OpenVPN site to site NAT
-
Hi guys
Im having a problem with network configuration.
Our company is moving and we cant keep our public ip.
But we have many services talking to it so i decided to keep pfsense box in old place and build new one for other location.And here is my current situation. I have successfully created OpenVPN tunnel. and can talk between endpoints.
What i want to achieve is to NAT traffic form wan 2.2.2.2 (AKA PfsenseA) to server on 192.168.10.182
What i do not want to do is to route all traffic from site b trough site a.
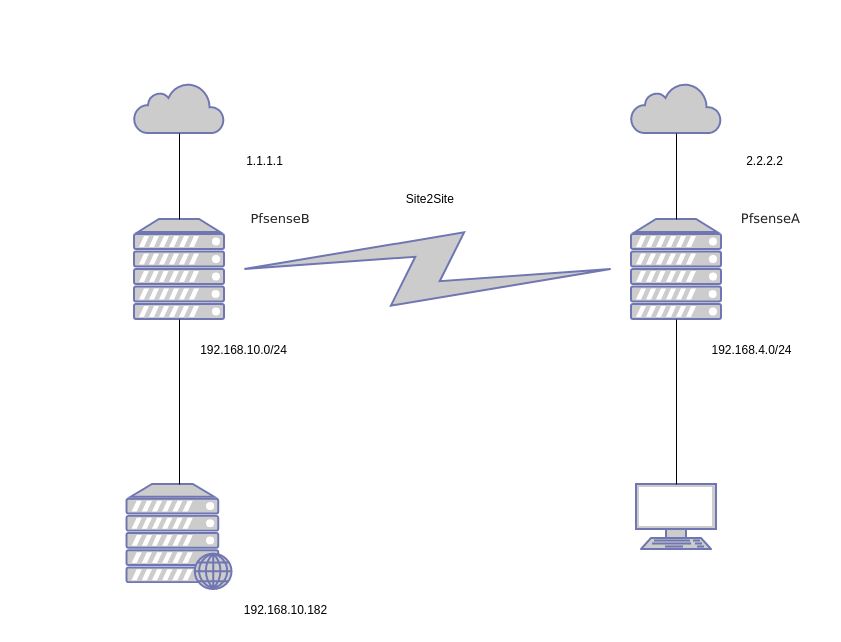
I hope i made my problem clear.
Thanks in advance for any tips how to solve this problem. -
@kryq said in OpenVPN site to site NAT:
Our company is moving and we cant keep our public ip.
But we have many services talking to itSo these services use the IP, not a host name, I assume?
Would be better to use host names, so you simply would have to change the IP in the DNS in this situation.Consider that the VPN increaes the latency. So I don't recommend to use this as persistent solution.
If you have multiple WAN connections on site B and don't need encryption, you can simply forward the traffic from A to B. If you can use A as default gateway on B this would also work with a single WAN.
-
@viragomann I don't really care about latency of remote connection.
And i can't really convert them to hostname anymore.
How can i achieve forwarding on pfsense ?
I tried with following rule and it doesn't seem to work (im testing on port 12121)on 192.168.1.182
nc -l -p 12121and on remote client
nc 2.2.2.2 12121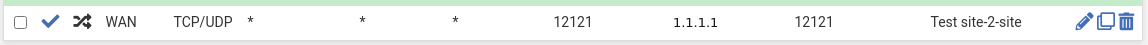
Im assuming i would need to create nat rules on pfsenseb but there isnt any blocked traffic to begin with
-
@kryq
Before you start, it doesn't work on pfSense CE 2.5.1 (at site B) due to a bug.Basically if your OpenVPN tunnel is up you need to assign an interface to the OpenVPN instance at B.
Then you can simply change the target IP in the NAT rule at A to 192.168.1.182 to forward the traffic.At B you have to remove firewall rules from the OpenVPN tab and add rules for allowing the packets from the other site on the VPN interface you have assigned to the connection before.
Also ensure that there is no floating pass rule matching that traffic. -
@viragomann your solution doesn't work on pf 2.5.1 or only mine attempt on forwarding wont work?
would upgrading to 2.5.2 fix this error?
-
@kryq
2.5.1 has a bug which causes that replies always go to the default gateway, regardless which interface the respective requests came in. But replies on packet which were forwarded from A need to go back A, otherwise you will run into an asymmetric routing issue.Yes, it will work on 2.5.2 and as well as on 2.5.0.
As a workaround when running 2.5.1 you can S-NAT the traffic on A, if this is an option for you.
-
@viragomann Ok i got it working.
It took some cleaning up after previous attempts and I wouldn't make it work if it wasn't for you info.
Thanks