NAT 1:1 Polycom VSX 7000
-
Ok well really you would need to get a packet capture of the SIP packets to check that it really is sending the external IP in the SIP connection to open replies to.
There is probably something similar there for the other services but we may not be able to see it.Steve
-
Hi Steve,
I performed a packet capture on WAN-ip, using filter on client remote address "140.242.250.200", my polycom is configured NAT for WAN-IP "189.20.108.XX", you can try to help me based on captured log's.vtcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on sk1, link-type EN10MB (Ethernet), capture size 262144 bytes 14:53:51.195282 IP 189.20.108.XX.3232 > 140.242.250.200.1720: Flags [S], seq 12312384, win 8192, options [mss 1456], length 0 14:53:51.349001 IP 140.242.250.200.1720 > 189.20.108.XX.3232: Flags [S.], seq 1312067764, ack 12312385, win 4380, options [mss 1460], length 0 14:53:51.351178 IP 189.20.108.XX.3232 > 140.242.250.200.1720: Flags [.], ack 1, win 8192, length 0 14:53:51.365850 IP 189.20.108.XX.3232 > 140.242.250.200.1720: Flags [P.], seq 1:229, ack 1, win 8192, length 228 14:53:51.520050 IP 140.242.250.200.1720 > 189.20.108.XX.3232: Flags [.], ack 229, win 5360, length 0 14:53:51.531834 IP 140.242.250.200.1720 > 189.20.108.XX.3232: Flags [P.], seq 1:111, ack 229, win 5360, length 110 14:53:51.533182 IP 189.20.108.XX.3232 > 140.242.250.200.1720: Flags [.], ack 111, win 8082, length 0 14:53:51.558796 IP 140.242.250.200.1720 > 189.20.108.XX.3232: Flags [P.], seq 111:261, ack 229, win 5360, length 150 14:53:51.559118 IP 189.20.108.XX.3232 > 140.242.250.200.1720: Flags [.], ack 261, win 8042, length 0 14:53:51.564237 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [S], seq 12440638, win 8192, options [mss 1456], length 0 14:53:51.716167 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [S.], seq 1302810247, ack 12440639, win 4380, options [mss 1460], length 0 14:53:51.717206 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 1, win 8192, length 0 14:53:51.783631 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 1:846, ack 1, win 8192, length 845 14:53:51.786574 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 846:857, ack 1, win 8192, length 11 14:53:51.885921 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 1:513, ack 1, win 4380, length 512 14:53:51.885933 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 513:945, ack 1, win 4380, length 432 14:53:51.887110 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 513, win 7680, length 0 14:53:51.887206 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 945, win 7248, length 0 14:53:51.887416 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 945:956, ack 1, win 4380, length 11 14:53:51.889096 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 956, win 7237, length 0 14:53:51.940740 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [.], ack 846, win 5915, length 0 14:53:51.940752 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [.], ack 857, win 5915, length 0 14:53:51.958866 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 857:864, ack 956, win 8181, length 7 14:53:51.963400 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 864:870, ack 956, win 8192, length 6 14:53:52.038397 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 956:969, ack 857, win 5915, length 13 14:53:52.039127 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 969, win 8179, length 0 14:53:52.063747 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 870:915, ack 969, win 8192, length 45 14:53:52.091200 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 915:1004, ack 969, win 8192, length 89 14:53:52.132462 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [.], ack 870, win 5915, length 0 14:53:52.143346 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 969:1014, ack 870, win 5915, length 45 14:53:52.145111 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 1014, win 8147, length 0 14:53:52.146042 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 1014:1112, ack 870, win 5915, length 98 14:53:52.147115 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 1112, win 8049, length 0 14:53:52.148748 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 1112:1249, ack 870, win 5915, length 137 14:53:52.149125 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 1249, win 7912, length 0 14:53:52.150236 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 1249:1284, ack 870, win 5915, length 35 14:53:52.151142 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 1284, win 7922, length 0 14:53:52.165168 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 1004:1031, ack 1284, win 7922, length 27 14:53:52.186843 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 1031:1058, ack 1284, win 8020, length 27 14:53:52.188603 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 1058:1069, ack 1284, win 8020, length 11 14:53:52.190754 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 1069:1077, ack 1284, win 8020, length 8 14:53:52.208542 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 1077:1206, ack 1284, win 8020, length 129 14:53:52.210436 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 1206:1214, ack 1284, win 8020, length 8 14:53:52.226882 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 1214:1241, ack 1284, win 8157, length 27 14:53:52.228475 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 1241:1249, ack 1284, win 8157, length 8 14:53:52.229118 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 1284:1293, ack 915, win 5915, length 9 14:53:52.231158 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 1293, win 8183, length 14:53:52.244894 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 1249:1284, ack 1293, win 8183, length 35 14:53:52.247840 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 1284:1311, ack 1293, win 8183, length 27 14:53:52.272856 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 