I need HELP on DNS RESOLVER!
-
@emirefek said in I need HELP on DNS RESOLVER!:
ubnt.i.lithium.com"
Did another test just now :
Flushed dns on my PC.
Flushed Resolver cache (by setting log details to level 2).
On my PC :C:\Documents and Settings\Gertjan.BUREAU>ipconfig /flushdns Configuration IP de Windows Cache de résolution DNS vidé. C:\Documents and Settings\Gertjan.BUREAU>nslookup Serveur par dÚfaut : pfsense.brit-hotel-fumel.net Address: 192.168.1.1 > ubnt.i.lithium.com Serveur : pfsense.brit-hotel-fumel.net Address: 192.168.1.1 Réponse ne faisant pas autorité : Nom : cs71.wac.edgecastcdn.net Address: 93.184.220.97 Aliases: ubnt.i.lithium.com.This is what pfSense told me (read from bottom to top) :
09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: query response was nodata ANSWER 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: reply from <lithium.com.> 208.74.204.2#53 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: response for ns4.lithium.com. AAAA IN 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: Verified that unsigned response is INSECURE 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: NSEC3s for the referral proved no DS. 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: Verified that unsigned response is INSECURE 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: NSEC3s for the referral proved no DS. 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: query response was ANSWER 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: reply from <edgecastcdn.net.> 72.21.80.6#53 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: response for ubnt.i.lithium.com. A IN 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: query response was REFERRAL 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: reply from <net.> 2001:503:231d::2:30#53 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: response for ubnt.i.lithium.com. A IN 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: query response was nodata ANSWER 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: reply from <lithium.com.> 208.94.148.13#53 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: response for ns5.lithium.com. AAAA IN 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: resolving net. DNSKEY IN 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: resolving ubnt.i.lithium.com. A IN 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: query response was CNAME 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: reply from <lithium.com.> 208.80.124.13#53 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: response for ubnt.i.lithium.com. A IN 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: resolving ns4.lithium.com. AAAA IN 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: resolving ns5.lithium.com. AAAA IN 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: query response was REFERRAL 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: reply from <com.> 192.43.172.30#53 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:46 unbound: [96547:0] info: response for ubnt.i.lithium.com. A IN 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:45 unbound: [96547:0] info: resolving com. DNSKEY IN 09-11-2018 17:12:44 Daemon.Info 192.168.1.1 Sep 11 17:12:45 unbound: [96547:0] info: resolving ubnt.i.lithium.com. A INLooks good to me. Not sure when reading the logs, but nslookup on my PC gave an answer.
Check if you have the same.
If some device (PC) doesn't show DNS logs on pfSense, then that device has no DNS (so : no answer!) or that device doesn't use pfSense as a DNS. -
They do have a bit of a problem to be honest with their setup... So the roots for .net only show 2 NS for that domain
dig @e.gtld-servers.net edgecastcdn.net NS ; <<>> DiG 9.9.5-3ubuntu0.17-Ubuntu <<>> @e.gtld-servers.net edgecastcdn.net NS ; (2 servers found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 16422 ;; flags: qr rd; QUERY: 1, ANSWER: 0, AUTHORITY: 2, ADDITIONAL: 5 ;; WARNING: recursion requested but not available ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;edgecastcdn.net. IN NS ;; AUTHORITY SECTION: edgecastcdn.net. 172800 IN NS ns1.edgecastcdn.net. edgecastcdn.net. 172800 IN NS ns2.edgecastcdn.net. ;; ADDITIONAL SECTION: ns1.edgecastcdn.net. 172800 IN AAAA 2606:2800:1::5 ns1.edgecastcdn.net. 172800 IN A 72.21.80.5 ns2.edgecastcdn.net. 172800 IN AAAA 2606:2800:1::6 ns2.edgecastcdn.net. 172800 IN A 72.21.80.6 ;; Query time: 17 msec ;; SERVER: 2001:502:1ca1::30#53(2001:502:1ca1::30) ;; WHEN: Tue Sep 11 12:39:14 CDT 2018 ;; MSG SIZE rcvd: 168But if you ask the SOA for that domain for its NS.. you get back 4 of them.
