pfSense being client and being gateway for a DMZ subnet
-
Hi there,
I'm running pfSense with an OpenVPN server.
Everything works well but the OpenVPN server interface is on a LAN subnet and i'd like to put it on a DMZ subnet. It's worth noting that I have no "real WAN" interface as everything is already NATed behind another firewall.
Actually I have no DMZ subnet and all the LAN subnets are routed with L3 switches. I'd like pfSense being the router for this new DMZ subnet to be able to filter it correctly (ACL on switches are hardly manageable).
So, in summary, my pfSense instance should have an IP address for the OpenVPN server inside the DMZ while being also the gateway for the very same DMZ subnet.
And this idea is a bit difficult to conceptualize in my head.
What would be the best way to implement it ? Should I add another interface to act as gateway ? A virtual IP address associated with the same physical interface that is already in use for the OpenVPN server ?
Thanks in advance for your support.
Kind regards,
Captain -
@CaptainPistache said in pfSense being client and being gateway for a DMZ subnet:
And this idea is a bit difficult to conceptualize in my head.
If you think your having a hard time - think about us ;)
I have read this like 3 times and have no idea what your wanting to accomplish.
You do have a wan on pfsense - this is the interface connected to your upstream router. Does not matter what the IP on this interface is - public or rfc1918.
Your vpn service would listen on this interface/IP. If its rfc1918, then you would have to forward at your upstream nat router to the IP of pfsense wan on the port your listening on.
You would use a tunnel network for this vpn connection that is something that does not overlap with any of your downstream networks of pfsense. If you have some downstream L3 switch doing routing. The only network on pfsense, no matter what you want to call it lan, optX, dmz would be a transit network to your downstream "router" (your L3 switch)..
Doesn't matter if you have only 1 network behind pfsense or 100, you would implement it the same way.. How many networks you have behind pfsense has nothing to do with how you would setup the vpn. Other than you would list in the vpn setup the local networks you want your vpn clients to get to.. Unless your setup up the client to send everything down the vpn.
Unless your trying to use tap vs tun.. Which makes no sense.. And almost never a good idea..
How about you draw up what your wanting to do - and we can go from there.
Here is a conceptual logical drawing..

How many networks you have behind pfsense, or if their downstream or directly attached to pfsense doesn't have really anything to do with the vpn connection from the client out somewhere on the internet/wan to pfsense..
Why do you think this vpn user needs an IP on some downstream network of yours? Are you needing/wanting to do some sort of L2 communication? Broadcast discovery? Again its almost never a good idea to use tap or bridge vpn connection.. Tun or routed is almost always a better choice.. You don't want broadcast traffic using up your vpn bandwidth.
https://community.openvpn.net/openvpn/wiki/BridgingAndRouting
TAP drawbacks causes much more broadcast overhead on the VPN tunnel adds the overhead of Ethernet headers on all packets transported over the VPN tunnel scales poorly can not be used with Android or iOS devices -
Thanks for the time you took to reply me with a detailed answer. Reading your reply, I realize that my request is not clear.
Here is a quick scheme of my actual situation :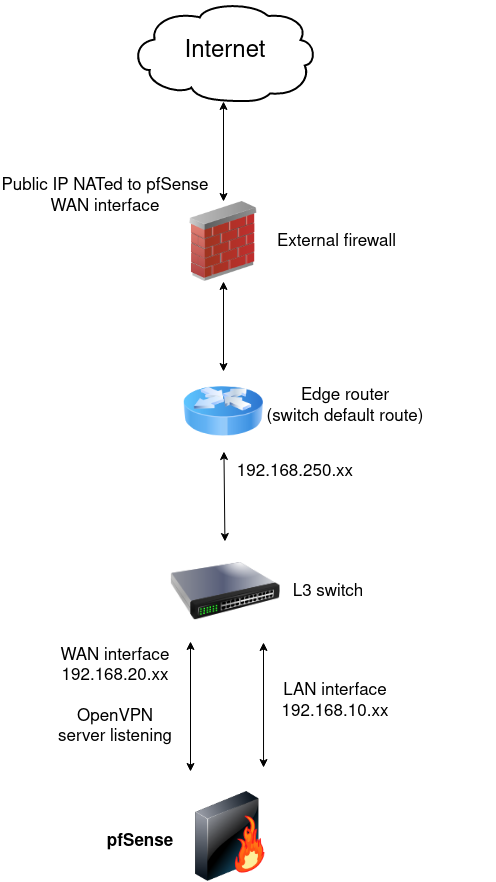
First, the OpenVPN server is working perfectly fine. I'm not interested to change anyhting beyond the edge router but only slight changes inside my private network.
