Vlans and firewall rules
-
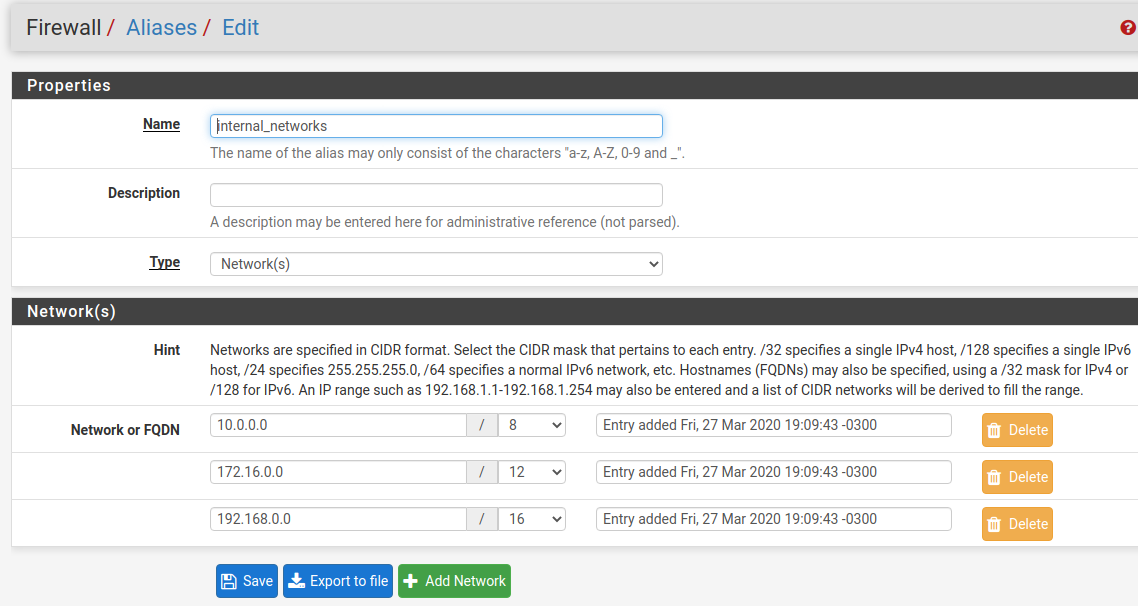
Ok here is a diagram of what I am after.
Best way to setup Firewall Rules for the below Scenarios?
Vlan 3 Scenario:
So Vlan 3 is Xbox, two Nvidia Shields and two Rokus.- only needs Internet access
- access to Vlan 4 unRaid Server and Port 9090 for plex
- My Iphone(Vlan 7) needs to be able to be used as a controller and screen casting to the two Shields
- My Iphone(Vlan 7) also needs access to Plex
Vlan 5 Scenario:
So Vlan 5 is 4 PiCore Players for streaming music from Pandora/Spotify and LMS(Logitech Media Server) on my unRaid box.- only needs Internet access
- access to Vlan 4 unRaid Server and Port 9000 for LMS
- My Iphone(Vlan 7) needs to be able to be used as a controller for LMS:9000
Also does it make sense to keep the Video Streamers and Music Streamers on different Vlans or combine them into one?
-
@cburbs VLAN3, I have a similar setup here.
I did like this for this specific VLAN: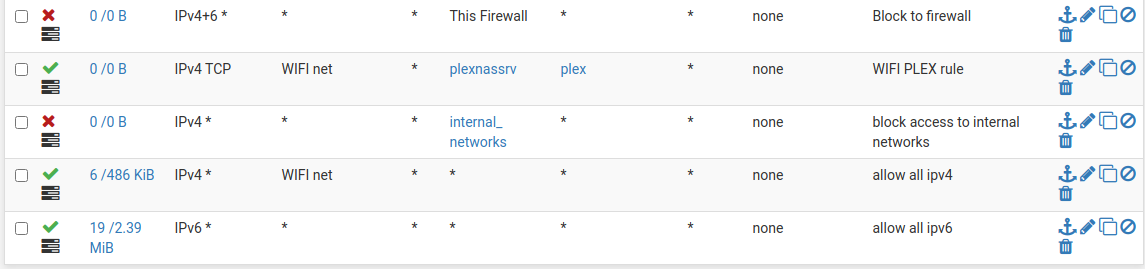
This VLAN is using an external DNS server.
-
@mcury Can you expand on your WIFI Plex Rule?
Are both plexnassrv and plex Aliases? -
@cburbs Yes, plexnassrv and plex are both aliases.