dig @ns1.edgecastcdn.net edgecastcdn.net NS ; <<>> DiG 9.9.5-3ubuntu0.17-Ubuntu <<>> @ns1.edgecastcdn.net edgecastcdn.net NS ; (2 servers found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 22695 ;; flags: qr aa rd; QUERY: 1, ANSWER: 4, AUTHORITY: 0, ADDITIONAL: 9 ;; WARNING: recursion requested but not available ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;edgecastcdn.net. IN NS ;; ANSWER SECTION: edgecastcdn.net. 3600 IN NS ns1.edgecastcdn.net. edgecastcdn.net. 3600 IN NS ns2.edgecastcdn.net. edgecastcdn.net. 3600 IN NS ns3.edgecastcdn.net. edgecastcdn.net. 3600 IN NS ns4.edgecastcdn.net. ;; ADDITIONAL SECTION: ns1.edgecastcdn.net. 172800 IN AAAA 2606:2800:1::5 ns2.edgecastcdn.net. 172800 IN AAAA 2606:2800:1::6 ns3.edgecastcdn.net. 3600 IN AAAA 2606:2800:e::5 ns4.edgecastcdn.net. 3600 IN AAAA 2606:2800:e::6 ns1.edgecastcdn.net. 172800 IN A 72.21.80.5 ns2.edgecastcdn.net. 172800 IN A 72.21.80.6 ns3.edgecastcdn.net. 3600 IN A 192.229.254.5 ns4.edgecastcdn.net. 3600 IN A 192.229.254.6 ;; Query time: 10 msec ;; SERVER: 2606:2800:1::5#53(2606:2800:1::5) ;; WHEN: Tue Sep 11 12:41:52 CDT 2018 ;; MSG SIZE rcvd: 292This really shoudn't stop you from resolving - but it does reflect a lack of proper dns control..
Did you run the dig +trace command pfsense?
[2.4.3-RELEASE][root@sg4860.local.lan]/: dig cs71.wac.edgecastcdn.net +trace +nodnssec ; <<>> DiG 9.11.2-P1 <<>> cs71.wac.edgecastcdn.net +trace +nodnssec ;; global options: +cmd . 485599 IN NS f.root-servers.net. . 485599 IN NS d.root-servers.net. . 485599 IN NS i.root-servers.net. . 485599 IN NS g.root-servers.net. . 485599 IN NS c.root-servers.net. . 485599 IN NS e.root-servers.net. . 485599 IN NS l.root-servers.net. . 485599 IN NS h.root-servers.net. . 485599 IN NS k.root-servers.net. . 485599 IN NS j.root-servers.net. . 485599 IN NS m.root-servers.net. . 485599 IN NS a.root-servers.net. . 485599 IN NS b.root-servers.net. ;; Received 239 bytes from 127.0.0.1#53(127.0.0.1) in 0 ms net. 172800 IN NS a.gtld-servers.net. net. 172800 IN NS b.gtld-servers.net. net. 172800 IN NS c.gtld-servers.net. net. 172800 IN NS d.gtld-servers.net. net. 172800 IN NS e.gtld-servers.net. net. 172800 IN NS f.gtld-servers.net. net. 172800 IN NS g.gtld-servers.net. net. 172800 IN NS h.gtld-servers.net. net. 172800 IN NS i.gtld-servers.net. net. 172800 IN NS j.gtld-servers.net. net. 172800 IN NS k.gtld-servers.net. net. 172800 IN NS l.gtld-servers.net. net. 172800 IN NS m.gtld-servers.net. ;; Received 846 bytes from 2001:500:1::53#53(h.root-servers.net) in 106 ms edgecastcdn.net. 172800 IN NS ns1.edgecastcdn.net. edgecastcdn.net. 172800 IN NS ns2.edgecastcdn.net. ;; Received 177 bytes from 192.5.6.30#53(a.gtld-servers.net) in 39 ms cs71.wac.edgecastcdn.net. 3600 IN A 72.21.91.97 ;; Received 69 bytes from 72.21.80.5#53(ns1.edgecastcdn.net) in 11 ms [2.4.3-RELEASE][root@sg4860.local.lan]/:This will tell you if pfsense would have a problem with resolving it.. I added the +nodnssec option to make the trace look cleaner - ie not include the dnssec info that roots and .net servers hand out
-
Things didn't get any better this morning : https://zonemaster.iis.se/?resultid=87deb85f04a58f9e
@emirefek : what about testing google.com *** ? So we can focus on your issues, not the one of the guy with severe DNS problems ?
