problems unblocking my sip provider
-
@stephenw10 said in problems unblocking my sip provider:
So you tried an outbound NAT rule with static ports? Not a static IP?
IPFire includes a SIP ALG, do you recall if it needed to be enabled?
If so SIProxd might work for you here.Steve
Someone mentioned SIProxy before. i had a quick look at it and i've never seen anything like it before. and as i keep saying....
i never had to use more then the settings i'm using now on my previous configuration and never had issues.
-
is there a way to can make pfSense stop blocking anything incoming on that port. i know its a security risk i want to try it temporarily and see if it solves my problem
-
So i have added so many firewall rules now that nothing shows up in my logs to do with any incoming or outgoing call attempts. I have also tried disabling snort cause i read a post from 3 years ago that "pfSense works perfectly with snort disabled"
but i am still having the same problems.
-
Try adding a 1:1 NAT rule to the SIP device. Then add a firewall rule on WAN allowing all traffic to that internal IP.
Yes, that's a big risk it exposes the SIP device completely. But that will add static outbound NAT and will pass everything.
If it still doesn't work there's some NAT issue like it's sending it's internal IP. That can only be solved by configuring the SIP device not to do that or using a SIP ALG that translates that.
Steve
-
are you sure its a 1:1 nat rule? i cant specify ports
isnt this what i want?
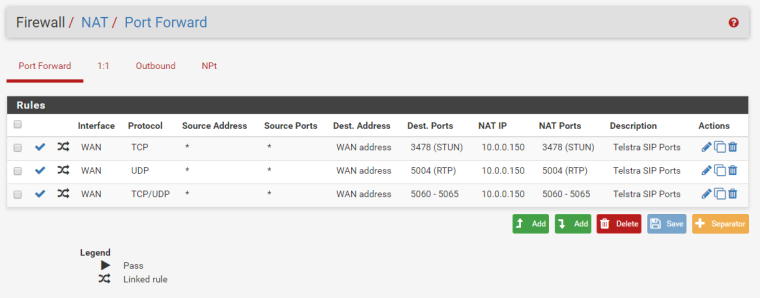
its doesn't work though
-
With a 1:1 rule all ports are forwarded. All incoming traffic will be sent to the SIP device. All outgoing traffic will leave using the same source ports the SIP device sets. That eliminates a number of possible problems.
1:1 NAT rules do not automatically open firewall rules though so you need to add a rule to pass what you need. As a test I suggest just passing everything.
However that will not help if, for example,m the SIP device is using it's private IP is SIP packets as the response address. Only looking at those packets will tell you that. If it is SIProxd could help.
Steve
-
Is there a nice guide for setting up siproxy?