All my private subnets are routed with the L3 switch and the Internet traffic is then going to the edge router.
What I want to do is :
- Create a new private subnet acting as a DMZ.
- This new subnet won't be routed by the L3 switch but only by pfSense.
- The L3 switch will only act as a L2 switch for this specific subet and forward the egress traffic to the edge router.
- Replace the pfSense WAN interface with an IP address in this new DMZ subnet.
Is this clearer ?
L3 switch configuration is not an issue but I'm struggling to find how I can implement this new DMZ subnet on pfSense.
Thanks.
Kind regards,
Captain -
Hello,
Your topology doesn't make sense.
You should have something like :
INTERNET => External Firewall (I suppose it's your ISP box) => pfSense => Internal switch (L2).Convert your L3 switch into an L2 (disable all routing taking place at the switch level, and make the pfSense handle the inter-VLAN routing and filtering).
Your EdgeRouter is useless in the above schema. -
@CaptainPistache said in pfSense being client and being gateway for a DMZ subnet:
Is this clearer ?
Sorry but no... Looks like a dumpster fire to be honest.. If its L3 doing routing? Stop calling it a switch.. Its being used as router?
Is it doing nat as well? What network is on wan side of your edge router?
Is this 192.168.250 a transit to get to the 192.168.20 that is behind your L3 router?
So logically you have this setup?

What masks are being used on these networks? /24 - what is the network between your edge router and your external? Assume all of these devices, external, edge and pfsense are all natting as well?
And you want to hang a new network off your pfsense and call it a dmz?
That just looks like a complete dumpster fire to me.. All of it could be replaced with just pfsense all the way at the external or replace the edge... I assume you also have other networks hanging off the edge and the L3? So without a whole shit ton of natting going on you would have a asymmetrical nightmare as well. Do you have other devices in these 192.168.250 and .20 networks? What about whatever network upstream of your edge router?
That fine if your using your L3 as both a router and L2 switch.. But it can get confusing drawing like you have... Just draw the logical connections and routing - forget the L2 connections. It doesn't matter from a logical point of view if all the networks go through the switch as vlans physically.
-
I understand the actuel scheme doesn't look optimal but there are reasons (historical / technical) behind this.
I should have added more information on the scheme :
- The MPLS routers and the upstream firewall are not part of my network. I cannot access nor modify their configs.
- There is no NAT inside the network before the "Partner's external firewall".
- The "Partner" acts as an ISP for our network.
- My scheme is truly a logical one. The one you have drawn does not correctly represent the routing as the subnet .10 is routed with the L3 switch (router if you want) and not through pfSense.
- I don't want pfSense routing all my private subnets because it is not hosted on a dedicated hardware and that's not my goal actually.
- pfSense has been added recently, its main goal was to provide a VPN solution but I thought it would be a good solution to create a DMZ subnet and let it filter it.
- Masks are /24.
- I have plenty of internal devices in the .20 network and in the .250 subnet, that's why I want my OpenVPN server in another subnet.
-
Ok.
So basically, if you want to create a DMZ :
- on your L3 switch, create a new VLAN to be used as a DMZ.
- DO NOT assign an IP address in this VLAN on the switch, this will prevent routing to take place on the switch directly.
- on pfsense :
- if you have spare NIC : patch the NIC to a port of the L3 switch in the new VLAN
- create a new interface "DMZ" using the new NIC - if you don't have a spare NIC :
- convert your LAN interface's switch port into a trunk, pass both LAN and DMZ VLAN on the trunk
- change your "LAN" interface on pfSense to use a sub-interface on the trunk, with VLAN ID matching the LAN VLAN
- create a new "DMZ" interface on pfSense and assign it a new sub-interface on the trunk, with VLAN ID matching the DMZ VLAN
- if you have spare NIC : patch the NIC to a port of the L3 switch in the new VLAN
On the L3 switch, you'll have to set a route telling the DMZ network can be reached through pfsense.
That's it.
The most important step : do not route any traffic to the DMZ VLAN on the L3 switch.
On Cisco switches, the simplest way to prevent that is not to create a vlanXYZ interface, and especially not assign it an IP address.But to be 100% clear, and as JohnPoz said, your topology is bogus.
You'll soon enter in a routing nightmare, good luck with that .
. -
Thanks a lot for your answer, I really appreciate.
@Myster_fr said in pfSense being client and being gateway for a DMZ subnet:
Ok.
