How do I allow VNC from one subnet to another?
-
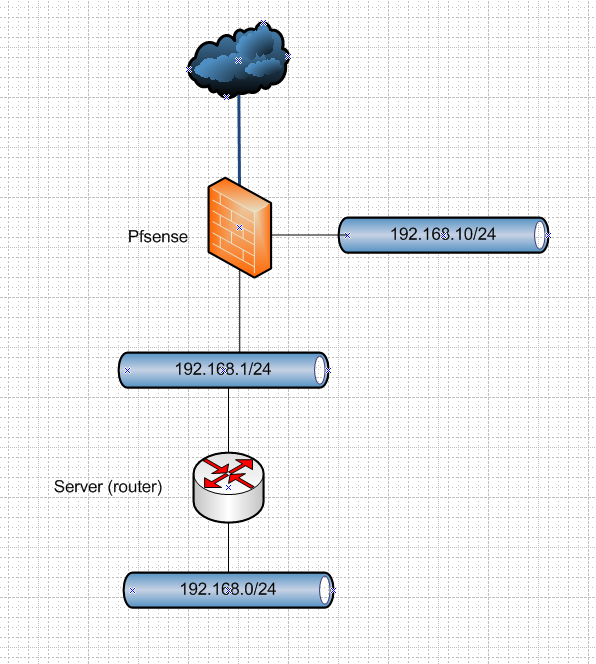
pfSense box: single WAN in, four port NIC out with four different subnets, and they are normally not allowed to interact. The server is connected to two of them, 192.168.1.x and 192.168.10.x But the last is blocked in Routing and remote access, so the server does not give access to it on the internal network (192.168.0.x).
That means that I have to VNC to the server and then use a VNC client on the server to control what's there. I would like to go from the 192.168.1.x subnet to he pfSense box and directly over to the 192.168.10.x and I think it's possible. I have tried to create rules in the pfSense box so that any address on the 192.168.1.x network is allowed to VNC to any client on the 192.168.10.x network, but it doesn't work. Do I need to mess with reverese DNS or something like that to achieve this?
-
Show us a screenshot of your Firewall Rules.
VNC per default is TCP Port 5900 and 5800.
Maybe you have Asymmetric Routing going on there....check your Firewall Logs.-Rico
-
@mastiff said in How do I allow VNC from one subnet to another?:
But the last is blocked in Routing and remote access
Blocked in routing? Huh?? Pfsense has the network attached it will know how to get there.. Are you saying your policy routing via firewall rules and show connections out a gateway?
As with pretty much all firewall related questions - post up a pic of your rules if you actually want valid help.
-
Rico, here you go:
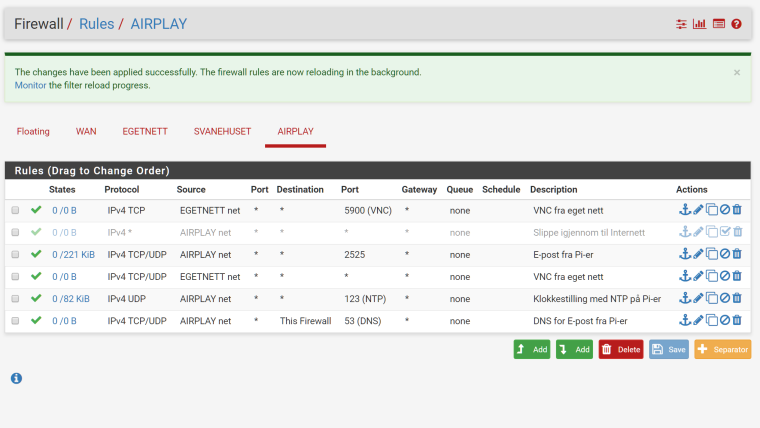
I tried to add 5800 too, but that didn't help any. I'm using 5900, btw. Egetnett is the subnet that the server has as it's WAN. It didn't work with "any" as the source either.
