Pfsense only OpenVPN Server with only single interface WAN
-
Hi, I installed pfsense in a server's Hyper-V virtual machine by assigning only the WAN interface.
I have configured OpenVPN Server for remote client access. The connection between the client and the VPN server works perfectly, but I can only remotely connect to the pfsense webgui: how can I connect to all the clients on the LAN of the VPN server?
in practice I would like to use pfsense only as a VPN server to allow access from outside to my LAN. it's possible?
thanks -
Hi,
basically that's possible in fact, but since your LAN devices use another upstream gateway than pfSense they will send responses to requests from a vpn client not back to pfSense.Best practice is to set up a transit network between the default gateway and pfSense and add a static route for the vpn tunnel network to the gateway to route vpn responses back.
If this is not an option for you, you either have to set a static route to each of your LAN devices for the vpn tunnel network pointing to pfSense or do masquerading (S-NAT) on pfSense and translate vpn source IPs to the pfSense LAN IP.
-
Best practice is to set up a transit network between the default gateway and pfSense and add a static route for the vpn tunnel network to the gateway to route vpn responses back.
Thanks for the reply. can you give me a guide to do this? or can you tell me specifically where I have to see?
I have been using pfsense recently and am not very experienced.for example I found this tips for linux that should do for me, I would like to understand how to replicate the thing in pfsense
-
What do want to do? I gave you three options.
I assume, the vpn is only for your own management purposes. So I would prefer the NAT method, which is the easiest to set up, but has disadvantages when you have multiple vpn users.
So you need an outbound NAT rule translating the source address of vpn packets to the interface address which is facing to your destination devices:To set it up, go to NAT > Outound, switch to hybrid mode, save this and add a new NAT rule:
Interface: WAN
Source: <openvpn tunnel="" network="">Destination: any
Tranlation: interface address</openvpn> -
thanks for the reply, I have configured the firewall and it works perfectly: D: D
-
Hello,
I have similar problem.
Can you help me ????
I have setup PFSENSE on GOOGLE CLOUD with only 1 WAN interface.
I want connect my remote office Pfsense with OpenVPN
I can connect to Google Cloud PFSENSE Web interface
OpenVPN connect between two PFSENSE and PING between PFSENSE work well but no communication with google internal address (10.142.0.xxx)
Only can ping (10.142.0.7) but i want ping (10.142.0.2) it's fail.
If I'm go in Google Cloud PFSENSE "Diagnostics" Menu and choose "Ping" it's work if choose Interface WAN for ping (10.142.0.2) but fail with interface OPENVPN
My Setup :
Google Cloud PFSENSE
HTTPS - 35.237.xx.xx (Google Cloud - PFSENSE WEB INTERFACE)
10.142.xx.xx/20 (Google Cloud WAN Internal IP)
OPENVPN IP (192.168.50.0/24)Remote Office PFSENSE
WAN IP (208.135.xx.xx/24)
LAN IP (192.168.9.1)
OPENVPN IP (192.168.50.0/24)Can you help me please ?
-
Hi,
your problem is presumably also the vpn endpoint which is not the default gateway in its local network. Above I mentioned three ways to solve that issue:
- Best: set up a transit network instead of LAN between pfSense and your default gateway. So you can add a route to the default gateway to direct packets meant to the remote site to the vpn endpoint.
- Add a static route for the remote network to each of the local device.
- Use outbound NAT on pfSense to masquerade the source address by the pfSense local address.
Using this method you will not be capable to determine the real source on the destination device. If that's no issue for you, that will be the easiest solution.
-
Ok!
Can you just point me in right direction for this, pfsense menu or …
i'm searching it since one Week and i'm bit confuse now…For set up transit network i'm need to create a new Gateway ?
Thx for you help !
-
No, you have to set up a separate network (VLAN) between your existing gateway and the pfSense vm. I don't know if that is possible on the gateway. If not you have to choose another option.