1293:1302, ack 1004, win 5915, length 9 14:53:52.273134 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 1302, win 8183, length 0 14:53:52.321386 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 1302:1311, ack 1031, win 5915, length 9 14:53:52.323134 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 1311, win 8183, length 0 14:53:52.350844 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 1311:1324, ack 1077, win 5915, length 13 14:53:52.351147 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 1324, win 8179, length 0 14:53:52.383996 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 1324:1333, ack 1249, win 7605, length 9 14:53:52.385144 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 1333, win 8183, length 0 14:53:52.417547 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 1333:1342, ack 1311, win 7605, length 9 14:53:52.419156 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 1342, win 8183, length 0 14:53:53.191208 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 1311:1322, ack 1342, win 8192, length 11 14:53:53.191891 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 1322:1330, ack 1342, win 8192, length 8 14:53:53.349391 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 1342:1355, ack 1330, win 7605, length 13 14:53:53.351151 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 1355, win 8179, length 0 14:53:54.079736 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 1330:1365, ack 1355, win 8192, length 35 14:53:54.091519 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 1365:1494, ack 1355, win 8192, length 129 14:53:54.233905 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 1355:1364, ack 1365, win 7605, length 9 14:53:54.235171 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 1364, win 8183, length 0 14:53:54.273647 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 1364:1373, ack 1494, win 9295, length 9 14:53:54.275186 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 1373, win 8183, length 0 14:53:54.286645 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 1494:1529, ack 1373, win 8192, length 35 14:53:54.301896 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 1529:1658, ack 1373, win 8192, length 129 14:53:54.448893 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 1373:1382, ack 1529, win 9295, length 9 14:53:54.451173 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 1382, win 8183, length 0 14:53:54.488835 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 1382:1391, ack 1658, win 10985, length 9 14:53:54.489155 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 1391, win 8183, length 0 14:53:54.499932 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 1658:1693, ack 1391, win 8192, length 35 14:53:54.514226 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 1693:1822, ack 1391, win 8192, length 129 14:53:54.658089 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 1391:1400, ack 1693, win 10985, length 9 14:53:54.659249 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 1400, win 8183, length 0 14:53:54.698031 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 1400:1409, ack 1822, win 12675, length 9 14:53:54.699194 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 1409, win 8183, length 0 14:53:54.709097 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 1822:1857, ack 1409, win 8192, length 35 14:53:54.724136 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 1857:1986, ack 1409, win 8192, length 129 14:53:54.866983 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 1409:1418, ack 1857, win 12675, length 9 14:53:54.869173 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 1418, win 8183, length 0 14:53:54.905928 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 1418:1427, ack 1986, win 14365, length 9 14:53:54.907210 IP 189.20.108.X.3233 > 140.242.250.200.3234: Flags [.], ack 1427, win 8183, length 0 14:53:54.919729 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 1986:2021, ack 1427, win 8192, length 35 14:53:54.931719 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 2021:2150, ack 1427, win 8192, length 129 14:53:55.076380 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 1427:1436, ack 2021, win 14365, length 9 14:53:55.077207 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 1436, win 8183, length 0 14:53:55.115922 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 1436:1445, ack 2150, win 16055, length 9 14:53:55.117191 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 1445, win 8183, length 0 14:53:55.128352 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 2150:2185, ack 1445, win 8192, length 35 14:53:55.145844 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 2185:2314, ack 1445, win 8192, length 129 14:53:55.284777 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 1445:1454, ack 2185, win 16055, length 9 14:53:55.285173 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 1454, win 8183, length 0 14:53:55.323921 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 1454:1463, ack 2314, win 17745, length 9 14:53:55.325200 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 1463, win 8183, length 0 14:53:55.340885 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 2314:2349, ack 1463, win 8192, length 35 14:53:55.352551 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 2349:2478, ack 1463, win 8192, length 129 14:53:55.504857 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 1463:1472, ack 2478, win 19435, length 9 14:53:55.505197 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 1472, win 8183, length 0 14:53:55.545598 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 1472:1481, ack 2478, win 19435, length 9 14:53:55.547156 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 1481, win 8183, length 0 14:53:55.561711 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 2478:2513, ack 