NTP - poor reach after 20 hours
-
@johnpoz
em0 - WAN
em1 - LAN
ovpnc4 (vpn provider) - OPT1. i have a few clients on LAN that use this as gateway.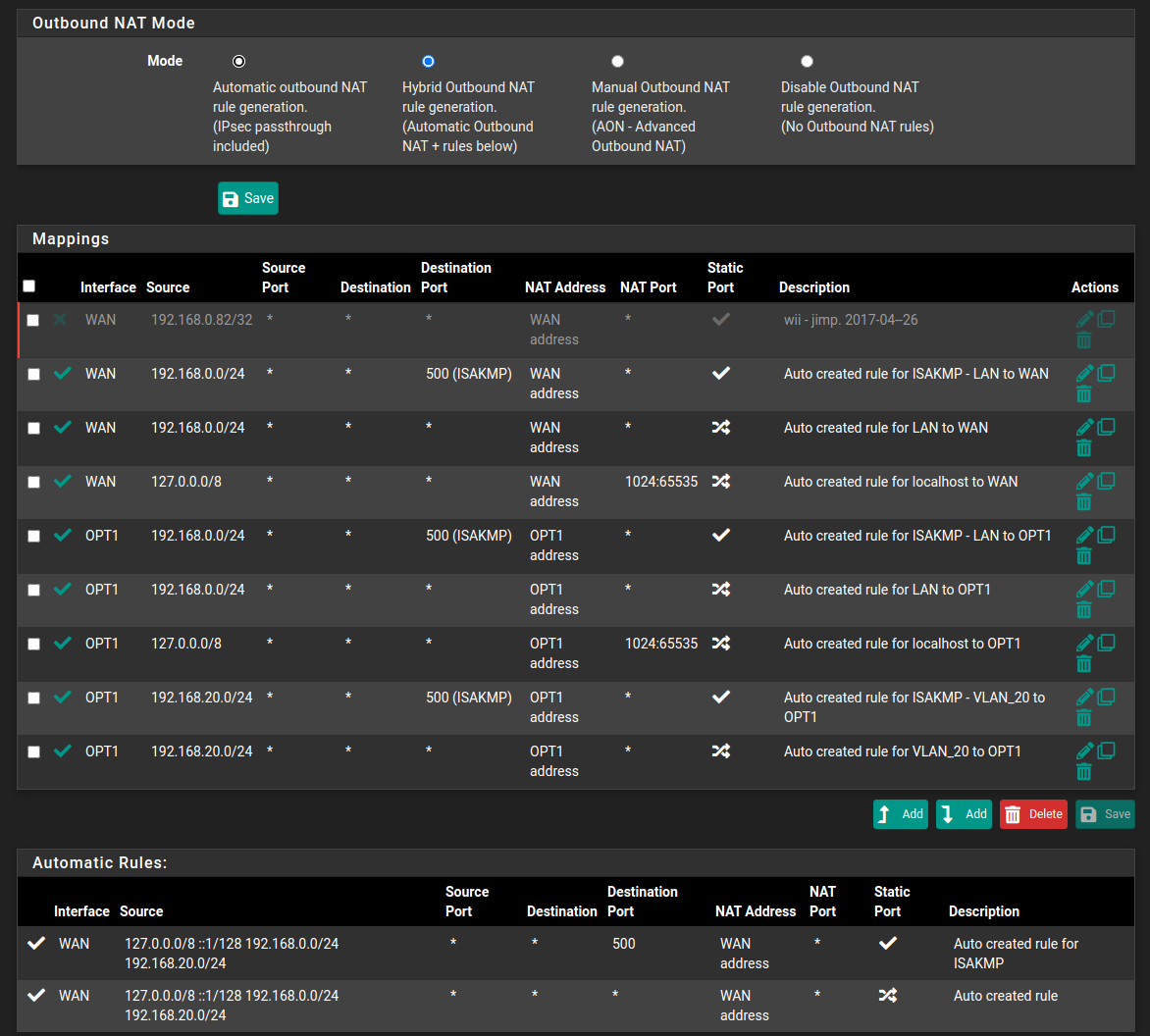
-
Turn all that off!
ok - disabled 1. VPN / client / my provider and 2. the LAN rule for OPT1 gateway (vpn_clients alias).
The NTP status seems to have suddenly improved after just 10 minutes. looks like will be all 377's in a few minutes! so what did I do wrong with my vpn client setup?
