Sonos speakers and applications on different subnets (VLAN's)
-
@qinn said in Sonos speakers and applications on different subnets (VLAN's):
I am fine-tuning the firewall rules for the ports needed, as the current rules suggested in the guide above, are not much of security.
Hi Qinn
Thanks for the detailed writeup and pointing me to this. So pimd replaces the need to have Avahi and igmpproxy? How stable is pimd daemon? Waiting to see what final rules you come up with for your vlans then I'd take a stab as well.
-
@vacquah said in Sonos speakers and applications on different subnets (VLAN's):
@qinn said in Sonos speakers and applications on different subnets (VLAN's):
I am fine-tuning the firewall rules for the ports needed, as the current rules suggested in the guide above, are not much of security.
Hi Qinn
Thanks for the detailed writeup and pointing me to this. So pimd replaces the need to have Avahi and igmpproxy? How stable is pimd daemon? Waiting to see what final rules you come up with for your vlans then I'd take a stab as well.
Well, I have not replaced them. In my setup IGMPproxy is not running, but Avahi is. Avahi is used here to let iOS devices, that are in several VLAN's, to access the one VLAN that contains all printers. So Avahi is used to traverse Apples "Bonjour" service over these VLAN's to make printing possible to iPad's and iPhones that are on different VLAN's than were the bonjour printers are.
The beauty with the PIM deamon/iOS is that once the Sonos applications (iPad and iPhones) have located the Sonos speakers they "remember" there IP's, so somehow.
IP's addresses seem to be saved or stored by the Sonos applications (I can't check it, as the Sonos applications are closed source). But it's been 2 weeks since I have been running the PIM daemon (once and quit it) and I can still access the Sonos speakers from a different VLAN.So practically I have started the PIM daemon only once, then waited for the applications (that are in a different VLAN then the Sonos speakers) to get access to the speakers (all Sonos speakers are in one VLAN) and then quit the PIM daemon (as described in my guide above).
Only running PIMD once and then quiting it minimizes the theoretical risk of running an package that has not been tested by the pfSense developers.
Cheers Qinn
-
On the subject of security, my preliminary investigation suggests the following:
To let the Sonos speakers access the Sonos applications (iPad and iPhones), they need to be able to access the VLAN that holds the Sonos applications on UDP port 1901 and TCP ports 3400 and 3401.
To let the Sonos applications access the Sonos speakers they need to be able to access the VLAN that holds the Sonos speakers on TCP/UDP ports 1400 and 1443
It's is of course best practice to create these rules only for the ip's of Sonos speakers and the Sonos devices that hold the Sonos applications.
Sorry, time is a challenge at the moment, but in time I will place a detailed rule set.
Cheers Qinn
-
Btw to anyone, if you are happy with my guide and it helped you, maybe also vote on the thread below and add a comment, maybe the pfSense developers might consider to add the PIMD package to pfSense....
https://forum.netgate.com/topic/139352/pimd-a-lightweight-standalone-pim-sm-ssm-v2-multicast-routing-daemon
-
@qinn said in Sonos speakers and applications on different subnets (VLAN's):
Btw to anyone, if you are happy with my guide and it helped you, maybe also vote on the thread below and add a comment, maybe the pfSense developers might consider to add the PIMD package to pfSense....
https://forum.netgate.com/topic/139352/pimd-a-lightweight-standalone-pim-sm-ssm-v2-multicast-routing-daemon@Qinn See comment by @jimp in this thread:
https://forum.netgate.com/topic/99211/multicast-with-pfsense
-
@vacquah said in Sonos speakers and applications on different subnets (VLAN's):
@qinn said in Sonos speakers and applications on different subnets (VLAN's):
Btw to anyone, if you are happy with my guide and it helped you, maybe also vote on the thread below and add a comment, maybe the pfSense developers might consider to add the PIMD package to pfSense....
https://forum.netgate.com/topic/139352/pimd-a-lightweight-standalone-pim-sm-ssm-v2-multicast-routing-daemon@Qinn See comment by @jimp in this thread:
https://forum.netgate.com/topic/99211/multicast-with-pfsense
Thanks for pointing that one out to me, I was aware, but I thought it was useless to reply on a thread that old and at that time there were (as memory serves) more issues with IGMP proxy https://redmine.pfsense.org/issues/6099
btw did you got it working on your Sonos setup?Cheers Qinn
-
Hi Qinn I'll try to using your guide with pim to configure a similar problem in my network with google devices and Logitech Media server, I hope that this works.
