pfSense sends packet as 0.0.0.0
-
Does the ping work from pfSense if you say the WAN interface is the source ?
-
@NogBadTheBad yes, with this selection works
-
Should just work out the box with automatic rules.
You should have your LAN subnets in the automatic rules as well.
-
@NogBadTheBad yes, all seems right. But still it does not work.
-
Post a screen shot of your NAT rules and your LAN rules.
You can just drag and drop them into the chat window.
-
@NogBadTheBad NAT outgoing:
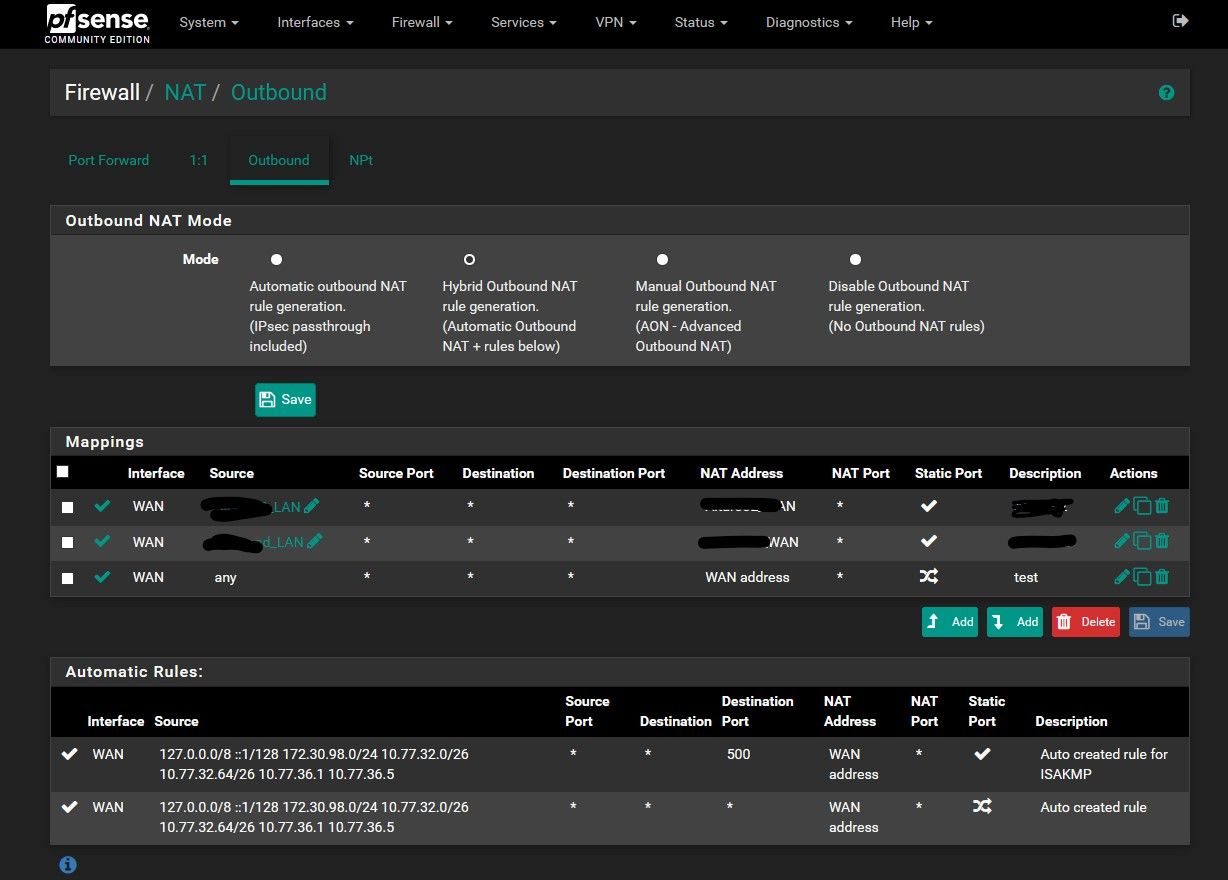
The last mapping is what I added as workaround.
