pritunl VPN - pass traffic to private network
-
Hello.
I have network like this:
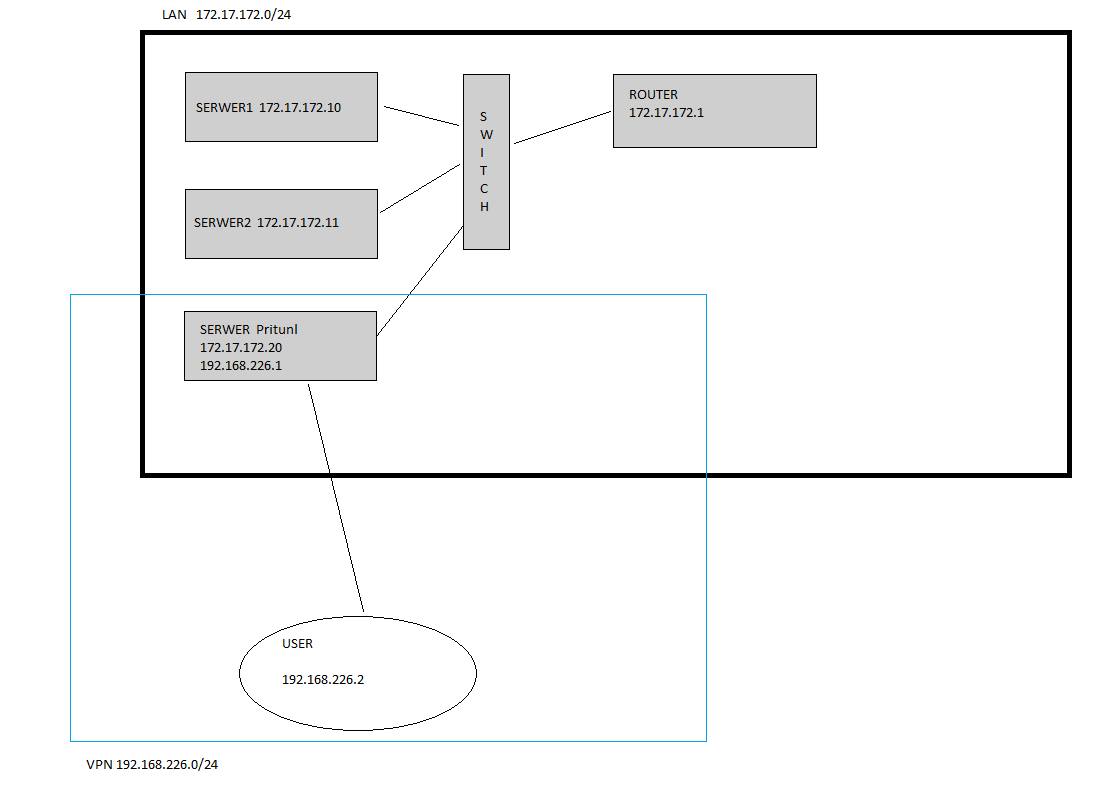 image url)
image url)I would to like open traffic form VPN client to network 172.17.172.0/24.
I have route on pritnul server to 10.0.0.0/8
When I pinging 172.17.172.10 from vpn client, in tcpdump on pritunl server i see:
06:36:24.593668 IP 192.168.226.2 > 172.17.172.10: ICMP echo request, id 1, seq 438, length 40
So i thing, I have to add "something" on pfSense router to create route from 10.0.0.0/8 to 172.17.172.0/24, but I don't know how do this.
Regards,
Tom -
So 'pritunl' is a remote access OpenVPN on pfSense here?
The 10/8 network doesn't appear anywhere on your diagram so I'm not sure why or where that is being used.
You need to pass a route to 172.17.172.0/24 to clients connecting to the server.
Steve
-
Looks to me like a asymmetrical mess waiting to happen.. Since I assume that router 172.17.172.1 is the default gateway for those servers.
And yeah don't see where this 10 network comes into play.. And unless your trying to summary route - 10/8 is a horrible Idea!!
Not sure why you would vpn from rfc to rfc in the first place... is that 192.168.226 your tunnel network?
-
First of all, you need to clarify if the pritunl VPN users (while connected) will be "going" out with their 192.168.22.x IP address , or with the IP address of the Pritunl network interface (192.168.226.1).
Also, I assume that you have created a Server in the pritunl that assigns the 192.168.226.x IP addresses. In that server, you will have to add a route towards the 172.17.172.x network (see below)
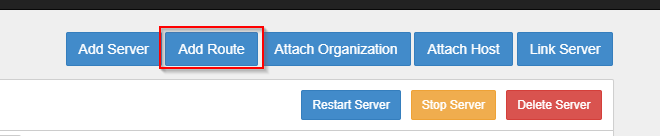
After you do the above, then you can start pinging from a VPN user towards your Servers. In order to see if the Pritunl VPN user is going out with its assigned IP addres (192.168.2226.2) and not with the Pritunl server IP (192.168.226.1), go to Packet Capture in pfsense and check the traffic on the pfsense interface that belongs to 172.17.172.x network.
*I would create an alias for these VPN users and name it "OpenVPN_Users" (Alias type is network with an IP address 192.168.226.0/24).
Then I would go to the firewall rules and I would add a rule to allow the OpenVPN_Users network towards the 102.17.172.0 network. Not sure if you have to configure the Advanced Settings on that rule, but if you still cannot ping the servers, you may have to go and change the TCP flags to "Any" and the State Type to "sloppy" (see below)
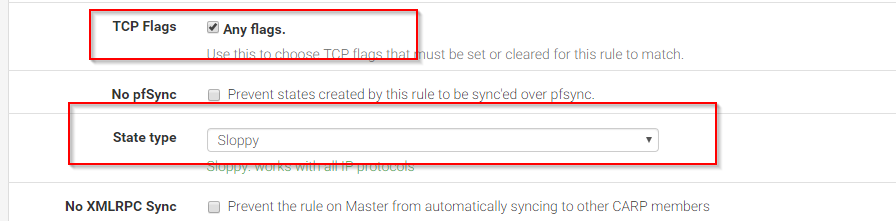
Also, I assume these VPN users will be having internet access via your pfsense, which means that they will be going to the outside world via the WAN interface. If so, maybe you would have to add a NAT rule, but check first if it works without any NAT rule.