Thanks.
Bull -
@bull said in Sonos speakers and applications on different subnets (VLAN's):
Hi Qinn I'll try to using your guide with pim to configure a similar problem in my network with google devices and Logitech Media server, I hope that this works.
Thanks.
Bulldid it work?
-
@qinn No, at the moment I don't have any positive results, it's quite frustrating, I don't know if I have a problem with netgear GS110TP switches or with pfsense I have it configured in a vmware environment with vlan(4096) and this may be blocking multicast to the router in vmware. I don't know how to continue I'm absolutely blocked, I've been trying and testing for a couple of weeks and starting over.
I need a rest, think so.
-
@bull said in Sonos speakers and applications on different subnets (VLAN's):
@qinn No, at the moment I don't have any positive results, it's quite frustrating, I don't know if I have a problem with netgear GS110TP switches or with pfsense I have it configured in a vmware environment with vlan(4096) and this may be blocking multicast to the router in vmware. I don't know how to continue I'm absolutely blocked, I've been trying and testing for a couple of weeks and starting over.
I need a rest, think so.
Did you turn the port to "promiscuous mode" in VMware for pfSense? That bit me in the butt once, a lesson I will not forget.
-
@tim-mcmanus In my setup(s) I do not use VMware at the moment, so I cannot advise. In theory the switch should not play a part, when it is in the private (RFC1918) subnet(s) and pfSense is controlling these subnets. So IGMP snooping should not be needed, the IGMP proxy or PIMD should do that part.
Have you checked what multicast is send (wireshark)? That's how I analyzed that 239.255.255.0 was used by Sonos and that native IGMP proxy used by pfSense did not traversed it over the subnets. -
@tim-mcmanus yes, promiscuous mode is enable on vmware NIC, anyway I haven't problems with unicast, I can ping and have conectivity across vlans inside and outside of the vmware. So I don't understand were the multicast cannot be routed
-
@qinn thank you, I'll try to disable IGMP on these switches later on, I let you know if it's work.
-
@bull said in Sonos speakers and applications on different subnets (VLAN's):
Hi Qinn I'll try to using your guide with pim to configure a similar problem in my network with google devices and Logitech Media server, I hope that this works.
Thanks.
BullBtw could you give a description of your setup?
-
@qinn said in Sonos speakers and applications on different subnets (VLAN's):
Btw could you give a description of your setup?
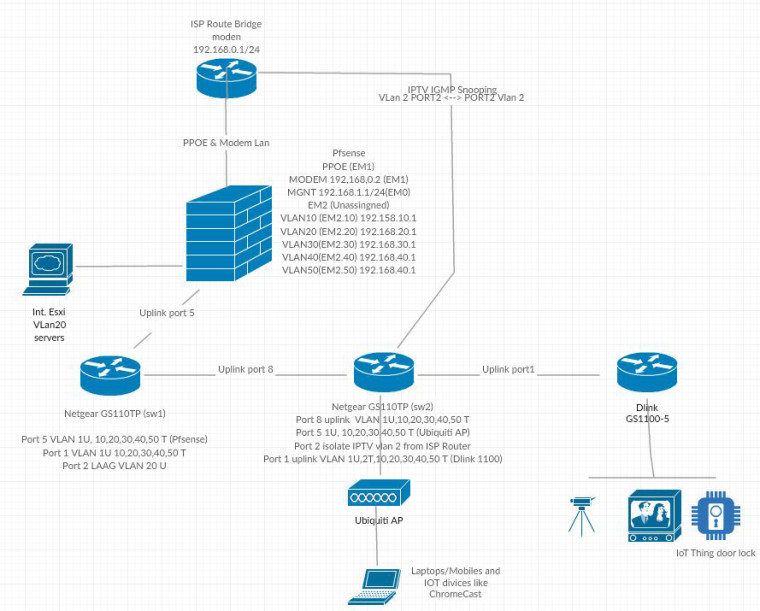
I have a ISP router on bridge mode conecting directly to a vmware nic (MODEM LAN 192.168.0.1/24) this interface works as PPPOE and route to modem network. (EM1)
the other nic i have created to vnic both in vlan 4095, the first one EM0 is de MGMT Lan (192.168.1.1/24) and the other vnic EM2 is configured as vlan 4095 and I've been created 5 port in the following tagged Vlan (10,20,30,40 and 50) from 192.168.10 to 50.1 subnet.
