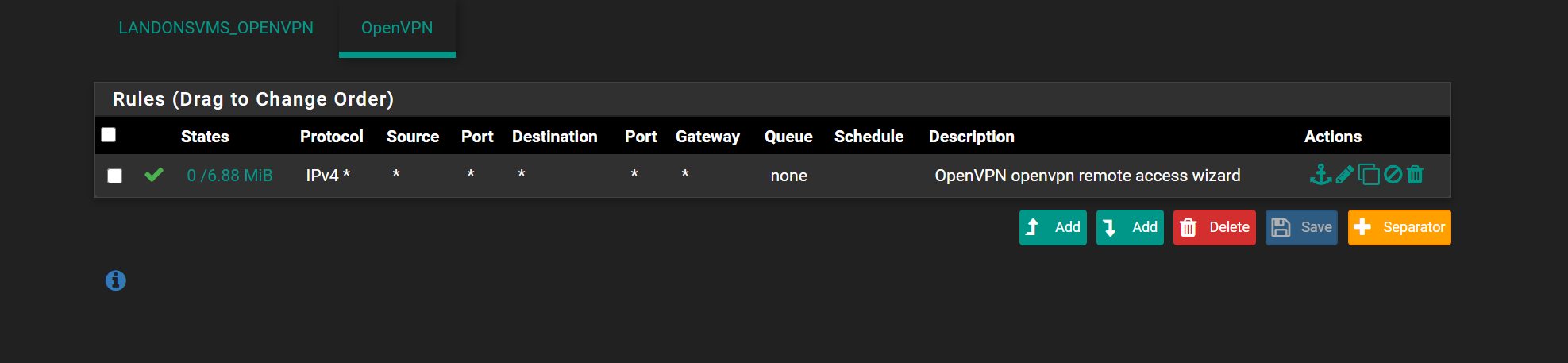
-
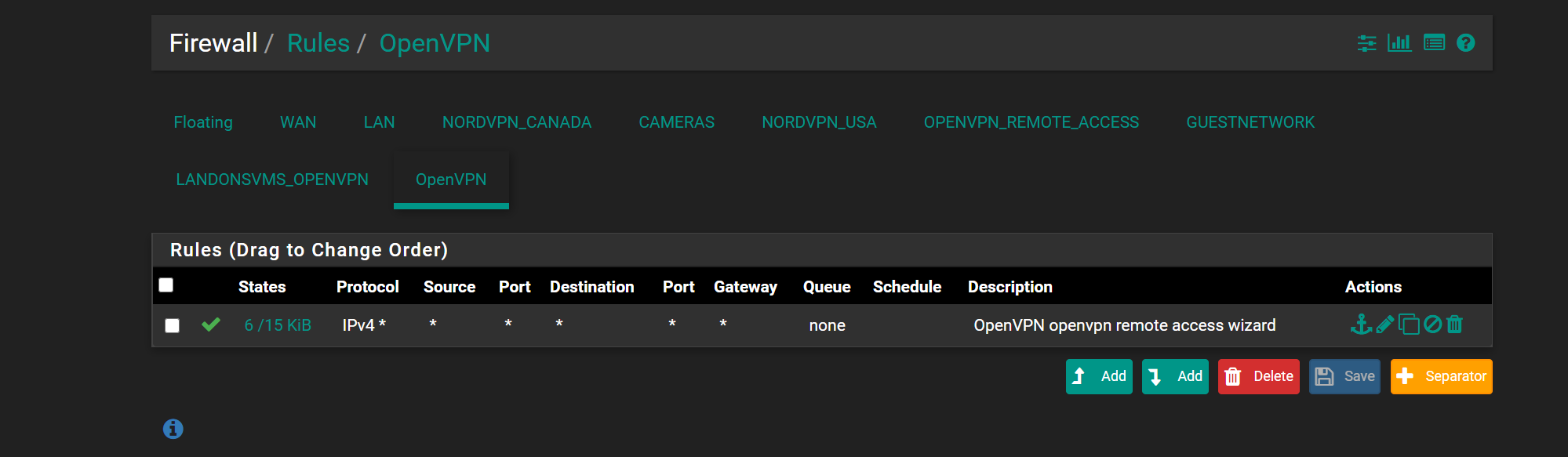
here is the openvpn server snap shots. maybe something i got configured wrong as its going to the wrong firewall rule