as this is my second dabble with connecting sip devices i really have no idea what i am doing -
Not other than this: https://docs.netgate.com/pfsense/en/latest/packages/siproxd-package.html
That really doesn't tell you much but generally it is discouraged.
The 1:1 NAT did nit help at all? Did you still see blocked traffic?
Have you tried looking at the SIP packets yet to see what IPs the device is sending?
Steve
-
i haven't tried the 1:1 NAT because the incoming IP address in not static, and at one point i had added so many rules added into the firewall that there was nothing appearing in the logs.
i still have the issue were outgoing calls drop after 15 minutes too
-
Might need to review at this point. What exactly do you have in place right now in terms of port forwards and firewall rules and SIProxd?
What VoIP issues are you now seeing?
Steve
-
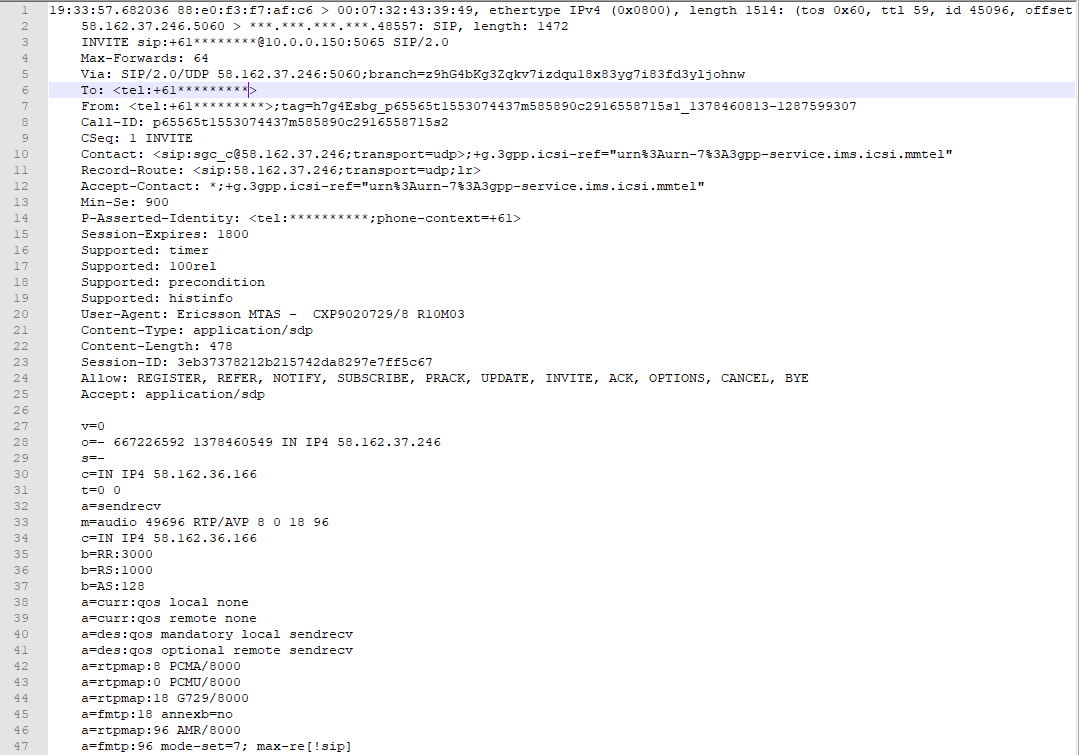
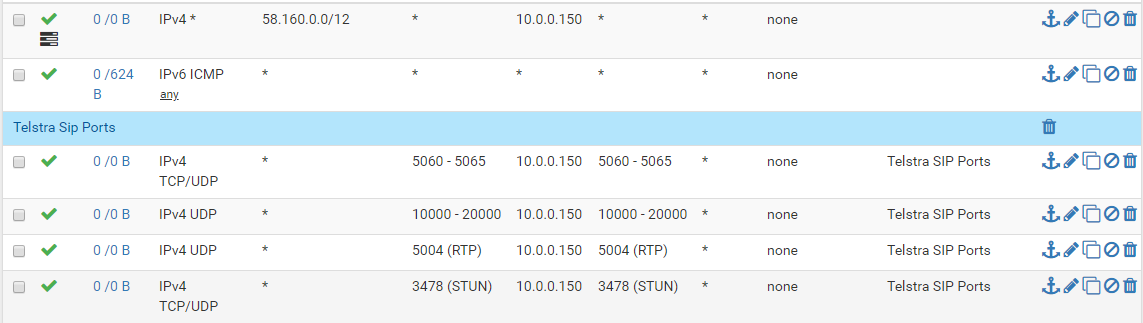
I have tried to open incoming traffic from telstra's entire sub net range.
the 5060-5065, 5004, 3487 ports are all allowed in firewall rules and NAT rules to forward them to my telstra sip device. i have included up to 5065 because i noticed in the logs that the incoming calls didn't only seem to come from 5060.
i had installed snort so I have tried removing it again.
Incoming calls almost never work and outgoing calls always get cut after about 15 minutes.
It can't be a double NAT issue and my mobile/cell phone uses the telstra device for its WiFi hot spot and it works fine.
I did not have these issues with the previous software firewall/gateway i used and all it took was to port forward the same ports i have currently configured into pfSense.
-
Ok, well there are two possibilities. It requires some static source NAT outbound that the old router provided. It requires a SIP ALG which the old router provided.
Just using 1:1 NAT and opening the phone up completely will test theory one.
To test theory two I would capture the SIP traffic and check the contents to see what's actually happening. Then deploy SIProxd if it's appropriate.
Steve
-
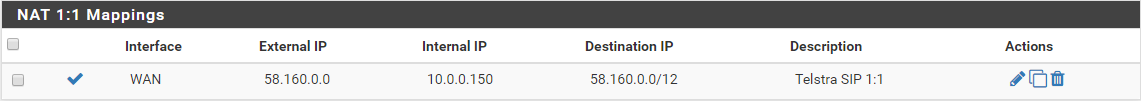
Just taking a complete guess at this.