*** well, maybe google.com isn't perfect neither. This one is.
-
@johnpoz
I typed your commands one by one and these are my outputs. And all outs from pfsense boxes comand promptdig @e.gtld-servers.net edgecastcdn.net NS
; <<>> DiG 9.11.2-P1 <<>> @e.gtld-servers.net edgecastcdn.net NS ; (2 servers found) ;; global options: +cmd ;; connection timed out; no servers could be reacheddig @ns1.edgecastcdn.net edgecastcdn.net NS
dig: couldn't get address for 'ns1.edgecastcdn.net': not founddig cs71.wac.edgecastcdn.net +trace +nodnssec
; <<>> DiG 9.11.2-P1 <<>> cs71.wac.edgecastcdn.net +trace +nodnssec ;; global options: +cmd . 24997 IN NS m.root-servers.net. . 24997 IN NS g.root-servers.net. . 24997 IN NS a.root-servers.net. . 24997 IN NS j.root-servers.net. . 24997 IN NS l.root-servers.net. . 24997 IN NS d.root-servers.net. . 24997 IN NS k.root-servers.net. . 24997 IN NS b.root-servers.net. . 24997 IN NS i.root-servers.net. . 24997 IN NS h.root-servers.net. . 24997 IN NS c.root-servers.net. . 24997 IN NS f.root-servers.net. . 24997 IN NS e.root-servers.net. ;; Received 811 bytes from 127.0.0.1#53(127.0.0.1) in 0 ms ;; connection timed out; no servers could be reachedthese are my results. I dont know but I cannot solve that damn domain.
And little info my setup on vmware esxi with pppoe -
@Gertjan I can solve this domain mate. This output from pfsense box.
dig test-domaine.fr
; <<>> DiG 9.11.2-P1 <<>> test-domaine.fr ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 38644 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;test-domaine.fr. IN A ;; ANSWER SECTION: test-domaine.fr. 10092 IN A 5.196.43.182 ;; Query time: 0 msec ;; SERVER: 127.0.0.1#53(127.0.0.1) ;; WHEN: Fri Sep 14 12:56:48 +03 2018 ;; MSG SIZE rcvd: 60 -
Logic
 I'm the DNS administrator of that domain.
I'm the DNS administrator of that domain.But your test tells me that your Resolver (DNS) works fine.
For what it's worth : when you setup pfSense (that is : assign LAN, WAN) and then you set up your WAN interface any device on your LAN should be able to access the net with any troubles.
Initially : do not touch firewall rules, VLAN's, DNS, nothing.Btw : again : you are not responsible for not resolving of sub domains. The fact that something works on this side of the planet doesn't mean it isn't broken on your side.
Seek contact with the guy that manages ubnt.i.lithium.com - or put in a DNS host over ride. -
looks to me like you can not talk to roots..
-
@johnpoz I can talk with blabla.root-servers.net. I try 5 or 6 of them with random choose.
-
Then why does your trace not get an answer back ??
You should of gotten back the next level - the NS for .net when you did your trace..
example
net. 172800 IN NS k.gtld-servers.net.
net. 172800 IN NS l.gtld-servers.net.
net. 172800 IN NS m.gtld-servers.net.
;; Received 846 bytes from 2001:500:1::53#53(h.root-servers.net) in 106 msMine talked via ipv6 when I did the trace - but ipv4 would do the same thing.. You just stopped at roots..
How did you test talking to them - a ping or an actual dns query?
