problems unblocking my sip provider
-
What i have right now is :
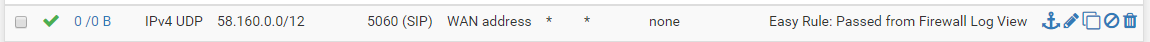
out of maybe 30 attempted incoming calls one worked... is there some kind of auto closing of established connections that could be going on?
-
looking at the out going packets from a out going call it seems to be normal.
the packets are being sent from my local device port 5065 to a receiving port of 5060.
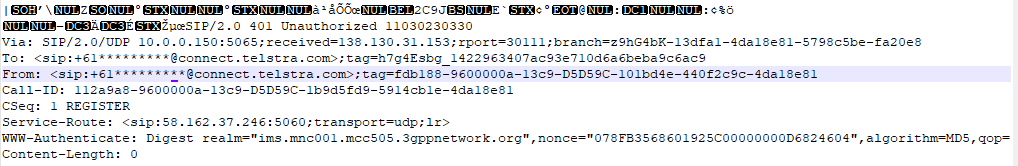
-
incomming packet sniff
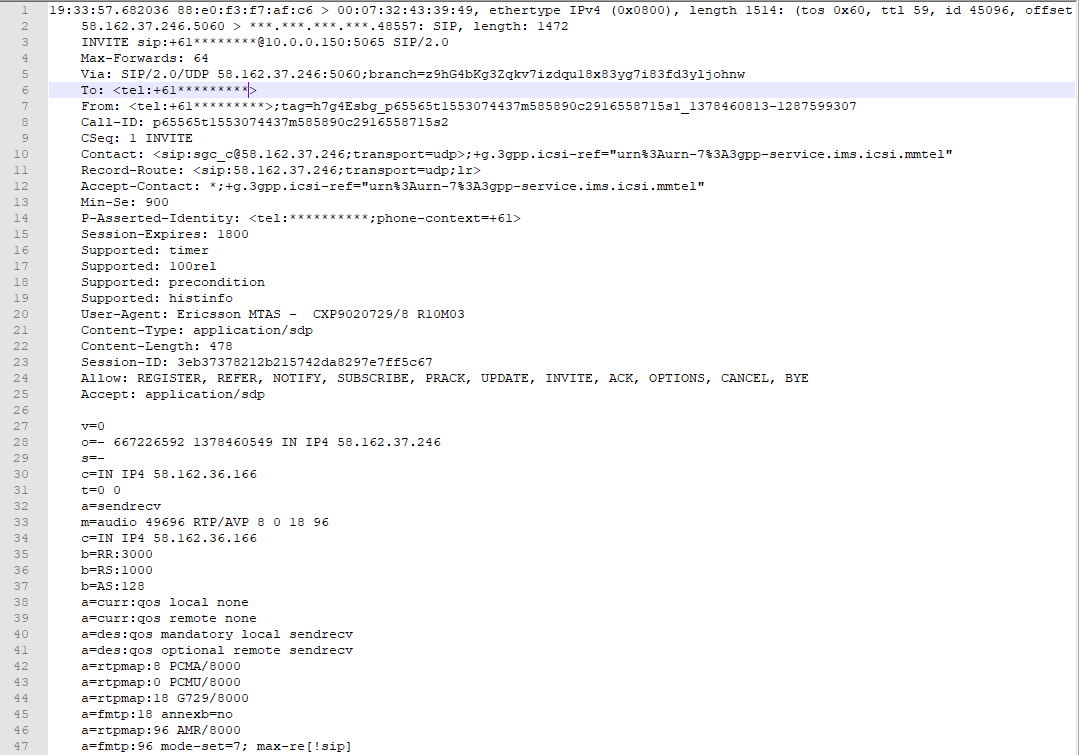
-
The external IP should be the WAN IP address in that 1:1 NAT rule.
Setting the destination as Telstras subnet there means it will only applky to traffic to or from that. So if they are using other IPs it won't pass it. I would leave that as 'any' as a test.
The reason traffic comes back to a random port is because it's replying to traffic the p[hone sent out and pfSense will randomise source ports for security. That should not be a problem. However the fact it's showing as blocked means that firewall state has closed so replies are not getting back to the phone.
You did set the firewall optimisation to conservative earlier? It might require exceptionally long timeouts there.The working 1:1 NAT rule will by-pass that though as traffic will be allowed back in even if the state has expired and source ports will not be changed.
Steve
-
I cant do a 1:1 NAT rule on my wan IP address because i do not currently have a static IP address. there isn't an option to just specify "wan address" like there has been for many other options.