Give both devices an IP in that network.
On pfSense you have to deactivate the Outbound NAT.Than if the vpn is a site-to-site, add a static route to your default gateway on Google cloud for the remote LAN pointing to the new WAN address of pfSense. If it is a remote access vpn you have to set the route for the tunnel network.
BTW: If it is a site-to-site, the tunnel network mask has to be a /30.
-
Sorry but i'm very confuse… :-(
If I give you access to you on my PFSENSE WEB interface on Google cloud can you help me ?
-
I'm not familiar with Google cloud. Is there a virtual environment with an internet gateway, where you're able to add virtual network interfaces and internal networks?
If that is not possible take another solution.
-
I have only network card on my pfsense VM with google cloud.
Google cloud NAT public IP directly on private IP.
Can access to PFSENSE WEB with public IP and WAN IP in console is private IP
I install PFSENSE with this guide … https://blog.kylemanna.com/cloud/pfsense-on-google-cloud/
for other method can you explain more please ?
-
The crux of the matter is the gateway here for this solution. If you cannot configure it, that won't work.
So let's try the NAT solution.
That is assuming that all settings are like you wrote in your first post here.
For this one you have to enable the Outbound NAT in the pfSense web-GUI. Firewall > NAT > Outbound. Select the hybrid mode and save that.
Add a new rule:
Interface: WAN
Source: any
Destination: 10.142.xx.xx/20 (the Google Cloud local network)
Translation address: Interface addressThat should work if the vpn is configured correctly.
-
Thx it's work now ! :-)
-
Hello,
I'm new with pfsense, and for now I need it only because OpenVPN.I installed it to some cloud, also only with one interface for wan.
Because there is no possibility on that hosting to put few servers in the same vlan, I wan't to try with OpenVPN.Is it possible only with bridging? I googled so much these days, and found only this 6 years old guide
https://hardforum.com/threads/pfsense-2-0-1-openvpn-configuration-guide.1663797/
but it seems like it is obsolete.
Also in netgate documentation there is this link
https://www.netgate.com/docs/pfsense/vpn/openvpn/openvpn-bridging.html
which also not works because it is "irrelevant" for current pfsense version.Can you direct me how to make possible to put different cloud standalone servers to the same vlan?
-