example
C:\>dig @m.root-servers.net net NS ; <<>> DiG 9.12.2 <<>> @m.root-servers.net net NS ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 23008 ;; flags: qr rd; QUERY: 1, ANSWER: 0, AUTHORITY: 13, ADDITIONAL: 27 ;; WARNING: recursion requested but not available ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;net. IN NS ;; AUTHORITY SECTION: net. 172800 IN NS m.gtld-servers.net. net. 172800 IN NS i.gtld-servers.net. net. 172800 IN NS a.gtld-servers.net. net. 172800 IN NS h.gtld-servers.net. net. 172800 IN NS k.gtld-servers.net. net. 172800 IN NS b.gtld-servers.net. net. 172800 IN NS c.gtld-servers.net. net. 172800 IN NS l.gtld-servers.net. net. 172800 IN NS g.gtld-servers.net. net. 172800 IN NS d.gtld-servers.net. net. 172800 IN NS j.gtld-servers.net. net. 172800 IN NS f.gtld-servers.net. net. 172800 IN NS e.gtld-servers.net. ;; ADDITIONAL SECTION: a.gtld-servers.net. 172800 IN A 192.5.6.30 b.gtld-servers.net. 172800 IN A 192.33.14.30 c.gtld-servers.net. 172800 IN A 192.26.92.30 d.gtld-servers.net. 172800 IN A 192.31.80.30 e.gtld-servers.net. 172800 IN A 192.12.94.30 f.gtld-servers.net. 172800 IN A 192.35.51.30 g.gtld-servers.net. 172800 IN A 192.42.93.30 h.gtld-servers.net. 172800 IN A 192.54.112.30 i.gtld-servers.net. 172800 IN A 192.43.172.30 j.gtld-servers.net. 172800 IN A 192.48.79.30 k.gtld-servers.net. 172800 IN A 192.52.178.30 l.gtld-servers.net. 172800 IN A 192.41.162.30 m.gtld-servers.net. 172800 IN A 192.55.83.30 a.gtld-servers.net. 172800 IN AAAA 2001:503:a83e::2:30 b.gtld-servers.net. 172800 IN AAAA 2001:503:231d::2:30 c.gtld-servers.net. 172800 IN AAAA 2001:503:83eb::30 d.gtld-servers.net. 172800 IN AAAA 2001:500:856e::30 e.gtld-servers.net. 172800 IN AAAA 2001:502:1ca1::30 f.gtld-servers.net. 172800 IN AAAA 2001:503:d414::30 g.gtld-servers.net. 172800 IN AAAA 2001:503:eea3::30 h.gtld-servers.net. 172800 IN AAAA 2001:502:8cc::30 i.gtld-servers.net. 172800 IN AAAA 2001:503:39c1::30 j.gtld-servers.net. 172800 IN AAAA 2001:502:7094::30 k.gtld-servers.net. 172800 IN AAAA 2001:503:d2d::30 l.gtld-servers.net. 172800 IN AAAA 2001:500:d937::30 m.gtld-servers.net. 172800 IN AAAA 2001:501:b1f9::30 ;; Query time: 77 msec ;; SERVER: 202.12.27.33#53(202.12.27.33) ;; WHEN: Fri Sep 14 08:03:45 Central Daylight Time 2018 ;; MSG SIZE rcvd: 825 -
@johnpoz said in I need HELP on DNS RESOLVER!:
@m.root-servers.net net NS
This output from my pfsense box. But I cannot talk it from my centos server and Im sure my centos dns settings are pointing my pfsense box.
dig @m.root-servers.net net NS
; <<>> DiG 9.11.2-P1 <<>> @m.root-servers.net net NS ; (2 servers found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 10472 ;; flags: qr rd; QUERY: 1, ANSWER: 0, AUTHORITY: 13, ADDITIONAL: 27 ;; WARNING: recursion requested but not available ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;net. IN NS ;; AUTHORITY SECTION: net. 172800 IN NS l.gtld-servers.net. net. 172800 IN NS b.gtld-servers.net. net. 172800 IN NS h.gtld-servers.net. net. 172800 IN NS i.gtld-servers.net. net. 172800 IN NS d.gtld-servers.net. net. 172800 IN NS e.gtld-servers.net. net. 172800 IN NS f.gtld-servers.net. net. 172800 IN NS a.gtld-servers.net. net. 172800 IN NS m.gtld-servers.net. net. 172800 IN NS c.gtld-servers.net. net. 172800 IN NS k.gtld-servers.net. net. 172800 IN NS j.gtld-servers.net. net. 172800 IN NS g.gtld-servers.net. ;; ADDITIONAL SECTION: a.gtld-servers.net. 172800 IN A 192.5.6.30 