SG-1100 Running Real VLANs
-
I just unboxed my SG-1100 and saw the default configuration is the following:
WAN (wan) -> mvneta0.4090 -> LAN (lan) -> mvneta0.4091 -> v4: 192.168.1.1/24 OPT (opt1) -> mvneta0.4092 ->It looks like 4090, 4091, 4092 are "fake" VLANs assigned somewhere by the SoC to differentiate between the physical ports. That's cool, but my LAN has ~5 real VLANs I need to assign to the LAN physical port.
I don't seem to see any traffic (using TCP dump) on any of the non "4090, 4091, 4092" VLANs inside the netgate device when I assign them coming in through the LAN port.
Ie;
WAN (wan) -> mvneta0.4090 -> LAN (lan) -> mvneta0.3 -> v4: 192.168.1.1/24WAN works. I see WAN traffic. LAN does not, I see no traffic coming in to mvneta0.3.
My LAN switch sends VLAN tagged frames out the port and I'm replacing an x86 pfSense box so I know the VLAN and switch config works.
Am I missing something? Can this device not do "real" VLANs?
I am also curious ... is this really just a single 1GBit port (ie; total bandwidth)?
-
https://forum.netgate.com/topic/139326/sg-1100/14
https://www.netgate.com/resources/videos/configuring-netgate-appliance-integrated-switches-on-pfsense-244.html-Rico
-
So, I have spent many hours on youtube, and have read many articles, (including the links above). Very helpful, BUT, SG-1100 acts differently. So it looks like it doesnt like to be set to Port VLAN Mode, as I cant do anything with it after hitting save. What is the proper way to add VLANs to Port 2 on 2.4.4P2? Having a heck of a time to accomplish the following
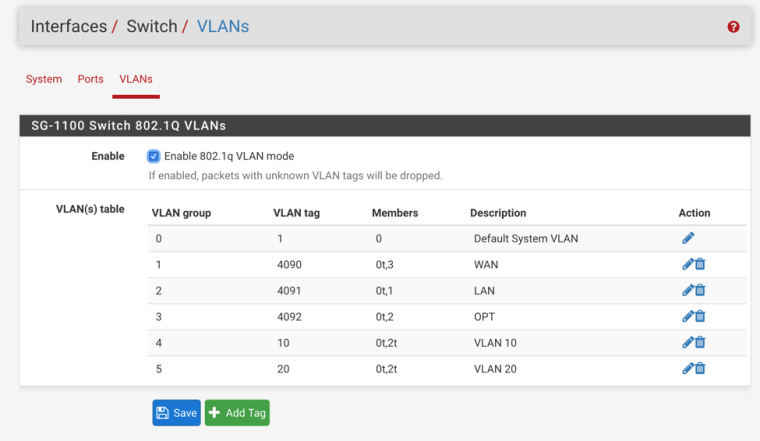
- Add VLAN10, for IoT, and VLAN 20 for Guest to Port 2 (LAN) Mostly from default config, so far defined VLAN, and interface (doesnt appear to associate to a port) and set DHCP server. Do I need to add anything under switches (like VLAN 10 0t, 2t) and have existing LAN VLAN 4091 set as 0t, 2t as well?
- I chose to do VLAN/port segregation from switch, How can I make LAN and OPT1, 2 port switches with same attributes?
I think whats throwing me off is that there isnt native hard ports to select on interface assignments.
Hope this makes sense. Lots of documentations on switch configs for SG-3100, XG-7100 and many others, but since SG-1100 is so new there isnt much out there, although I know concept is the same.
-
@bsd29 said in SG-1100 Running Real VLANs:
WAN works. I see WAN traffic. LAN does not, I see no traffic coming in to mvneta0.3.
My LAN switch sends VLAN tagged frames out the port and I'm replacing an x86 pfSense box so I know the VLAN and switch config works.
Am I missing something? Can this device not do "real" VLANs?Sorta, You need to set the VLAN's up in the WebUI, and assign them to the interface (tagging them as needed), see the guides @Rico sent over
I am also curious ... is this really just a single 1GBit port (ie; total bandwidth)?
No, it's Two 1 Gigabit Ethernet Ports, configured as dual WAN or one WAN one LAN
plus four-port 1 gbps Marvell 88E6141 switch, uplinked at 2.5 gbps to the third port on the SoC for LAN. -
@penicheiro said in SG-1100 Running Real VLANs:
Add VLAN10, for IoT, and VLAN 20 for Guest to Port 2 (LAN) Mostly from default config, so far defined VLAN, and interface (doesnt appear to associate to a port) and set DHCP server. Do I need to add anything under switches (like VLAN 10 0t, 2t) and have existing LAN VLAN 4091 set as 0t, 2t as well?