this nic is connected to a Netgear GPT110PT in port 6 vlan 10,20,30,40,50 as tagged an 1 untagged, I have a LAGG vlan 20 too connected to a NAS. from this switch is connected another one in port 1 vlan 10,20,30,40,50 as tagged an 1 untagged to port 8.
In port 5 from this second switch, I have a Ubiquiti AP with some wifi ssid configured with vlans 30,40,50, this port also configured with vlans as 10,20,30,40,50 as tagged an 1 untagged
both swicthes have IGMP Snooping enabled, configured IGMP vlan configuration for vlan 1,30,50 (testing at the moment) with querier enable and queriers enable and configured with vlan 1,30 and 50 pointing to each router ip subnet address 1,1 for vlan 1 30.1 for vlan 30...
May be this is a little confuse without a diagram but I don't have any software to have a grafical view of my network.
Many thanks
Bull -
@bull said in Sonos speakers and applications on different subnets (VLAN's):
I don't have any software to have a grafical view of my network.
There is plenty of free software or even just websites that would allow you to draw your network.
Here are 2 you can do it in pure ascii
https://textik.com/
http://asciiflow.com/Here is decent one
https://www.gliffy.com/
another
https://creately.com/lp/network-diagram-software-onlineActual download software
https://www.yworks.com/products/yed
http://dia-installer.de/Lets not forget the office type apps that are free, openoffice, LibreOffice that have drawing - even google draw ;)
Or you take out a crayon and and a napkin and then snap a photo of it with your phone!
-
@johnpoz said in Sonos speakers and applications on different subnets (VLAN's):
Or you take out a crayon and and a napkin and then snap a photo of it with your phone!
Thanks for the suggestions, I tried to do the best I know.
 W
W -
Disable IGMP Snooping on physical Switches didn't change anything.
Is possible that the problem is that I'm using default vlan 1 as default router ip network and this vlan don't work as spected with multicasting?
I think so from vmware point of view the configuration of the vnic on vlan 4095 is correct.
many thanks
Bull -
4095 on a vswitch will pass all tags to the VMs connected to the switch.
To be honest not a fan of dicking with multicast like to feed it into other Layer 2 networks. If the companies want to be so short sighted to think that their users don't run multiple segments and a way for access through a firewall and different segments then either don't use them.. I mean how hard would it be to let the app put in the IP, and clearly lists what ports need to be allowed, etc.
Or if you really want to use them, then just put all the devices on that L2... I do this with printer - its on the one wireless network.. So if you want to print you just need to make sure your on that SSID.. Not really a big deal... For example when want to control my roku devices with my phone or tables I join the roku vlan.
-
@johnpoz I'm agree with you but looking for the future where more and more IOT devices could be connected in a home lan without any "security" control, would be necesary that the developers that works in security bring to those people that want more security in their home a tool that would be it posible. The company or solution that bring that, win the battle.
I know that is not normal that the mayority of the people had segmented the lan network in their home to have a better view/control of their devices, but how many people had an antivirus installed in their system some years ago?
I'm not want to desviate from the thread, unfortunatly this morning the multicast was working with google devices, I don't know how, I leave home and shutdown the laptop and now I cannot see the chromecast, so... I don't know where my problem is.