Previous two are specific rules (working well) for two specific hosts in the LAN that need specific outgoing IP address. -
@NogBadTheBad rules LAN
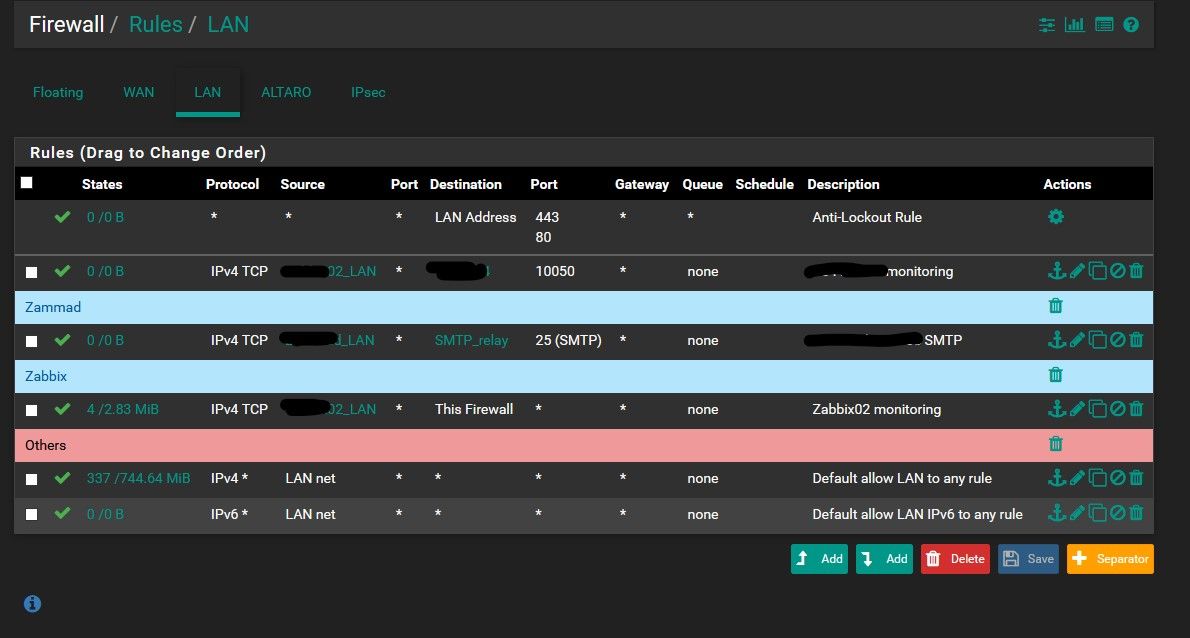
-
Curious why do you have 2 specific IPs in your auto outbound nats? 10.77.36.1 and .5
What specific IP of client where you pinging from to 1.1.1.1 when you saw the outbound from 0.0.0.0?
And your hybrid, so you have specific vips on your wan?
Trying to figure out how your auto rules match up to your networks.. From your rules I see only 2 interfaces. So that would be 2 networks in auto. If it was showing your 2 ipsec, why do you only have 3 there should be 4?? And if the singles are your ipsec? Where is the 3rd range coming from..
So yeah a bit confusing...
-
@johnpoz I was pinging from pfSense itself, not from a client. From clients works.
Yes I have some additional VIPs
Yes I have two LANs + two IPSECs. LANs are 10.77.32.0/26 and 10.77.32.64/26. 10.77.36.1 and .5 are IPs on the point-to-point IPSEC tunnels. 172.30.98.0/24 is a subnet on the remote side of IPSEC (this is strange, yes).
However as I said the problem is not from the connected networks. The problem is only from pfSense itself.
-
Can we see an example in a pcap?
-
@Topogigio said in pfSense sends packet as 0.0.0.0:
but is seems having trouble connecting to Internet.
In what manner? Are you saying it can not check for updates? Unbound is not working... What is not working.. Other than when you do a manual ping, you say you see source of all zeros? When you don't pick an interface?
-
@johnpoz I noticed the problem because it was unable to populate the available package list..
So I noticed that it was unable to resolve DNS, then that was unable to ping, and so on.
After the outpoing NAT rule I added as workaround all started to work. -
so when you remove that rule, it doesn't work anymore? Or maybe unbound just had an issue? If you can not resolve.. Did you see dns traffic going out with all zeros as source?