1481, win 8192, length 35 14:53:55.573761 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 2513:2642, ack 1481, win 8192, length 129 14:53:55.725037 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 1481:1490, ack 2513, win 19435, length 9 14:53:55.727196 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 1490, win 8183, length 0 14:53:55.765379 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 1490:1499, ack 2642, win 21125, length 9 14:53:55.767187 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 1499, win 8183, length 0 14:53:55.780891 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 2642:2677, ack 1499, win 8192, length 35 14:53:55.794249 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 2677:2806, ack 1499, win 8192, length 129 14:53:55.944518 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 1499:1508, ack 2677, win 21125, length 9 14:53:55.945185 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 1508, win 8183, length 0 14:53:55.984359 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 1508:1517, ack 2806, win 22815, length 9 14:53:55.985173 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 1517, win 8183, length 0 14:53:56.001818 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 2806:2841, ack 1517, win 8192, length 35 14:53:56.014327 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 2841:2970, ack 1517, win 8192, length 129 14:53:56.164897 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 1517:1526, ack 2841, win 22815, length 9 14:53:56.165186 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 1526, win 8183, length 0 14:53:56.205638 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [.], ack 2970, win 24505, length 0 14:53:56.206037 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 1526:1535, ack 2970, win 24505, length 9 14:53:56.207233 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 1535, win 8183, length 0 14:53:56.219839 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 2970:3005, ack 1535, win 8192, length 35 14:53:56.233469 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 3005:3134, ack 1535, win 8192, length 129 14:53:56.371796 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [.], ack 3005, win 24505, length 0 14:53:56.373793 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 1535:1544, ack 3005, win 24505, length 9 14:53:56.375309 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 1544, win 8183, length 0 14:53:56.414175 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 1544:1553, ack 3134, win 26195, length 9 14:53:56.415189 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 1553, win 8183, length 0 14:53:56.428395 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 3134:3169, ack 1553, win 8192, length 35 14:53:56.444410 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 3169:3298, ack 1553, win 8192, length 129 14:53:56.583387 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 1553:1562, ack 3169, win 26195, length 9 14:53:56.585194 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 1562, win 8183, length 0 14:53:56.622732 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 1562:1571, ack 3298, win 27885, length 9 14:53:56.623175 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 1571, win 8183, length 0 14:53:56.640433 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 3298:3333, ack 1571, win 8192, length 35 14:53:56.652612 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 3333:3462, ack 1571, win 8192, length 129 14:53:56.803268 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 1571:1580, ack 3333, win 27885, length 9 14:53:56.805199 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 1580, win 8183, length 0 14:53:56.842812 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 1580:1589, ack 3462, win 29575, length 9 14:53:56.843208 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 1589, win 8183, length 0 14:53:56.861649 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 3462:3497, ack 1589, win 8192, length 35 14:53:56.873558 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 3497:3626, ack 1589, win 8192, length 129 14:53:57.022749 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 1589:1598, ack 3497, win 29575, length 9 14:53:57.023187 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 1598, win 8183, length 0 14:53:57.063389 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 1598:1607, ack 3626, win 31265, length 9 14:53:57.065192 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 1607, win 8183, length 0 14:53:57.080970 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 3626:3661, ack 1607, win 8192, length 35 14:53:57.094297 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 3661:3790, ack 1607, win 8192, length 129 14:53:57.243129 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 1607:1616, ack 3661, win 31265, length 9 14:53:57.245203 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 1616, win 8183, length 0 14:53:57.283870 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 1616:1625, ack 3790, win 32955, length 9 14:53:57.285184 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 1625, win 8183, length 0 14:53:57.301597 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 3790:3825, ack 1625, win 8192, length 35 14:53:57.314168 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [P.], seq 3825:3954, ack 1625, win 8192, length 129 14:53:57.462710 IP 140.242.250.200.3234 > 189.20.108.XX.3233: Flags [P.], seq 1625:1634, ack 3825, win 32955, length 9 14:53:57.463192 IP 189.20.108.XX.3233 > 140.242.250.200.3234: Flags [.], ack 1634, win 8183, length 0Best regards,
Wesley Santos -
You need to look into the SIP protocol and see what it's doing.
-
Yes, you would need to filer additionally by port 5060 and then download and check the actual SIP packets to see what is being sent. You probably don't want to post that publicly though.
