Blocking DNS over HTTPS. Seems the only way is to fire a shotgun at it
-
I know it's a crude solution, but it's all I have until something else is suggested.
-
I hear you, and agree with you what the companies are doing is utter shitstorm... Looking out for the users my ass.. They just want the dns queries sent to them.. And they want them from each of their products directly so they can better track every single user vs a bunch of users hiding behind a caching server..
These companies are not trying to better anything - they are finding more ways to monetize user data..
This whole dot, doh is just one large shit show... That is is for damn sure.
If your going to roll it out, it sure and the hell should be mandatory opt-in, and it should check for a canary that the local enterprise can put in place to make sure its turned off on any browser on the corp network, where dhcp handed the OS a corp dns server.
Atleast with dot, port 853 its easy enough to block. Hiding it inside 443 is just more sneaky bs..
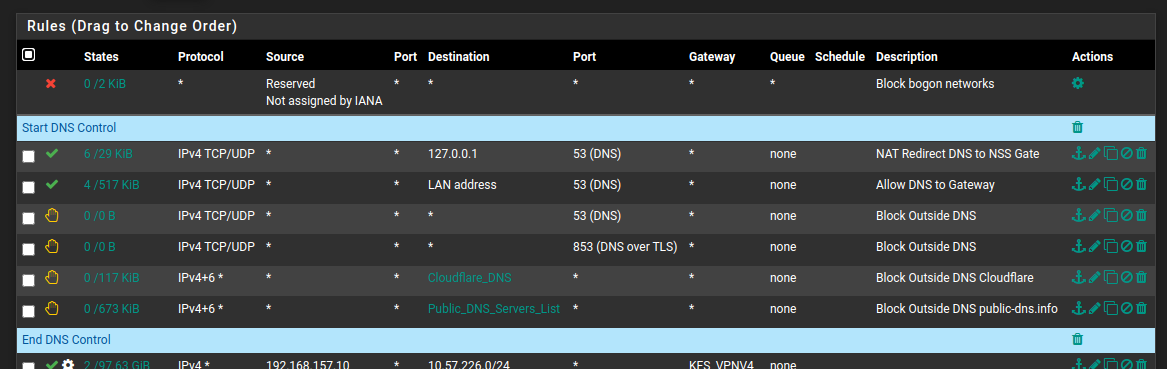
Here is list of doh IPs I am using
https://raw.githubusercontent.com/Sekhan/TheGreatWall/master/TheGreatWall_ipv4This it the IPs they list for cloudflare doh
# Cloudflare 1.1.1.1 1.0.0.1 104.16.248.249 104.16.249.249 104.18.2.55 104.18.3.55 104.18.27.128 104.18.26.128Also when they control your dns - pretty difficult to block ads based on dns..
Anyone that thinks this is doing anything but giving these companies more control and more info is blinded by the BS.. Trust us we will make you safer my F'ing ASS! ;)
You can look here for a list of doh fqdn
https://github.com/curl/curl/wiki/DNS-over-HTTPSAnd they have a script to help you parse it.
-
@johnpoz Thanks for that list, I'll study that. In fact I'll evaluate the efficacy of that list in place of the blanket block I currently test.
-
I also have put in some host overrides to resolve most of these fqdn to local IP that I block, and log - so I can see what IP might be trying to hit it
local-zone: "use-application-dns.net" always_nxdomain local-zone: "local." always_nxdomain local-data: "dns.adguard.com. 120 IN A 172.19.19.19" local-data: "dns-family.adguard.com. 120 IN A 172.19.19.19" local-data: "dns.google. 120 IN A 172.19.19.19" local-data: "cloudflare-dns.com. 120 IN A 172.19.19.19" local-data: "dns.quad9.net. 120 IN A 172.19.19.19" local-data: "dns9.quad9.net. 120 IN A 172.19.19.19" local-data: "dns10.quad9.net. 120 IN A 172.19.19.19"It is much longer than that - but really need to work out a more elegant way than just entries in unbound.. Just haven't gotten around to it yet.. And nothing has hit any of my rules.. I always make sure sure its turned off any browser I use..
see my edit above for a github list that lists many of the fqdn used..
