How renew date expiration of Certificate Authorities, OpenVpn Server Certificates and User Certificates in pfSense?
-
Hi everyone,
First, I want tell you that I haven't experience with certificates.
I have a pfSense 2.4.5-RELEASE-p1 with two Certificate Authorities that expire next year. These CA has been used to generate the certificates of two OpenVPN Servers and the Users Certificates that expire next year too.
Can I change or expand the expire date of the Certificate Authorities, OpenVpn Server Certificates and User Certificates in pfSense ?
If yes, how can I do this?
Best regards
-
@ramses-sevilla
Update to 2.5 before expiration:
https://github.com/pfsense/docs/blob/master/source/releases/2-5-0-new-features-and-changes.rst -
On 2.5.0 you can renew CA and certificate entries in-place. You will need to give new copies of the entries to the clients who need them, though, since the certs will be different, even if their content is the same (except the dates)
-
Hi,
I have a pfSense 2.4.5_1 with OpenVPN Server in production.
This pfSense have:
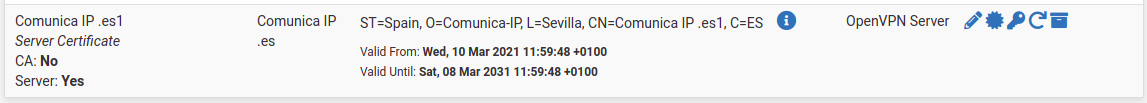
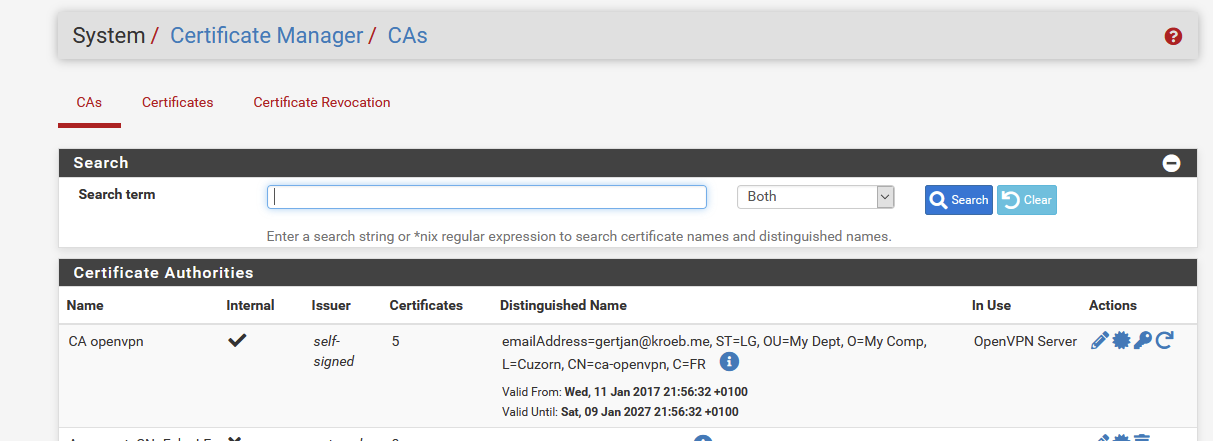
Certificate Authorities --> ca-prod-1 --> Valid from: 23 Apr 2020 --> Valid Until: 21 Apr 2030 (Internal) --> OpenVPN Server
Server Certificate (OpenVPN) --> srv-prod-1 --> Valid from: 23 Apr 2020 --> Valid Until: 21 Apr 2030
User Certificate --> usr-prod-1 --> Valid from: 23 Apr 2020 --> Valid Until: 21 Apr 2030
Certificate Authorities --> ca-prod-2 --> Valid from: 21 May 2002 --> Valid Until: 16 May 2022 (External) --> IPsec Tunnel
IPsec Tunnel --> ip-prod-2 --> Valid from: 18 Sep 2019 --> Valid Until: 16 May 2022 (External) --> IPsec Tunnel
What would happend if expire the CA, Certificate OpenVPN Server or User Certificates date?. Would it stop working the OpenVPN Server or could not connect the Users to the OpenVPN Server?