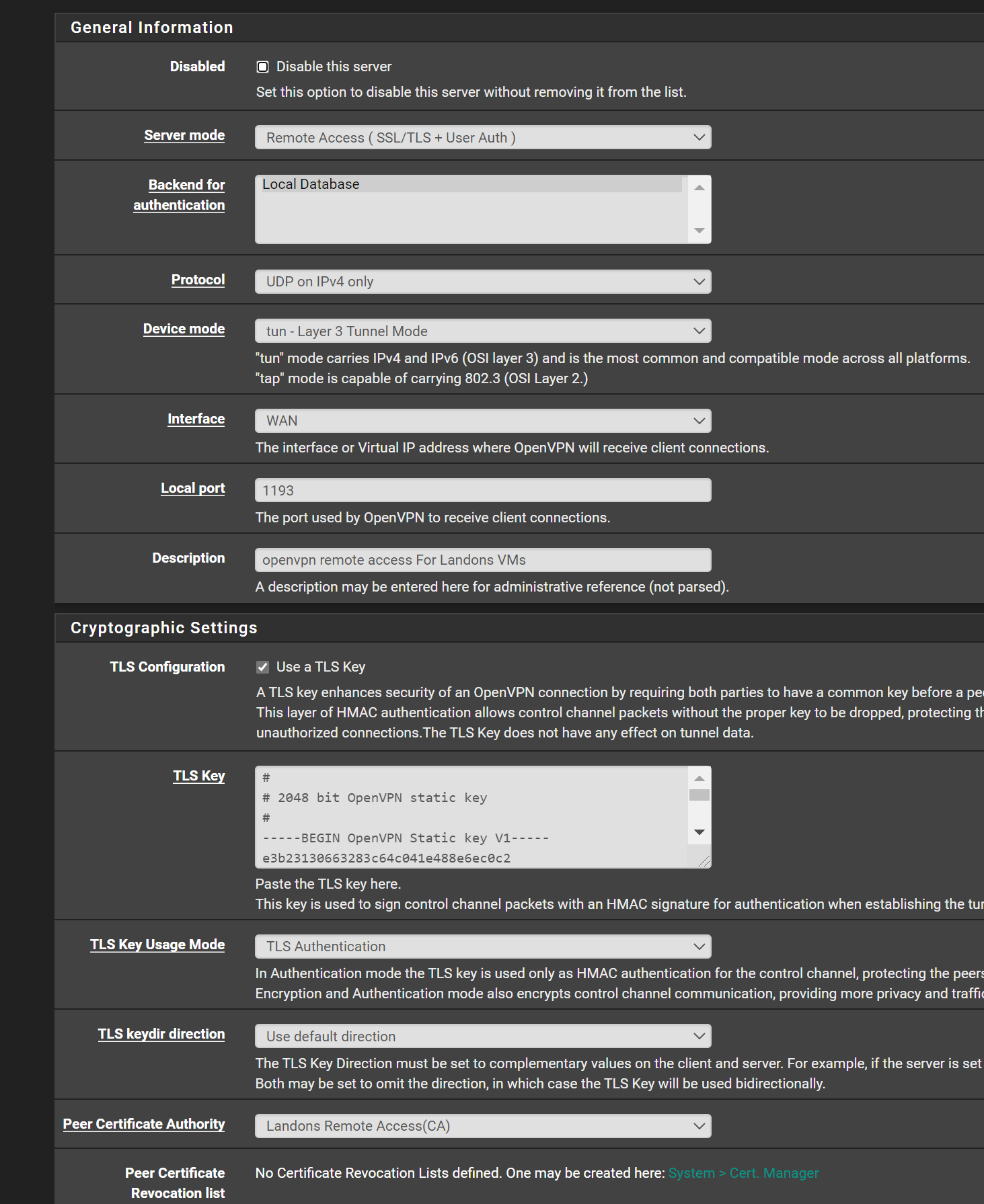
![server2.PNG] (/assets/uploads/files/1598668037411-server2.png)
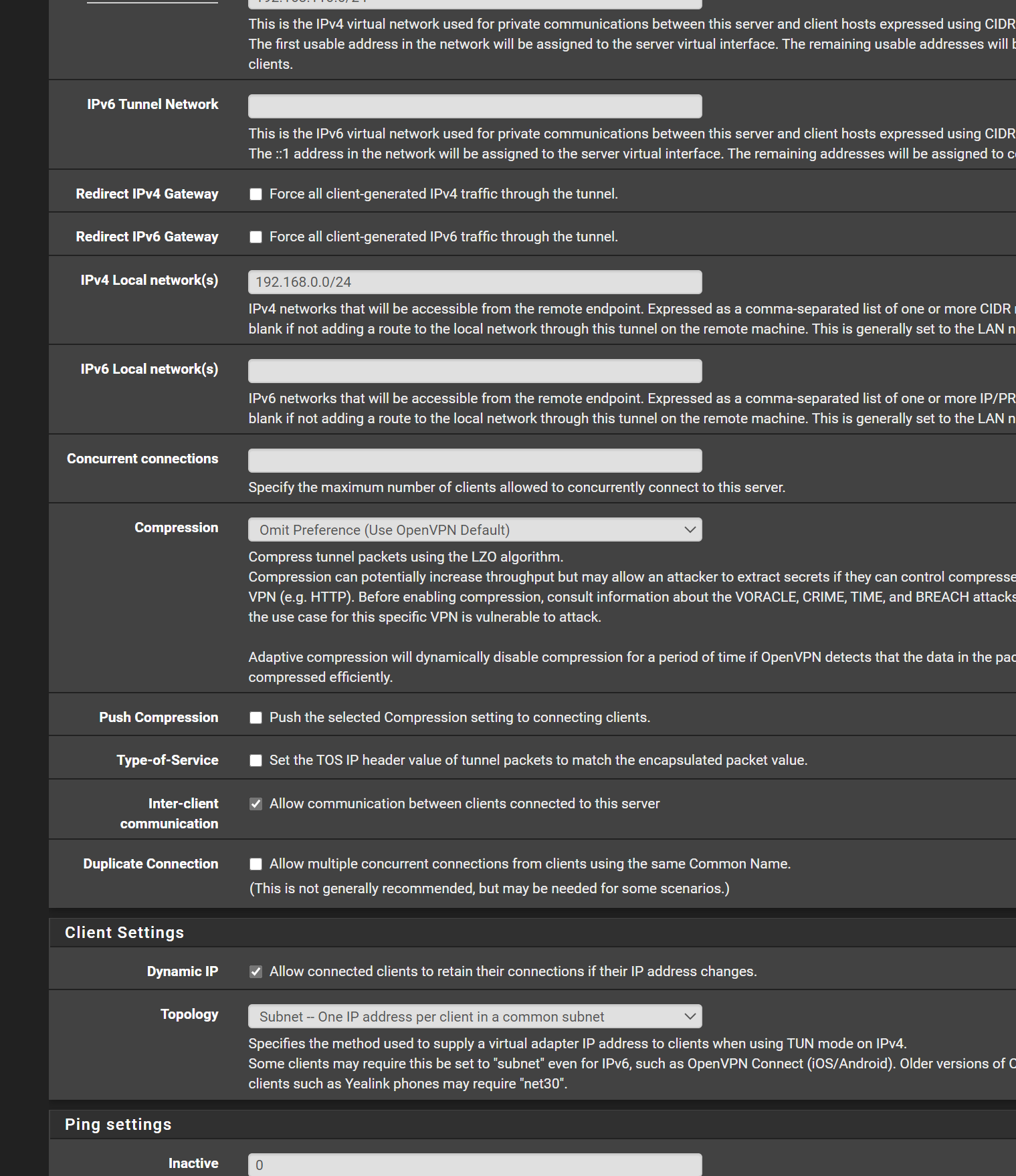
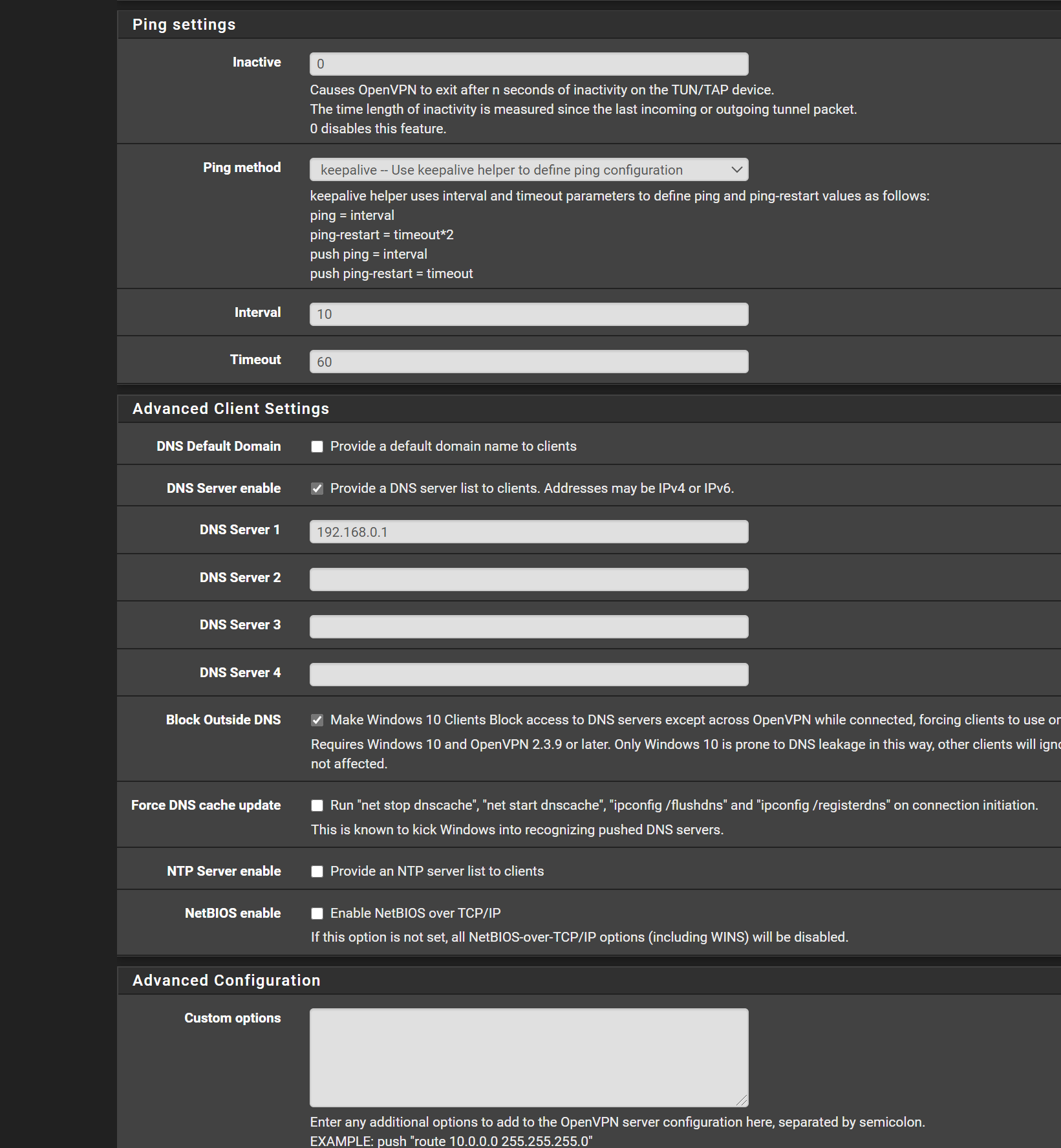