b.gtld-servers.net. 172800 IN A 192.33.14.30 c.gtld-servers.net. 172800 IN A 192.26.92.30 d.gtld-servers.net. 172800 IN A 192.31.80.30 e.gtld-servers.net. 172800 IN A 192.12.94.30 f.gtld-servers.net. 172800 IN A 192.35.51.30 g.gtld-servers.net. 172800 IN A 192.42.93.30 h.gtld-servers.net. 172800 IN A 192.54.112.30 i.gtld-servers.net. 172800 IN A 192.43.172.30 j.gtld-servers.net. 172800 IN A 192.48.79.30 k.gtld-servers.net. 172800 IN A 192.52.178.30 l.gtld-servers.net. 172800 IN A 192.41.162.30 m.gtld-servers.net. 172800 IN A 192.55.83.30 a.gtld-servers.net. 172800 IN AAAA 2001:503:a83e::2:30 b.gtld-servers.net. 172800 IN AAAA 2001:503:231d::2:30 c.gtld-servers.net. 172800 IN AAAA 2001:503:83eb::30 d.gtld-servers.net. 172800 IN AAAA 2001:500:856e::30 e.gtld-servers.net. 172800 IN AAAA 2001:502:1ca1::30 f.gtld-servers.net. 172800 IN AAAA 2001:503:d414::30 g.gtld-servers.net. 172800 IN AAAA 2001:503:eea3::30 h.gtld-servers.net. 172800 IN AAAA 2001:502:8cc::30 i.gtld-servers.net. 172800 IN AAAA 2001:503:39c1::30 j.gtld-servers.net. 172800 IN AAAA 2001:502:7094::30 k.gtld-servers.net. 172800 IN AAAA 2001:503:d2d::30 l.gtld-servers.net. 172800 IN AAAA 2001:500:d937::30 m.gtld-servers.net. 172800 IN AAAA 2001:501:b1f9::30 ;; Query time: 84 msec ;; SERVER: 202.12.27.33#53(202.12.27.33) ;; WHEN: Fri Sep 14 16:06:49 +03 2018 ;; MSG SIZE rcvd: 825Output from centos:
[root@ekcentos ~]# dig @m.root-servers.net net NS ; <<>> DiG 9.9.4-RedHat-9.9.4-61.el7_5.1 <<>> @m.root-servers.net net NS ; (2 servers found) ;; global options: +cmd ;; connection timed out; no servers could be reached [root@ekcentos ~]#EDIT:I blocked all other dns servers to LAN side from rules section when I do that centos cannot solve that hostname but when I allow all dns servers to lan side centos can solve this domain too.
-
one question? are you using carp? if so, use the carp vips on dns resolver. for outbound interface you only need localhost.
-
@bahsig No Im not my setup is very simple. 1 WAN(PPPOE) - and 2 LAN (one of them for WIFIaps)
I seeted up my box with that tutorial: https://www.youtube.com/watch?v=RrQrt8r_uYg
And my plugins are pfblocker, snort and squid but I didnt configure it yet.
-
So your problem has nothing to do with dns it seems like, but more your dns rules?
Lets see these rules for your centos box network interface on pfsense..
-
@johnpoz
here they are I block all other dns servers because of I dont want to clients pass pfblocker with other dns servers.
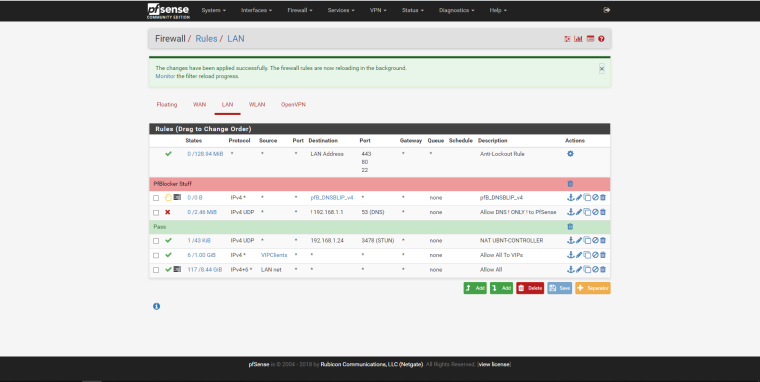
-
@emirefek said in I need HELP on DNS RESOLVER!:
EDIT:I blocked all other dns servers to LAN side from rules section when I do that centos cannot solve that hostname but when I allow all dns servers to lan side centos
Your DNS ! ONLY ! to pfSEnse rule is UDP only ....

Read this https://serverfault.com/questions/404840/when-do-dns-queries-use-tcp-instead-of-udp and start slapping yourself.
Act upon this information (and also activate DNSSEC, it will work this time ^^).
edit : https://en.wikipedia.org/wiki/Domain_Name_System#Protocol_transport - see "DNS Protocol transport"
edit : tip : Instead of "192.168.1.1" as a destination address, use "LAN Address". This will protect you for the next pitfall : the day you introduce IPv6.
-
@gertjan Oh. I change it to TCP/UDP and I can solve it now on centos. And I was enable DNSSEC now and I change To LAN Address on rules section.
But I cannot solve damn edgecastcdn.net anyway.
