Guest network to Netgate SG-1100 (without modem) installation
-
Hello all,
I write the forum as someone relatively new to networking. I have attempted several times to connect my SG-1100 router to a guest RJ45 (wall outlet) at work and have yet to connect to the internet. I noticed in the user manual that internet connection can be gained by booting up a cable modem and router simultaneously, which I have successfully done with the SG-1100 in my home network. Is there any way to gain internet connection from an ethernet wall outlet to the SG-1100? If so, am I experiencing a firewall or hardware issue?
Your help is greatly appreciated!! -
The WAN is set to grab an IP via DHCP. If the network you're plugging into doesn't have a DHCP server to assign addresses, then you're not going to get anywhere. In that case, you would need to manually assign an address, mask, gateway and DNS to connect.
-
Also, by default the WAN interface blocks private IP addresses (RFC-1918), so if it is served a private IP address by the DHCP server behind the wall socket, nothing works unless you allow private addresses on WAN.
-
@keyser I don't know if it works that way. Block RFC1918 is meant to stop unsolicited inbound traffic. A DHCP offer is a reply to a DHCP discovery so the state is already established, so the traffic should flow. I'm assuming pfSense can track a reply to a broadcast. Like you said, otherwise it would appear dead and that's not good.
-
As far as I recall nothing worked the last time I tried until i lifted the 1918 block. But my memory is not what is has been, so I'm not a 100% sure... Age - who needs it?
-
Actually I know for a fact that it works. I just remembered that in my virtual lab (virtualbox), I have pfSense configured to use my real LAN as its WAN and another private network as its LAN. It has no problems getting a WAN address from my real router.
-
Yeah not sure why there is such a misunderstanding about this rule.. Its meant to stop unsolicited traffic from rfc1918 hitting your port forwards. It in no way would stop your pfsense from getting an IP from a rfc1918 dhcp server.
There are rules in place to allow dhcp to the wan, that are not shown.. Doesn't matter if you have a rule to block rfc1918..
The only reason you should ever have to turn that rule off is if your behind a nat and you want something on wan side of pfsense to be able to get to some port forward you setup..
Other reason you might turn it off is just don't want to see it ;) Since it really doesn't do much from a security aspect.. If I forwarded a port, and the source is set to any.. I don't really care if some rfc1918 hits me, etc. ;) To be honest the bogon pretty much falls into the same boat.. And think the rules themselves cause more questions and posts and issues.. Have seen lots of times users putting the bogon rules on lan side network, or ever the rfc1918 rules and then wondering why X doesn't work.
Both of those rules don't really provide much "security".. And cause prob way more questions if anything, but not an issue for your box not being able to get a dhcp address.
-
Thanks for the clarification.
Have I mentioned lately that I hate hidden rules? They should be visible in the GUI, in their proper order, and greyed out so you can't move or edit them in any way. But at least you know they are there and what they do. And yes, I'm aware I could go to shell and do a rule dump but that's an ugly hassle.
-
I concur - there should be a toggle for sure that can display them.. I would vote as well for such an option.. I think it the big picture it would confuse more users than help others that understand what they are doing ;)
Maybe have to pass a test of basic understanding of firewall rule concepts before you can show the hidden rules ;)
I could see a flood of, how do I stop the rule that allows the firewall outbound.. And then wondering why they are offline because the firewall can not even ask for a dhcp address or query for dns, etc. etc.
There was a recent post about wanting to block pfsense from talking outbound.. It was his firewall, he didn't want it to be able to talk outbound without him allowing it.. Do you know how many systems would be useless or how many posts and calls that would generate. if users could stop the firewall from talking outbound, or would have to allow it to happen for say dhcp to work ;)
-
@johnpoz Thanks for the clarification - my bad :-) Must have been some other situation I remembered. Good to know going forward :-)
-
@KOM Thanks for the reply! This was definitely helpful for me.
-
I'm a little late to this party, but I would also vote "yes" to having a "display hidden rules" option in the GUI. Would be fine to default the option to "off".
I managed Checkpoint firewalls for many years and they also have hidden rules except they call them "implied rules". But there is a mechanism to display them in their firewall management GUI tool if you had a need to examine them.