Is there a way i can put in a request for this option?
-
another idea i had now that i'm thinking of it, can i put the telstra device in a dmz on its own vlan and just tell pfsense to forward anything to that single ip address. that would mean anything that didn't originate from my internal lan would get forwarded to the tesltra device, and if it got hacked, its in its own vlan, so they cant do anything anyways.
-
Hmm, interesting I hadn't considered that. Just as a test you can add you current IP as the destination though. You don't want to have that open on all ports permanently. If it works we can look at why it worked and how to replicate that woth port forwards.
Steve
-
sorry i took so long to reply. was sick for like 6 days and had no motivation to look at something with i'm already too frustrated with.
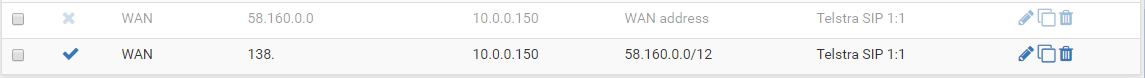
i tried both of these, neither have worked. did i not set it up the way you meant?
i get the occasional incoming call but i think it has more to do with the timing of my sip device re-establishing a connection before it getting dropped out after 15 minutes.
-
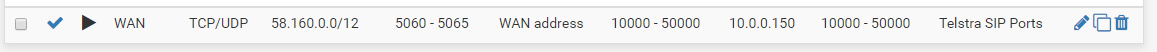
The active rule is correct there though I would leave the destination as 'any' at least for a test.
It does depend what firewall rules you have there also. Again as a test I would open it up completely, re-register the phone and test incoming calls.
If that doesn't work it's not a firewall rule issue and probably is reliant on a SIP ALG.
Steve
-
If I get time I will go through this whole thread later and see what pops out.
Are you still trying to use a STUN server?
Who is your SIP provider??
-
I see now who your provider is..
Apparently from the graphics showing the firewall logs above your LAN device (SIP Unit) is not listed in the SIP header. Otherwise the address would show as the SIP device. Id be interested in your state table.
SIroxd is very easy to set up and probably a good idea here.
Unless specified leave it blank (or default) for now.
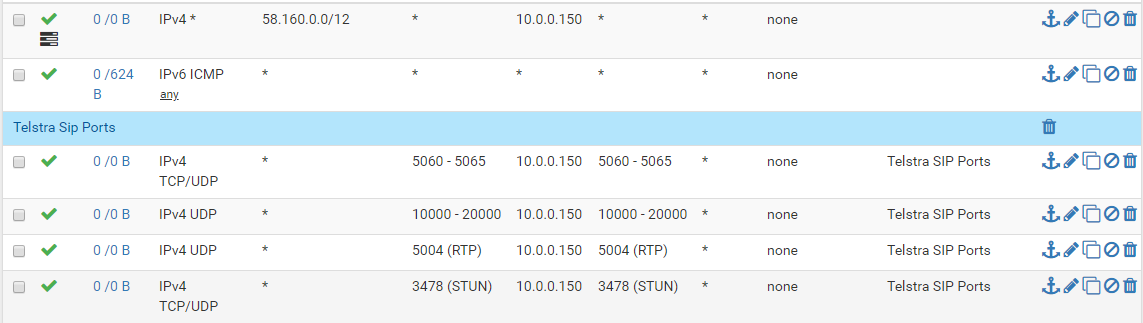
Delete any port forwards or static NATting you have done.
Inbound Interface- whatever ethernet port your sip device is plugged into.
Outbound Interface- whatever ethernet port goes out to your internet.
Go down to RTP proxy. Enable It.
RTP Port Range (Lower) looks like 5004 from your stuff above.
RTP Port Range (Upper) 5059
Save!
Get the stun server stuff out of the mix for now. I do not believe you need it.
Reboot your SIP device.