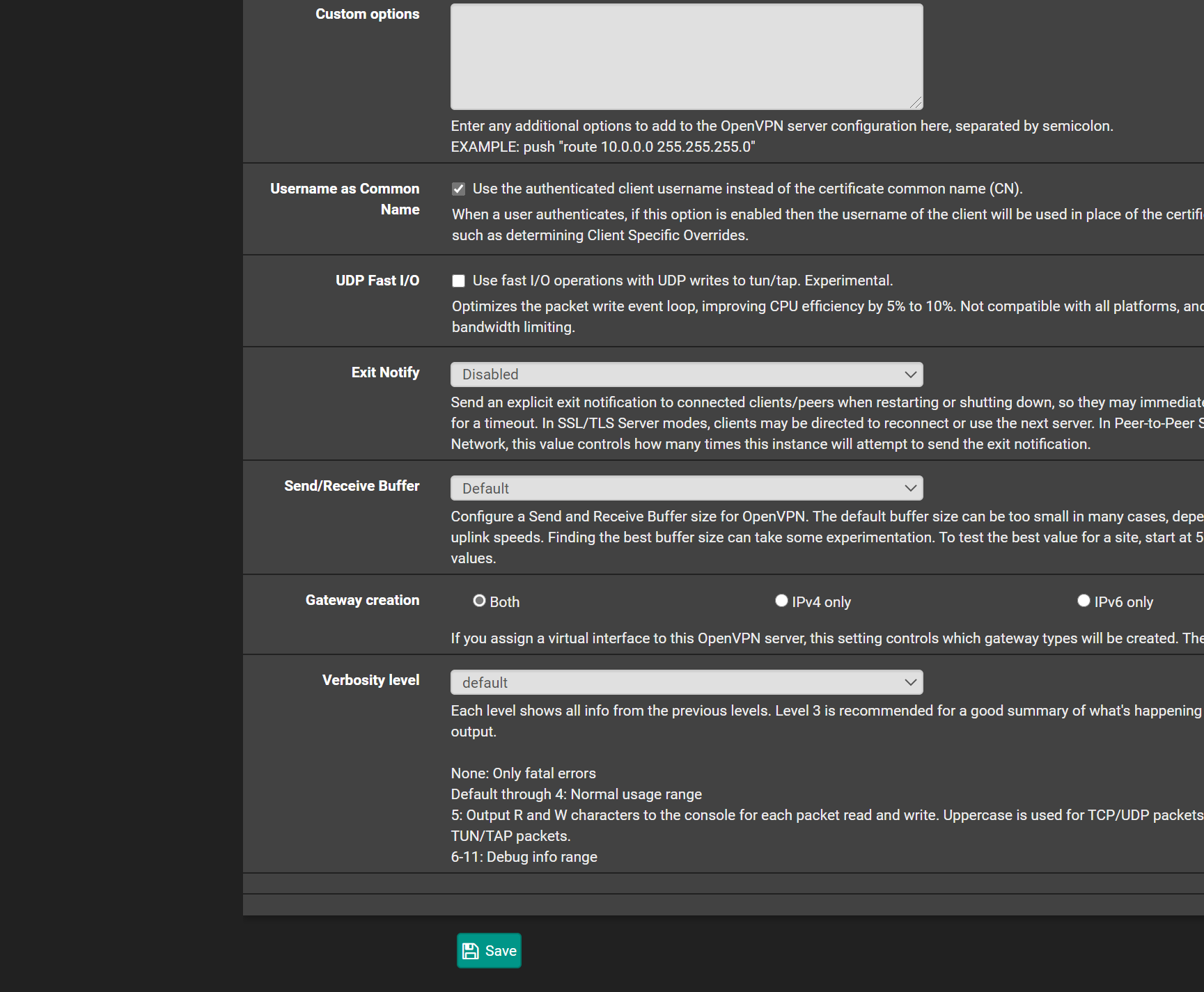
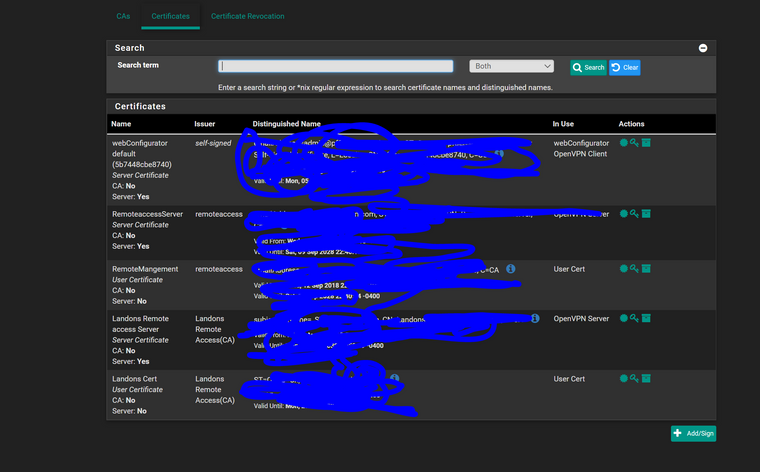
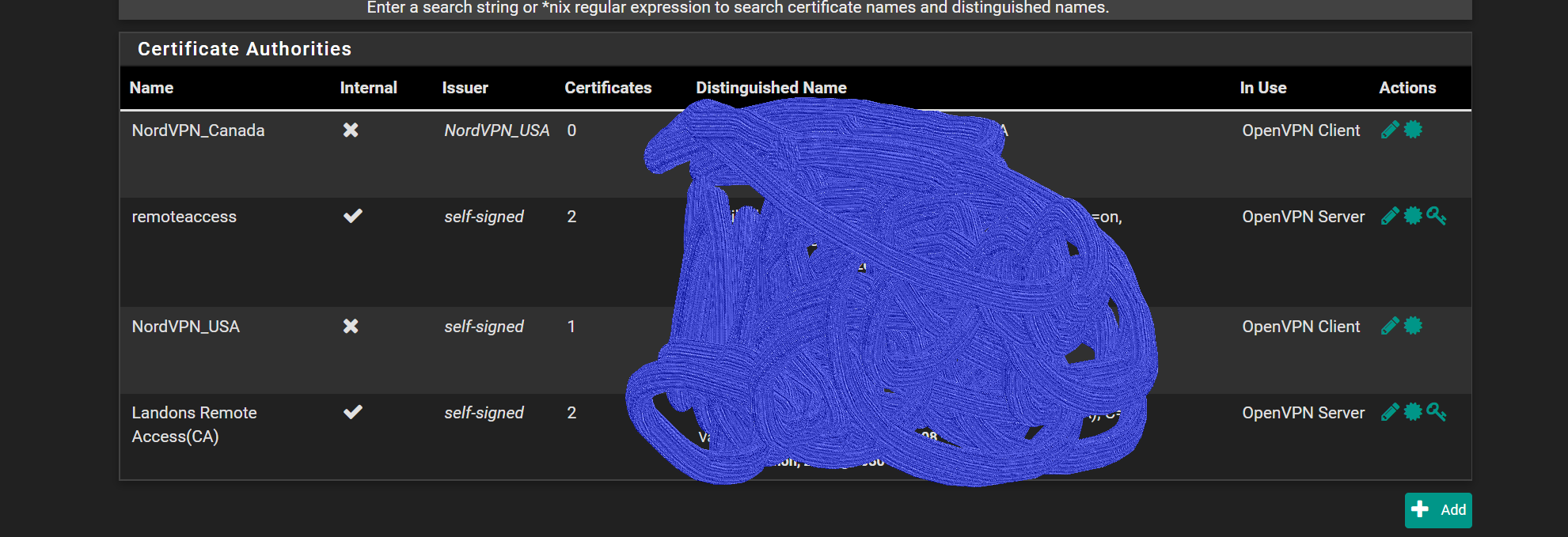
-
so i think i kinda know the issue and not sure how to fix..