Yes/No.
Yes, you need to add the VLAN's on the interfaces and tag them
No, 4090/4091/4092 are VLAN uplinks and should rarely be changed.I chose to do VLAN/port segregation from switch, How can I make LAN and OPT1, 2 port switches with same attributes?
From above, 4090/4091/4092 are VLAN uplinks and should rarely be changed. This is one of the few times where you change the uplink to match.
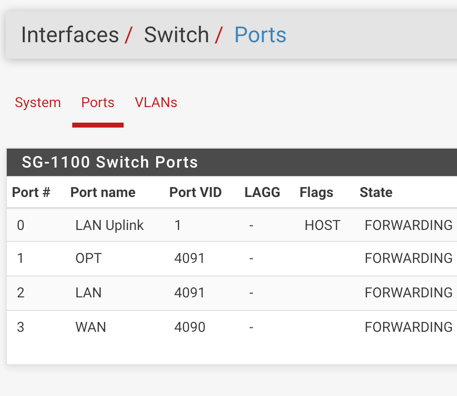
I think whats throwing me off is that there isnt native hard ports to select on interface assignments
They are different, but once you get them, they behave in a similar fashion
Lots of documentations on switch configs for SG-3100, XG-7100 and many others, but since SG-1100 is so new there isnt much out there, although I know concept is the same
They are the same. One has 3 ports, the others have 4 and up. You are right, the concepts are the same.
-
@chrismacmahon said in SG-1100 Running Real VLANs:
No, it's Two 1 Gigabit Ethernet Ports, configured as dual WAN or one WAN one LAN
plus four-port 1 gbps Marvell 88E6141 switch, uplinked at 2.5 gbps to the third port on the SoC for LAN.Did you confuse the 3100 with the 1100 there, I don't see 6 ports on the 1100.
-
https://store.netgate.com/pfSense/SG-1100.aspx
Network Interfaces 1x Marvell 88E6141 networking switch
3x GbE Ethernet (WAN/LAN/OPT)We only use 3 of the 4 ports on the sg-1100, the 4th is the miniPCIe Bus (wifi)
-
@chrismacmahon said in SG-1100 Running Real VLANs:
https://store.netgate.com/pfSense/SG-1100.aspx
Network Interfaces 1x Marvell 88E6141 networking switch
3x GbE Ethernet (WAN/LAN/OPT)We only use 3 of the 4 ports on the sg-1100, the 4th is the miniPCIe Bus (wifi)
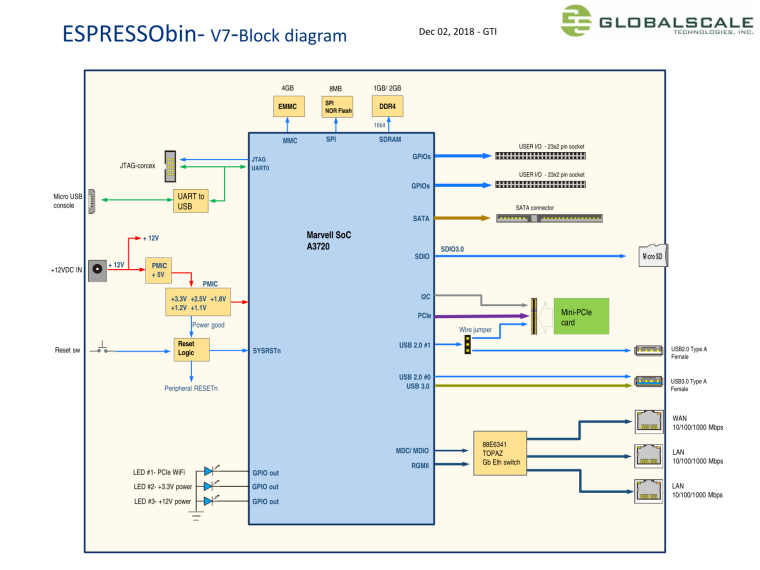
So looking at the official ESPRESSObin schematics your information seems to be wrong. The switch is linked to the SOC and then offers 3 Ethernet ports, which also aligns with the default VLAN configuration. So these are not dedicated Ethernet interfaces and it is in essence a router on stick with the switch already included.