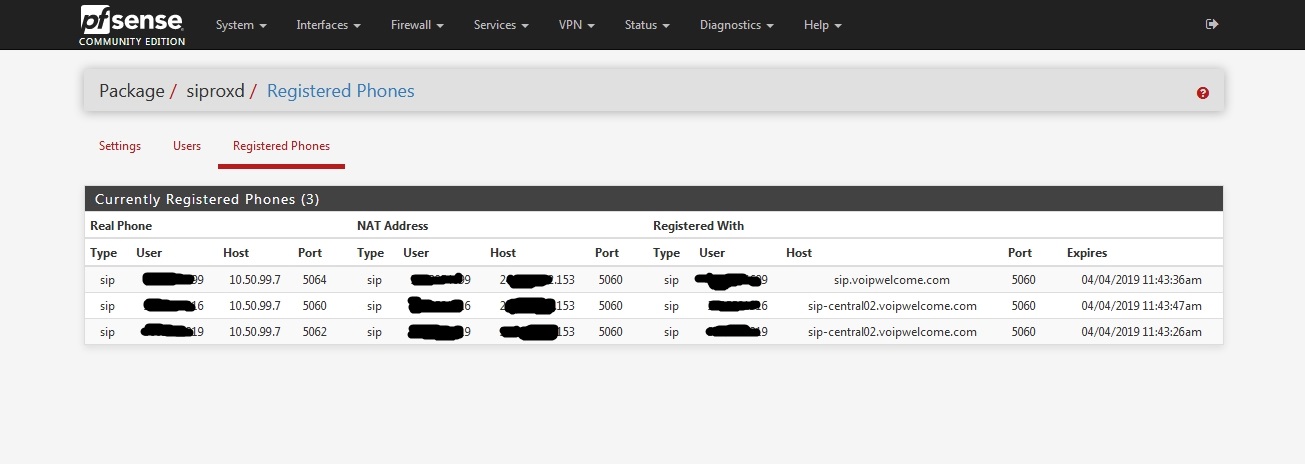
Watch the "Registered Devices" tab and see if your phone shows up there.
If it does not you can add a proxy to the device config or see if they will do that for you.. The proxy address is your LAN address (or address of the ethernet port your SIP device is plugged into.)
Your WAN firewall rules above pointing at "this firewall" should work although I always use "wan address"..
-
http://siproxd.sourceforge.net/ for some details if your so inclined.
-
chpalmer: Cheers mate. trying it out and testing it.
i thought i should have provided this from the very get go.
pretty sure i said before they don't officially support this, but this is the information i found online to get it working originally.
https://crowdsupport.telstra.com.au/t5/Modems-Hardware/ports-for-firewall-in-front-of-telstra-router/m-p/720153#M36304
-
doesn't seem to do anything.
In fact i couldn't even make outgoing calls.THIS
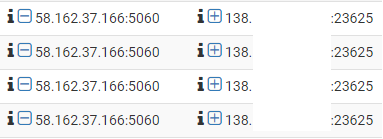