[root@ekcentos ~]# dig @e.gtld-servers.net edgecastcdn.net NS ; <<>> DiG 9.9.4-RedHat-9.9.4-61.el7_5.1 <<>> @e.gtld-servers.net edgecastcdn.net NS ; (2 servers found) ;; global options: +cmd ;; connection timed out; no servers could be reached [root@ekcentos ~]# dig @e.gtld-servers.net edgecastcdn.net NS ^C[root@ekcentos ~]# dig @ns1.edgecastcdn.net edgecastcdn.net NS ^C^C^C^Cdig: couldn't get address for 'ns1.edgecastcdn.net': not found [root@ekcentos ~]# -
@emirefek said in I need HELP on DNS RESOLVER!:
ig @ns1.edgecastcdn.net edgecastcdn.net NS
Possible that you test also with another PC with some Microsoft OS on your LAN - and then use the 'dig' of Microsoft : nslookup.
Just to be sure that your Centos does things as they should.Btw : try also disabling for some time your rule number 3 (the DNS block rule).
-
your rules are not going to allow centos to query anything other than 192.168.1.1 for dns - sothat dig on centos would never work with that rule in place.
-
@gertjan I already disable that rule and mate I cannot resolve this domain on pfsense box too. Its not about rules I think.
-
your trace will show you where you have a problem.. A +trace is exactly what resolver does.. It walks down from roots to the authoritative ns for a domain, then queries an authoritative ns for the domain your looking for for the record you seek..
If you can not resolve thee ns for edgecastcdn.net then no your never going to be able to resolve a record they are authoritative for
Now that you have removed that rule and centos can talk to any dns it wants... Lets see its trace for that record as I posted before.
So how that is resolved
; <<>> DiG 9.11.2-P1 <<>> cs71.wac.edgecastcdn.net +trace +nodnssec ;; global options: +cmd . 47128 IN NS a.root-servers.net. . 47128 IN NS b.root-servers.net. . 47128 IN NS c.root-servers.net. . 47128 IN NS d.root-servers.net. . 47128 IN NS e.root-servers.net. . 47128 IN NS f.root-servers.net. . 47128 IN NS g.root-servers.net. . 47128 IN NS h.root-servers.net. . 47128 IN NS i.root-servers.net. . 47128 IN NS j.root-servers.net. . 47128 IN NS k.root-servers.net. . 47128 IN NS l.root-servers.net. . 47128 IN NS m.root-servers.net. ;; Received 239 bytes from 127.0.0.1#53(127.0.0.1) in 0 ms net. 172800 IN NS a.gtld-servers.net. net. 172800 IN NS m.gtld-servers.net. net. 172800 IN NS b.gtld-servers.net. net. 172800 IN NS c.gtld-servers.net. net. 172800 IN NS e.gtld-servers.net. net. 172800 IN NS k.gtld-servers.net. net. 172800 IN NS i.gtld-servers.net. net. 172800 IN NS j.gtld-servers.net. net. 172800 IN NS f.gtld-servers.net. net. 172800 IN NS h.gtld-servers.net. net. 172800 IN NS d.gtld-servers.net. net. 172800 IN NS g.gtld-servers.net. net. 172800 IN NS l.gtld-servers.net. ;; Received 846 bytes from 192.36.148.17#53(i.root-servers.net) in 35 ms edgecastcdn.net. 172800 IN NS ns1.edgecastcdn.net. edgecastcdn.net. 172800 IN NS ns2.edgecastcdn.net. ;; Received 177 bytes from 192.31.80.30#53(d.gtld-servers.net) in 42 ms cs71.wac.edgecastcdn.net. 3600 IN A 72.21.91.97 ;; Received 69 bytes from 72.21.80.5#53(ns1.edgecastcdn.net) in 18 msIt asks roots hey roots who is NS for .net domain, hey .net NS who is authoritative for edgecastcdn.net, hey hey ns1.edgecastcdn.net what is the A record for cs71.wac.edgecastcdn.net.
You can see that happen in the trace - and exactly what IP got asked..
If pfsense can not do that - then you need to figure out why.. You can sniff when you run the command and see exactly what gets asked and what gets returned.. On pfsense wan.. If you send a query and don't get a response then the problem is upstream.. Maybe your ISP dicks with dns queries? Maybe you have a network problem talking to the NSers for edgecastcdn.net? maybe they block your IP, etc. etc.