So basically, if you want to create a DMZ :
- on your L3 switch, create a new VLAN to be used as a DMZ.
- DO NOT assign an IP address in this VLAN on the switch, this will prevent routing to take place on the switch directly.
Yes, this is clear and I have already implemented this part.
- on pfsense :
- if you have spare NIC : patch the NIC to a port of the L3 switch in the new VLAN
- create a new interface "DMZ" using the new NIC
- if you have spare NIC : patch the NIC to a port of the L3 switch in the new VLAN
This is where I'm a bit stuck.
pfSense is running on a VM so I can add as many NIC I want.
As this DMZ interface is going to be the route to the Internet and my WAN interface, what would be its upstream gateway ?
Also, the interface of my OpenVPN server is going to be in the DMZ subnet too.
So, should I have ?- One interface (let's say 192.168.30.250/24) that will act as the DMZ subnet gateway linked to a vNIC connected to the DMZ vlan.
- One interface (let's say 192.168.30.10/24) that will act as my OpenVPN server IP address linked to the same vNIC connected to the DMZ vlan ?
On the L3 switch, you'll have to set a route telling the DMZ network can be reached through pfsense.
That's it.
The most important step : do not route any traffic to the DMZ VLAN on the L3 switch.
On Cisco switches, the simplest way to prevent that is not to create a vlanXYZ interface, and especially not assign it an IP address.Yes, this is clear.
But to be 100% clear, and as JohnPoz said, your topology is bogus.
You'll soon enter in a routing nightmare, good luck with that .
.Would be it smarter to create another pfSense instance to act as a router for the DMZ network ?
-
@CaptainPistache you cannot have your DMZ be the route to the internet.
A DMZ is meant to be a stub network, only accessible through the firewall (here pfSense).
A DMZ cannot have direct internet access, or it will bypass your pfSense and you'll have no security.So :
- you need an additional vNIC attached to your pfSense box, which will be your "DMZ" interface", assigned to the new VLAN you've created.
- you need to assign this vNIC to a "DMZ" interface in pfsense
- you need to assign this pfSense "DMZ" interface an IP address (as you suggested, 192.168.30.250 will be fine, though a convention is usually to use .1 as the gateway interface on a given network, but that's up to you).
Then, your OpenVPN server (am I right assuming this will be a dedicated server, not OpenVPN daemon running on pfSense ?) :
- create a VM or use a physical server
- attach it to the DMZ VLAN on your switch (or VMWare, whichever)
- give your OpenVPN server an IP address in DMZ scope (so 192.168.30.10 as you suggested)
- set your OpenVPN server's default gateway as the pfSense interface = 192.168.30.250
Don't forget to put the inbound NAT rules accordingly to forward port TCP/1194 (OpenVPN) from your pfSense WAN IP address to you DMZ's OpenVPN server.
Will basically look like this:

-
@Myster_fr said in pfSense being client and being gateway for a DMZ subnet:
@CaptainPistache you cannot have your DMZ be the route to the internet.
A DMZ is meant to be a stub network, only accessible through the firewall (here pfSense).
A DMZ cannot have direct internet access, or it will bypass your pfSense and you'll have no security.So you mean I should only route my LAN traffic to my WAN interface and not through my DMZ interface which must be reserved for the services (i.e. OpenVPN) running on it ?
Then, your OpenVPN server (am I right assuming this will be a dedicated server, not OpenVPN daemon running on pfSense ?) :
No, there are both on the same server
 and that's exactly my question, how should I proceed in such case ? (should I ?)
and that's exactly my question, how should I proceed in such case ? (should I ?) -
Sorry but that doesn't make any sense again, you are over-compexifying your network.
You don't need a DMZ.
You must not bind OpenVPN server on the DMZ interface.If your pfSense box is meant to be the OpenVPN server, then OpenVPN must be bound to the pfSense WAN interface, there's no point of having it listening into the DMZ ??
Basically :
- external OpenVPN clients establish a tunnel on the pfSense box, on it's WAN IP address.
- external OpenVPN clients are thus filtered by pfSense to control what they can reach internally (on your LAN).
- your L3 switch must have a route back to your OpenVPN client's scope, through pfSense.
No need for new VLAN, no need for new interface.
Two steps :
- configure OpenVPN server on pfSense, bound to WAN
- set a route on the L3 to your OpenVPN client scope, through pfSense.
-
Ok, now I understand.
Thanks a lot for the time invested to answer me. -
No problem, come back if you have further issues