To update the expiration date of the CA and the certificates recommended me that update to pfSense 2.5.0
I have see in the forum that thre are some problems with the update to 2.5 with hardware (SuperServer 5018D-FN8T), IPsec and DHCP Relay that I use in my production environment.
I have updated to pfSense 2.5.0 a test environment to view the renew feature and I have some boubts:
-
If I renew the CA, would something stop working?
-
If I renew the Certificate OpenVPN Server, would something stop working?
-
If I renew the User Certificates, would something stop working?
As I said before, I haven't experience with certificates.
Sorry if my English is not very good.
Best regards
-
-
What you could do, without any risk :
Make a backup of the pfSense config.
Basically, no joke, but just did half of the work.Now : remove from every user in the user manager the certificate used for the VPN access.
When they are all removed from all the users, you can remove the 'per user' certificates.This is such a certificate :
Their will be a certificate per OpenVPN user.
When this is done, you can remove the "main" OpenVPN certificate that is based of the CA OpenVPN certificate.
This one :
Now, goto the CA tab and you will be able to remove the OpenVPN certificate.
This one :
Btw : these certificates are all "10 years" or so.
Now, same thing, in de reverse order.
Create a "OpenVPN" CA (on the CA tab).
Make a new "OpenVPN" certificate (on the Certificate tab).
Goto the User manager, and for every OpenVPN user, create/add a new certificate, based on the "OpenVPN" certificate.
Export a OpenVPN config file.
Test it for this one user.
Deploy the config files to all the users (and while doing so, check all the user install for the latest OpenVPN client version, etc etc).Something goes wrong ?
Just import the config backup - reboot - and your back where you started.Btw : this took more time to type as to do it.
True : it seems 2.5.0 add 'renews' all over the place. Didn't test them yet.
I'll give it a go in 2027 or so. -
@gertjan thanks so much by your answer.
Your solution has a problem for me and It is that I have over 300 OpenVpn Users.
I am looking for another solution that permit me renew the expire date of the CA, Server and User Certificates without stop working.
Is this possible?
How can I do?
Best regards
-
If you renew the CA but all the details stay the same it should continue to work, but in some cases you may have to copy the new CA to clients. Certificates will still see they are signed by the CA even after renewal since it's just renewed, not a different CA.
Server certificates (GUI, OpenVPN, mobile IPsec, etc) can be renewed at any time, those aren't copied to clients.
If you renew a user certificate you will have to copy the renewed certificate to the client, you can't avoid that.
There isn't a way to do batch operations like mass renew in the GUI or shell currently.
-
@jimp I am checking in a testing environment the renew certificate option in pfSense 2.5.0.
The CA Certificate renew, apparently, it does success.
The User Certificate renew, apparently, it does success.
But when I try renew the Server Certificate used by the OpenVPN server the following error is displayed:
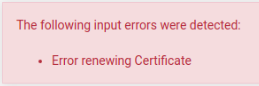
And I can't renew the Server Certificate used by the OpenVPN Server.
What could it be?
Best regards
-
I'm not aware of what might cause that general error. There may be some aspect of the certificate that is deprecated or no longer supported in OpenSSL for new certs. Hard to say without more details.
-
@jimp What more details do you need know about the server certificate?
The certificate were created in pfSense 2.4.5-p1, in the proccess of create the OpenVPN Server, before update to pfSense 2.5.0.
Regards
-
@ramses-sevilla
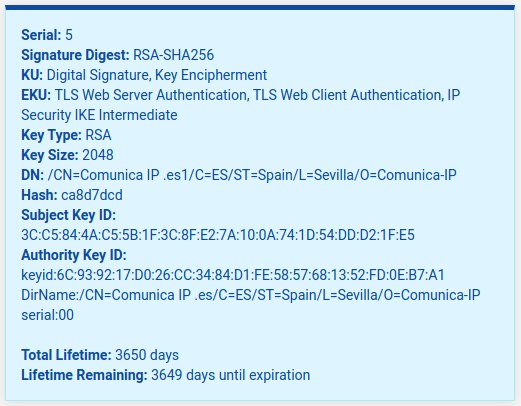
Aren't these valid like 'ten years' or so ?