is the bit that is confusing me the most.the traffic is being sent from port 5060 to 23625(seems to be randomly generated). no matter what i put into pfSense i cant write the rules so that ANY traffic that comes from port 5060 to ANY port on my firewall is forwarded to my SIP device. I am sure this is what i have to do to get this to work.
If I am understanding what I am doing here correctly we are writing rules so any packet that get sent to port 5060 on my firewall gets redirected. This is not what my provider is actually doing.
can i just make it so any packet that was transmitted from port 5060 to my wall get redirected to my sip device without any other conditions?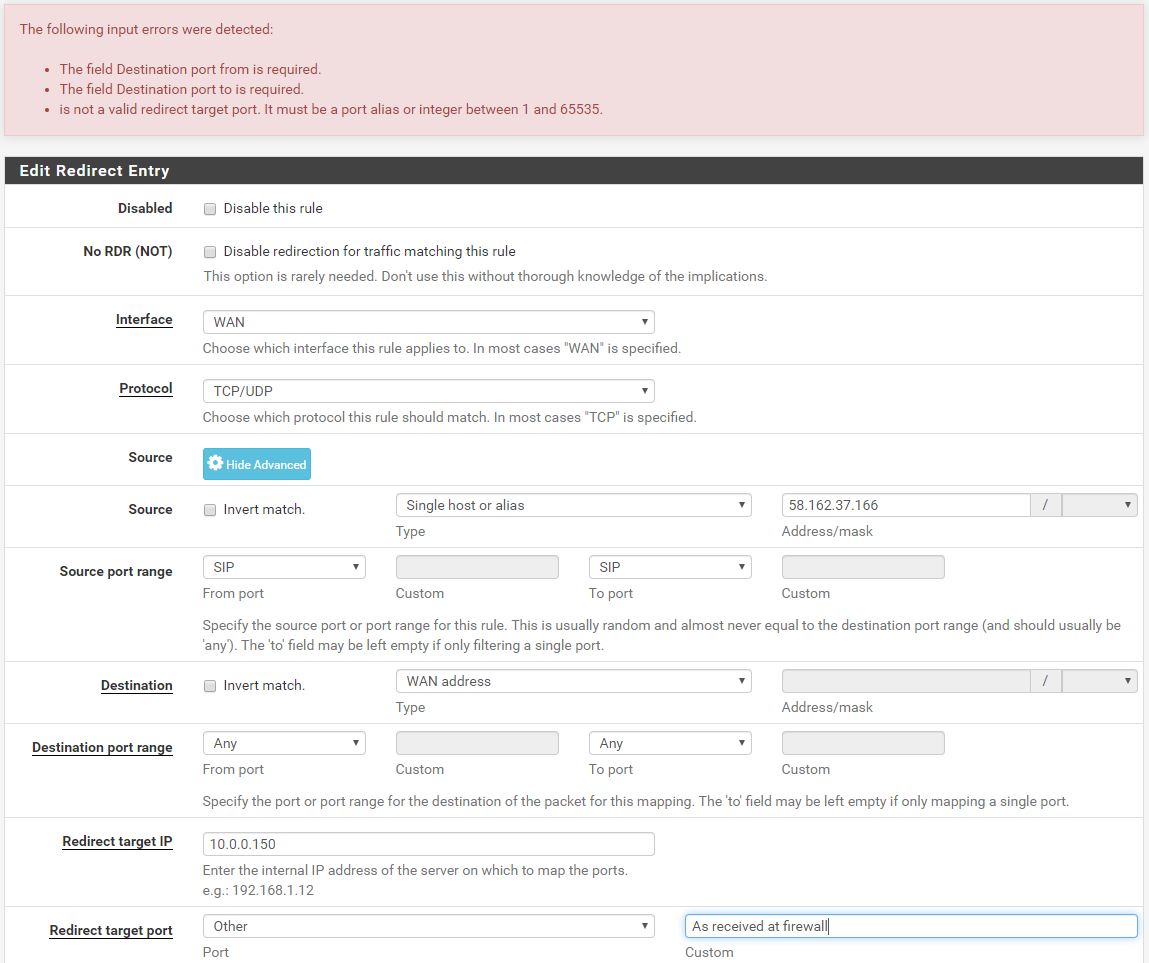
-
Im reading through the Telstra forum post right now. Does not look solved to me.
But- If you have SIProxd in place and the system is still trying to connect to a port other than the 5060 to 5080 range as in your picture above then the box is not connecting to the proxy. I would take it that you do not have anything showing up in "registered devices". You might leave it off the air overnight and then try again in the morning. Your SIP server and device are probably holding on to an earlier registration.