Johnpoz, I just meant that I can't use the Windows Server role Routing and remote acces on the server to get to this subnet, like I could if I had the server NIC on the 192.168.10.x subnet marked with "Enable NAT on this interface". But I see that I shouldn't really have mentioned that, it just clouds the issue.
-
How would egetnett EVER be source into airplay interface..
If you want egetnett to get to airplay then those rules would go on the egetnett interface not airplay..
Rules are evaluated as traffic enters and interface from the network the interface is attached too.. First rule to trigger wins, no other rules are evaluated..
In NO scenario would the egetnett IPs ever be source inbound into your airplay interface..
-
Silly me. I thought it was the other way around, that you opened up on the interface you wanted to GET to. So I have made this rule, but it still doesn't work, probably something else I have missed:
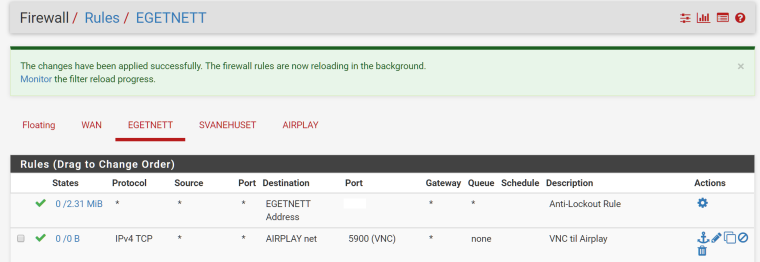
-
Nothing?
-
I don't see any hits on that rule see the 0/0
Do you have any floating rules?
Are you hitting 5900 or 5800? VNC could use both - one is the java port. -
Thanks for answering! Right, so that's what those numbers are! Eh...not as far as I know. Not if they're not built in, because I have never heard about them, so I haven't made any myself.
-
So sniff on egetnett for your source IP, try and open up your vnc... Do you see traffic?.. Are you suing some fqdn.. Maybe that resolve to public IP or something..
Are you putting in IPaddress that is on your airplay net? If so that rule would see a hit ie would change from 0/0
That rule would allow traffic to port 5900..
-
I don't see anything at all in the log either. But is the rule enough, or is there some kind of an "outbound NAT" if that's even a thing that's necessary to get to the other subnet?
I am pretty sure there's nothing in the system that can resolve to a public IP, no. And 5900 is for VNC, yeah.
When I capture, I get this in Wireshark, in red:
14 1.776350 192.168.0.50 192.168.10.102 TCP 66 52111 → 5900 [SYN] Seq=0 Win=64240 Len=0 MSS=1460 WS=256 SACK_PERM=1
-
Ok you sent syn.. Sniff on the airplay interface when you do that... Do you see the syn going to the IP 192.168.10.102, the thing you wan to to vnc too... If you do but you see no answer, then that means its not listening on 5900, or it has a firewall... Or its not using pfsense as its gateway.
No there is no outbound nat to do, pfsense does not NAT between local networks. Unless you put some gateway on pfsense interface for your local networks - they are LAN side network and no there would be no nat between them, unless you messed with the outbound nat rules.
-
Thanks! I set up a VM on the server directly on the 1.x segment, and it turned out that I could both sniff and get to the 10.x segment from that. So it seems the problem is in my server, which is kind of logical when I think about it. The Windows Server 2016 needs to know that requests to 10.x should go through the 1.x network. I tried setting up a static route in Routing and remote access on the server, but that didn't work, so I have to experiment a bit more to find out how I can route that.
-
HUH??
So you have multihomed server, ie it have interfaces in more than 1 network? Why would it go through your 1 network if its on the 10 network already??
Why don't you draw up how you have this server actually connected... Multihoming a server is normally BAD IDEA!!!!