There should exist smaller solutions for OpenVPN only.
You can get access by a transit network and routing if you have access to the default gateway, as already mentioned here. Or by adding a route to each remote device you want to reach or by NAT.
Also by bridging, in theory, but my experience tells me, that you will not get much support here for bridged openVPN, but you may try a new thread.
I can't help. -
Hi I am trying to do the same thing, could you share a screenshot of younnat config for this?
Thanks
-
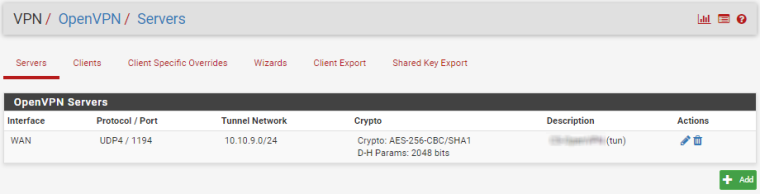
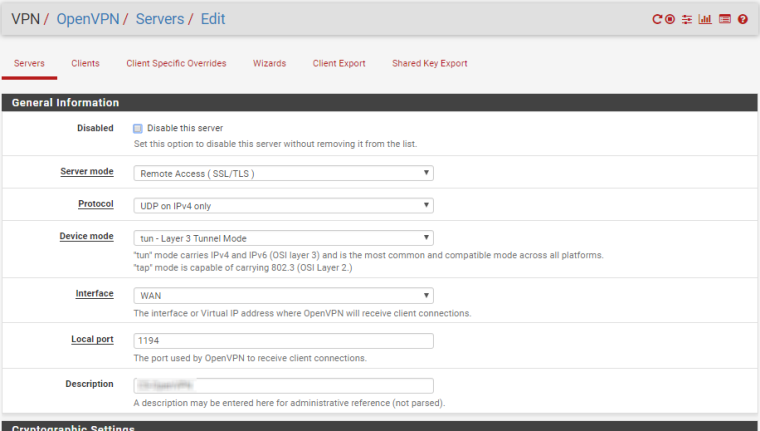
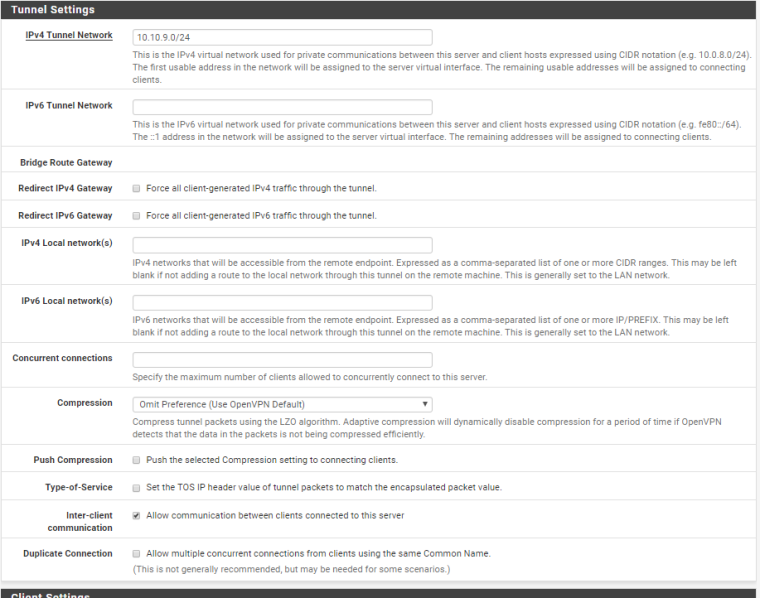
Hello, I succeeded to setup on cloud with one WAN openvpn and connect devices from different places to one network.
ISP is Hetzner.
This is the configuration if someone need. Mostly done via Wizards, with small corrections afterwards.
Still need a little bit to harden firewall.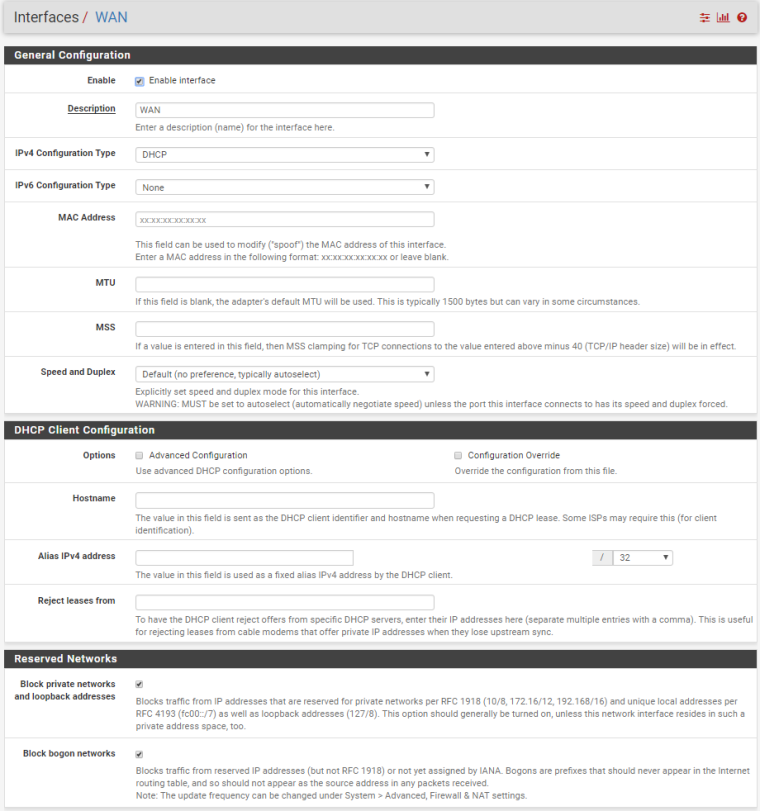
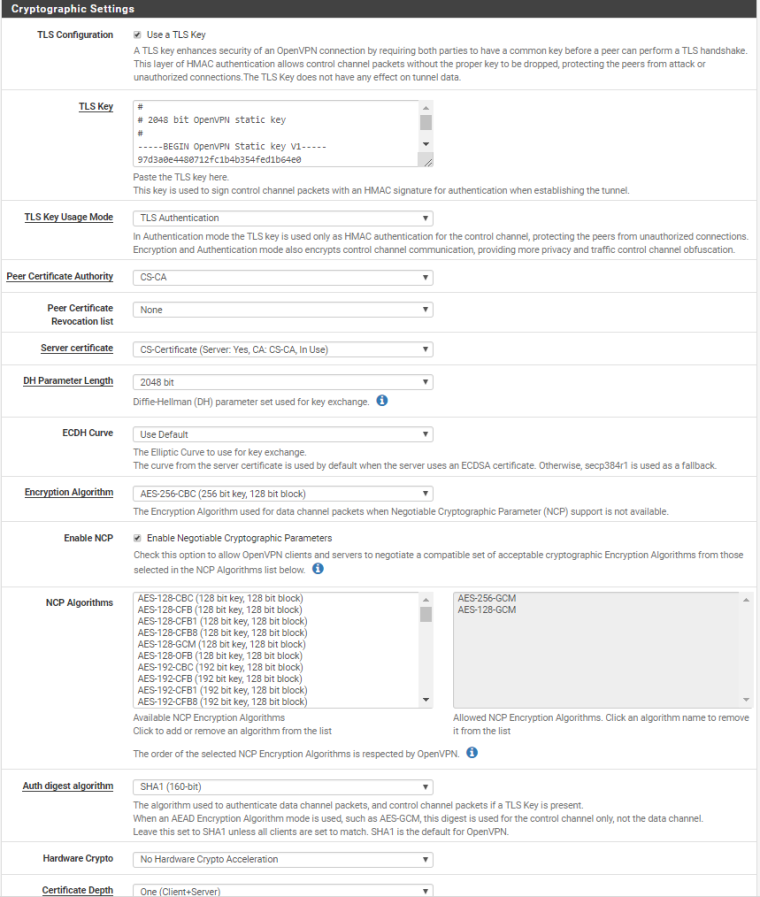


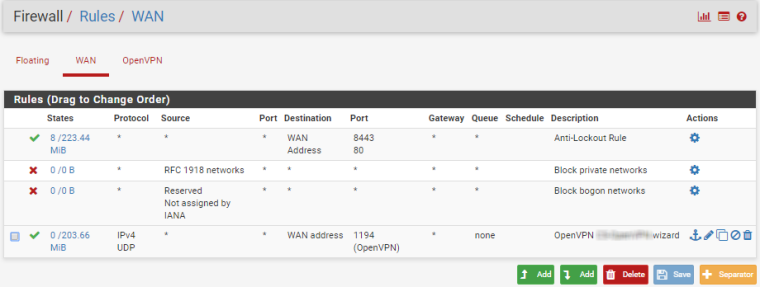
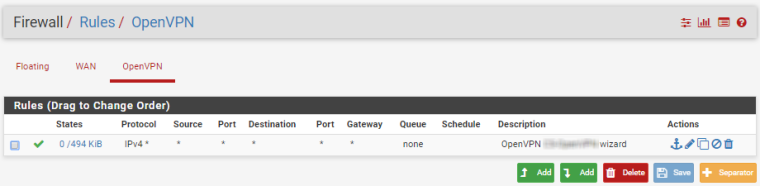
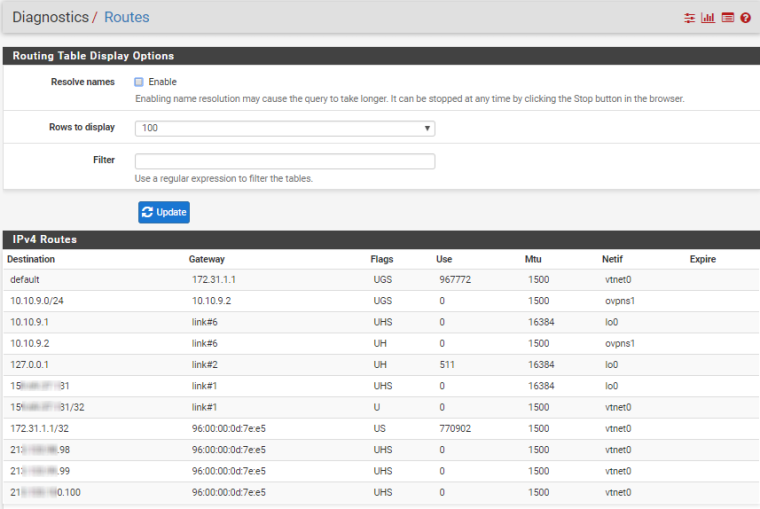
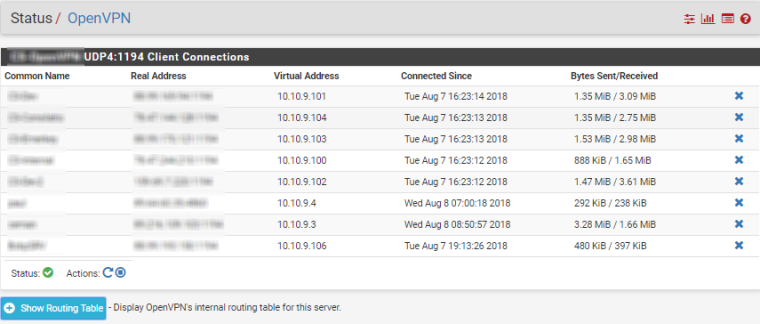
-
Hello again ! :-)