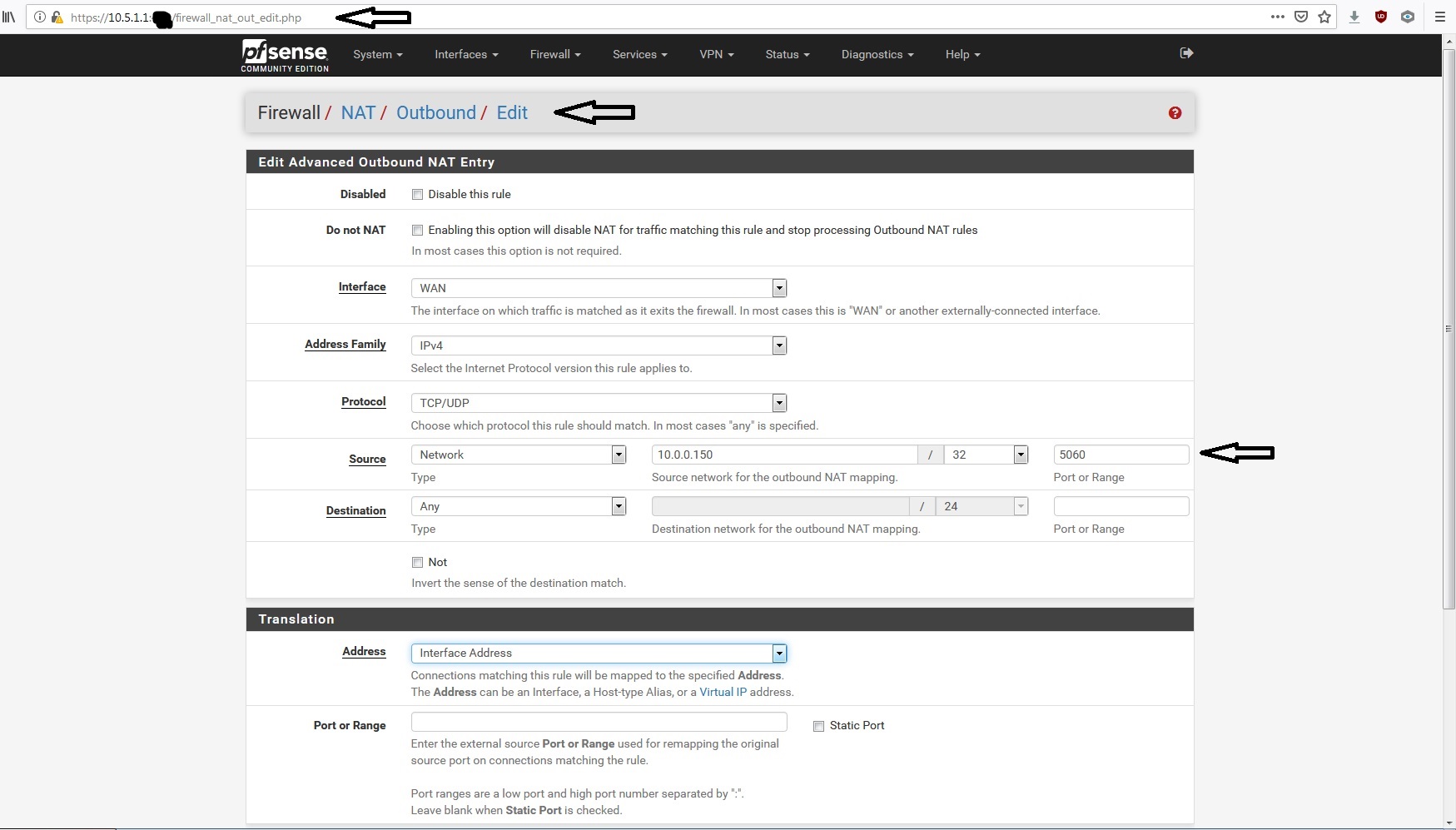
You can set up a static port in the router at Firewall/Nat Outbound NAT tab. Make the whole LAN address of the device "static" and see what that does for you. If this box connects correctly your firwall will show connections to your LAN device and never your WAN address. That is why I think they are doing something hinky.
-
Redirect Target Port is a numerical input and not what you have typed. If you want a 1:1 then do a 1:1. Otherwise do a port forward for each port or range of ports.
-
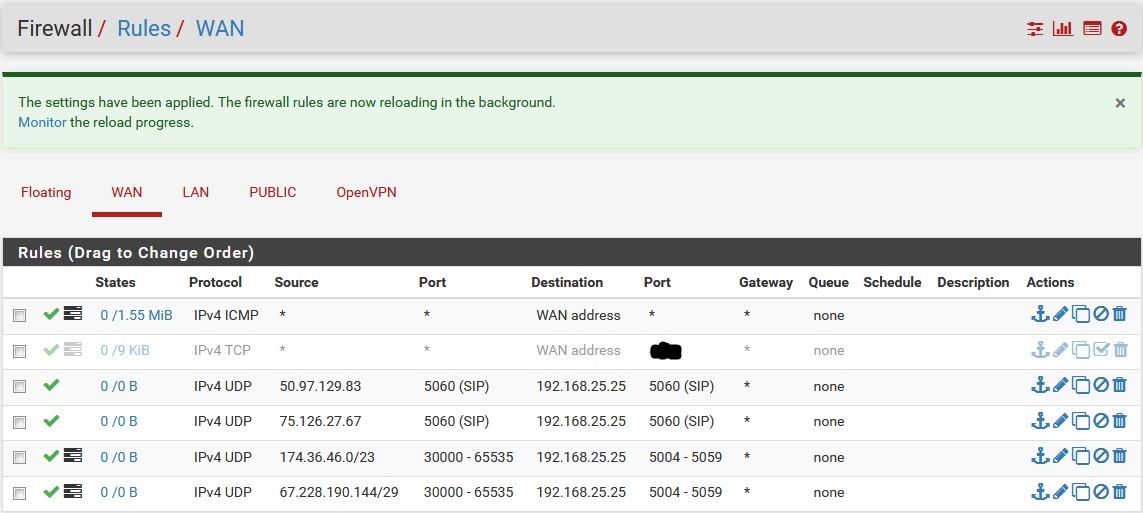
I can't show you a port forward example because I never port forward to an ATA or phone. But the same idea can be seen from one of my spur office ATA setups..
-
The ports in the answer worked perfectly on my previous software firewall IPFire. pfSense is just more tightly programmed.


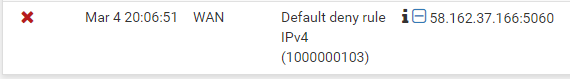
1:1 doesn't work either. the firewall still blocks it.
even when i try this

it still doesn't work. but nothing shows up in the firewall logs -
The states from that box

-
Have you tried a Static port?