-
- You should never have an outbound NAT rule with a source of
any-- fix that before anything else. You are in hybrid mode so it's unnecessary anyhow. - Let's see the pcap, or a screenshot of it loaded in wireshark
- What shows up in Diagnostics > States for the traffic that is sourced as
0.0.0.0?
The last time this happened there was something unusual on the user's setup, though I can't remember what it was. I want to say maybe it was an IPv6-only IPsec VTI instance but I'm probably misremembering.
- You should never have an outbound NAT rule with a source of
-
@johnpoz If I remove that rule, it does not work anymore. If I remove that rule I see traffic (ICMP request for example) from pfSense with 0.0.0.0 as source. Only traffic from pfSense itself, not traffic from other hosts routed through it.
-
- I know it. I added it as workaround, without that pfSense is unable to contact the world to resolve DNS or download updates.
- sorry, a pcap from where? I have access to pfSense and nothing else on the external side.
From the pfSense:
PING 8.8.8.8 (8.8.8.8): 56 data bytes
--- 8.8.8.8 ping statistics ---
3 packets transmitted, 0 packets received, 100.0% packet loss
15:37:32.819751 IP 0.0.0.0 > 8.8.8.8: ICMP echo request, id 32851, seq 0, length 64
15:37:33.830224 IP 0.0.0.0 > 8.8.8.8: ICMP echo request, id 32851, seq 1, length 64
15:37:34.840837 IP 0.0.0.0 > 8.8.8.8: ICMP echo request, id 32851, seq 2, length 64states: I cannot find anything related to 8.8.8.8
I have IPSEC VTI interfaces, but I'm sure that the problem has started AFTER I configured them (because I required OSPF so I installed the package after the VPNs were connected. However can be something there, I agree. But I cannot understand why and what..
-
No states shown for 0.0.0.0 either?
-
@stephenw10 sorry, found:
WAN icmp 0.0.0.0:25462 -> 8.8.8.8:25462 0:0 3 / 0 252 B / 0 B
-
Show the entire output of
ifconfig -aandnetstat -rn.Something is broken in your setup and it's not NAT. The NAT is hiding the real issue.
-
@jimp Routing tables
Internet:
Destination Gateway Flags Netif Expire
default X.X.X.254 UGS hn0
10.0.0.0/24 10.77.36.1 UG1 ipsec100
10.0.1.0/24 10.77.36.1 UG1 ipsec100
10.0.2.0/24 10.77.36.1 UG1 ipsec100
10.20.0.0/22 10.77.36.1 UG1 ipsec100
10.40.0.0/25 10.77.36.1 UG1 ipsec100
10.40.0.0/24 10.77.36.1 UG1 ipsec100
10.40.0.128/25 10.77.36.1 UG1 ipsec100
10.77.32.0/26 link#6 U hn1
10.77.32.1 link#6 UHS lo0
10.77.32.64/26 link#7 U hn2
10.77.32.65 link#7 UHS lo0
10.77.36.1 link#8 UH ipsec100
10.77.36.2 link#8 UHS lo0
10.77.36.5 link#9 UH ipsec200
10.77.36.6 link#9 UHS lo0
X.X.X.104 link#5 UHS lo0
X.X.X.104/32 link#5 U hn0
X.X.X.105 link#5 UHS lo0
X.X.X.105/32 link#5 U hn0
X.X.X.106 link#5 UHS lo0
X.X.X.106/32 link#5 U hn0
X.X.X.40/30 10.77.36.1 UG1 ipsec100
X.X.X.84/30 10.77.36.1 UG1 ipsec100
X.X.X.246 X.X.X.254 UGHS hn0
X.X.X.38 X.X.X.254 UGHS hn0
127.0.0.1 link#1 UH lo0
X.X.X.254 02:00:00:5f:28:ad UHS hn0