-
I tested the list at https://raw.githubusercontent.com/Sekhan/TheGreatWall/master/TheGreatWall_ipv4
Unfortunately, Chrome immediately started sending queries to 162.158.161.161 in Singapore and bypassing my countermeasures. -
I realise Cloudflare cannot be using their entire IP space to serve up DNS, but they're clearly using a lot of IPs embedded in many, many subnets, either as a part of their design, or deliberately to obfuscate the target server for network admins.
-
Hi-
How do you feel about using this list in PF Blocker https://heuristicsecurity.com/dohservers.txt.I know not everyone uses PF blocker, but how does a list of the DNS ip work for blocking when the query is sent out FQDN?
-
I'm now playing with a host override in my DNS resolver, pointing cloudflare-dns.com at local IPs to monitor, as you suggest above. However, I am seeing completely different IPs being queried from Chrome, also with DNS leak test websites. If I do a DNS lookup from the gateway itself, on those Cloudflare FQDNs, the IPs returned are in the blocklist. IPs queried from Chrome are not in the blocklist. Chrome must be using a different, unknown FQDN
-
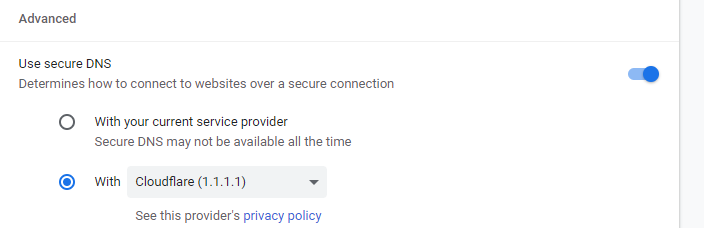
What exactly are you settings in chrome? So you have it on purpose set to try and use doh, and your trying to block it?
You have it set like this
If so, I can do that and look to see what its doing.. Logging all traffic coming from the machine.. with a sniff.
And see if dns works.
-
@johnpoz Yes, Chrome DoH set to use system DNS, host machine set to use 1.0.0.1 and 1.1.1.1
This particular machine in Bangkok keeps using IP 162.158.161.161 when using DNS leak test website
-
Show me the setting you have set, like I have above - you have the other setting set..
And how your seeing that IP is from a leaktest.. I think your not understanding how those tests work.. Then.. Just because you see an IP there doesn't mean your client talked to that IP..
-
@johnpoz I have experimented with all the setting variants i.e. like in your screenshot above, and the other "current provider" setting. It appears to have the same result. If I choose Google, or CleanBrowsing, my countermeasures work. However, with Cloudflare, it is extremely difficult to block as far as I can see, without blocking all of their IPs.
-
@johnpoz said in Blocking DNS over HTTPS. Seems the only way is to fire a shotgun at it:
I think your not understanding how those tests work.. Then.. Just because you see an IP there doesn't mean your client talked to that IP..
Perhaps so. I am merely using that leak test site as an easy reference to see if that endpoint is using the DNS provider I specify in the gateway, or Cloudflare. It's ALWAYS Cloudflare without the blanket ban on Cloudflare IPs in place. You are correct in that I'm not understanding why this is so. I am trying to understand so I can remedy it.
-
chrome is using this
chrome.cloudflare-dns.com
With the setting I had above..
added that to my block list, and no more chrome working for anything with that setting.