See my image above. -
Yes, this server certificate is valid for ten years but I am testing the renew certificates option that has been introduced in pfSense 2.5.0 and I can renew de CA Certificate and the User Certificate but when I try to renew the OpenVPN Server Certificate the following error is displayed:
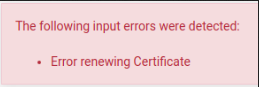
And I don't know why.
Best regards
-
@ramses-sevilla
Just a guess, but have you tried disabling the server before renewing the certificate? -
@ramses-sevilla said in How renew date expiration of Certificate Authorities, OpenVpn Server Certificates and User Certificates in pfSense?:
Yes, this server certificate is valid for ten years but I am testing the renew certificates option that has been introduced in pfSense 2.5.0 and I can renew de CA Certificate and the User Certificate but when I try to renew the OpenVPN Server Certificate the following error is displayed:
Can you share the details of the certificate as shown in the GUI list and info box (click the "i" icon)? Nothing I have tried has resulted in that error.
@provels said in How renew date expiration of Certificate Authorities, OpenVpn Server Certificates and User Certificates in pfSense?:
@ramses-sevilla
Just a guess, but have you tried disabling the server before renewing the certificate?That's not necessary, the renewal process will restart servers using the certificate afterward.
-
-
I have renewed all kinds of certificates, server and otherwise, in 2.5 and they all work for me. Which leads me to believe it's something in your certificate data triggering the problem.
Can you try adjusting the CN so it doesn't have a space in it?
Not that it should be a problem but typically that's a short name or hostname and not a string like that. I can't recall if I tested that sort of value.
-
It's definitely the space in the CN doing it. I can reproduce that here:
-
To adjust the CN I need create a new certificate, isn't it?
I can't modify the CN of the Server Certificate, isn't it?
The CA has space in the CN and renews the certificate without problem.
I have created a new certificate without spaces in the CN and renews fine.
Will the problem be solved?
Best regards
-
@ramses-sevilla said in How renew date expiration of Certificate Authorities, OpenVpn Server Certificates and User Certificates in pfSense?:
To adjust the CN I need create a new certificate, isn't it?
Yes, but since it's a server certificate which doesn't need to be sent to clients, that's typically easy, make a new cert, pick it to be used as the server cert, and that's it.
I can't modify the CN of the Server Certificate, isn't it?
Correct.
The CA has space in the CN and renews the certificate without problem.
That's expected as a CA is a different type of entry from a certificate, certificates have a lot more data in them and a lot more to go wrong.
Will the problem be solved?
Yes, I tracked it down further and the real problem is a lack of SAN entries in the certificate. Normally it will take the common name and add that as a SAN entry, but in these cases that kind of common name cannot be a valid SAN entry. The SAN list ends up empty since there are no manual entries nor the entry for the CN. The certificate renewal code was assuming all certificates have a SAN, which in these cases is not true.
You can install the System Patches package and then create an entry for
09d3fe621a56292817a85a54916e8b99e2b26c00to apply the fix. With that fix applied, you can renew certificates with spaces or x509-escaped characters in their CN which lack SANs. -
I have applied the patch and now I can renew the Server Certificate fine in my testing environment.
I have the production environment with a cluster in pfSense 2.4.5-p1. I had thought update to pfSense 2.5.0 because I need renew CA, Server and User Certificates but I have seen in the forum that the update to pfSense 2.5.0 break some services (Hardware, IPsec, DHCP Relay,...) that I have configured in my environment.
I have some doubts:
-
Do you recommends me wait to the next pfSense version?
-
Will all patches be included in the next version?
-
How long will it take to get out the next version?
-
Can I renew a Certificate without problems if It has expired?
Best regards
-