the OpenVPN servers all goto OpenVPN fire wall rules
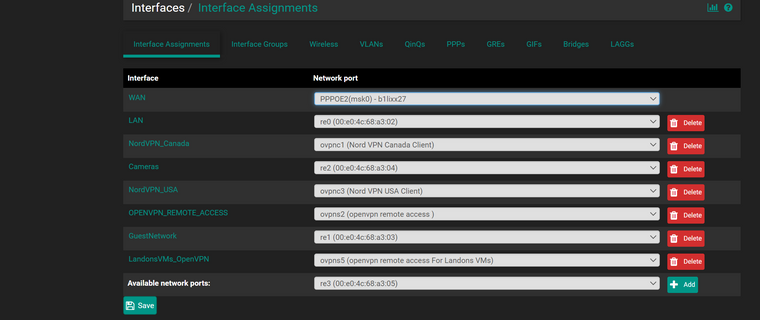
no matter if the Interface (Landons OpenVpn) :opvn5 remote access etc
and interfacce (openvpnremote access) :opvn remote access for admineven though it populates it all goes to the OpenVPN firewall rule and not the specific interface rule
so i dont know how to modify it to redirect to the proper firewall interface rule
-
since i cant delete the OpenVPN firewall tab
is there a way to tell it when openvpn server set to interface A to run the rules under A
and if someone loges into server set to interface B to run the rules under B
i cant seem to get
LandonsVMOpenVPN to get the rules keeps going to OpenVPN
is there a way to delete OpenVPN firewall rule and that probably force the 2 Interfaces to go to there servers properly -
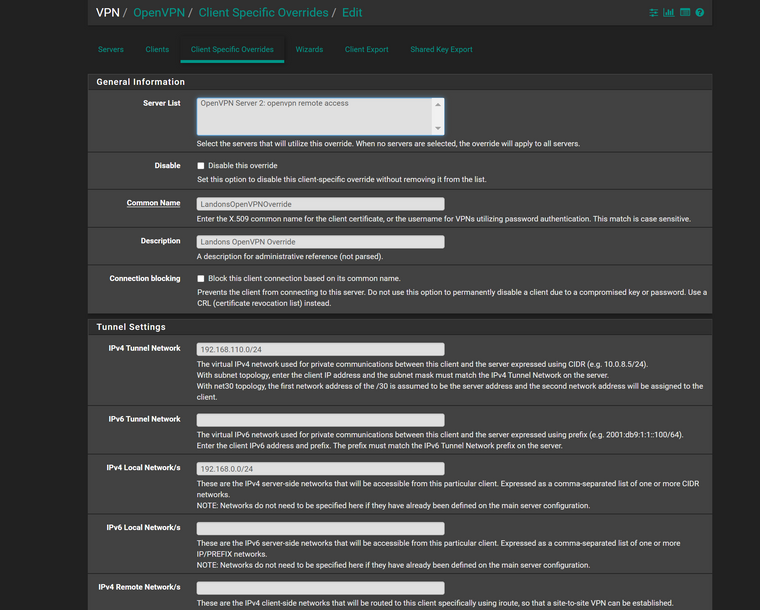
@comet424 You most likely have to push a static IP address to LANDON, and then make a firewall rule(s) on your openvpn tab for that specific IP address to access stuff - either PASS or BLOCK.
Pushing an IP address can be found here:
VPN -> OpenVPN -> Client Specific Overrides -> Landon's User Name
And then, all the way at the bottom of this windw, in the box called Client Settings -> Advanced, add this text:
"ifconfig-push X.X.X.X 255.255.255.0;" without the quotes. For the X parts, assign him a specific IP address, like 1 subnet different than your internal LAN subnet addresses. So, how I do mine at work, LAN = 10.0.1.0/24 and OVPN clients get 10.0.5.X addresses, set in the field above. Everything works perfect like this.
Hope that helps!
Jeff
-
@akuma1x
didnt work still LandonOpenVPN and RemoteAccessVPN (admin) still goes to OpenVPN firewall.. they arent going to the specfic Firewall settings.. why is it defaulting OpenVPN.. id like to delete it.. then it has no choice to goto the proper Interfaces..
and what does the iconfig and and the pushing do? and what if you had 100 users in business would u have to do 100 client specific overrides?maybe i configuring something wrong.. and i chose 192.168.110.0 since thats what i set for in the openvpn server file page.. i getting frustrated why isnt it going to the specific firewall rule and damn OpenVPN i cant even rename it or add it to interfaces.. its not there
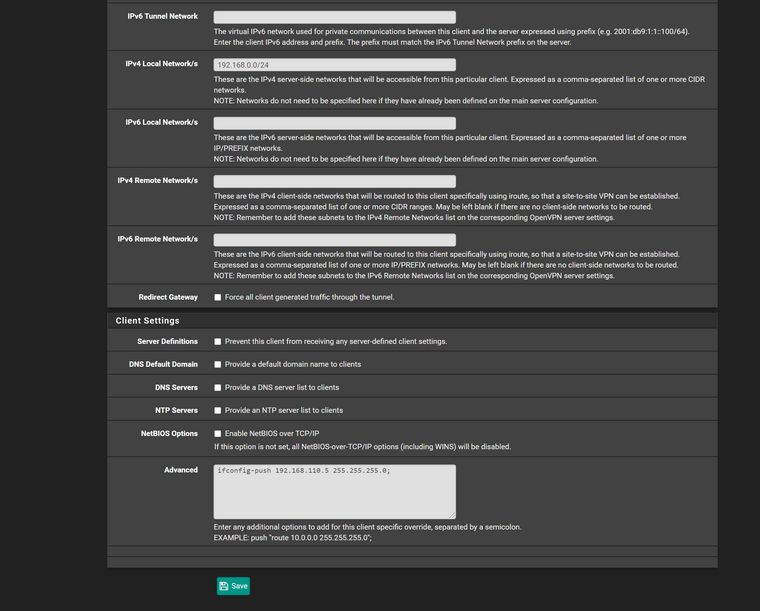
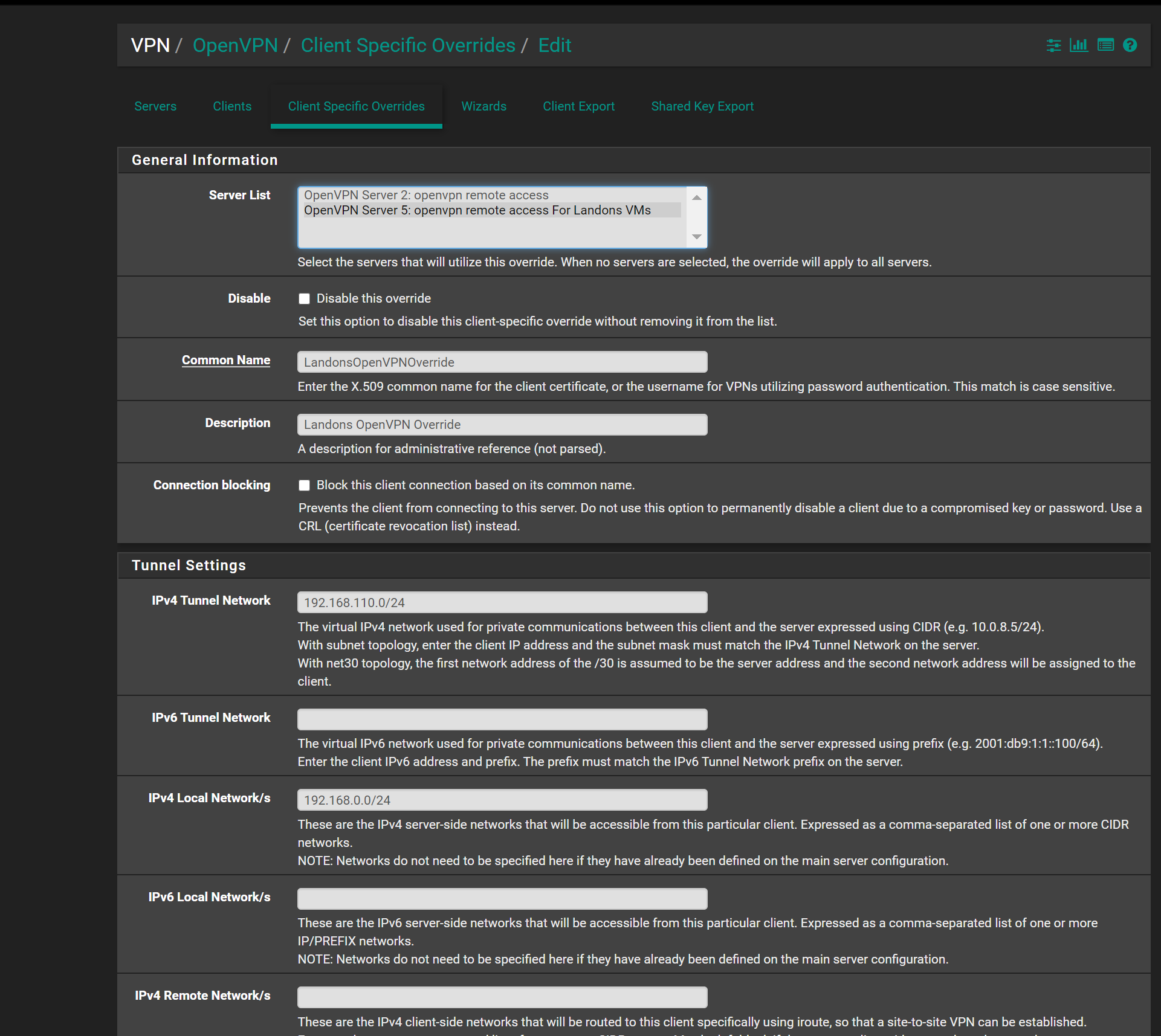
if i keep deleting the server in openvpn and re create it and set it to the CA cert and server cert.. it keeps adding to OPENVPN not to darn Specific Landon Interface
ive had enough of thos tonight.. 1:15am and i cant get it to go where its supposed to go.. its linked to interface but both VPN Servers wont go to there specific firewall tab ugh
OPENVPN tab isnt even an interface so dont know why its even there as a firewall tabhad enough of it tonight
-
so im getting confused
i googled. and was reading the netgate docs... it says openvpn can be directed to specific interfaces but really doesnt tell you how to do it..