If you want to know what its doing, and what IPs it talking to - vs those stupid leak tests.. Just sniff.. See right away where its going
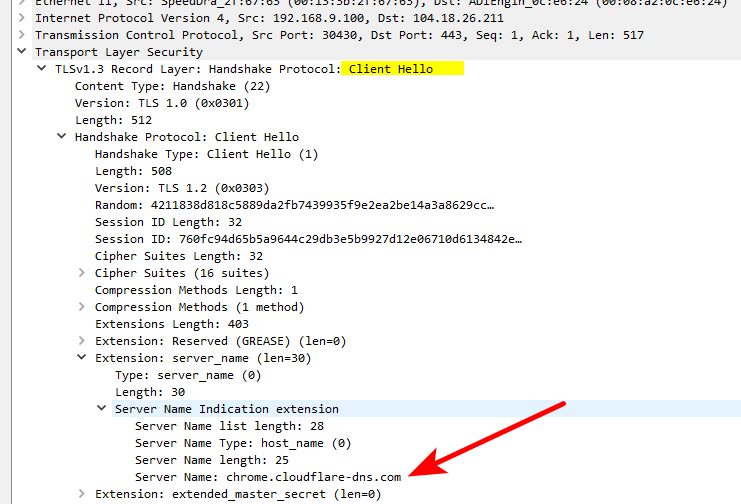
Those leak tests don't show you what IP the client talked to, they show you what IP ended up resolving the test fqdn they used... So it could be some IP upstream of where you asked that actually resolved it... Those tests are pointless scare tactics to get users to be scared -- OMG its "leak" without clue one to what actually is going on..
It never shows you 1.1.1.1 or 9.9.9.9 in those stupid tests.. It might show you your lame ISP dns if your using that - which NS uses the same IP to resolve with as it listens for queries on.. Small setups not enterprise or CDN setups..
The real problem here is users don't actually even understand what dns is or how it works - and if someone says hey your "leaking" they jump!!! OMG.... the man knows what I did a dns query for... The black helicopters are coming.. Without clue one to the basics of how any of it works in the first place... They can not tell you the difference between a forwarder or resolver, etc..
Sorry for the rant... Those dns leak tests don't do anything other than scare users to be honest.
-
@johnpoz Kudos!!! So it was indeed a previously unknown FQDN. That's sure going to make things easier for me.
-
Oh you got me started - sorry... The above example where I show how easy it is to see where you went in a simple sniff..
Should show these users.. They are so worried omg my ISP knows what websites I am going to... Hiding your dns doesn't stop them from knowing that.. Even encrypting it and sending it all to whereever..
They still see the IPs you go to, and right there in the freaking hello is what fqdn you were trying to hit.. Exact same info dns gives them..
So what are you doing other than handing all your dns to someone else, along with your ISP still having the info, and making your dns slower to boot.. But OMG a freaking leak<rolleyes>
-
https://redmine.pfsense.org/issues/10969 - feature request for adding https://github.com/Sekhan/TheGreatWall feeds to pfBlockerNG
-
Just to update this topic, setting the following in my resolver's custom options. . .
server: local-zone: "use-application-dns.net" always_nxdomain local-zone: "cloudflare-dns.com" static. . . and adding the following IP lists to the firewall as blocked aliases. . .
https://public-dns.info/nameservers.txt
https://raw.githubusercontent.com/Sekhan/TheGreatWall/master/TheGreatWall_ipv4. . . completely hamstrings Firefox and Chrome's attempts to use DoH. I'm sure they will find new ways to screw with network admins, but for the time being, this appears to be highly effective, while keeping things pretty neat and tidy. This is what I am deploying on my production network.
NOTE: Anyone reading this, don't just throw this into your config and forget. You MUST also have the DNS redirects to your local resolver/forwarder in place first.
-
@Lanna said in Blocking DNS over HTTPS. Seems the only way is to fire a shotgun at it:
local-zone: "cloudflare-dns.com" static
That is a great solution.. Since you set it static, unbound will not try to resolve any subdomains of that be it the Mozilla or the chrome one..
-
@Raffi_
Yea, that "managed environment..." seems to work for domain aware devices. I imported their Active Directory settings into my home domain (Windows Server 2016), and it comes up as disabled by default on domain members. I did turn off the Chrome DNS function via their policy additions anyway (and disabled DOT in Firefox too using their extensions). I then turned my attention to the non-domain stuff so added a NAT redirect for 53 on my IOT VLAN to catch all the 53 to 8.8.8.8 and redirect to my DNS, and don't allow 853 to the internet. DOH from the non-domain-joined IOT was still an issue, so I just setup Lanna's suggestion of the two block lists and the local-zone setting.This seems like a lot of work to stop software from doing something against my wishes. I was using DOT for a bit but decided I was still handing over my my browsing history to some company so I am just letting the router do the resolving to root servers now.
Feels like a cat and mouse game, or wack a mole...