I'm setup PFSENSE (1 WAN nic) on google cloud with 6 pfsense (client) connected site-to-site, all client can PING my google cloud network 10.142.x.x/20
But when connect to my server on my google cloud 10.142.x.4 i'm can't PING my local network client ….
If i'm connect on pfsense GUI (server-side) 10.142.x.7 and make PING test on my internal local client 10.10.5.249 it's WORK !!!!
pfsense server 10.142.0.7
google cloud server 10.242.0.4pfsense client 10.10.5.1
Workstation client 10.10.5.249ping from 10.10.5.249 to 10.142.0.7 ---- WORK
ping from 10.10.5.249 to 10.142.0.4 ---- WORKping from 10.142.0.7 to 10.10.5.249 ----- WORK
ping from 10.142.0.4 to 10.10.5.249 ----- FAILTraffic fail on one side … can you help me whit my route table please….
THX !!!!
-
@n1tr0666 said in Pfsense only OpenVPN Server with only single interface WAN:
I'm setup PFSENSE (1 WAN nic) on google cloud with 6 pfsense (client) connected site-to-site
6 site-to-site clients are connected to a single server? With CSO?
@n1tr0666 said in Pfsense only OpenVPN Server with only single interface WAN:
ping from 10.142.0.4 to 10.10.5.249 ----- FAIL
You have to tell the cloud server where to go to reach 10.10.5.249. Add a static route to it for the network of 10.10.5.249 and direct it to pfSense 10.142.0.7.