from what i read all openvpn server connections all go to OpenVpn firewall tab and then needs to be redirectedto sum it up i want
openvpn server 1(admin) ===>OpenVPN firewall tab(redirected)==>AdminOpenvpn Firewall Tab
openvpn server 2(landons) ===>OpenVPN Firewall tab(redirected) ==>LandonOpenVpn Firewall Tabso i read the custom routes or the push routes etc
but in the negate docs i read " In such cases the OpenVPN tab firewall rules still apply, but there is a separate tab specific to the assigned VPN instance that controls traffic only for that one VPN" but i havent found how to do that
-
@comet424 Ok STOP, let's start over from the beginning...
On my pfsense box, I have the OpenVPN server setup and running. In these settings, I have setup all of the users that can access the server with user names and passswords. This is done under System -> User Manager -> Users. Create a new user for Landon, and give the user a good password.
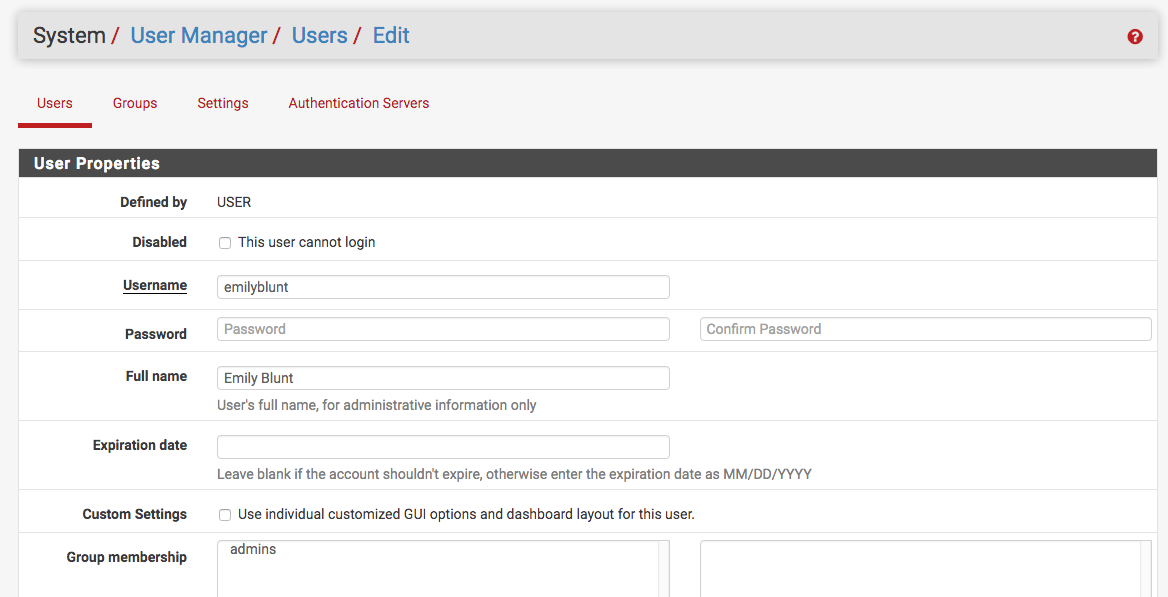
Now, because you've already got an OpenVPN server instance created and it's known to work, DELETE the second (or third, or more) one you created specifically for Landon. Make sure all the extra WAN rules you've got for port 1193 are also deleted. And, speaking of WAN rules, I don't see the specific "port 1194" created from the OpenVPN wizard. What happened to that one? There's also a 1196 one in there, too.
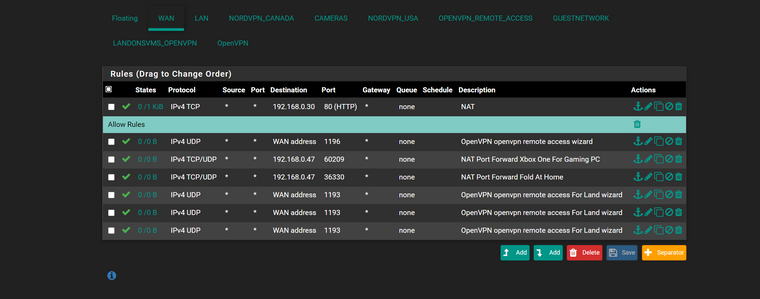
You can both technically use the same VPN server connection. On your VPN server, you still want to give Landon a specific IP address, this is how you filter how and where he goes on your internal networks. Please be aware, when you start an OpenVPN server, the system automatically creates a firewall tab called "OpenVPN" in the list. You can add all of your traffic rules right here. You don't have to create extra OpenVPN firewall tabs. Or, for that matter, even activate them as interfaces in pfsense.
The single tab in the screenshot below is what was created from the initial setup wizard, and as you can see, tons of traffic has already passed thru the allow any rule there. That's traffic from about 12 other users, not shown, that have been working from home for 5 months.
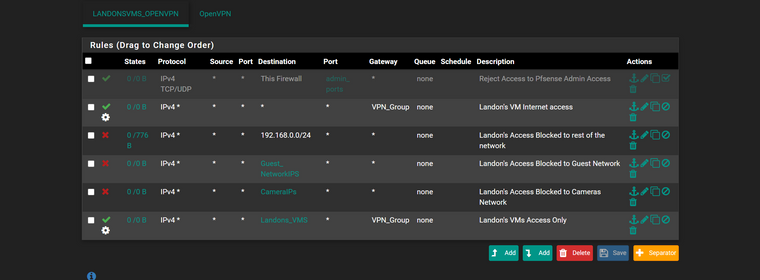
So, I just added a new user to my pfsense system, called her "emily". Setup a user name and password for her, like I detailed above. There's a pass any and all rule on my OpenVPN firewall tab, and I put a block rule for emily up at the top to keep her from getting to a server on the LAN network.