-
The server does not have (shared/NAT-ed/routed) interfaces in more than one network. The pc I want to connect from is on the server's internal network, 192.168.0.x, the server uses the 1.x segment from the pfSense box as it's WAN, and then I wanted to go like this:
Pc on 192.168.0.50 --> Server internal NIC 192.168.0.1 --> Server WAN 192.168.1.4 --> pfSense egetnett (the server's wan) 192.168.1.1 --> pfSense Airplay 192.168.10.x
-
If your server is a downstream router... Then its wan this 192.168.1 network becomes a transit.. There should be NO hosts on this network.. It is a transit network between routers.. If your going to put hosts on it.. Then this server (router) would need to nat traffic from the 192.168.0 to 192.168.1.x (its wan address).. If you expect the 192.168.10 to know how to get back to it..
If you do not nat, then pfsense needs to know to get to the 192.168.0 network to talk to this servers (downstream router) IP on the 192.168.1 network.
-
The server sees the .1 network as a pure WAN, yeah. The server has no outgoing DNS, DHCP or anything else to that net, everything there is controlled by the pfSense box.
But I'm afraid I need it dumbed a bit down, sorry... Do you mean that I need to put some kind of a static route from the 10.x network to the 0.x network with the server's external IP as the gateway? I thought the 10.x network would see the contact coming from the server's external IP on the 1.x network (192.1681.4), and that the rest had to be done in the server.
-
If your server nats the 192.168.0 netework to to its WAN ip 192.168.1.x then you have not problems. If it is NOT natting this and pfsense is seeing a source IP of 192.168.0 on its egetnett interface then for starters you need to allow for that.. Since 192.168.0 is NOT egetnett network 192.168.1
And pfsense also needs to know how to get to 192.168.0 via a route and a gateway..
where did you sniff this
14 1.776350 192.168.0.50 192.168.10.102 TCP 66 52111
If you sniffed that on pfsense then your server is NOT natting to its 192.168.1 address.And its not a static route from the 10 network.. Its route on PFSENSE saying hey to get to 192.168.0 talk to 192.168.1.x
So you need a gateway setup. And you need to create the route... And then you will need to enable the rules on egetnett to allow for 192.168.0
And if you want 192.168.0 to get to the internet you would have to make sure that pfsense does outbound natting of this 192.168.0 networkFor the life of me have no idea why you would do it this way... Why not just directly connect 192.168.0 to pfsense - what is the point of this server doing routing downstream of pfsense?
So you have other devices on this egetnett? If so them talking to stuff on the 192.168.0 is going to be asymmetrical..
-
I understand. I see that nothing happens in the Firewwall log when I try to VNC out, and there's no mentioning anywhere in the firewall logs about a 0.x segment, only 192.168.1.4 (the server's external network) so that should mean that the server should NAT to the WAN.
The sniffing was done on the internal network, on the same 0.50 pc that's trying to get to the VNC's on the 10.x network.
And 0.x has always gotten to the Internet, that's a problem. It's just getting from the internal network via the Server and to the 10.x segment that doesn't work. Which led me to think that I needed a static route to the 10 network. pfSense sees "hey, 192.168.1.4 on the Egetnett wants to talk to somebody on the .10 net, so I'll route it". And it can. So I think this is a matter of finding out how the Server can be aware that it needs to go to the pfSense on 192.168.1.1 to get to the 10.x network. I guess that's what you're saing in the bottom added part, right?
-
OMG dude...
Sniff on pfsense egetnett interface for 5900 tcp... Try and get to your 192.168.10 address from your 192.168.0 address.
Do you see traffic?? What is the source IP?
Now sniff on the airplay interface for tcp 5900 and try and get there again... Do you see pfsense send on the traffic???
"hey, 192.168.1.4 on the Egetnett wants to talk to somebody on the .10 net, so I'll route it".
Pfsense KNOWS how to route to any network connected to it... You do not have to create any routes... You have to allow it via a firewall rule on egetnett interface.
You say that 192.168.0 can get to the internet... So how is the default gateway of this server your 192.168.0 behind NOT pfsense IP address in the 192.168.1 network?? If its NOT then NO its never going to get to the 10.. Does this server your 192.168.0 have some other default gateway.. Does it have some other connection to the internet that you say the 192.168.0 can get to?
This is your network???