-
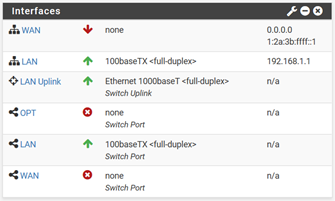
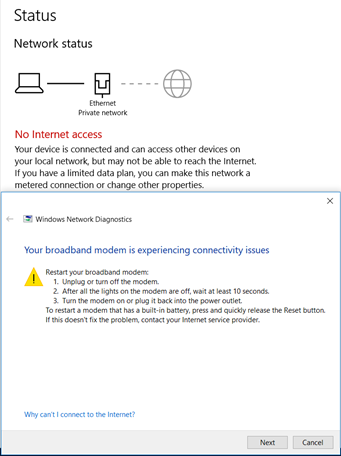
Hey all, so I have a couple questions about manually assigning an address, mask, etc. @KOM might be able to help me the most here. I went to the PFsense user interface, clicked on the System tab and scrolled down to the Setup Wizard secondary tab. Proceeding to step 4, I configured and typed in a static IP. Is this the correct approach? The WAN port is still down as seen in the attached photo. I have also included the error I am getting on Windows 10.
-
Well if your wan is down - not sure how you think some pc on your lan is going to have internet?
-
WAN is 0.0.0.0 which means it's in DHCP mode but did not get an address from your ISP. Maybe there is something going on with your switch port config. I've never used Netgate hardware so I don't really know much about that.
-
@rpwoods13 said in Guest network to Netgate SG-1100 (without modem) installation:
to a guest RJ45 (wall outlet) at work and have yet to connect to the internet.
If this is like any actual work network, any unused ports would be disabled.. And if live they would have some sort of port security on them - only specific mac, or have to auth via 802.1x etc.
But your not going anywhere unless you can get an IP on wan.
-
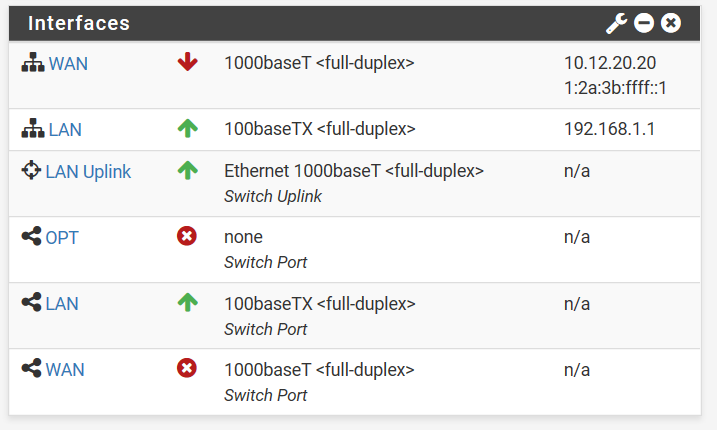
I assigned a static IP address once again to get an IP for the WAN port. The WAN port is still down, but instead of ‘none’ consistently showing, I have ‘1000baseT<full-duplex>‘ alternating with ‘none’. Thoughts?
-
-
Was that static IP address assigned to you by your ISP? You can't just pick one out of the air and use it and expect it to work.
-
Again, I don't know much about Netgate hardware and the switch port but the fact that your WAN switch port is down is probably not a good sign.
-
-
You can not just assign a random static IP and expect get anywhere..
if your interface keeps going up down, errors, etc. then points to something wrong with that port, or security set on it, etc. Like I mentioned if work network - they should unless some ma and pop shop, have some sort of NAC setup so random people can not just plug shit into any random port and get on the network.
I suggest you get with the IT dept on what your wanting to do.
edit: example even our conference rooms, there are multiple interfaces right in the table.. But they are disabled until specifically requested to be turned on and connected to the guest network. Most guests are expected to just use the wireless guest network. If for some reason they request a wired port, then we would enable that port for guest access. And when the meeting over the port would be disabled.
If that interface is suppose to be active.. Then its should just be dhcp, or the IT dept would tell you what IP/MASK and gateway to setup. But if the interface status is bouncing up/down/duplex changing, etc. Then it points to something wrong with that port or cable your using.. Or something wrong with the port on the sg1100.. If you plug the sg1100 wan into say your soho router at home does it get an IP?
-
Until you see thr WAN switch port show a link you have no upstream connectivity. The wall jack you are testing may just be disconnected from what we are seeing right now.
Steve