Additionally miniPCIe does not carry Ethernet, unless you cooked up something completely outside the standards there.
-
Your correct, looks like the material was old I was pulling from:
https://www.cnx-software.com/2016/09/23/marvell-espressobin-board-with-gigabit-ethernet-sata-pcie-and-usb-3-0-to-launch-for-39-and-up-crowdfunding/
Network Connectivity
1x Topaz Networking Switch
2x GbE Ethernet LAN
1x Ethernet WAN
1x MiniPCIe slot for Wireless/BLE peripherealsMy pre-caffeine google fu was not the best.
-
@penicheiro said in SG-1100 Running Real VLANs:
Do I need to add anything under switches (like VLAN 10 0t, 2t) and have existing LAN VLAN 4091 set as 0t, 2t as well?
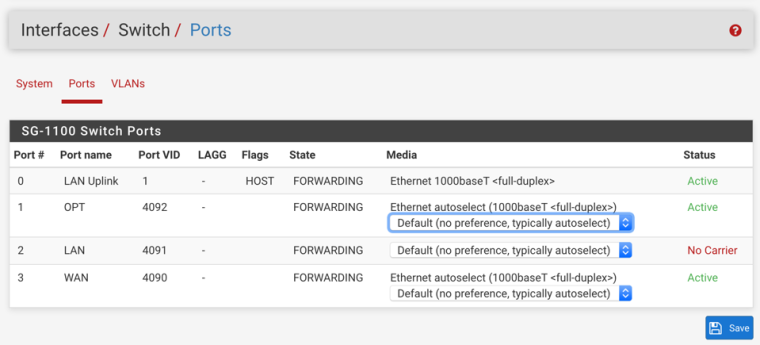
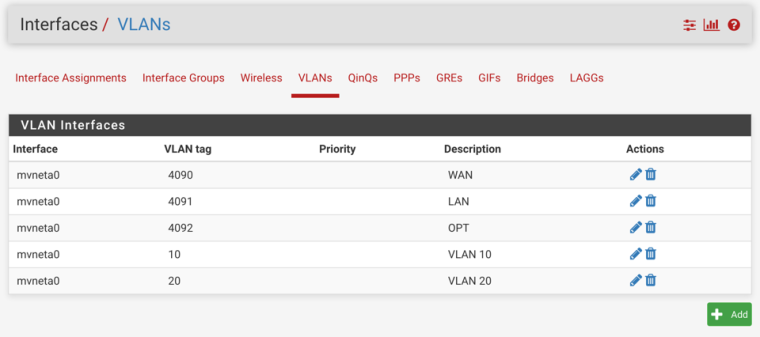
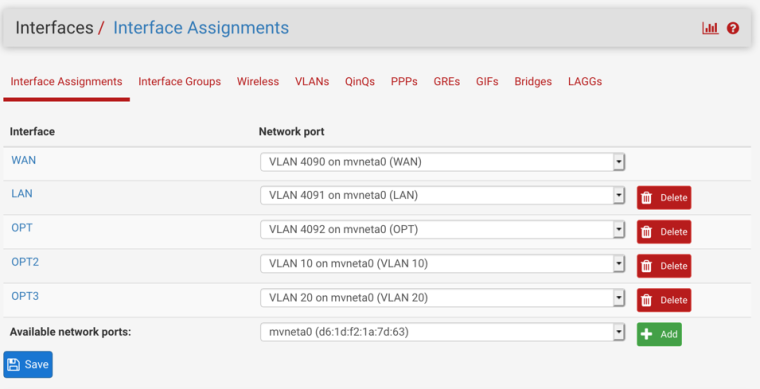
In the following configuration, whatever is connected to switch port 2 (OPT) will need to be configured for:
Whatever you want the existing OPT network, untagged. For consistency this should probably be VLAN 4092 in the switch. If you would like 4092 tagged to the switch, just check tagged on port 2 in Interfaces > Switches, VLANs and edit the PVID on port 2 to VLAN 1 (or some other unused VLAN id) in Interfaces > Switches, Ports
VLANs 10 and 20 tagged.
Just edit, enable, and number OPT2 and OPT3 as desired, make desired ingress firewall rules, configure DHCP servers, Captive Portals, etc.
-
@derelict You must have been typing as I edited those. VLANs now working!! All of the tutorials i had viewed made no mention of the VLANs TAB under SWITCHES. That was it. Added VLAN 10 and 20, tagged 0 and 2, and that was it, everything else I had configured. THANK YOU. Working very Stably right now.