172.16.0.0/22 10.77.36.1 UG1 ipsec100
172.19.0.0/16 10.77.36.1 UG1 ipsec100
172.19.16.64/26 10.77.36.1 UG1 ipsec100
172.19.32.0/20 10.77.36.1 UG1 ipsec100
172.26.0.0/16 10.77.36.1 UG1 ipsec100
172.27.0.0/16 10.77.36.1 UG1 ipsec100
172.27.64.0/19 10.77.36.1 UG1 ipsec100
172.29.0.0/16 10.77.36.1 UG1 ipsec100
172.30.94.0/26 10.77.36.1 UG1 ipsec100
172.30.94.64/26 10.77.36.1 UG1 ipsec100
172.30.94.128/26 10.77.36.1 UG1 ipsec100
172.30.96.0/24 10.77.36.1 UG1 ipsec100
172.30.98.0/24 10.77.36.1 UGS ipsec100
172.30.99.0/24 10.77.36.1 UG1 ipsec100
172.30.252.0/24 10.77.36.1 UG1 ipsec100
172.30.254.1/32 10.77.36.1 UG1 ipsec100
172.30.254.2/32 10.77.36.1 UG1 ipsec100
172.30.254.11/32 10.77.36.1 UG1 ipsec100
172.30.254.12/32 10.77.36.1 UG1 ipsec100
172.30.254.13/32 10.77.36.1 UG1 ipsec100
172.30.254.14/32 10.77.36.1 UG1 ipsec100
172.30.254.15/32 10.77.36.1 UG1 ipsec100
172.30.254.16/32 10.77.36.1 UG1 ipsec100
172.30.254.28/32 10.77.36.1 UG1 ipsec100
172.30.254.29/32 10.77.36.1 UG1 ipsec100
172.30.254.34/32 10.77.36.1 UG1 ipsec100
172.30.254.35/32 10.77.36.1 UG1 ipsec100
172.30.254.46/32 10.77.36.1 UG1 ipsec100
172.30.254.47/32 10.77.36.1 UG1 ipsec100
172.30.254.53/32 10.77.36.1 UG1 ipsec100
172.30.254.54/32 10.77.36.1 UG1 ipsec100
172.30.254.55/32 10.77.36.1 UG1 ipsec100
172.30.254.56/32 10.77.36.1 UG1 ipsec100
172.30.254.59/32 10.77.36.1 UG1 ipsec100
172.30.254.60/32 10.77.36.1 UG1 ipsec100
172.30.254.63/32 10.77.36.1 UG1 ipsec100
172.30.254.64/32 10.77.36.1 UG1 ipsec100
172.30.254.71/32 10.77.36.1 UG1 ipsec100
172.30.254.72/32 10.77.36.1 UG1 ipsec100
172.30.254.73/32 10.77.36.1 UG1 ipsec100
172.30.254.74/32 10.77.36.1 UG1 ipsec100
172.30.254.76/30 10.77.36.1 UG1 ipsec100
172.30.254.80/30 10.77.36.1 UG1 ipsec100
172.160.10.0/24 10.77.36.1 UG1 ipsec100
192.168.0.0/24 10.77.36.1 UG1 ipsec100
192.168.1.0/24 10.77.36.1 UG1 ipsec100
192.168.2.0/24 10.77.36.1 UG1 ipsec100
192.168.19.0/24 10.77.36.1 UG1 ipsec100
192.168.21.0/24 10.77.36.1 UG1 ipsec100
192.168.22.0/24 10.77.36.1 UG1 ipsec100
192.168.24.0/24 10.77.36.1 UG1 ipsec100
192.168.29.0/24 10.77.36.1 UG1 ipsec100
192.168.32.0/24 10.77.36.1 UG1 ipsec100
192.168.33.0/24 10.77.36.1 UG1 ipsec100
192.168.34.0/24 10.77.36.1 UG1 ipsec100
192.168.41.0/24 10.77.36.1 UG1 ipsec100
192.168.47.0/24 10.77.36.1 UG1 ipsec100
192.168.51.0/24 10.77.36.1 UG1 ipsec100
192.168.52.0/24 10.77.36.1 UG1 ipsec100
192.168.96.0/24 10.77.36.1 UG1 ipsec100
192.168.97.0/26 10.77.36.1 UG1 ipsec100
192.168.97.64/26 10.77.36.1 UG1 ipsec100
192.168.100.0/24 10.77.36.1 UG1 ipsec100
192.168.103.192/26 10.77.36.1 UG1 ipsec100
192.168.190.0/24 10.77.36.1 UG1 ipsec100
195.43.163.9/32 10.77.36.1 UG1 ipsec100
195.43.178.150/32 10.77.36.1 UG1 ipsec100Internet6:
Destination Gateway Flags Netif Expire
::1 link#1 UH lo0
fe80::%lo0/64 link#1 U lo0
fe80::1%lo0 link#1 UHS lo0
fe80::%hn0/64 link#5 U hn0
fe80::ff:fe5f:28ad%hn0 link#5 UHS lo0