Steve
-
What would the tcpdump command syntax look like, just to filter everything to my wan-ip port 189.20.108.XX port 5060?
-
I would do it from the GUI but: https://docs.netgate.com/pfsense/en/latest/monitoring/performing-a-packet-capture.html
Steve
-
Hi Steve, how are you?
I monitored a connection made by my videoconferencing system, using "pftop" CLI my polycom connects with the target, but "NO_TRAFFIC: SINGLE" communication errors occur.PR DIR SRC DEST STATE AGE EXP PKTS BYTES rsvp In 192.168.40.251:0 140.242.250.200:0 NO_TRAFFIC:SINGLE 00:15:15 00:00:19 0 0 tcp In 192.168.40.251:3233 140.242.250.200:1720 ESTABLISHED:ESTABLISHED 00:07:57 23:58:04 15 1096 tcp Out 189.20.108.XX:3233 140.242.250.200:1720 ESTABLISHED:ESTABLISHED 00:07:57 23:58:04 15 1096 tcp In 192.168.40.251:3234 140.242.250.200:3242 ESTABLISHED:ESTABLISHED 00:07:57 23:59:35 181 10480 tcp Out 189.20.108.XX:3234 140.242.250.200:3242 ESTABLISHED:ESTABLISHED 00:07:57 23:59:35 181 10480 udp In 192.168.40.251:3232 140.242.250.200:3262 NO_TRAFFIC:SINGLE 00:07:56 00:00:30 19850 13004860 udp Out 189.20.108.XX:3232 140.242.250.200:3262 SINGLE:NO_TRAFFIC 00:07:56 00:00:30 19850 13004860 udp In 192.168.40.251:3231 140.242.250.200:3261 NO_TRAFFIC:SINGLE 00:07:51 00:00:29 95 7220 udp Out 189.20.108.XX:3231 140.242.250.200:3261 SINGLE:NO_TRAFFIC 00:07:51 00:00:29 95 7220 udp In 192.168.40.251:3233 140.242.250.200:3263 NO_TRAFFIC:SINGLE 00:07:51 00:00:29 95 9120 udp Out 189.20.108.XX:3233 140.242.250.200:3263 SINGLE:NO_TRAFFIC 00:07:51 00:00:29 95 9120 udp In 192.168.40.251:3235 140.242.250.200:3265 NO_TRAFFIC:SINGLE 00:07:51 00:00:29 95 7220 udp Out 189.20.108.XX:3235 140.242.250.200:3265 SINGLE:NO_TRAFFIC 00:07:51 00:00:29 95 7220 udp In 192.168.40.251:3237 140.242.250.200:3267 NO_TRAFFIC:SINGLE 00:07:51 00:00:29 95 7240 udp Out 189.20.108.XX:3237 140.242.250.200:3267 SINGLE:NO_TRAFFIC 00:07:51 00:00:29 95 7240Best regards,
Wesley Santos -
That's not necessarily an error but you would expect more traffic when it connects correctly.
I would bet it's sending it's internal private IP still we've seen that many many times. Including numerous times when a VoIP provider told us it definitely wasn't and we had to prove it was using packet captures.
We would need to see the SIP packets to be sure.
PM them to me if you prefer. I'll take a look when I have time.
Steve
-
can i send you a .pcap packet capture for you to help analyze?
-
Yes, start a chat and attach it there.
-
not allowed, your chat is restricted to people you follow only
-
Post whatever it is you think is telling you that. If that is the case it should not be. People chat me all the time without following.
-
ERROR
This user has restricted their chat messages. They must follow you before you can talk to them -
Hmm, must have changed the default at a forum update or something. I've changed that setting now, try again.
Steve
-
Your chat is now released.
-
Dear, I made the capture available on Google Drive
-
Great I have that.
There are no SIP packets in there so I can't check that directly but it looks like it's still sending it's internal IP as the address to connect back to which can never work. For example:
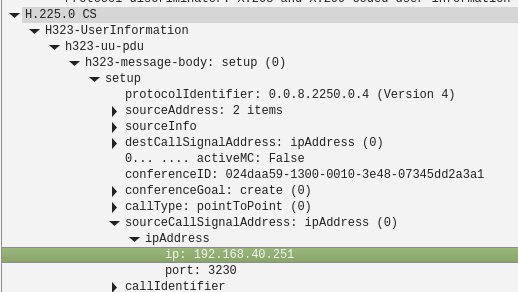
And:
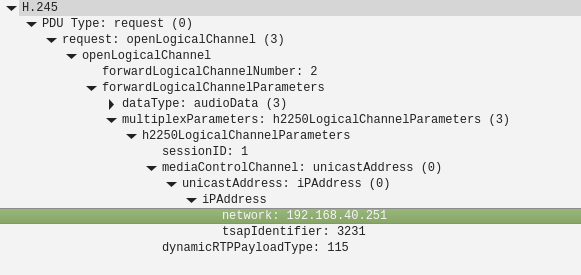
I won't to be any sort of expert in those protocols but from your description of the behaviour and the fact we see only outgoing RTP traffic in the pcap I think it is not configured to send the external IP.
