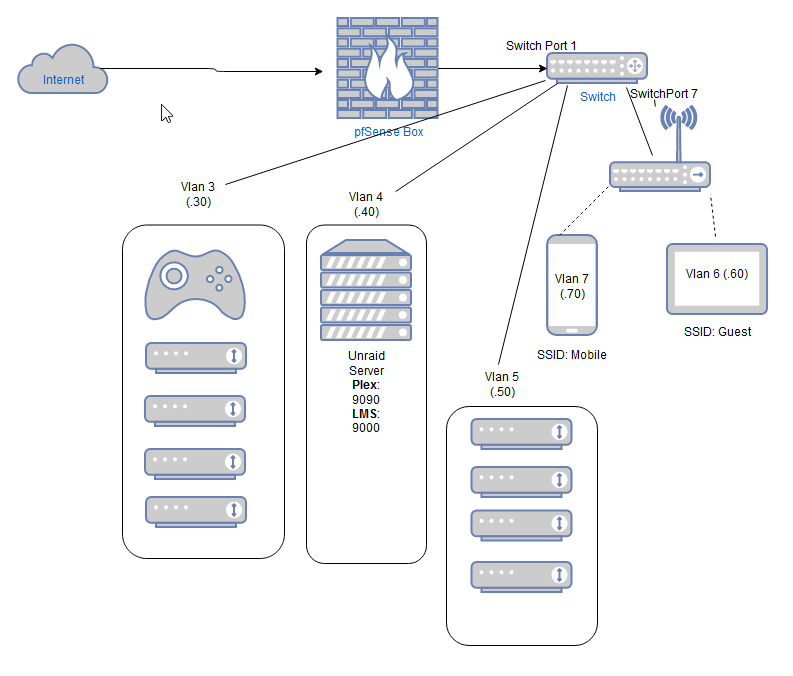
Vlans and firewall rules
-
Also I noticed on my Vlan test I can still ping all my devices on my LAN even though I have a rule set for that.
So..
Laptop on Lan can ping test vlan. But only one of the devices not both which is odd. This is by IP.My other laptop on test vlan can ping my lan pfsense, switch, AP, etc
Also I have pfblockerng setup on my lan. What needs to be done to pass all Vlans on this as well?
-
@cburbs said in Vlans and firewall rules:
Also I noticed on my Vlan test I can still ping all my devices on my LAN even though I have a rule set for that.
So..
Laptop on Lan can ping test vlan. But only one of the devices not both which is odd. This is by IP.
My other laptop on test vlan can ping my lan pfsense, switch, AP, etcWhat switch do you have? Some cheap switches are known to leak VLAN1.
Also I have pfblockerng setup on my lan. What needs to be done to pass all Vlans on this as well?
You can tick the box inside pfblocker to create floating rules, or just select the interfaces you would like to pfblocker to create the firewall rules.
-
-
@cburbs I'm not sure if this switch has a problem with VLAN 1.
I know other TP-Link switches that this problem happens, like TL-SG105E or TL-SG108E, in hardware revisions 1, and 2.If I remember correctly, they fixed this in revision 3, 4 and 5..
And they were leaking multicast and broadcast, not sure if that was happening to ICMP ..
Do you have a firewall rule to block ICMP from vlan test to LAN?
-
It is Versionn 4..0
No on the ICMP rule.
-
@cburbs If you don't have a block rule, this ping from vlan test to LAN will work through the Internet Rule or (ipv4 allow all)
You have to explict block it, and put this rule above the internet rule.
-
@mcury Makes sense! Thanks.
-
Ok I have my Picore music Player working with my LMS server.
So vlan 60(test vlan) can talk to my LMS server.
I also have an Nvidia Shield on this Vlan 60. My Iphone is just on my lan network what needs to be done so I can cast something from my phone to the Shield?
-
@cburbs Chromecast works with mdns, which can be accomplished with the avahi package in pfsense.
Not sure if nvidia shield works with mdns, you would have to test and confirm.Then, after installing avahi, you would need to create firewall rules to allow your iphone to reach the nvidia shield.
Chromecast uses tcp 8008 and 8009, but not sure about nvidia shieldFor testing purposes, you can create a rule to allow everything from your iphone to the nvidia shield.
Or, just put the nvidia shield in the same VLAN as the wireless devices..
-
Do you think it makes sense to have Vlan3(video streamers) and vlan5(music streamers) or would you just put them into one Vlan?
Also if in Vlan5 I have one device that just needs Internal access and nothing else is that just a block rule?
-
@cburbs said in Vlans and firewall rules:
Do you think it makes sense to have Vlan3(video streamers) and vlan5(music streamers) or would you just put them into one Vlan?
I always choose to separate servers, like samba, nas with file storage, and plex, from other devices.
So, in my scenario, I have 4 vlans.
MGMT - To manage devices
LAN - Servers
WIFI - My family devices, TVs, chromecasts, printers and etc
GUEST - for friends that come hereIn your case, I would remove VLAN5, and put video streamers and music streamers in the same vlan, which would be VLAN3.
But that is my personal choice, of course other users could have a different approach.
Also if in Vlan5 I have one device that just needs Internal access and nothing else is that just a block rule?
If you have a device in VLAN5 that needs to access VLAN3, you would create a firewall rule allowing the device (IP address), to access VLAN3, then, you would create a second rule, below the first one, blocking the entire network to access other vlans.
In the last position, the internet rule, allowing any. -
Let me rephrase that....
In vlan3 I have one device(AVR) that doesn't need access to anything.My Iphone just needs access to it to control it from an App.
-
@cburbs The idea would be the same.
Firewall rules goes from top, to bottom.Just block the DVR to access all other things, this rule must be in the top.