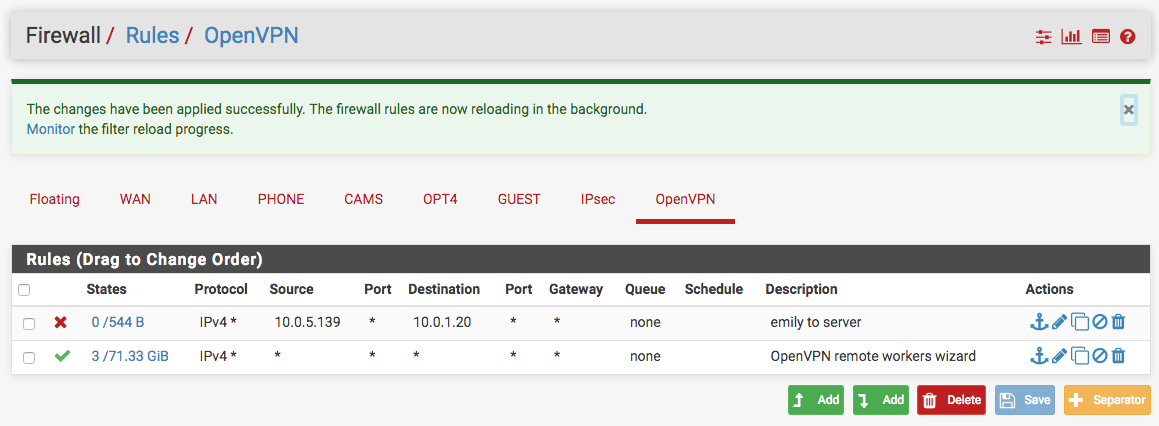
Just tested, and it works. This user can login to the OpenVPN server, gets a static address from the system (10.0.5.139), and is BLOCKED from accessing the server at 10.0.1.20 with the single rule I created.
So, in review. 1 OpenVPN server running, I've got many users setup to remote in to use it, but only 1 is blocked from this particular server on LAN. You should be able to do the same, with your user account, and Landon's user account.
Jeff
-
@akuma1x
so the ports i was using is
1197 site to site openvpn
1196 admin openvpn
1193 was landon openvpn server
1194 was landon openvpn server both i was testing at same time to try to get away from OpenVPN tab and into the corresponding interfacesorry suffering migrain today so i havent worked on it.. rain gives it to me among other issues.. i missed something
ya i like the idea of 1 server make its easier thats why i was hoping grouping worked or source could be user name
as i want admin to have full access to the network.. and landon only right now would have access only to 2 IP address on the network when logged inand with me being a visual learner, learning disability i gotta
but i missed something where do you link emily user account to 10.0.5.139 do you enter that in her user account credentials? so that be like 192.168.5.139 for mine a random ip address.. so i kinda got lost there how do i get the static ip for each user..
so static ip for admin static ip for landon or any other user..kind sucks that you make the cert/ca and you can link it in an interface but the vpn tab doesnt go to the interface but the openvpn
so if you could go back a step fo me be great.. on the OpenVPN server gets a statick address from the system (10.0.5.139) that being linked to emily could you explain that better for me like a dummy book