[2.5.1-RELEASE][admin@pfsense.home]/var/log: ntpq -p remote refid st t when poll reach delay offset jitter ============================================================================== +time.cloudflare 10.14.12.181 3 u 79 256 377 22.335 -1.920 0.680 -rolex.netservic 64.113.44.55 2 u 210 256 177 27.977 +1.981 1.938 +rb.steadfastdns 208.100.0.253 2 u 48 256 177 22.434 -1.686 4.161 -time.skylineser 130.207.244.240 2 u 120 256 177 25.379 -3.370 0.421 *n1.taur.dk .PPS. 1 u 36 256 177 131.326 -2.014 3.197 -
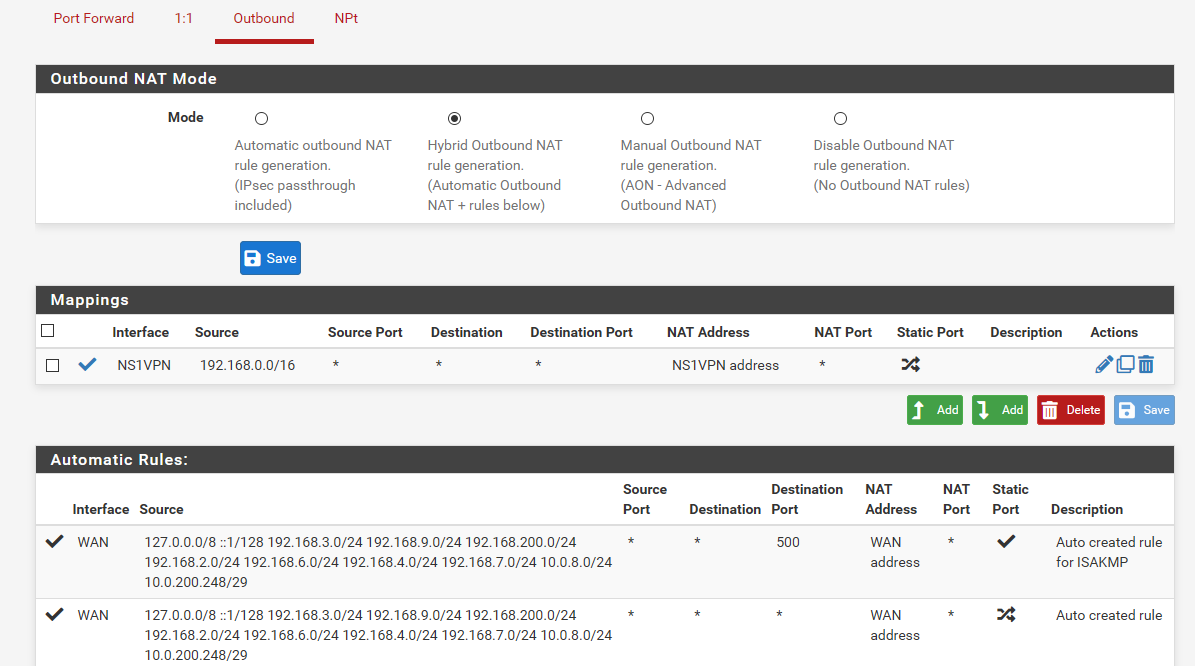
Why would you set this?
Or the other one for wan? for 127/8 ?
Not sure why you would set hybrid for something your doing in auto anyway?
edit: Did you setup a static on opt1 and set a gateway? Auto nat would of never created that unless it thought it was a normal wan connection, a gateway was put on it??
But it never would of set those ports? Really confused on how that would of be auto generated like the description says.
-
Did you setup a static on opt1 and set a gateway? Auto nat would of never created that unless it thought it was a normal wan connection, a gateway was put on it??
no static routes. here are the Gateways.
-
@johnpoz
Regarding NAT rules, I copied the wan rules and adjusted for OPT1 according to vpn provider's instructions. -
@farmerjohn said in NTP - poor reach after 20 hours:
according to vpn provider's instructions.
And what clueless vpn was this? Do you have a guide you followed?
Yah normally need just 1 hybrid rule ;)
edit:
BTW.. Even if you wanted to send other traffic down a vpn connection from pfsense - your dns for example. If wouldn't ever be a good idea to try an do ntp through a vpn connection. -
@johnpoz
Travelling for next few days, will try your example when get back. Thank you. -
@johnpoz
I like the simplicity of your example, how would I get there from my current setup? Just delete All my NAT rules - clean slate? -
Yeah just delete all those hybrids you have.. No idea why any guide would say you need those.. Especially those with specific ports 1024:65k
What guide did you follow?
Also the other thing pretty much every vpn service guide I have looked at wants you to route everything through them.. When most likely you don't want that.. Don't pull routes in your client config, and then just policy route what "you" want to send down the vpn. Which could be all if you want, but ntp down a vpn is going to be a horrible setup.
-
@johnpoz
I deleted all the Outbound NAT rules and added one as you suggested. I also disabled 'pull routes' in client config. Everything working well so far and NTP status is still showing 377's for the five individual servers.I presently have 1.1.1.1 and 9.9.9.9 in System > general > DNS servers. Leak tests showing VPN public IP (good) and DNS servers as cloudflare and quad9 (should I care? Is it cloudflare trust vs VPN provider trust?). Here are my DNS Resolver settings in case I'm wrong/confused on something.