Your phone, that I'm assuming that is in other VLAN, you create a firewall rule in this other VLAN allowing the iphone to access the DVR, then you block other devices to access the other vlans, and finally the internet rule allowing everything.
In case iphone and DVR are in the same VLAN, they wouldn't communicate through the firewall, it would go directly through the switch.
-
Drawing it out as it helps me sometimes
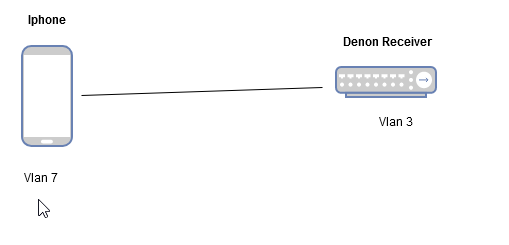
So my Iphone which is on Vlan7 needs to talk to my Denon Receiver on Vlan3.
You mention creating the rule in Vlan 7 to talk to the device in Vlan 3.
Could you also do it the other way around and create the rule on Vlan 3 to allow the Iphone in?
Is one way better than the other? and why?
-
@cburbs Creating the rule in VLAN3 wouldn't work.
The interface where the packet is coming from, needs to allow that flow in first place, otherwise the firewall would drop the packet.
pfsense is a stateful firewall, which means that if the packet is allowed to enter, the return of the packet would work, even without a rule.
So, for an example, you can create a rule blocking everything in VLAN3, so all VLAN3 ip addresses would be blocked to enter the firewall.
But, if you come from VLAN7, and if there is a rule allowing this flow, the return traffic from VLAN3 would work, even with a block everything rule.
-
@cburbs
My Onkyo Remote APP won't play if my phone/Ipad isn't on the same Vlan.
The Phone (App) simply won't detect the AMP.Bloody sw devs
Considering to trace a bit on the APP , and maybe try this package, if it fits the need
https://forum.netgate.com/topic/155698/how-can-i-get-this-udp-relay-package-for-casting-across-vlans
-
So if I setup the "Block to firewall" rule like you have in the one post but I have no internet access when it is enabled? Am I missing something ,,
Isn't that just blocking access to anything on the pfsense box?
-
@cburbs That is not how it works.
The packet has a source, and a destination.
When the packet goes to the internet, the any is the destination, let's say google DNS for an example, so the destination is this case would be 8.8.8.8;
The firewall would see a packet going to 8.8.8.8, and not to the firewall itself.That "Block to firewall" rule, is to block users from reaching the firewall itself, and not to block users to go through it..
If the firewall is the destination of the packet, the pfsense GUI for an example, that "Block to Firewall" rule would block it
-
Ok I looked at one of your earlier posts -
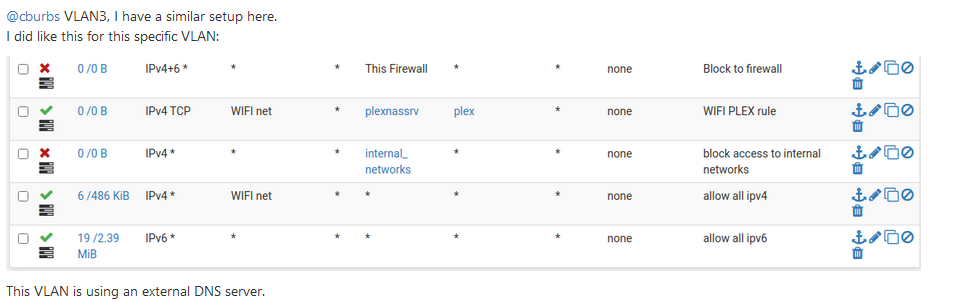
Saw your note about DNS - That was my issue no DNS being used.
So let's back track for a moment -
These items I want on Internet Only Vlans I still want to protect them in a sense.- would still like to use the DNS resolver I am using on the main Lan
- Still want them also hitting pfblockerng as well
- Can't access other lan/vlan
Doable, strange, silly, odd?
-
@cburbs It would be like this:
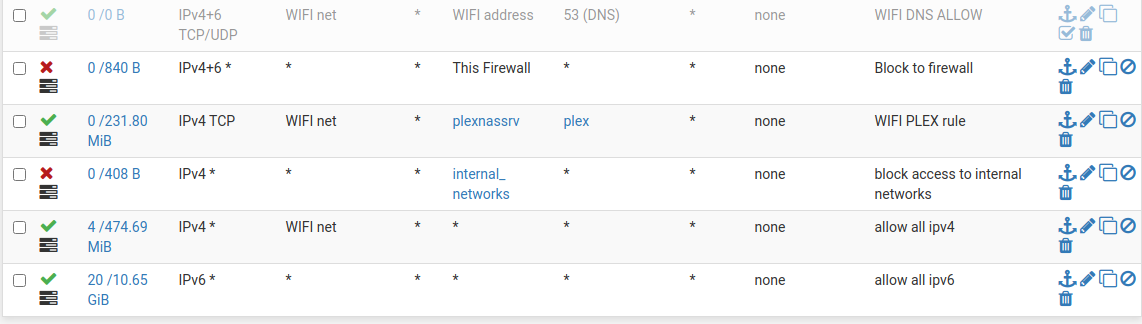
First rule is the DNS, in my case, it's disabled, but its only to show you, in your case, you would need to enable it.
First rule allows DNS to pfsense.
Second rule block everything to the firewall itself.
Third rule allows Plex from WIFI_NET to the plexnassrv in another vlan
4th rule blocks everything from this vlan to the other vlans
5th rule Internet allow ipv4
6th rule Internet allow ipv6