You need to set that correctly in the Polycom device before it can work behind NAT.
Steve
-
Hi, thanks for your effort to help solve my case.
Please can you explain if I used the filter correctly, I intended to monitor only LAN-ip traffic, using a filter for polycom IP address "192.168.40.251", when NAT requests occur, they should be caught in tcpdump using the command filter below?tcpdump -nvxi re0 -w capture.pcap host 192.168.40.251I captured packets from the WAN-ip interface, using a filter for WAN-ip and LAN-ip addresses, but when analyzing wireshark did not find NAT requests, I will forward the link of this packet in your chat.
I used the command below.tcpdump -nvxi sk1 -w new.pcap "(host 189.20.108.XX or host 192.168.40.251)"Best regards,
Wesley Santos -
It has nothing to do with the filter.
The PBX is telling the far side to connect back to 192.168.40.251 on port 3230 for RTP.
Obviously the far side cannot do that because that is your inside, non-routable, RFC1918 address.
You need to tell the PBX to send your outside WAN address there instead.
It is embedded in the SIP protocol. NAT can't translate it and there is no SIP ALG in pfSense to do it for you either.
-
Hey man, how you doing?
I reviewed all NAT settings applied to "Polycom VSX 7000", also restored the applied settings and configured them again. I can not understand what I am configuring wrong with NAT inside the pfsense firewall, the polycom NAT settings are very simple, below are some pictures of the polycom NAT settings.LAN properties.
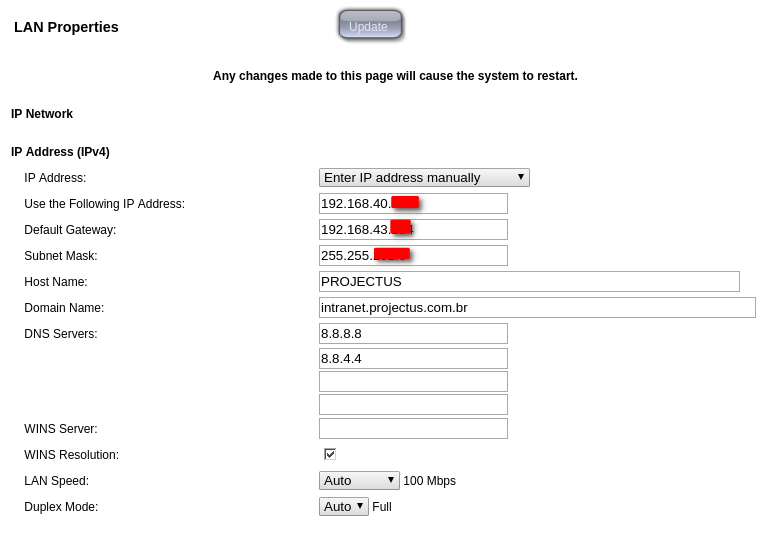
Polycom NAT Settings.
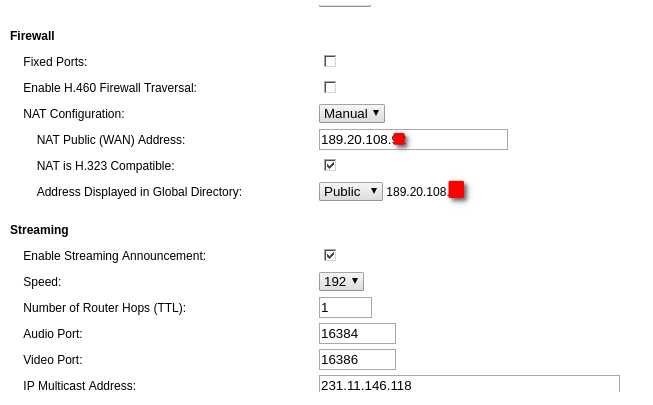
Best regards,
Wesley Santos