and the part for the custom routes where i added in the other server for landon i had.. the route 192.29.x.x.x 255.x.x.x what did that actually do
and too bad firewall tab for Source didnt have option of "user accounts" so no need for IP just uses a group of user accounts in an alias..
but thats just me.. but ya if you could explain better abovefor me to acheve the ip address.. no rush as i no hurry
i appreciate the help you doing so far. and working with me... i know i no professional so thank you so far for all the help from thje other guys input too
-
@akuma1x
so re reading your posts and reading
https://docs.netgate.com/pfsense/en/latest/vpn/openvpn/configuring-a-single-multi-purpose-openvpn-instance.html#:~:text=OpenVPN%20Client%20specific%20overrides,second%20one%20will%20be%2010.33.and then re reading your posts i think i kinda set it up properly couple spots i think i done it wrong where docs say dont use a ip4 local IP address so dont use my 192.168.0.x
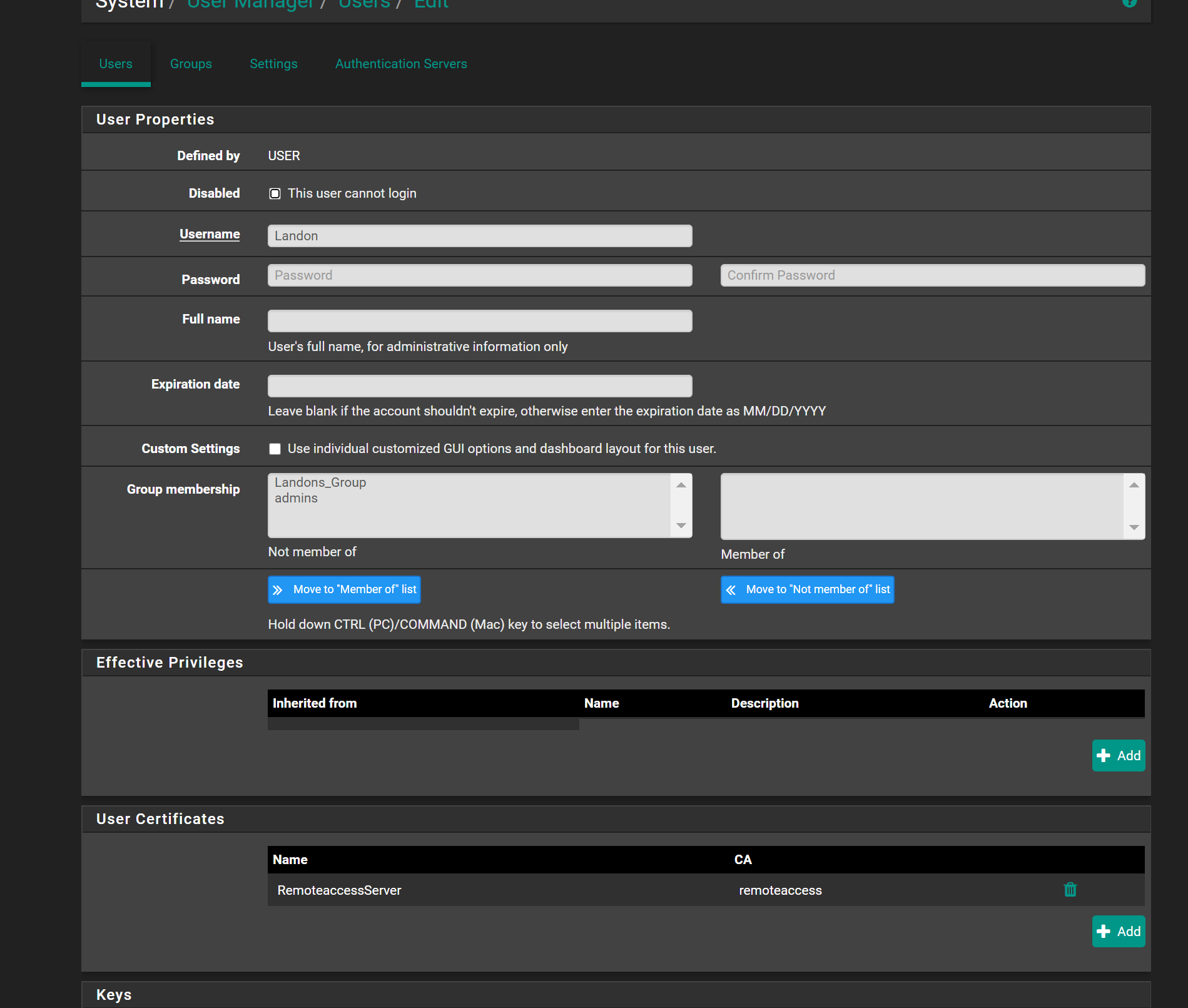
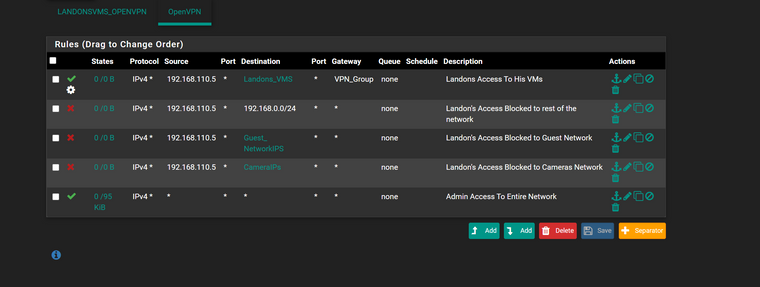
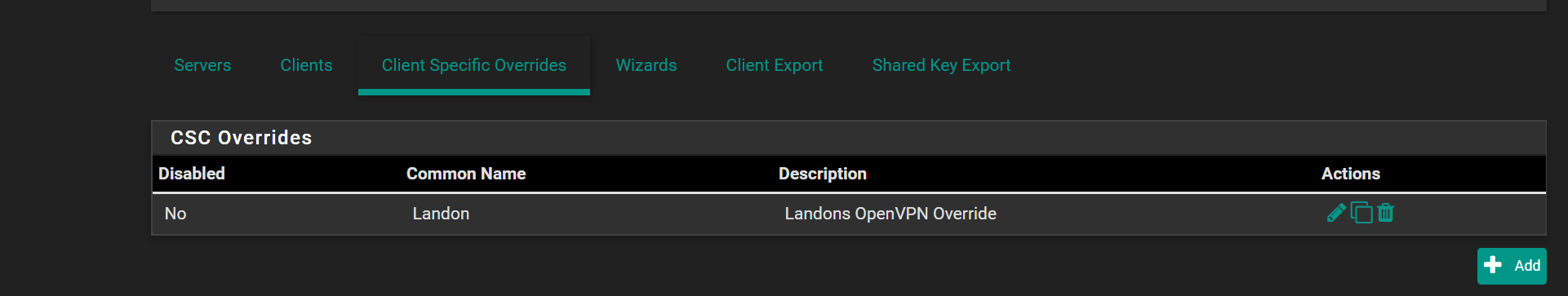
and i confused.. how does my client override link directly to the useraccount landon? im sure i have mistakes but i think its better.. and i hope the images posted in the correct order.. i havent tested it as im not sure how the client override links directly to a user account as i didnt say Useraccount(Landon) = clientoverideaccount anywhere in settings.. maybe you can explain how that works as i got confused reading the docs too
openvpn rules
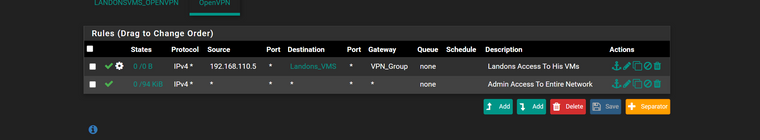
wan rules
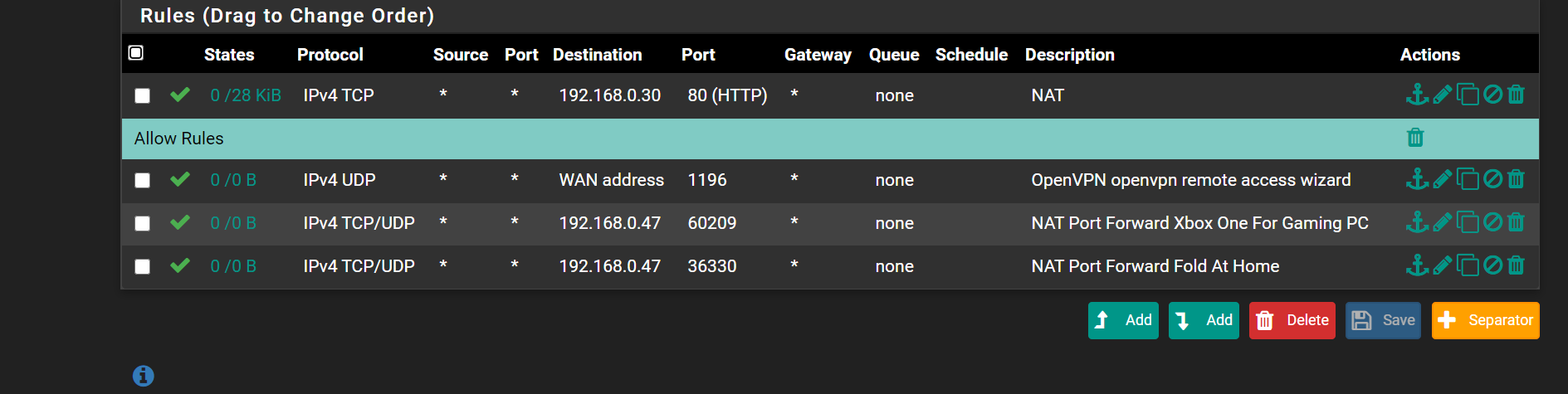
client override (landon)
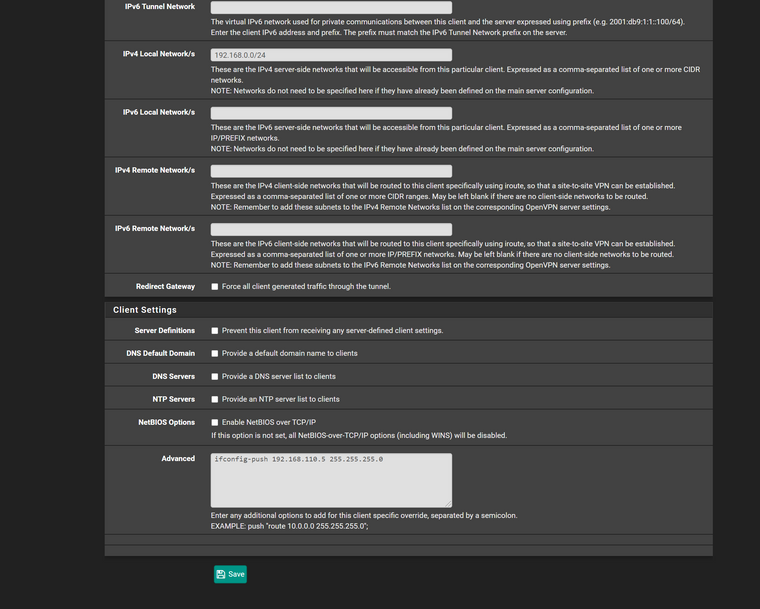
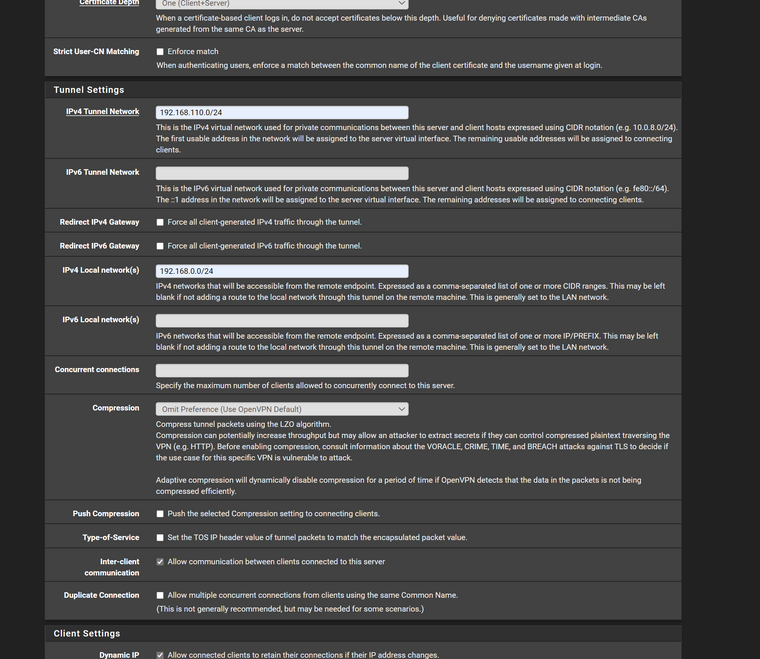
landon account
forgot i needed to added the block rules here is updated
update..