fe80::%hn1/64 link#6 U hn1
fe80::215:5dff:fe5a:1601%hn1 link#6 UHS lo0
fe80::%hn2/64 link#7 U hn2
fe80::215:5dff:fe5a:1602%hn2 link#7 UHS lo0
fe80::%ipsec1000/64 link#8 U ipsec100
fe80::215:5dff:fe5a:1601%ipsec1000 link#8 UHS lo0
fe80::%ipsec2000/64 link#9 U ipsec200
fe80::215:5dff:fe5a:1601%ipsec2000 link#9 UHS lo0Shell Output - ifconfig -a
lo0: flags=8049<UP,LOOPBACK,RUNNING,MULTICAST> metric 0 mtu 16384
options=680003<RXCSUM,TXCSUM,LINKSTATE,RXCSUM_IPV6,TXCSUM_IPV6>
inet6 ::1 prefixlen 128
inet6 fe80::1%lo0 prefixlen 64 scopeid 0x1
inet 127.0.0.1 netmask 0xff000000
nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL>
groups: lo
enc0: flags=41<UP,RUNNING> metric 0 mtu 1536
nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL>
groups: enc
pfsync0: flags=0<> metric 0 mtu 1500
groups: pfsync
pflog0: flags=100<PROMISC> metric 0 mtu 33160
groups: pflog
hn0: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> metric 0 mtu 1500
options=48001b<RXCSUM,TXCSUM,VLAN_MTU,VLAN_HWTAGGING,LINKSTATE,TXCSUM_IPV6>
ether 02:00:00:5f:28:ad
hwaddr 02:00:00:5f:28:ad
inet6 fe80::ff:fe5f:28ad%hn0 prefixlen 64 scopeid 0x5
inet X.X.X.104 netmask 0xffffffff broadcast X.X.X.104
inet X.X.X.105 netmask 0xffffffff broadcast X.X.X.105
inet X.X.X.106 netmask 0xffffffff broadcast X.X.X.106
nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL>
media: Ethernet autoselect (10Gbase-T <full-duplex>)
status: active
hn1: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> metric 0 mtu 1500
options=48001b<RXCSUM,TXCSUM,VLAN_MTU,VLAN_HWTAGGING,LINKSTATE,TXCSUM_IPV6>
ether 00:15:5d:5a:16:01
hwaddr 00:15:5d:5a:16:01
inet6 fe80::215:5dff:fe5a:1601%hn1 prefixlen 64 scopeid 0x6
inet 10.77.32.1 netmask 0xffffffc0 broadcast 10.77.32.63
nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL>
media: Ethernet autoselect (10Gbase-T <full-duplex>)
status: active
hn2: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> metric 0 mtu 1500
options=48001b<RXCSUM,TXCSUM,VLAN_MTU,VLAN_HWTAGGING,LINKSTATE,TXCSUM_IPV6>
ether 00:15:5d:5a:16:02
hwaddr 00:15:5d:5a:16:02
inet6 fe80::215:5dff:fe5a:1602%hn2 prefixlen 64 scopeid 0x7
inet 10.77.32.65 netmask 0xffffffc0 broadcast 10.77.32.127
nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL>
media: Ethernet autoselect (10Gbase-T <full-duplex>)
status: active
ipsec1000: flags=8051<UP,POINTOPOINT,RUNNING,MULTICAST> metric 0 mtu 1422
tunnel inet X.X.X.104 --> X.X.X.246
inet6 fe80::215:5dff:fe5a:1601%ipsec1000 prefixlen 64 scopeid 0x8
inet 10.77.36.2 --> 10.77.36.1 netmask 0xfffffffc
nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL>
reqid: 1000
groups: ipsec
ipsec2000: flags=8051<UP,POINTOPOINT,RUNNING,MULTICAST> metric 0 mtu 1438
tunnel inet X.X.X.104 --> X.X.X.38
inet6 fe80::215:5dff:fe5a:1601%ipsec2000 prefixlen 64 scopeid 0x9
inet 10.77.36.6 --> 10.77.36.5 netmask 0xfffffffc
nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL>
reqid: 2000
groups: ipsec