Onto my next task. In order to make LAN and OPT port work as a switch.
-Under SWITCH/PORTS edit port VLAN on OPT from 4092 to 4091.- Add Port 1 to TAGGED VLANS 10 and 20
Is the last step to add port 1 to VLAN 4091 (untagged), and delete VLAN 4092?
Just want to confirm I am not missing anything, and that I wont get locked out AGAIN. lol
Thanks
-
Just posted this a couple hours ago lol
https://forum.netgate.com/topic/140000/sg-1100-configuring-lan-and-opt-to-be-on-the-same-vlan
-
@derelict MIND READER!!! Thank you SIR!! Still adjusting to this interface, coming from tomato, and so far... I am impressed.
-
Ok, I have been reading through many threads and watching all the videos on vlan setups. I have tried just about everything and spent hours trying to get my vlans set up on my sg-1100. I can never get DHCP working on my unifi AC, if I try and set it up on extra vlans. Are you saying you got yours to work? This is driving me crazy.
-
Yes, they work. post your interface and switch configuration and describe what you are trying to do.
-
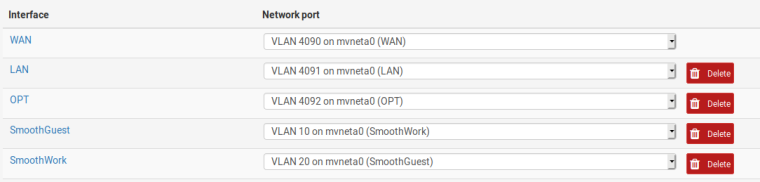
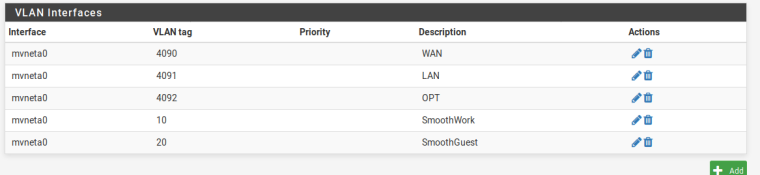
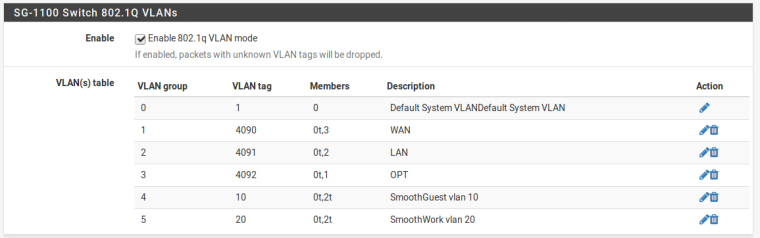
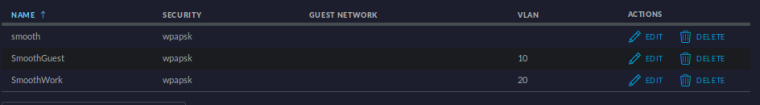
I also have the firewall rules for each vlan, as well as the DHCP set for each. However clients are never able to grab a DHCP address. I am hoping its just something simple I am missing.
-
And the pfSense switch ports tab?
-
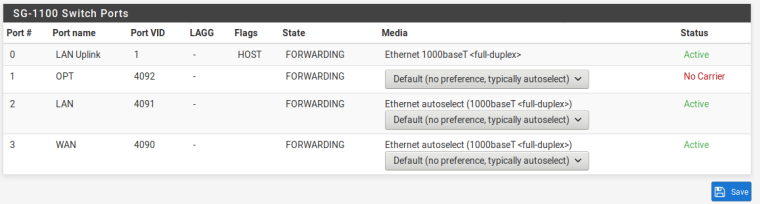
-
That all looks fine for managing that AP on a LAN address if it is connected to port 2.
Anything in the DHCP logs? DHCP has automatic rules for any interface with a DHCP server enabled.
Based on what you have posted I'd look at the DHCP logs and packet captures on UDP port 67.
Does the smooth network work?
-
Nothing showing up in the DHCP logs then I try to connect to the Work or Guest network. I can connect just fine to the regular Smooth network, clients connect and get a DHCP address. Port two is connected to a switch. I had a similar setup working with untangle, just want to make the jump to pfsense.