i never specified a nat source for outbound previously, nor a SIP ALG. i just forwarded the ports
-
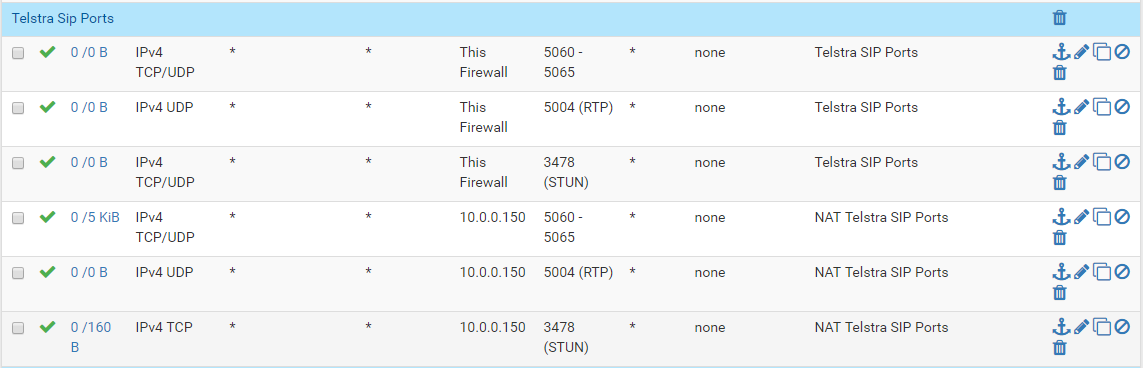
-

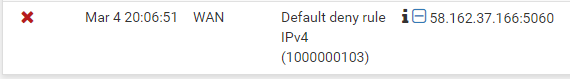
I'm sure THIS is why its not working... even when i managed to get that to stop showing up it still seems to be blocking it
-
i also can't list a nat rule like this
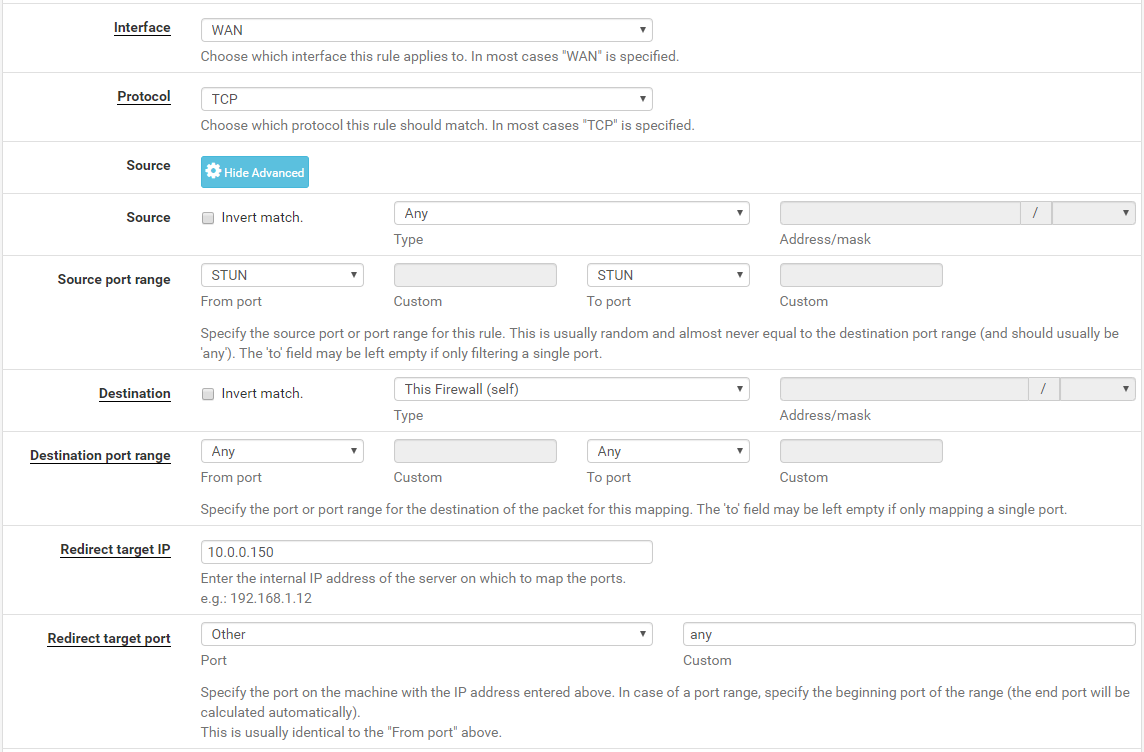
it requires me to put a redirected port in.. but the source it transmitting from port 5060 to 44780.

i cant just specify any port recieved from the source port of 5060 to forward it
-
am i reading these logs wrong.. it looks like my provider is trying to send sip packets from port 5060 to a random port on my gateway, where pfSense seem to want to to come from a random port from the source and arrive at port 5060
-
What i have right now is :
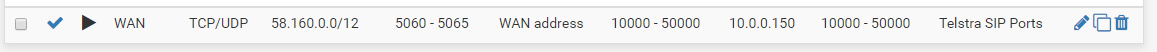
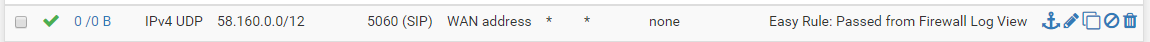
out of maybe 30 attempted incoming calls one worked... is there some kind of auto closing of established connections that could be going on?
-
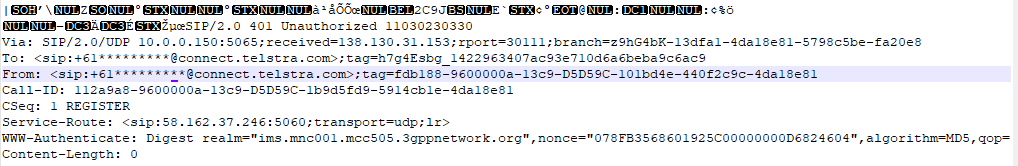
looking at the out going packets from a out going call it seems to be normal.
the packets are being sent from my local device port 5065 to a receiving port of 5060.
-
incomming packet sniff