My NAS is not only a plex server, that is the reason that it is in a separate VLAN.plexnassrv is an alias with only one IP, but in your situation, you could add more for the unRaid server.
plex is an alias with port 32400 that is the plex default port. In your case, it would be 9090.
You can add more than one port to this alias.Regarding the first rule (Block to Firewall), that is needed, because without it, this VLAN would be able to access pfsense GUI trough it's WAN IP address.
So, this rule blocks access to all pfsense interfaces.Edit: internal networks is also an alias, that contains the other VLANs.
-
How do you have your Alias "Internal Networks" set?
-
I set RFC1918 because I'm always adding and removing VLANs.
But you can add only your VLANs, it would work in the same way.Just remember, in case you add a guest VLAN for an example, you would need to edit this alias and add the guest vlan.
-
Yep - Seems alot of people go that route. Some even add IPv6 stuff to it.
-
@cburbs In my situation, only "VLAN3" has IPV6 connectivity.
So, it was easy for me.Edit: I don't like the idea of my servers using IPV6.
Also, my ISP only gives me a /64.. -
Also I noticed on my Vlan test I can still ping all my devices on my LAN even though I have a rule set for that.
So..
Laptop on Lan can ping test vlan. But only one of the devices not both which is odd. This is by IP.My other laptop on test vlan can ping my lan pfsense, switch, AP, etc
Also I have pfblockerng setup on my lan. What needs to be done to pass all Vlans on this as well?
-
@cburbs said in Vlans and firewall rules:
Also I noticed on my Vlan test I can still ping all my devices on my LAN even though I have a rule set for that.
So..
Laptop on Lan can ping test vlan. But only one of the devices not both which is odd. This is by IP.
My other laptop on test vlan can ping my lan pfsense, switch, AP, etcWhat switch do you have? Some cheap switches are known to leak VLAN1.
Also I have pfblockerng setup on my lan. What needs to be done to pass all Vlans on this as well?
You can tick the box inside pfblocker to create floating rules, or just select the interfaces you would like to pfblocker to create the firewall rules.
-
-
@cburbs I'm not sure if this switch has a problem with VLAN 1.
I know other TP-Link switches that this problem happens, like TL-SG105E or TL-SG108E, in hardware revisions 1, and 2.If I remember correctly, they fixed this in revision 3, 4 and 5..
And they were leaking multicast and broadcast, not sure if that was happening to ICMP ..
Do you have a firewall rule to block ICMP from vlan test to LAN?
-
It is Versionn 4..0
No on the ICMP rule.
-
@cburbs If you don't have a block rule, this ping from vlan test to LAN will work through the Internet Rule or (ipv4 allow all)
You have to explict block it, and put this rule above the internet rule.
-
@mcury Makes sense! Thanks.
-
Ok I have my Picore music Player working with my LMS server.
So vlan 60(test vlan) can talk to my LMS server.
I also have an Nvidia Shield on this Vlan 60. My Iphone is just on my lan network what needs to be done so I can cast something from my phone to the Shield?
-
@cburbs Chromecast works with mdns, which can be accomplished with the avahi package in pfsense.
Not sure if nvidia shield works with mdns, you would have to test and confirm.Then, after installing avahi, you would need to create firewall rules to allow your iphone to reach the nvidia shield.
Chromecast uses tcp 8008 and 8009, but not sure about nvidia shieldFor testing purposes, you can create a rule to allow everything from your iphone to the nvidia shield.
Or, just put the nvidia shield in the same VLAN as the wireless devices..
-
Do you think it makes sense to have Vlan3(video streamers) and vlan5(music streamers) or would you just put them into one Vlan?
Also if in Vlan5 I have one device that just needs Internal access and nothing else is that just a block rule?
-
@cburbs said in Vlans and firewall rules:
Do you think it makes sense to have Vlan3(video streamers) and vlan5(music streamers) or would you just put them into one Vlan?
I always choose to separate servers, like samba, nas with file storage, and plex, from other devices.
So, in my scenario, I have 4 vlans.
MGMT - To manage devices
LAN - Servers
WIFI - My family devices, TVs, chromecasts, printers and etc
GUEST - for friends that come hereIn your case, I would remove VLAN5, and put video streamers and music streamers in the same vlan, which would be VLAN3.
But that is my personal choice, of course other users could have a different approach.
Also if in Vlan5 I have one device that just needs Internal access and nothing else is that just a block rule?
If you have a device in VLAN5 that needs to access VLAN3, you would create a firewall rule allowing the device (IP address), to access VLAN3, then, you would create a second rule, below the first one, blocking the entire network to access other vlans.
In the last position, the internet rule, allowing any. -
Let me rephrase that....
In vlan3 I have one device(AVR) that doesn't need access to anything.My Iphone just needs access to it to control it from an App.