i rechanged the common name for client over write to "Landon" as i guess thats how it links it from reading the description
-
@akuma1x
i ended up wanting to start fresh.. so i deleted the openvpn certs server, ca,cert, usernames and did a clean setup
i still use the openvpn tab for the 192.168.110.5 for user Landon
but i having issue when he logs in it isnt workfor cert override advanced i have it as
ifconfig-push 192.168.110.5 255.255.255.0;but i thnk i did it wrong?
but i did a clean setup of it all and changed firewall port cleaned up my clutter so not soo messy
i did notice when i deleted the nat rules for 192.168.110.x it diddnt get created when i ran the openvpn wizard.. do i need them -
@Gertjan @akuma1x
so i got it to work partially..
i did a clean setup of the openvpn and cleaned up some rules etc
i can login with user admin or Landon
admin has full access it seemslandon does get his ip 192.168.110.5
he cant access the network ip address's i gave but can use internet
i added the rule thie firewall.. and that works so he can access the Firewall but not the ips in the landons_vms groupi did get a webpage saying tunnel error
so where do i look that i messed it up.. and thank you guys for all the help so far i had to re read things 10 times to really understand it.. too bad there isnt college course in pfsense.. learn as i go
i did 2 ips that point to 192.168.0.5 one static number and 1 inside the landons_vms to see if it was an issue.. but nope.. cant access but the this firewall works ok
it seems that it might be working just everything is being blocked
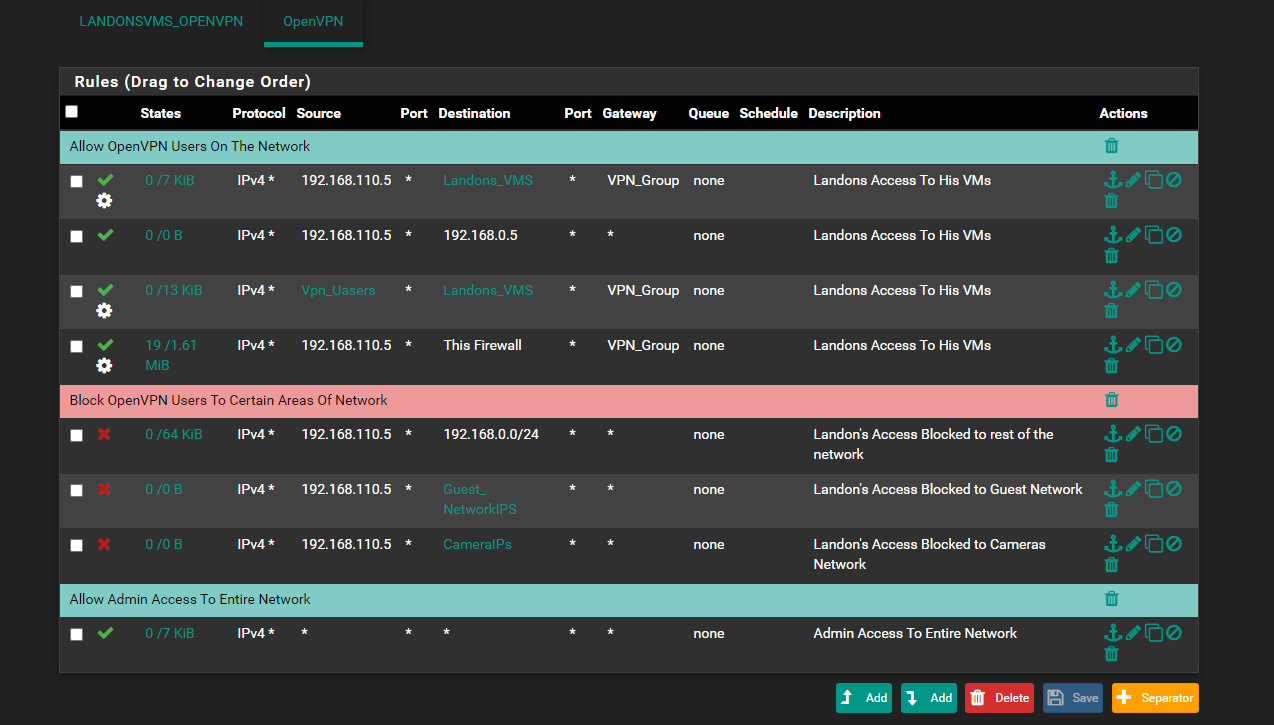
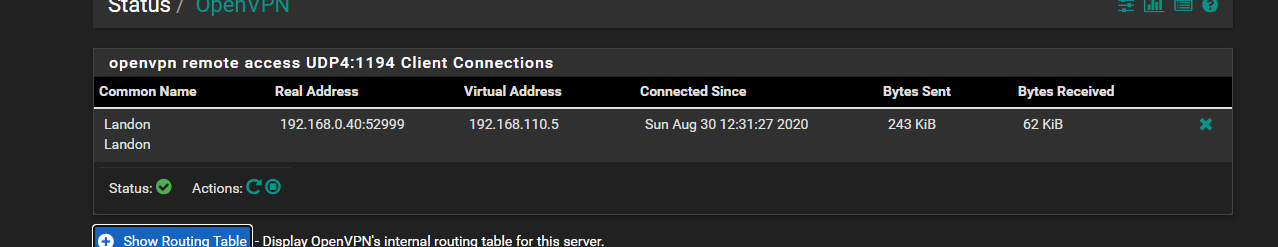
-
@comet424 said in how do you setup users with restricted access:
too bad there isnt college course in pfsense
Do not under estimate the pfSense manual for quick reference.
Also : Youtube => Netgate has nearly all the setups covered.Pilots in planes use GUI to control the plane. SpaceX implemented the same thing in the Dragon capsule. Cars have been invaded a long time ago.
Still, you have to have your license to drive your car, plane ..... dono what's needed for a round trip to IIS in the Dragon.
Using world's biggest data network needs some studying too.pfSense does nothing what hasn't been done already elsewhere. It's just a router firewall with a nice collection of networks tools . This doesn't mean you have to master them all.
Consider this : you should be able to set up a OpenVPN server on any (PC ?) type device on your LAN, like I could do with my Syno NAS. Then it would be this device that should be "VPN natted" by pfSense - pfSense role stops there. All devices on your network should be set up to accept connections from some VPN range IP's, and not others.
-
ya i think i got it working
i did a bunch of googling,. but sometimes when you dont know what specific words to look for doesnt always help... and since last time i really did command line routers etc was 20 yrs ago in college cisco routers and redhat linux since then been asus dlink routers gui and that was it.. only got into pfsense a couple years ago.. as the asus dlink couldnt do what i wanted..
so ya i learn but since im a visual learner the negate docs little harder for me the talk but when it says +4 to the number above doesnt make sense to me.. they could detail that better which number do you increase by 4... and pictures be nice in documents...not i not sure if i did it totally right but it seems to be working.. but i hear ya.. if you know the concept like driving a car.. the better cars (routers like pfsense) do the same stuff just more features... learning the features isnt always found in google or the youtube videos... watched 4 youtube videos but didnt go in depth what i wanted
but it seems to be working now to get teamviewer or something better to access a ubuntu vms desktop be easier if i could just ip address in like a rdp app for windows..
and thank you for all the help (: wish i explained better at the beginning maybe i wouldnt replied with soo many pics lol
ah ok and its not like MCSE you gotta master it all just to get a certificate.. never fished doing that years ago
would been nice youtube 20 yrs ago if it was invented.. so needed help with netware cisco routers books werent always helpful lol
and not help forums back then -
@Gertjan
the only thing i didnt figure out yet is ..dnsleaktest site.. says my local internet
shouldnt it say ipaddress 192.168.110.5 dns server 192.168.0.1 my pfsense this way you know your secure.. openvpn tunnel.. so i havent figure or found video yet for that